
Okta
Octa
When logging in to Google Workspace, I tried to allow only some users to log in without going through Okta
Introduction
Many SaaS use SAML to link with IDaaS represented by Okta, and login to SaaS will be uniformly via Okta. Therefore, after linking, you will not be able to log in with the same ID/password as before on the SaaS side.
By ensuring that all SaaS logins go through Okta, IP address restrictions, multi-factor authentication, and SaaS login history can be checked. It is recommended to integrate SaaS and Okta with SAML from the point of view of centralized management of login to SaaS on the Okta side and from the viewpoint of strengthening security.
However, if Google Workspace and Okta are SAML linked and all users are via Okta, the welcome email for logging in to Okta for the first time cannot be opened, and as a result, there is a problem that it is impossible to log in to Okta and Google Workspace.
Previously, when Google Workspace and Okta were linked with SAML, it was uniformly via Okta. In November 2021, there will be a God update on the Google Workspace side, and only any user belonging to a specific organizational unit or group can log in directly with the conventional Google Workspace ID / password without going through Okta. Now possible.
For details, please refer to the official website of Google.
https://workspaceupdates-ja.googleblog.com/2021/11/saml-sso-sso.html
In this blog, I will introduce how to automate the following two with the Okta Workflows function.
- How to set some users to log in directly to Google Workspace without going through Okta
- For users who have completed their first login to Okta, the operation to change via Okta
Setting method to log in to Google Workspace without going through Okta
The settings on the Google Workspace side are described below.
<Settings on the Google Workspace side>
- Log in to the Google Workspace admin console
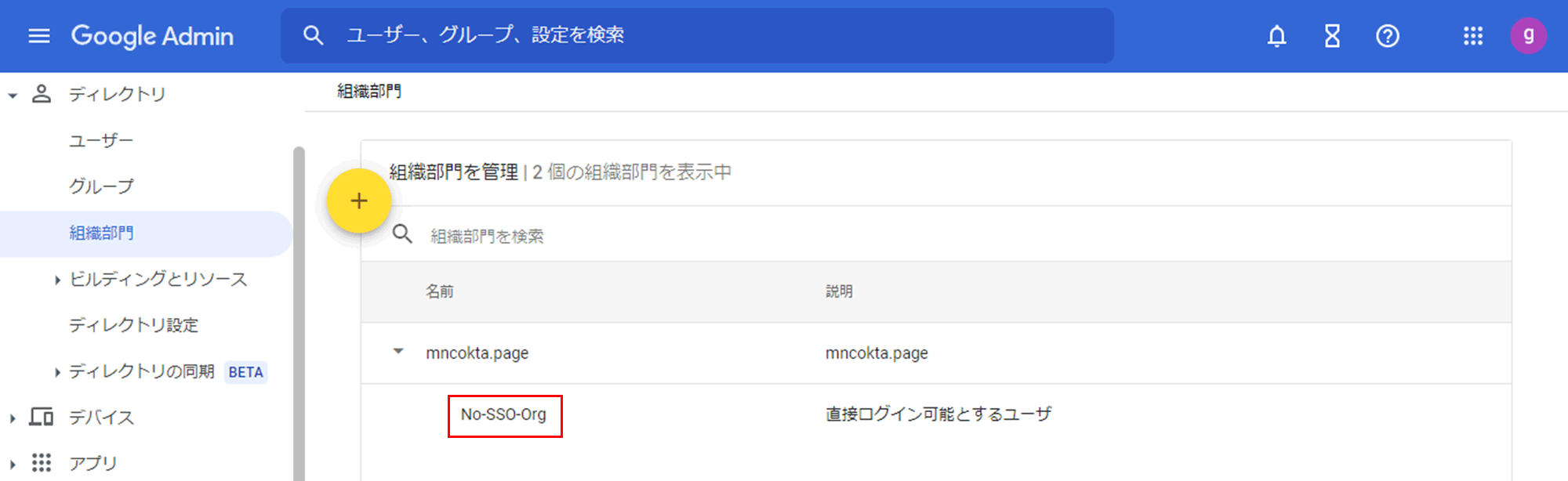
- Create an "organizational unit" or "group" to which users who can log in directly belong
(Example: Create an organizational unit "No-SSO-Org")
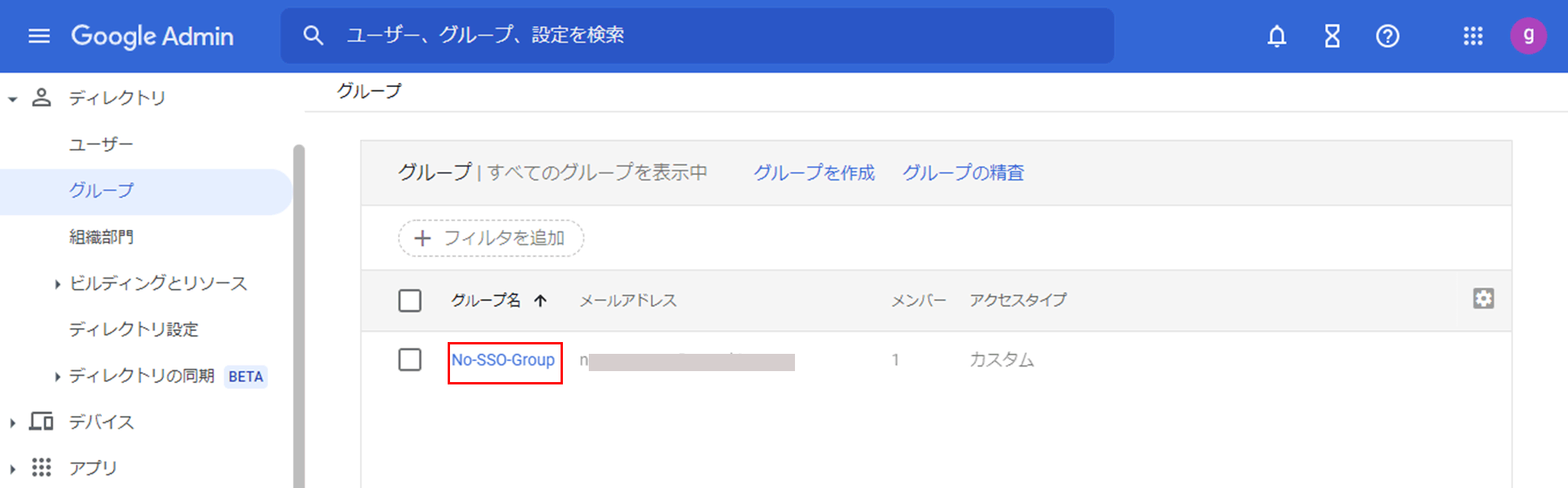
(Example: Create a group "No-SSO-Group")
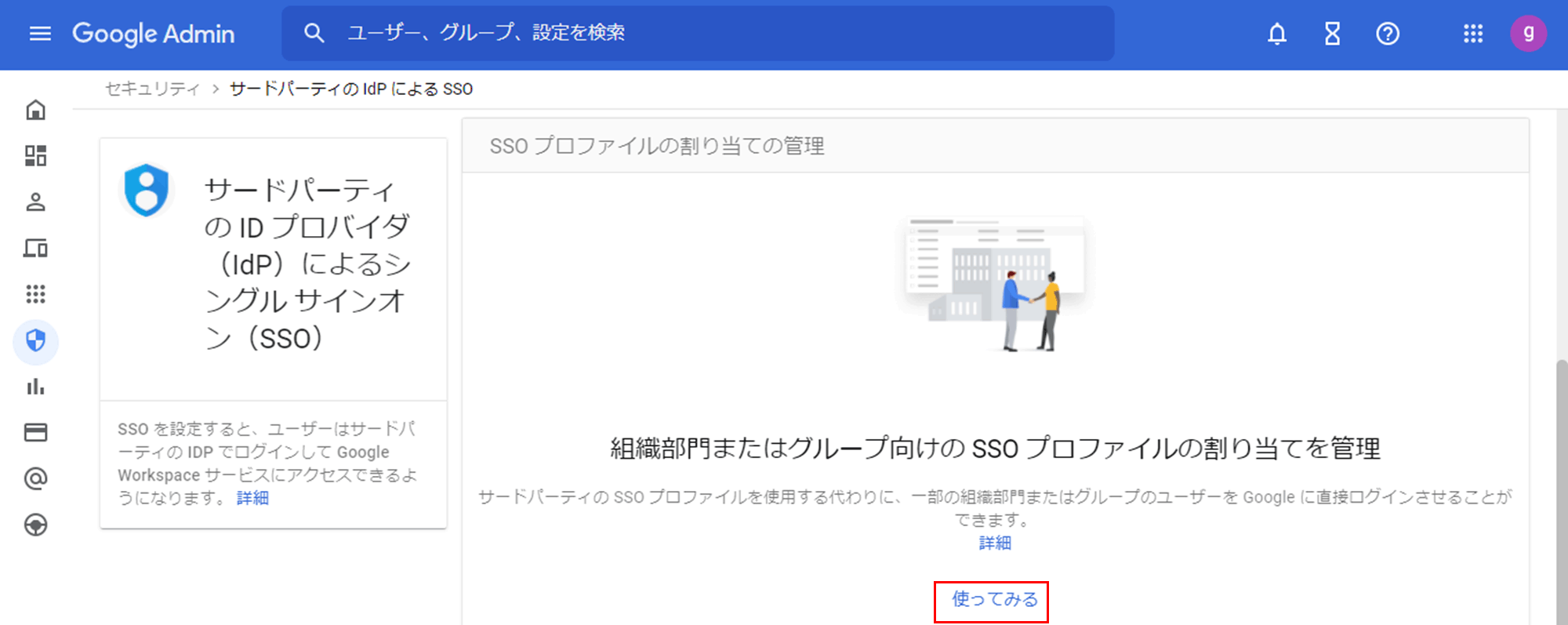
- Go to Security > Authentication > Single Sign-On (SSO) with 3rd Party Identity Provider (IdP)
- Under Manage SSO profile assignments, click Try it
* "Try it" is displayed only when SAML linkage setting is completed.
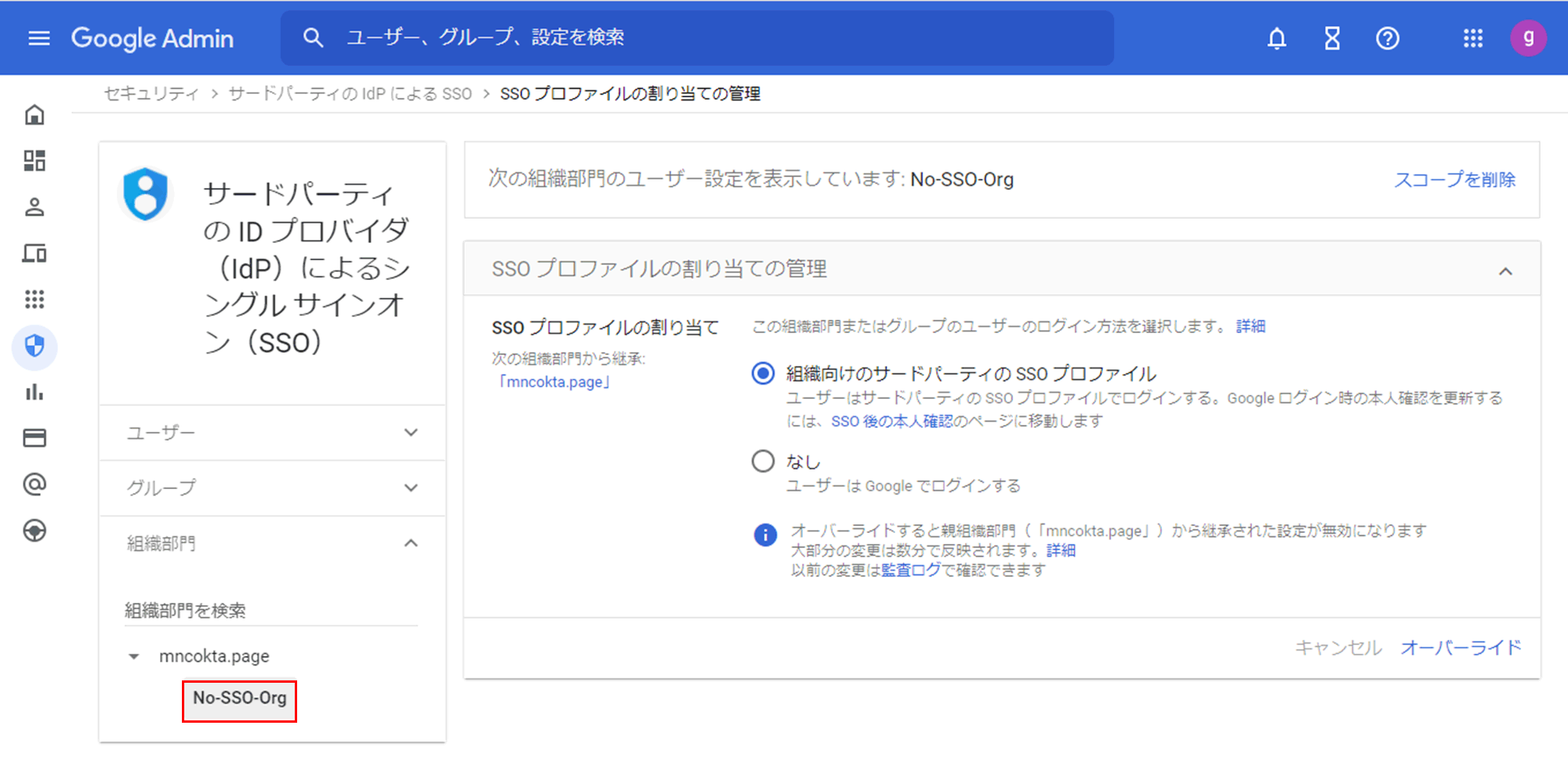
- Select the desired Organizational Unit or Group in the left pane
(Example: Set the organizational unit "No-SSO-Org")
(Example: Set the group "No-SSO-Group")
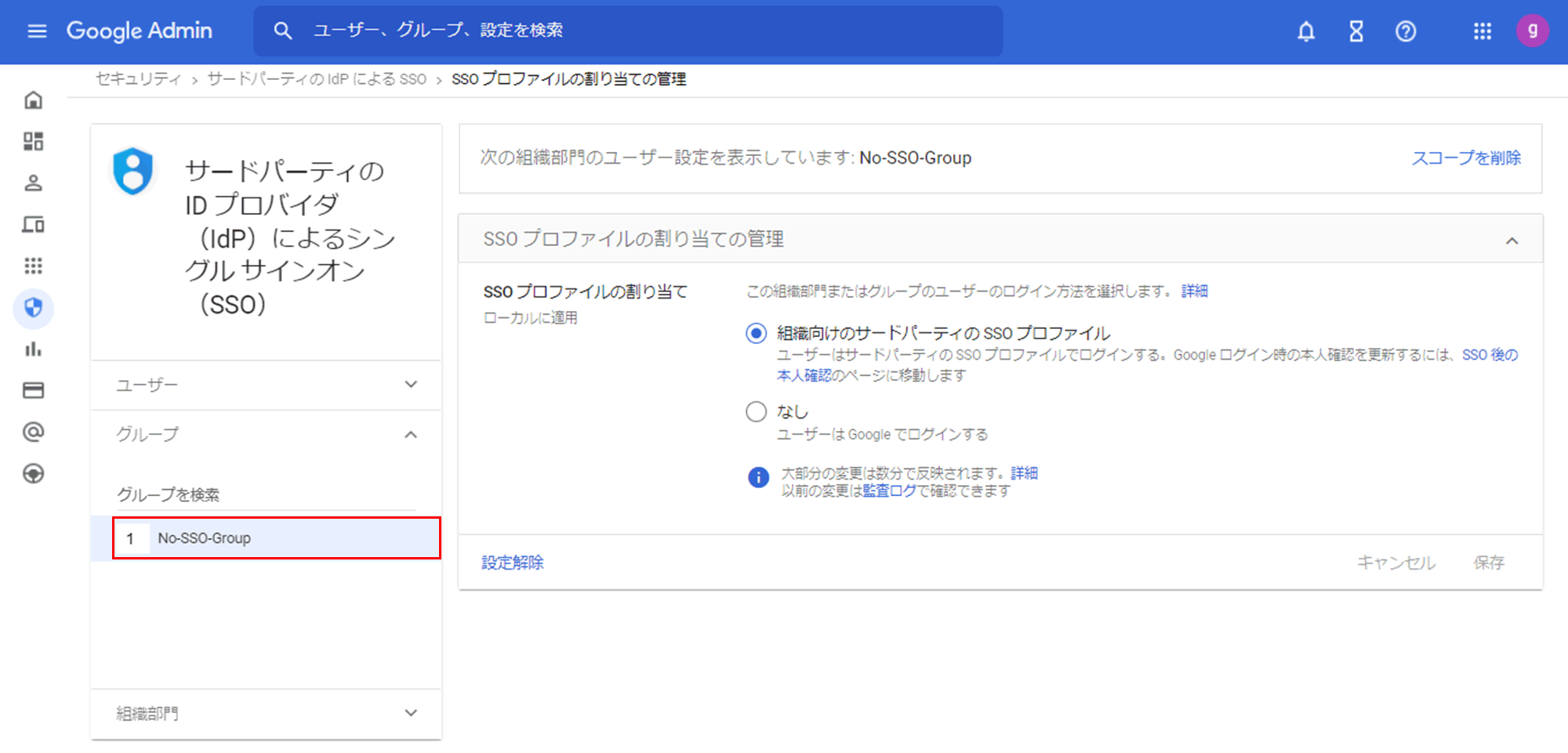
- Select None for Assign SSO Profile
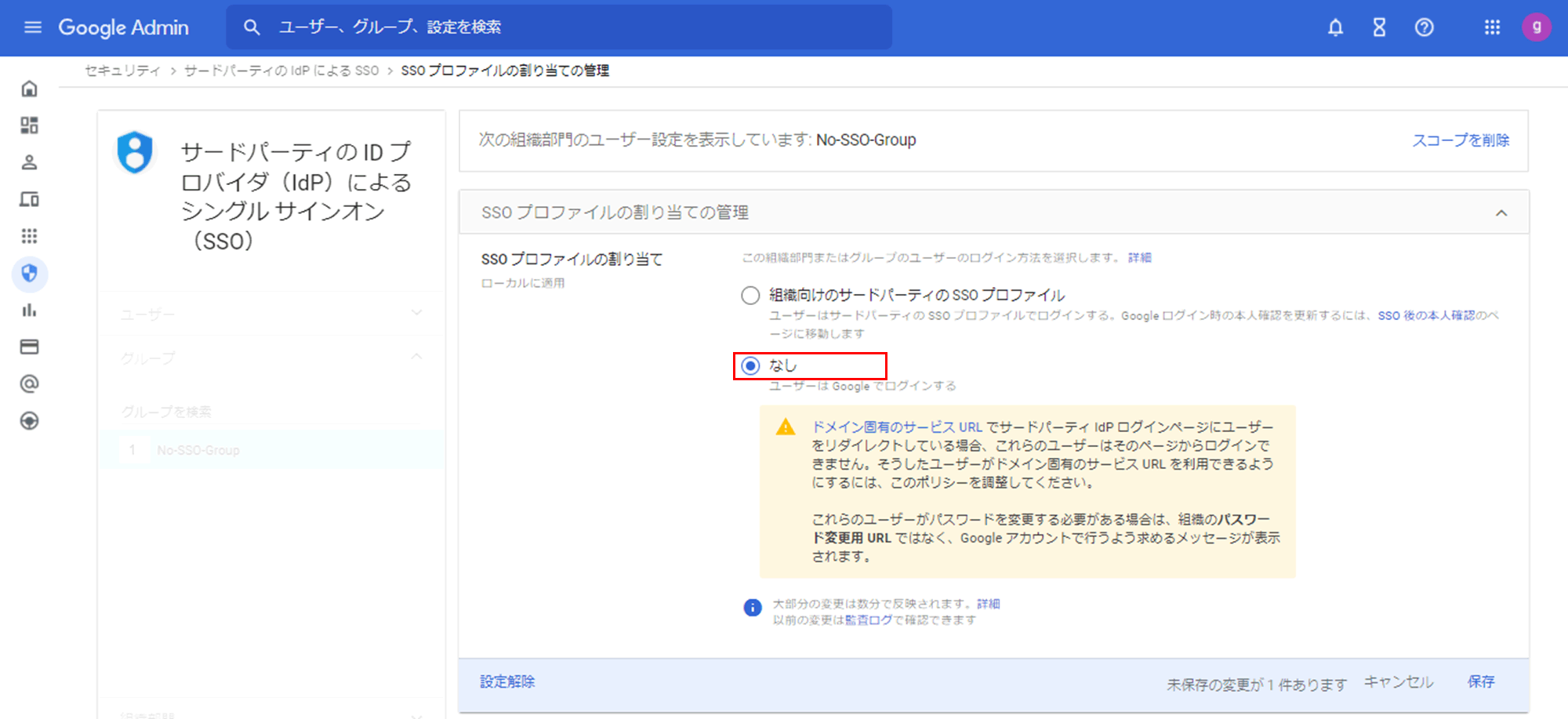
By performing the above settings, users belonging to the set organizational unit or group will be able to log in with their Google Workspace ID/password even if they are linked with Okta via SAML.
Also, if you have provisioned settings between Google Workspace and Okta, you can assign any user to organizational units and groups from Okta. The setting method for this is as follows.
*Please note that the provisioning function requires a Lifecycle Management (LCM) license.
<Okta side settings (group management)>
- Login to Okta admin screen
- Transition to Google Workspace setting screen
*Google Workspace and Okta are assumed to have completed SMAL/Provisioning linkage. - Move to the "Assign" tab and assign by user or group
- Select the corresponding organizational unit in "Organizational unit" of assignment details
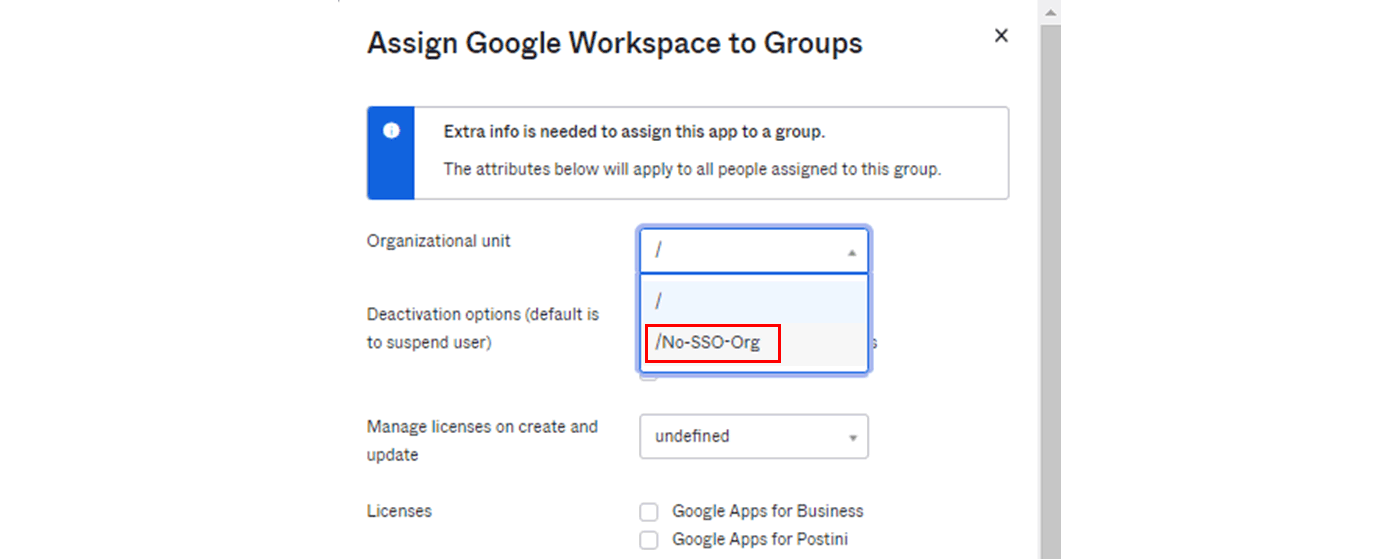
- Arbitrarily set other assignment contents and complete the assignment
With the above settings, you can assign an organizational unit to any user, and as a result, you will be able to log in directly to Google Workspace.
<Okta side settings (group management)>
- Login to Okta admin screen
- Create a group for linking to Google Workspace on the Okta side
*If the group names on the Okta side and the Google Workspace side are different, overwriting will occur on the Okta side, so it is recommended to create them with the same name. - Transition to Google Workspace setting screen
*Google Workspace and Okta are assumed to have completed SMAL/Provisioning linkage. - Go to the "Push Groups" tab and synchronize the groups on the Okta side and the Google Workspace side (Link Group)
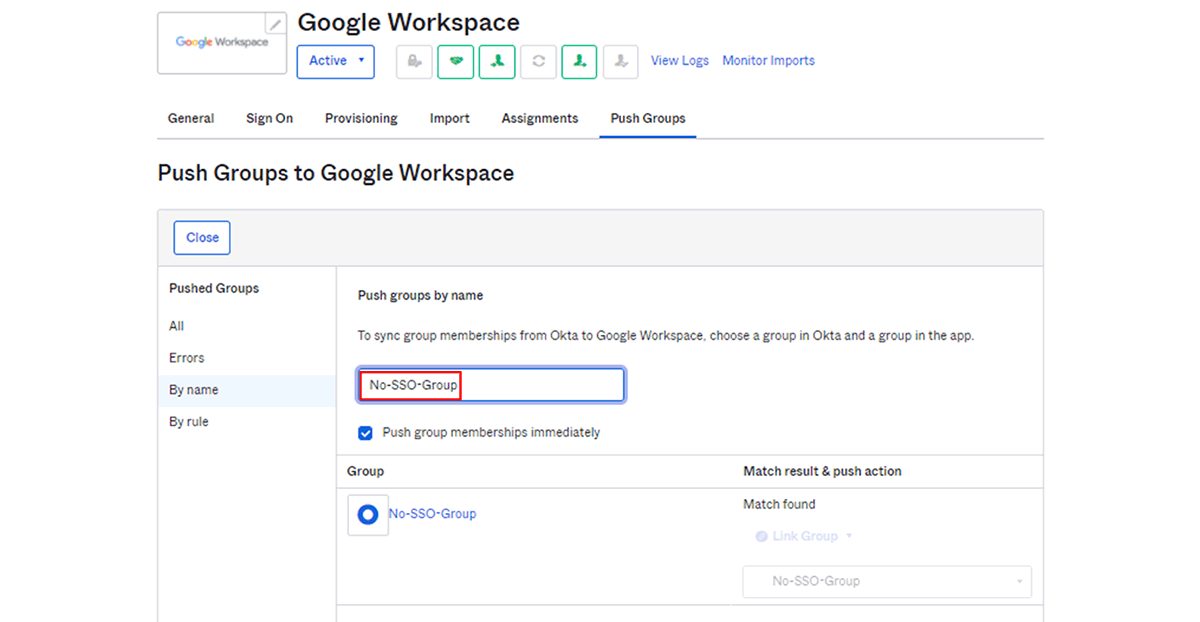
With the above settings, users who belong to the group created on the Okta side will belong to the synced group on the Google Workspace side, and as a result, they will be able to log in directly to Google Workspace.
Automation with Okta Workflows
With the above method, users who can directly log in with their Google Workspace ID/password can be managed on Okta. Furthermore, it is possible to change to logging in via Okta by excluding them from the group they belong to after completing their first login.
Although it is possible to manually exclude only the target user from the group to which it belongs, it takes man-hours to check whether the user has completed the first login and exclude only the completed user from the group. Also, if the number of target users is large, there is a concern that operational errors may occur. In fact, the operator will think that it is a simple work and it is a "troublesome" work.
This "tedious" work can be automated using the Okta Workflows feature. Okta Workflows automates a variety of processes without complex custom code and is GUI-based for easy setup.
*Please note that the Okta Workflows function can be used for free up to 5 flows, but more than that requires a Workflows (Light/Medium/Unlimited) license.
The flow for excluding users who have completed their first login to Okta (status is "Active") from the target group is as follows.
<Simplified diagram>
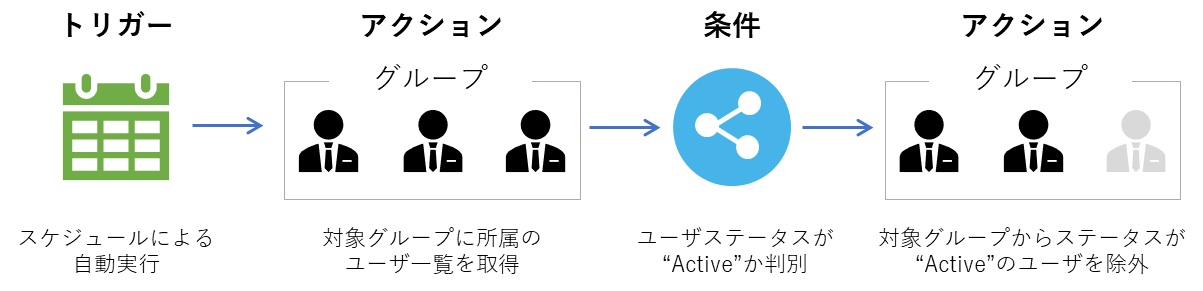
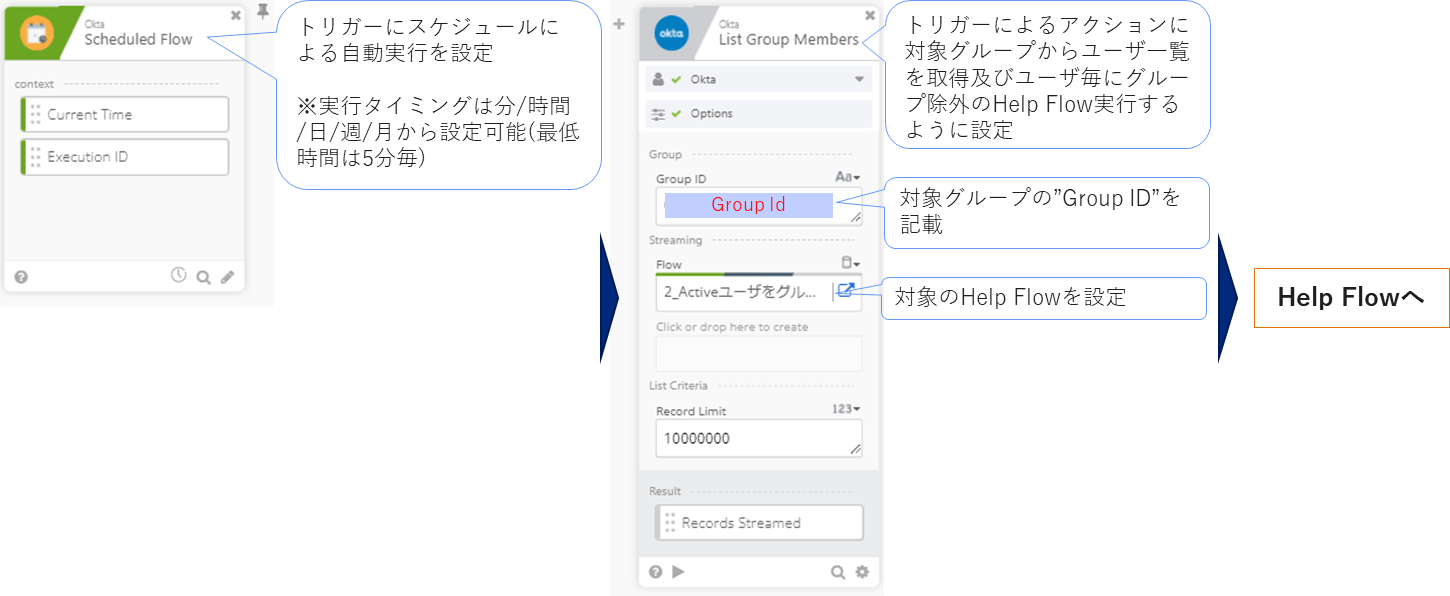
<Actual flow content>
Main flow
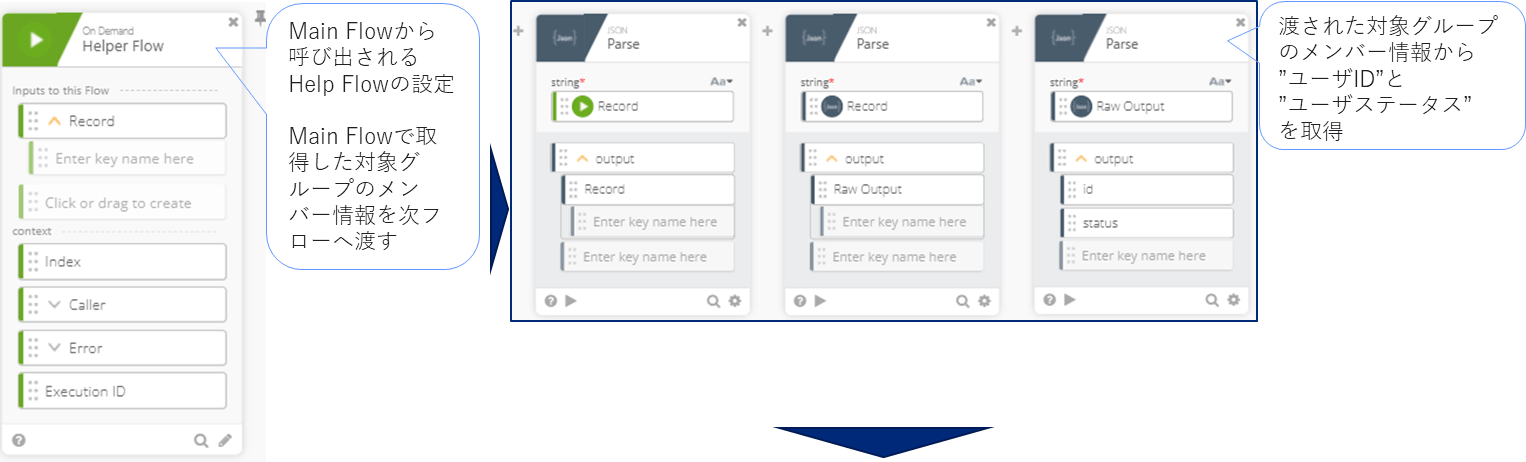
Help Flow
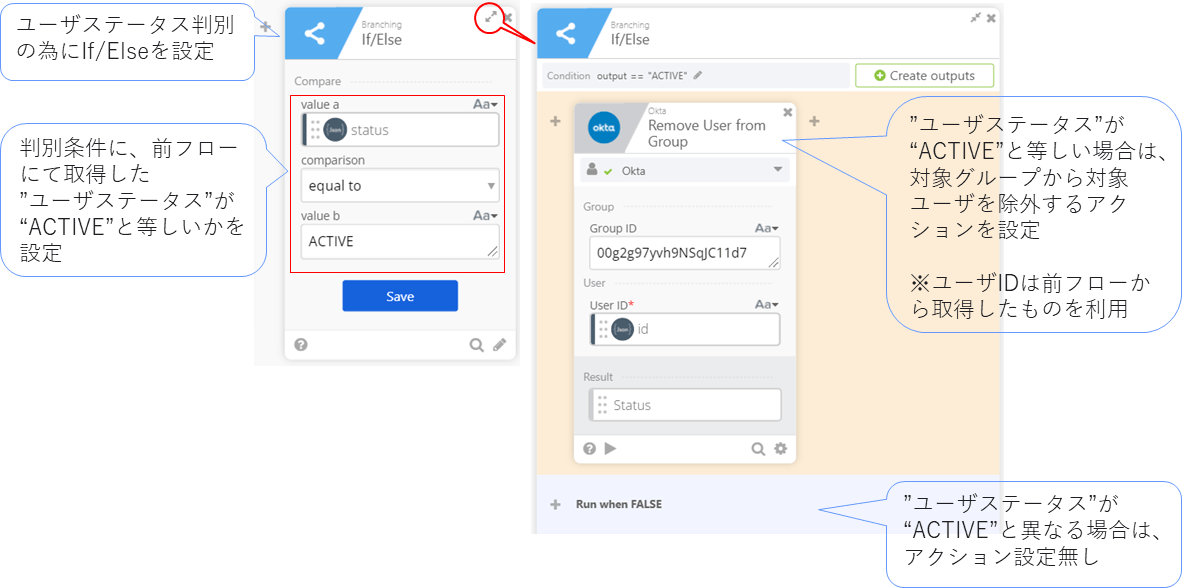
Summary
When Google Workspace and Okta are linked with SAML, only any user can log in directly with the ID / password on the Google Workspace side without going through Okta. , I introduced how to manage users in Okta and how to automate with the Okta Workflows feature.
Were the concerns about SAML integration between Google Workspace and Okta resolved?
In particular, we believe that automating with the Okta Workflows function will contribute to the reduction of operation man-hours and operational errors. What I introduced this time is one of the usage examples of Okta Workflows, but there are other functions that have the potential to solve various problems.
If you are interested in Okta and Google Workspace integration, integration with other SaaS, or Okta Workflows functionality, please contact Macnica.
Inquiry/Document request
In charge of Macnica Okta Co., Ltd.
- TEL:045-476-2010
- E-mail:okta@macnica.co.jp
Weekdays: 9:00-17:00

