
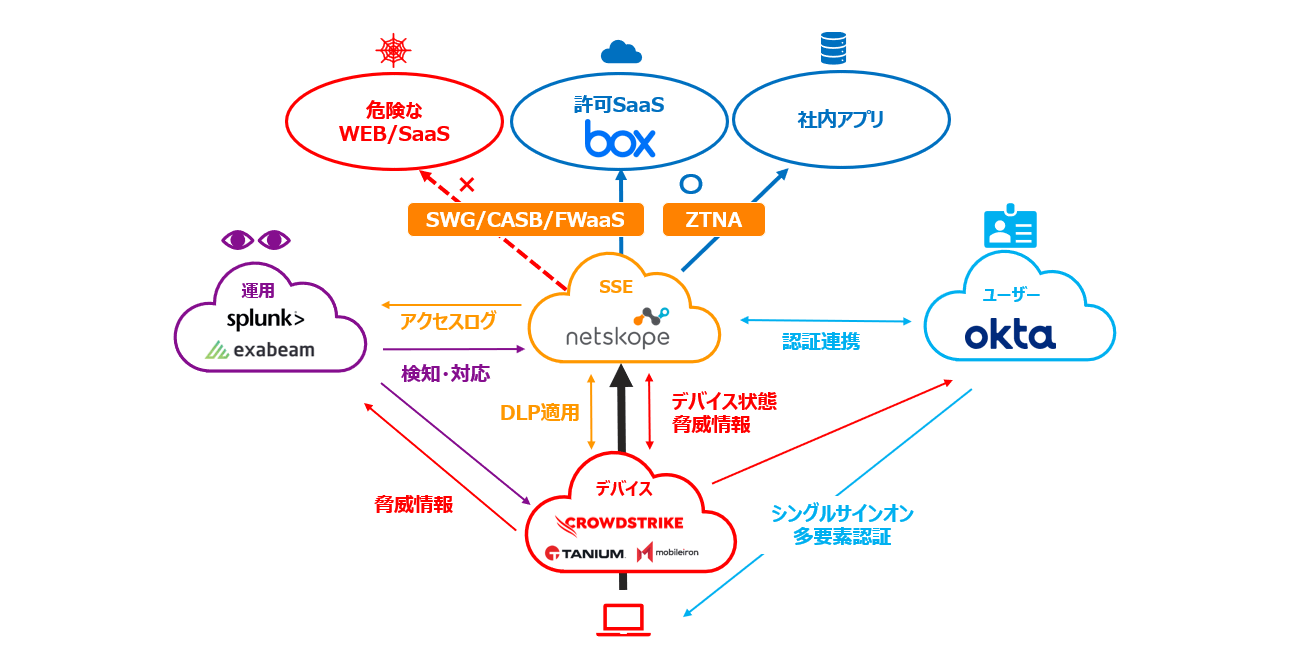
Netskope
netscope
Realization of multi-vendor zero trust
- Netskope has formed alliances with numerous vendors to form an open ecosystem.
- In particular, the vendors introduced below are mutually linked at the API level, and various automation is possible.
- In order to realize Zero Trust, it is essential to cooperate with solutions such as IDaaS, EDR, etc., in addition to SSE.
- Netskope becomes the hub for Zero Trust enablement, allowing all solutions to be loosely coupled
- It is possible to prevent lock-in by a single vendor and achieve multi-vendor Zero Trust.
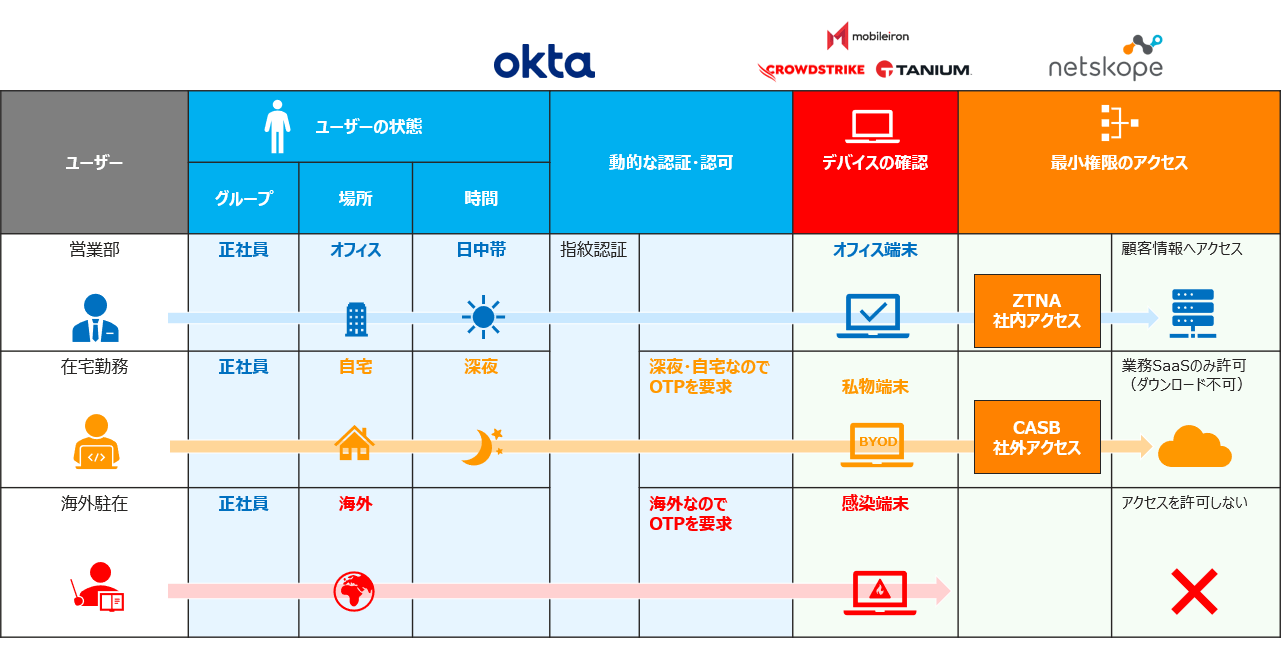
Zero trust access based on user/device
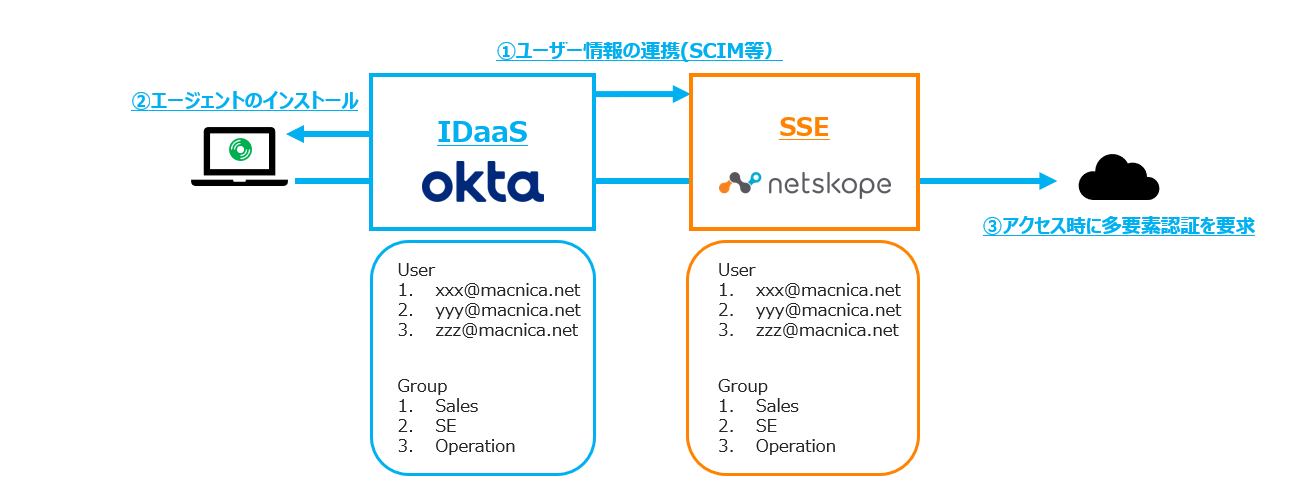
IDaaS integration: synchronization of user information
- User/group information can be synchronized by linking with IDaaS such as Okta
- Agent installation on terminals can also be simplified by linking with IDaaS
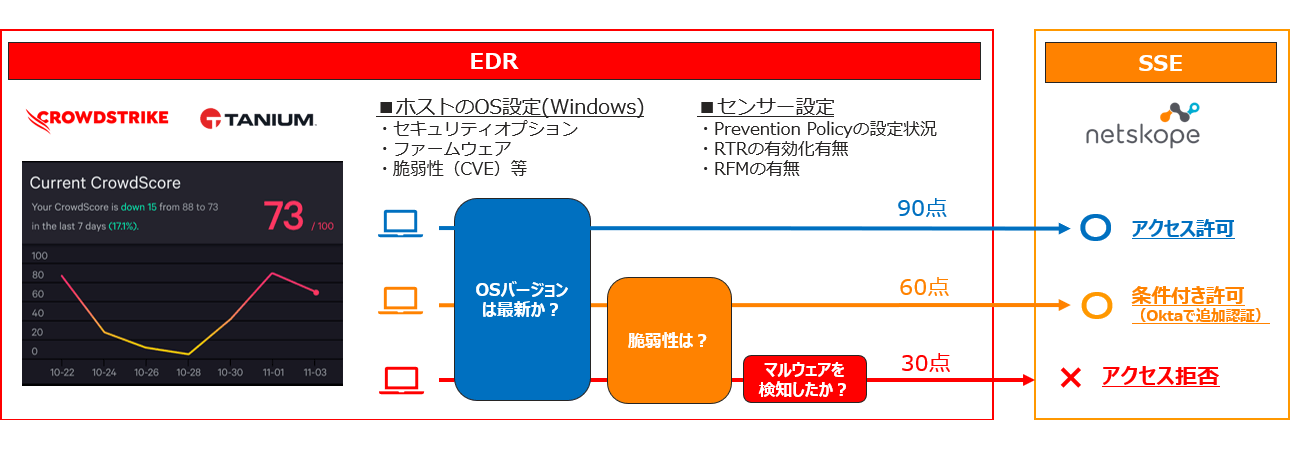
EDR linkage: access according to device threats and risks
- Even if it is a company-provided device, it is not necessarily a safe device (static device checks are insufficient)
- CrowdStrike calculates real-time device scores and shares device threat scores with Netskope via API
- Realize adaptive control according to threat score on Netskope side
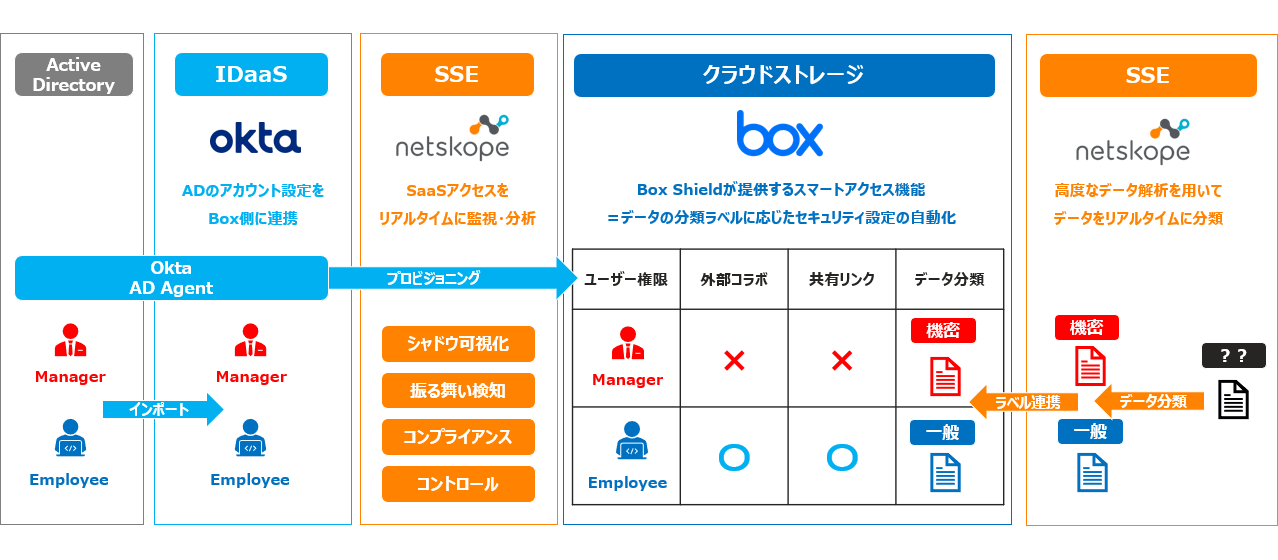
BOX linkage: Access control based on data importance
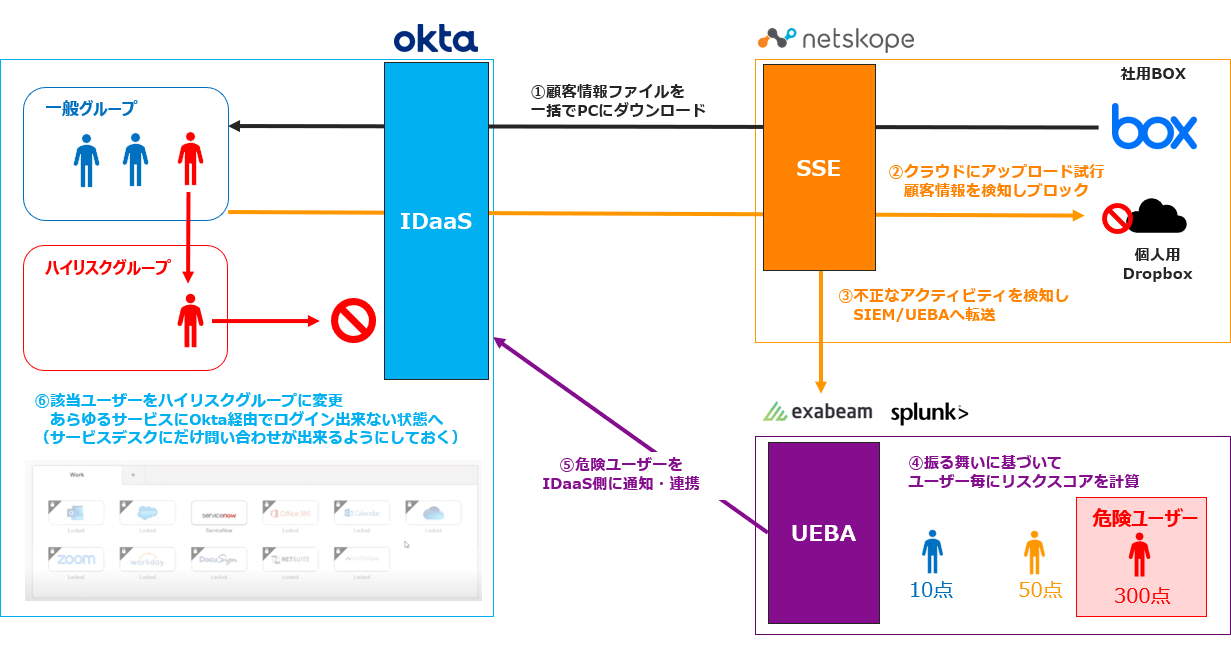
UEBA integration: detection and integration of unauthorized activities
Inquiry/Document request
In charge of Macnica Netskope Co., Ltd.
- TEL:045-476-2010
- E-mail:netskope-info@macnica.co.jp
Weekdays: 9:00-17:00