product
- Menlo Security Secure Internet (Web isolation)
- Menlo Security Secure Office 365/Secure G Suite (Email isolation)
- Menlo Security Global Cloud Proxy
- Menlo Security Insights
- CASBs
- DLP
- Mobile Isolation
- Secure Application Access (formerly: MPA)
- HEAT Shield
- SSE
- Secure Enterprise Browser
- VOTIRO File Sanitization Solution
Specifications/Technical Information

Menlo Security
Menlo Security
Information Security Strategy Seminar -Forefront of Security Measures in the New Normal Era-

In order to respond to changes in the business environment and the rapid increase in telework due to COVID-19, there is an urgent need to shift from perimeter defense such as firewalls and VPNs to Zero Trust, which monitors and verifies access from all directions. A new approach to endpoint protection, "isolation," is attracting attention as an essential solution for realizing this. In this presentation, an outline of isolation and its merits were explained.

Macnica Networks Corp.
Manager, 3rd Section, 1st Technology Department, 1st Technology Management Department
Mr. Naohiro Uemura

Menlo Security Japan Co., Ltd.
Senior System Engineer Manager
Mr. Daichi Terada
New Security Approach "Isolation"
"Zero trust" is attracting attention as a new security concept that corresponds to the way of working in the new normal and IT tools.
Mr. Naohiro Uemura of Macnica networks said that the four elements necessary for Zero Trust are ``realization of authentication and authorization'', ``monitoring of device safety'', ``zero trust access permission'', and ``operational transformation in the era of zero trust''. List one.
“Among them, what is attracting particular attention due to the spread of telework is zero trust access permissions for SaaS and the web. , From now on, we will change to the form of granting least privileged access regardless of internal or external routes." (Mr. Uemura)
Why is traditional threat detection-based security failing to achieve zero trust permissions? There are three main reasons for this.
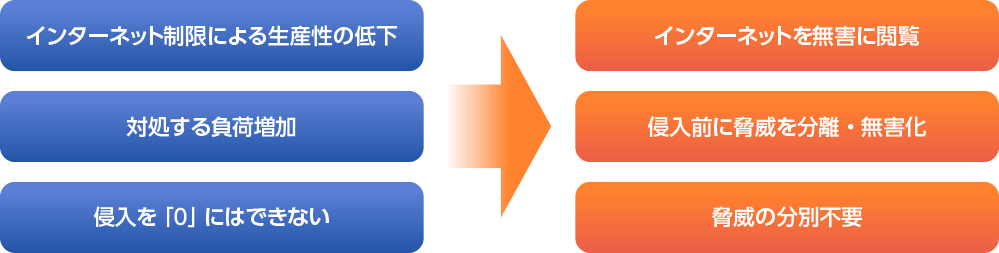
"The first is 'decreased productivity due to Internet restrictions.' Access restrictions by URL filtering often block sites that are necessary for work, which inevitably leads to a decrease in user productivity.
The second is "increase in security operation load to deal with". New detection methods such as Box and machine learning have been appearing one after another, but of course, the number of detection alerts has increased accordingly, increasing the load on security operations.
The third is that "intrusion cannot be reduced to zero". Even if a new detection method comes out, a new attack method that evades it will soon emerge. As a result, no matter how many countermeasures are taken, it is virtually impossible to eliminate intrusions.” (Mr. Uemura)
One of the limitations of detection methods is "zero-day attacks," which exploit the time lag between the day a security hole is discovered and the day a countermeasure is established to eliminate the vulnerability. Security vulnerabilities can be addressed by applying security patches from vendors, but zero-day periods will inevitably occur. In some cases, released patches are not applied immediately to ensure that there is no impact on running applications.
Also, no good or bad detection method is 100% accurate in identifying zero-day attacks or new methods. As a result, mistakes will inevitably occur, erroneous detections and oversights will not disappear, and the load will increase.
“Isolation (separation and detoxification), which is a completely new security approach, is attracting attention. It is done separately from the network, and only completely safe things are sent inside the corporate network.” (Mr. Uemura)
Prevent Malware Threats with Isolation Technology
Menlo Security is highly rated for this isolation technology. Founded in the United States in 2013, the company's solutions have also been adopted by the US Defense Information Systems Agency (DISA), which provides IT and communications services to the US Department of Defense.
Then, what kind of mechanism is the new security "isolation"? Mr. Daichi Terada of Menlo Security Japan explains this as follows.
"Isolation involves downloading and executing any content in an environment separate from the endpoint. This environment is typically assigned to each user as a container. At the endpoint, external content is Since nothing is executed, no malware infection can occur.In addition, only safe rendering information, keyboard and mouse input can be exchanged with the endpoint, so even if the container is compromised, other information can be transmitted to the endpoint. will never reach ”.
When the user ends the session, the entire container is deleted, so a clean environment is always maintained. No special software needs to be installed on the endpoint, and users can continue to use their familiar browsers and applications. Therefore, it does not impair user operability and productivity.
“Menlo Security utilizes this isolation technology to provide services globally. Currently, more than 90% of security breaches are said to occur via the web and email. We provide solutions aimed at preventing these three threats." (Mr. Terada)
Eliminate web and email threats
First, "Web Isolation" is used to counter threats via the Web.
Web isolation eliminates web-based threats by separating website browsing and file download/execution processing from the website from the endpoint. All content is downloaded and executed in containers on the cloud, and only safe rendering information reaches the endpoint.
“Websites are made up of various types of content, and active content, such as JavaScript, that is executed at endpoints causes malware infections. However, it is not uncommon for websites that are generally trusted to contain malicious active content.By utilizing web isolation, such threats can be prevented.” (Mr. Terada)
Threats hidden in document files can also be completely eliminated. For example, if you download a Word file from a website, the original file will run in a container in the cloud and the user will see its contents in your browser, not in Word. It can also be downloaded locally in a threat-free format, and supports more than 30 file formats such as Excel, PowerPoint, and PDF.
Another way to prevent threats via email is "Email isolation".
Email isolation when you open an attached file or click on a URL link in an email that has been sent, the content is converted so that it is downloaded and executed in a container. sent to the user. The files are wrapped in HTML and are viewed by users using a web browser. Even password-protected files can be viewed safely.
If you need to edit the file, you can download it after security checks, including Box. However, since the original file is not zero risk, it is possible to prohibit this download.
“Unlike existing security measures, isolation does not detect detection.Therefore, we no longer have to worry about a large number of alerts and requests from users, which greatly reduces the burden and cost of security operations. Since content can always be browsed in a safe state, there is no need for excessive access restrictions, and user productivity can be improved,” says Mr. Terada. It will be an effective option for organizations that are considering building an access environment that does not impair the safety and convenience of telework.
The idea of isolation
既存のWebセキュリティ対策は、様々な制限や負荷の増大を招き、思ったほどの効果を上げることが難しい。これに対しアイソレーションは、侵入前に脅威を分離・無害化するため、現場の負担とコストを大幅に軽減できる
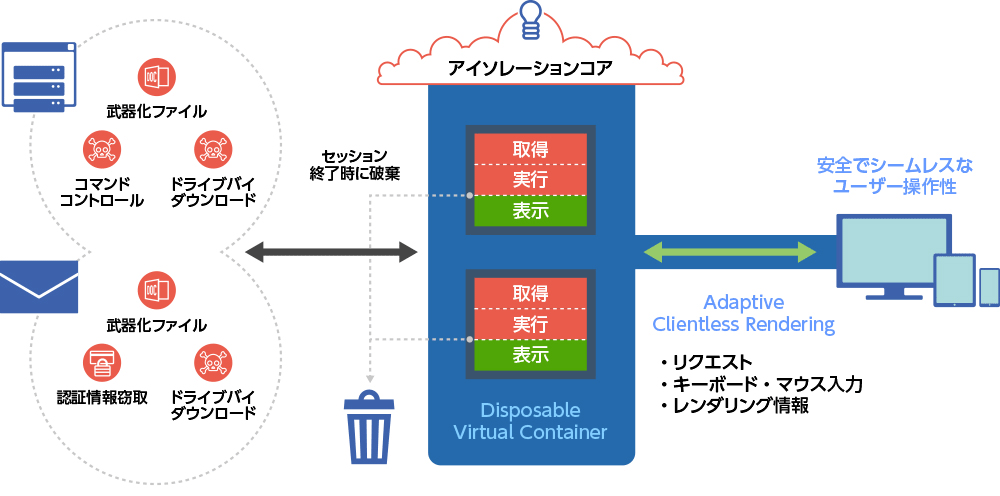
Detection Independent Isolation Technology
Instead of detecting whether the access is good or bad, Menlo Security implements a mechanism that prevents the device from being directly damaged by isolating the access via the web or email from the device. is doing
Inquiry/Document request
In charge of Macnica Menlo Security
- TEL:045-476-2010
- E-mail:menlo-sales@macnica.co.jp
Weekdays: 9:00-17:00
