
Okta
Octa
Okta's OIN catalog app "Google Workspace" supports multi-IdP linkage
Introduction
Among the SaaS used via Okta, one of the most major SaaS is Google Workspace. Until now, Okta's OIN app could not be linked with multiple IdPs, and had to be linked as a custom app.
This time, I will introduce the actual multi-IdP integration of Okta-Google Workspace.
What is multi-IdP integration?
Multi-IdP integration refers to linking a single SaaS with multiple IdPs. By doing this cooperation, the following cases can be handled.
- Single sign-on (SSO) to common SaaS with different IdP for each group company
- Single sign-on (SSO) with Okta only for some users when switching from another IdP to Okta
What is OIN
OIN is an abbreviation for "Okta Integration Network" and is a "setting template for SaaS linkage" prepared in advance by Okta.
Cooperation by OIN
Okta currently provides more than 7,400 SSO integration templates with SaaS, and even if you are setting up Okta and SaaS integration for the first time, you can easily and quickly set it up by using OIN.
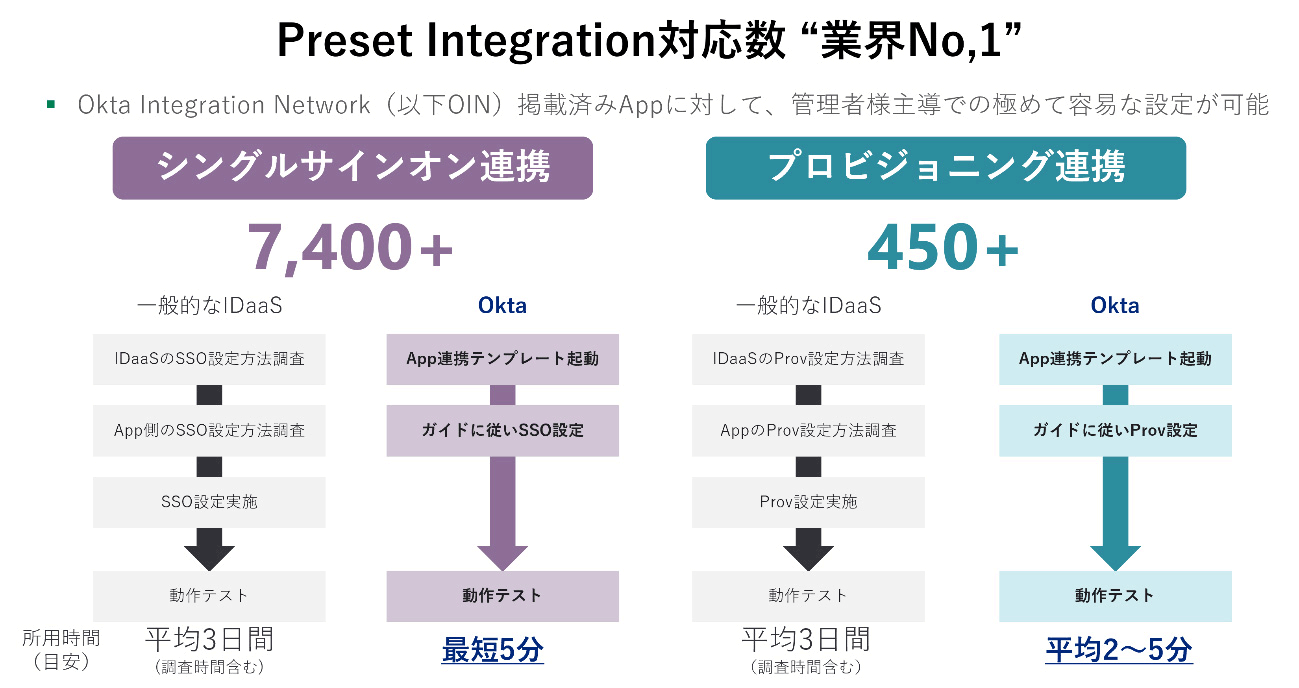
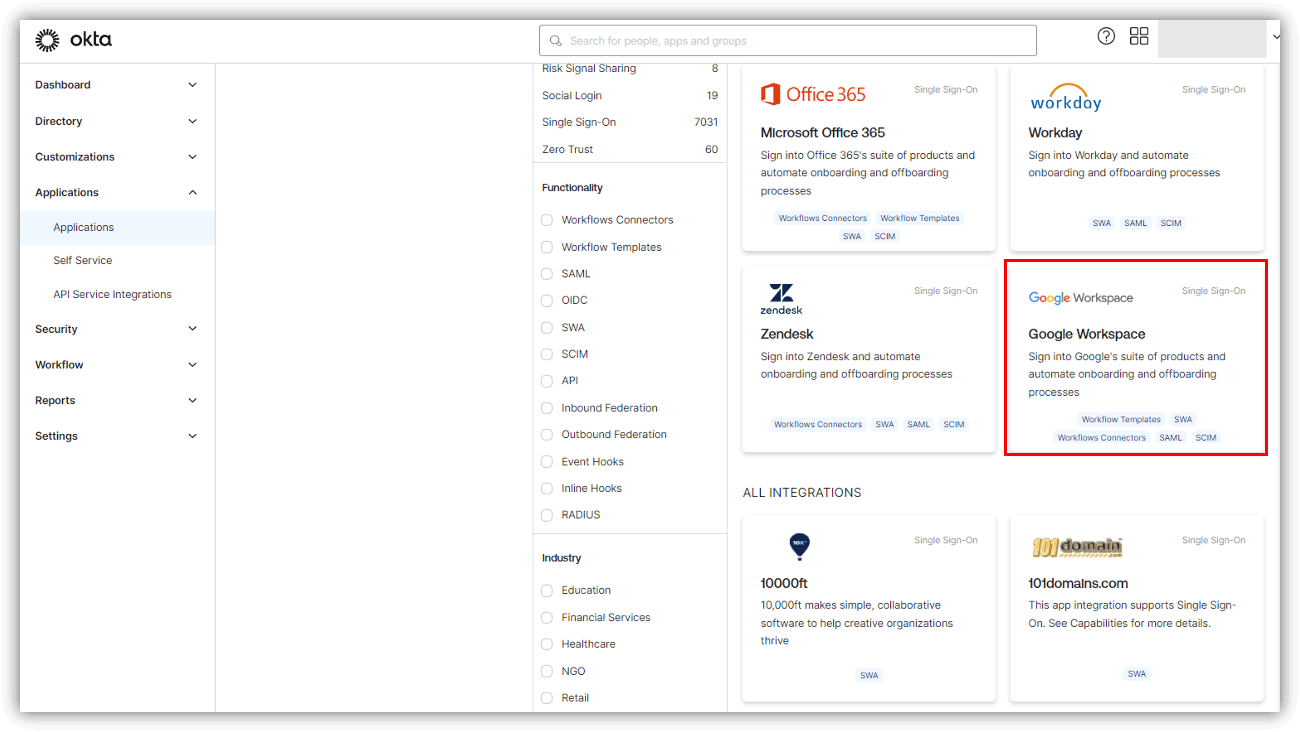
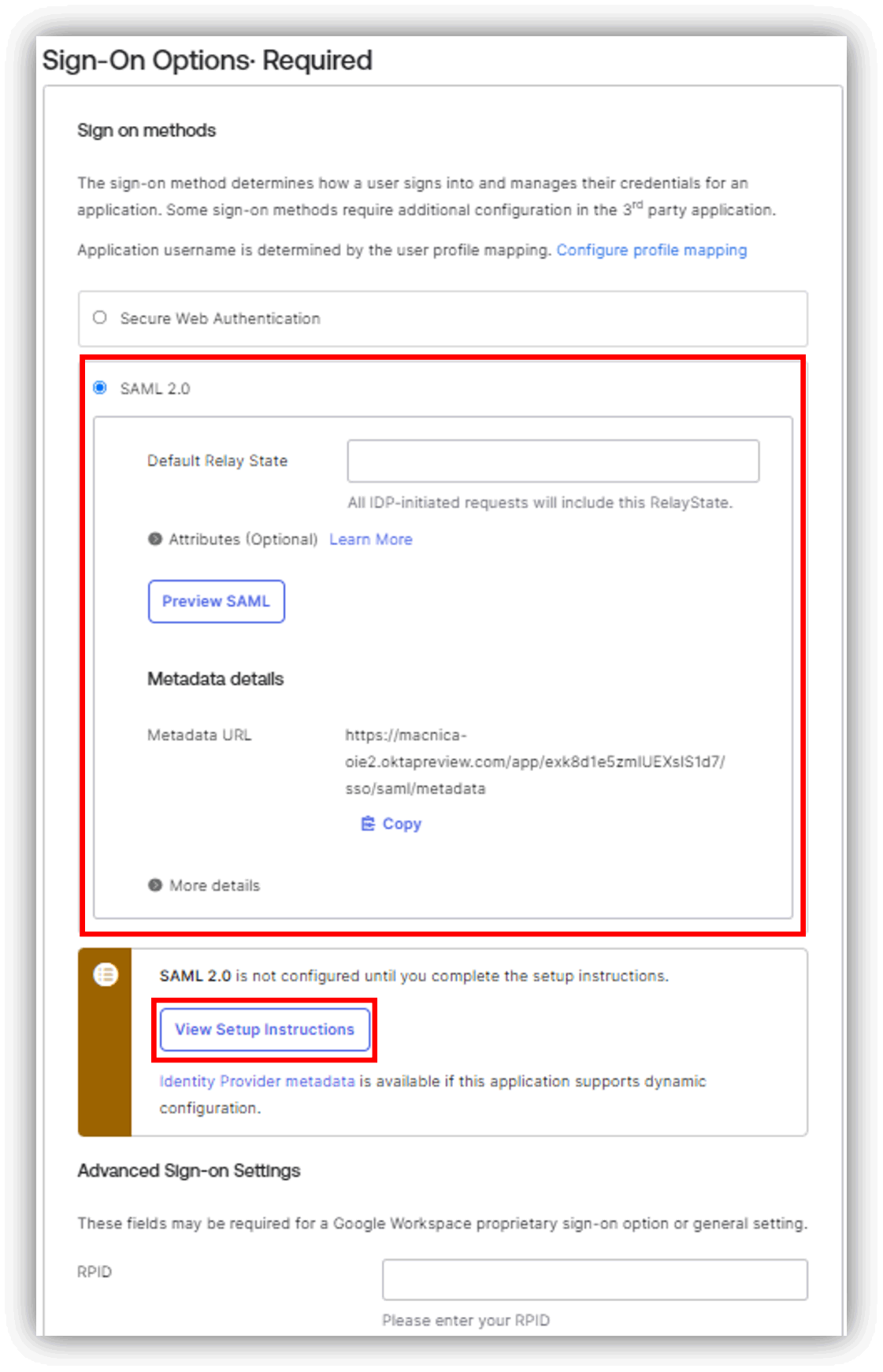
The following (red frame) is the link setting template of Google Workspace.

Okta-Google Workspace multi-IdP configuration example
We will introduce the settings assuming single sign-on (SSO) to Google Workspace via different IdPs for the head office (entire organization) and group companies.
In addition, this time, it is assumed that the IdP settings for the entire organization are set in Google Workspace's "Third-party SSO profile for organizations".
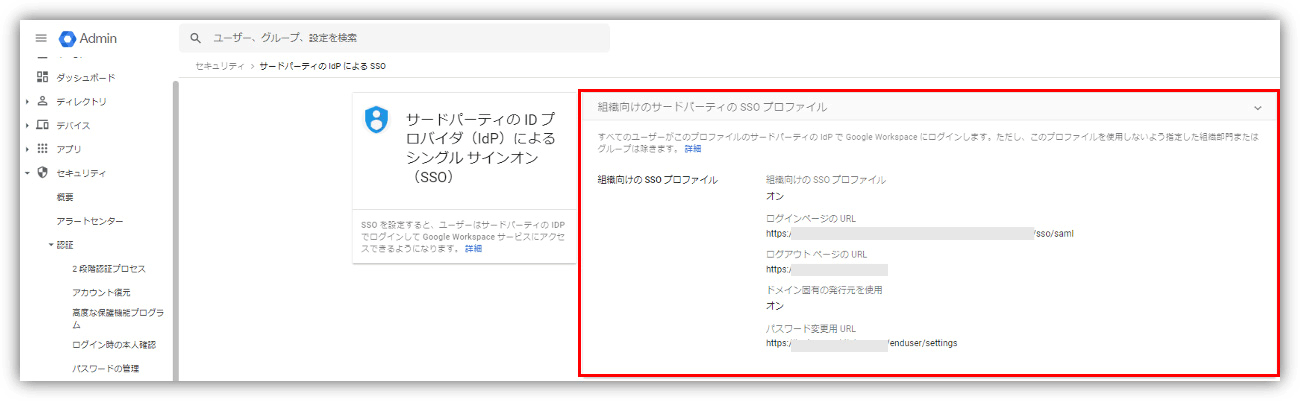
Organization-wide IdP settings
Group company IdP settings
- Scroll down Okta's Setup Instructions screen and check the information required for SAML integration in "SSO profile values"
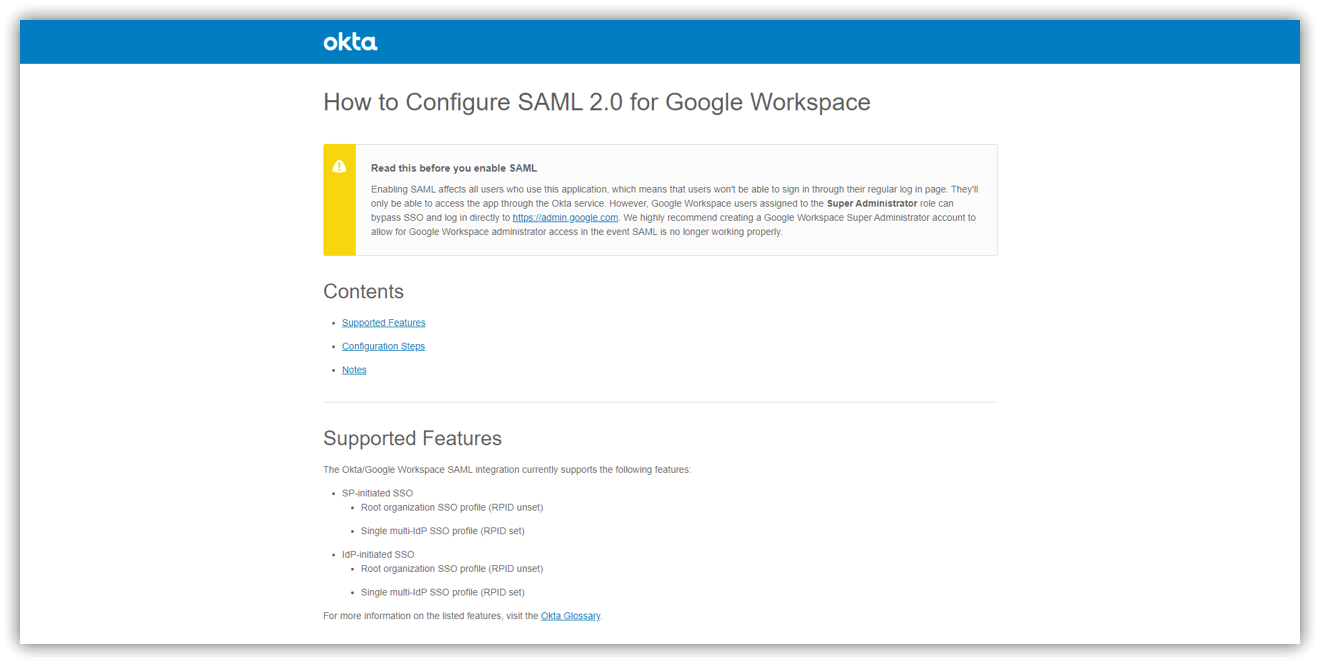
(Okta)SAML setup instructions
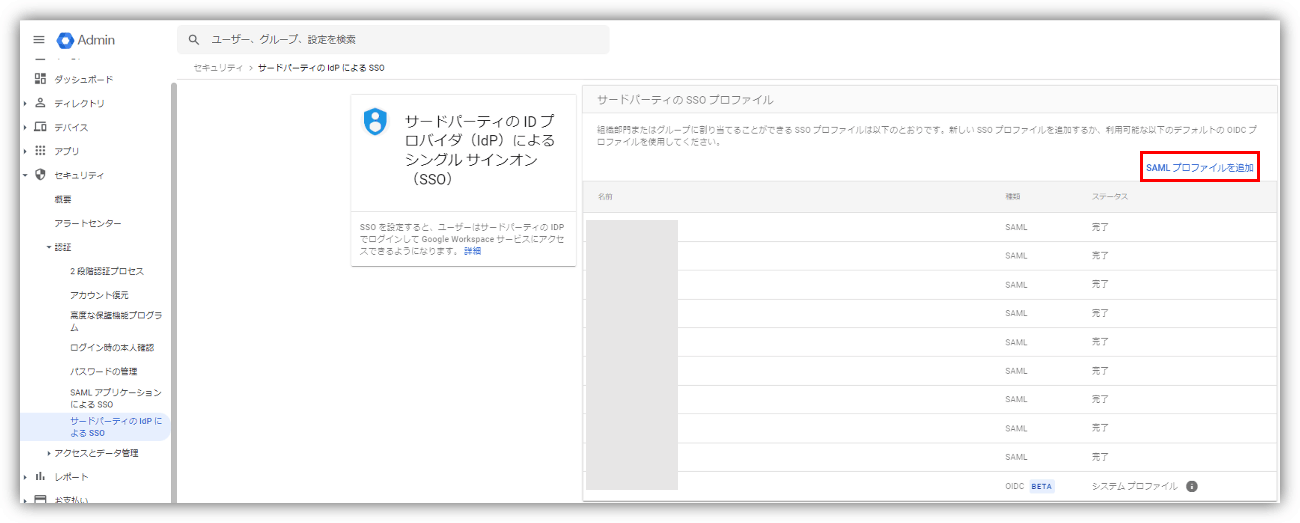
- Click "Add SAML profile" to add SAML linkage profile for group company
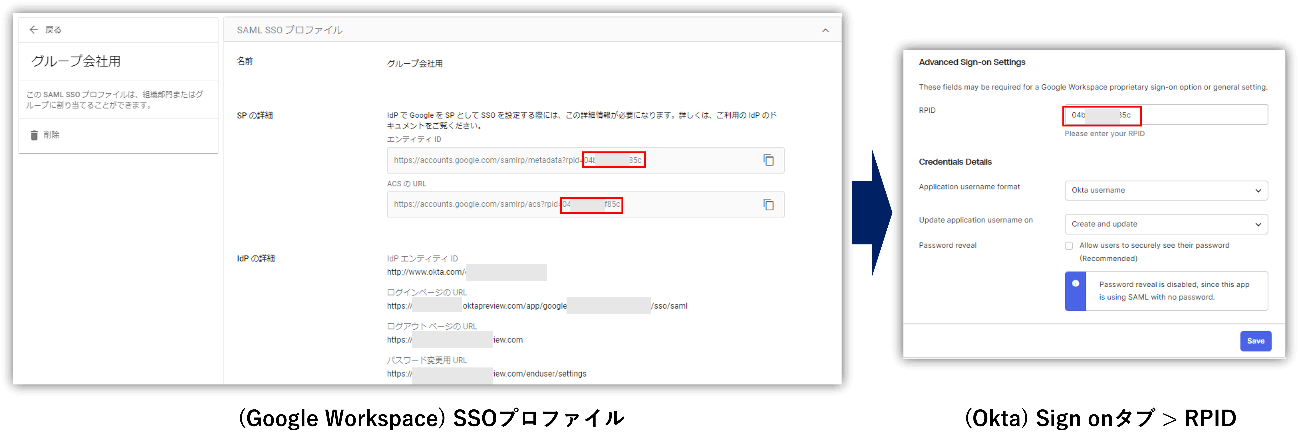
- Enter and upload the values and certificates of the following items described in "SSO profile values" in Okta's Setup Instructions to each item of Google Workspace's SAML SSO profile.
① IdP entity ID
② Sign-in page URL
③ Sign-out page URL
④ Verification Certificate
⑤ Change password URL
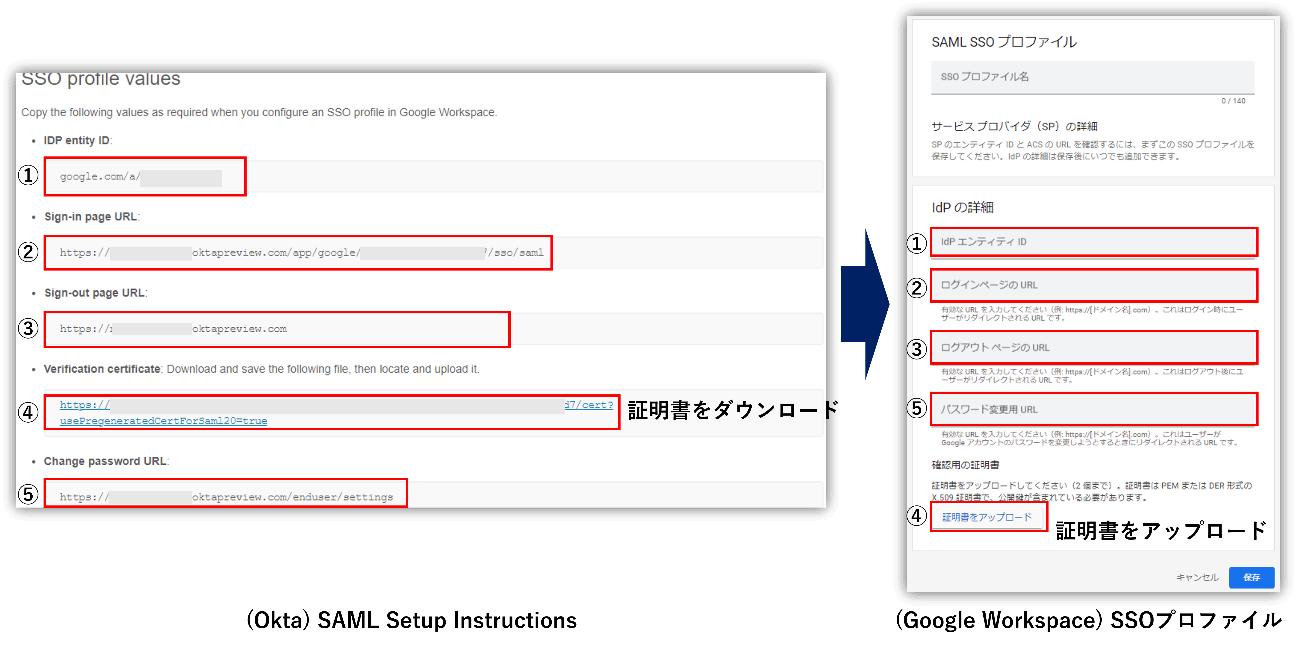
- Enter and upload the values and certificates of the following items described in "SSO profile values" in Okta's Setup Instructions to each item of Google Workspace's SAML SSO profile.
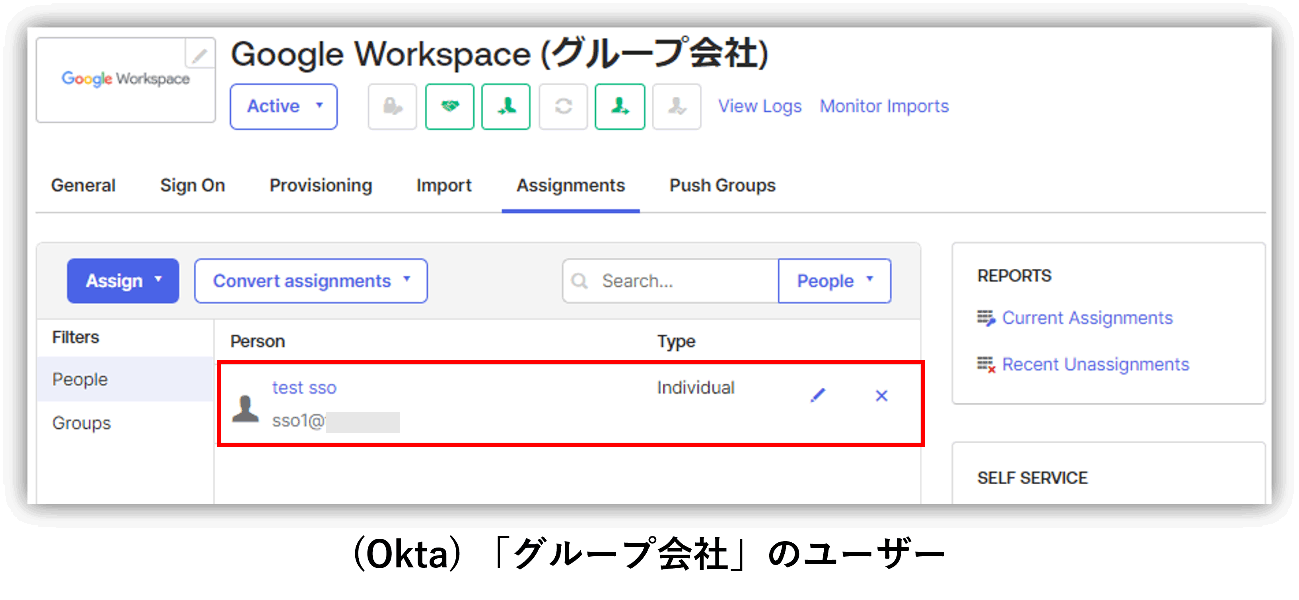
*The created SAML SSO profile can be assigned to each user/group/organizational unit.
*If you check "Redirect to this profile's IdP login page after Google prompts for a username", when an account belonging to a "group company" attempts to log in to Google Workspace, authentication will be redirected to Okta. can be set to
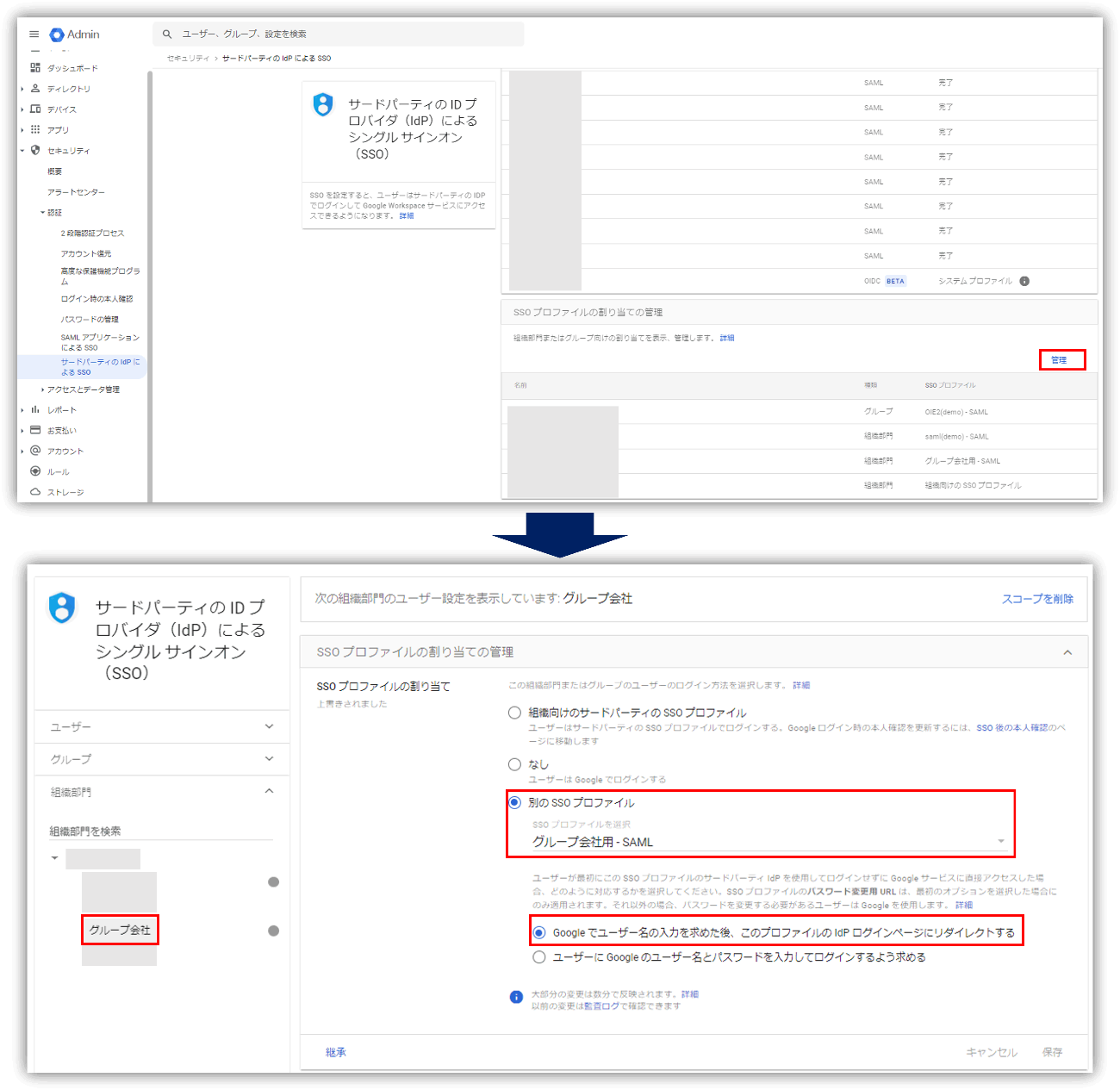
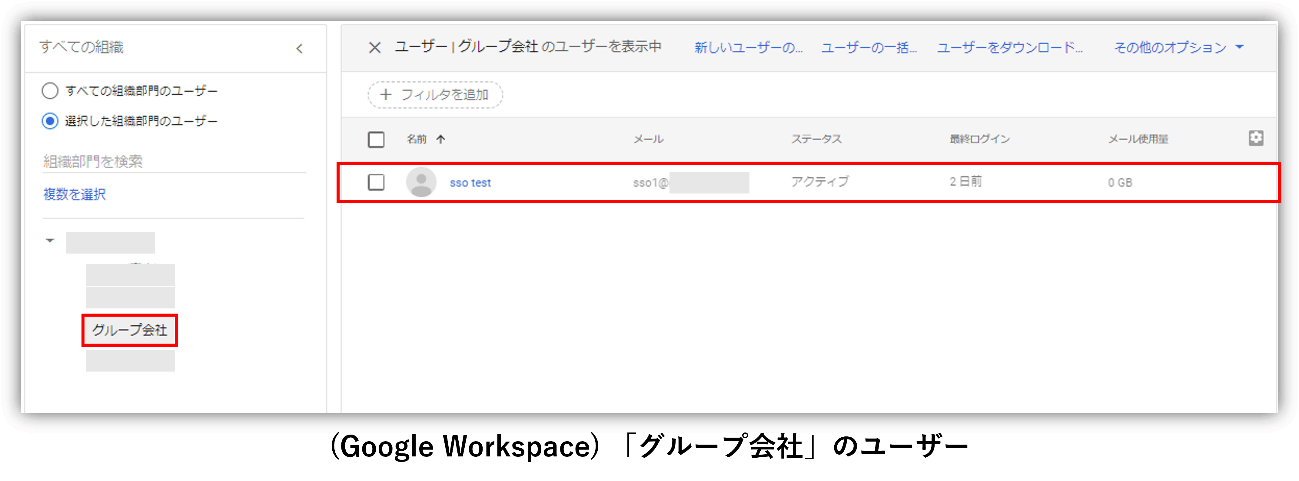
With the above settings, only users belonging to "group companies" can use single sign-on with an IdP that is separate from the entire organization.
Summary
In this blog, I introduced multi-IdP integration with Google Workspace using OIN (Okta Integration Network).
OIN has always been a convenient tool that allows you to easily and quickly integrate with SaaS, but with the release of new features, such as multi-IdP integration with Google Workspace introduced this time, IT administrators will be pleased with the enhancements. I'm here.
Okta can be set up very easily even for SaaS integration other than Google Workspace. If you are interested or have any other inquiries about Okta, please contact us.
Inquiry/Document request
In charge of Macnica Okta Co., Ltd.
- TEL:045-476-2010
- E-mail:okta@macnica.co.jp
Weekdays: 9:00-17:00

