
Okta
Octa
[No need for UEM/MDM] How to control access based on device requirements with Device Assurance
Understanding Device Management/Access Device Restrictions in Okta
Okta allows you to restrict which devices can access your application and require MFA authentication for non-managed devices.
In conventional Okta, UEM/MDM must be installed to manage devices, and it was not possible to check the security status of unmanaged devices.
However, by using the function "Device Assurance" updated in August, it is possible to specify the OS version of accessible devices without UEM / MDM, realizing secure use of unmanaged devices. .
What is Device Assurance?
Device Assurance allows you to set security requirements for devices accessing your applications. By specifying device security requirements, you can allow only secure device access, even if the device is unmanaged.
*If you are using an older version of Okta Verify, you may not be able to use Device Assurance.
See below for details.
https://help.okta.com/oie/en-us/Content/Topics/identity-engine/devices/device-assurance.htm
Device Assurance can be used for devices whose OS is “Android”, “iOS”, “macOS” and “Windows”. In addition to specifying the version, the following settings are available for each OS.
- Android
- Whether the screen lock is set
- Whether biometric authentication has been set for unlocking the screen
- Whether the disk is encrypted
- Whether it supports hardware backup key
- Not rooted or not
- iOS
- Whether a passcode has been set
- Whether you have enabled Touch ID or Face ID
- Whether the device is not jailbroken
- macOS
- Whether the password has been set
- Whether the disk is encrypted
- Whether it supports Secure Enclave
- Windows
- Whether the password has been set
- Whether Windows Hello is enabled
- Whether the disk is encrypted
- Whether you are using the Trusted Platform Module
How Device Assurance Works
In conventional device management using UEM/MDM, the security state of the device is managed by UEM/MDM, and access of the managed device is permitted by Okta.
On the other hand, when using Device Assurance, Okta Verify inside the device tells Okta the security status of the device, Okta itself determines whether the security status allows access to the device, and allows access. .
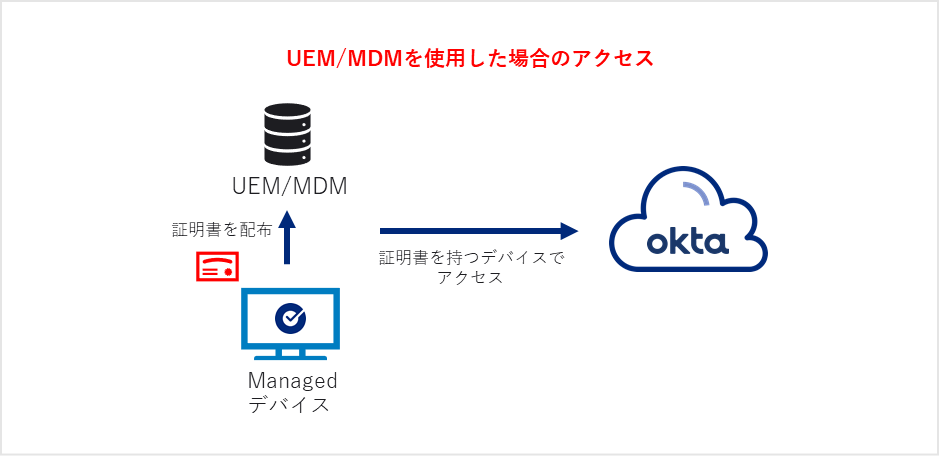
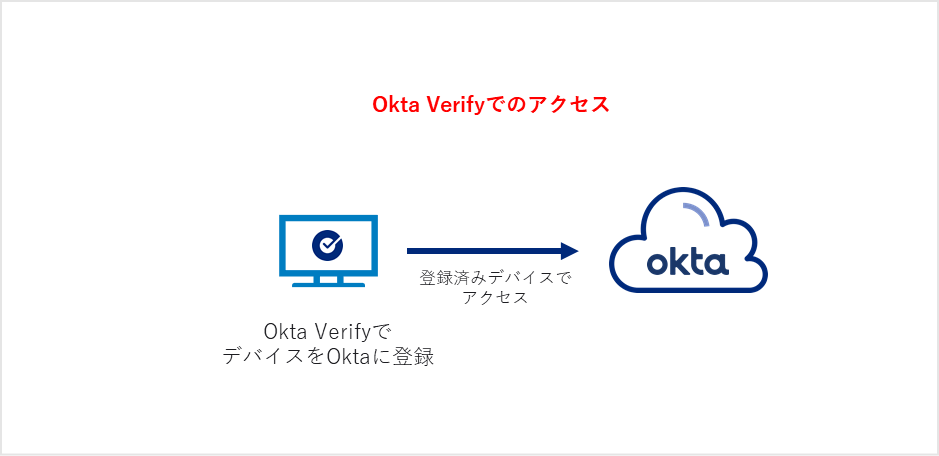
I used Device Assurance to limit access to Windows devices to version 11
Now let's actually implement access control using Device Assurance.
Setup steps
- Create Device Assurance Policy
Go to the Security > Device Assurance Policies page on the admin screen and create a Device Assurance Policy from the Add Policy button. Set the Device Assurance Policy as shown below.
*In the figure below, a Device Assurance Policy named "Windows 11" is created.
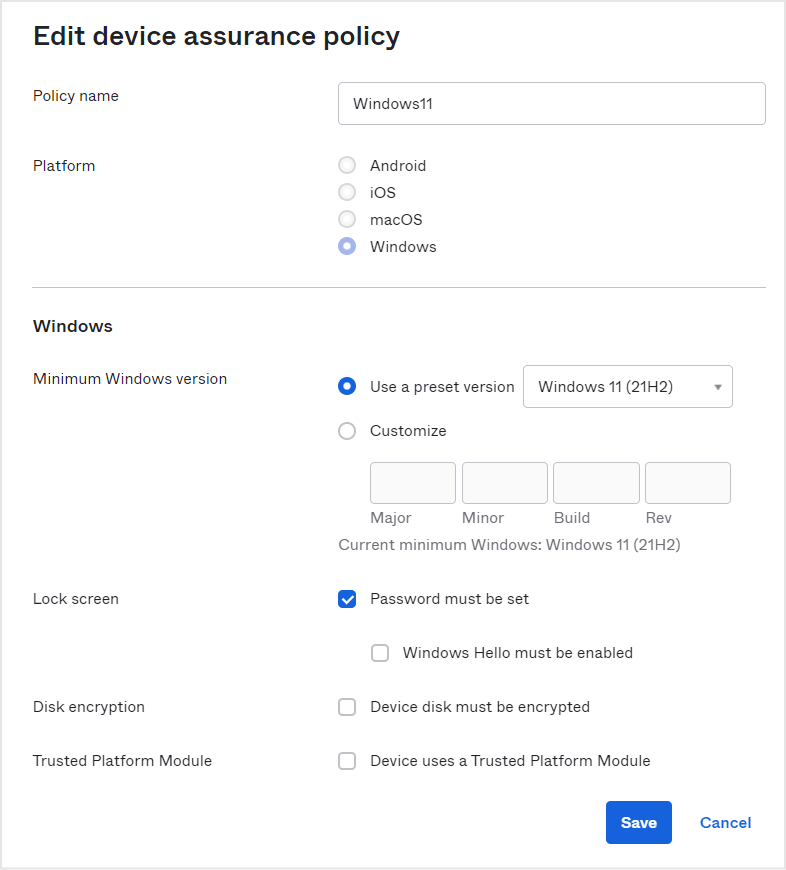
- Set to allow Windows 11 access
Go to the Security > Authentication policies page in your Shopify admin and select the application for which you want to configure access control.
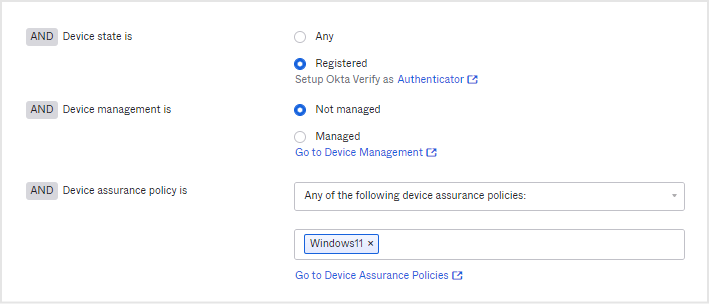
From Ad Rule, set to allow Windows 11 device access, and click the Save button to save. At this time, it is necessary to set the following three items as shown in the figure below.
- Device state is : Registered
- Device management is : Not managed
- Device policy assurance is : Select the policy created in step 1 ("Windows 11" in the figure below)
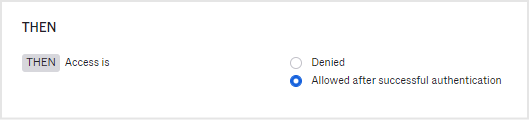
- Access is : Allowed after successful authentication
- Set to deny access other than Windows 11
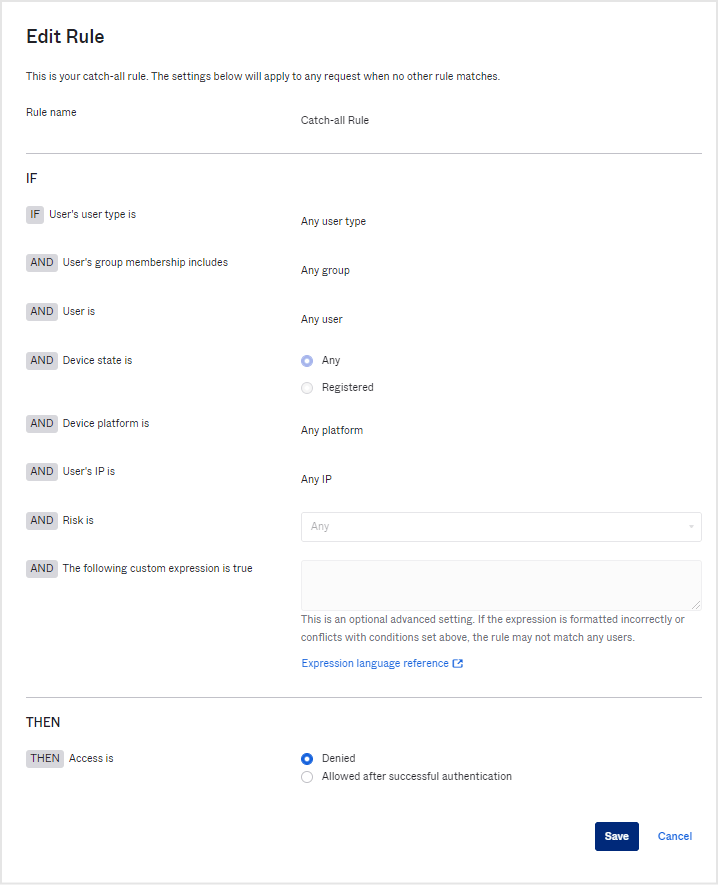
Click Actions > Edit of Catch-all Rule in the application policy for access control. Set “Access is” to “Denied” as shown below and click Save to save.
motion
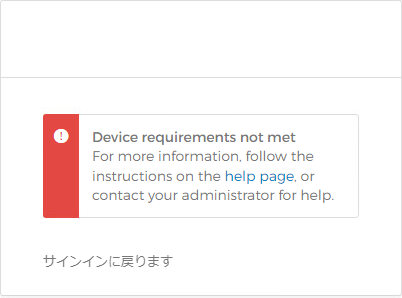
If you actually access it as a Windows 10 user who has registered for OktaFast Pass in advance, you will see an error screen as shown below. You can see that access is denied because it is not Windows 11 and access control is successful.
Summary
This time, we introduced Okta's function "Device Assurance" that restricts devices that can be accessed without using UEM/MDM.
Since it is a very easy-to-use function, I think it will attract attention from companies that have not introduced UEM/MDM.
If you are a company that has not introduced UEM/MDM and thought that it would be difficult to control access based on device requirements, why not give it a try?
Inquiry/Document request
In charge of Macnica Okta Co., Ltd.
- TEL:045-476-2010
- E-mail:okta@macnica.co.jp
Weekdays: 9:00-17:00

