product
- Menlo Security Secure Internet (Web isolation)
- Menlo Security Secure Office 365/Secure G Suite (Email isolation)
- Menlo Security Global Cloud Proxy
- Menlo Security Insights
- CASBs
- DLP
- Mobile Isolation
- Secure Application Access (formerly: MPA)
- HEAT Shield
- SSE
- Secure Enterprise Browser
- VOTIRO File Sanitization Solution
Specifications/Technical Information

Menlo Security
Menlo Security
Cyber security turbulent era What is the power of "Email isolation" that should be noted now?

On February 6th, Macnica hosted a Menlo Security seminar titled ``Mail isolation, the next Email isolation of the expanding web separation, arrives in Japan for the first time - Don't miss the security standards of the new era!!''. As cyber attacks have become more sophisticated and diverse in recent years, many people are interested in countermeasures against cyber attacks. The venue, which has a capacity of 200 people, was almost full with many visitors, and the event ended on a high note. Below is an overview of the seminar.
What the 2018 figures reveal about how an organization should survive in turbulent times
The keynote speaker was Mr. Yoichi Shinoda, Distinguished Professor at the Information Society Infrastructure Research Center, Japan Advanced Institute of Science and Technology, who has held important posts related to information security in various organizations, including Assistant to the Cabinet Cyber Security Center. Under the title of "Towards an era of turbulence in cybersecurity," he talked about the points that organizations should focus on in cybersecurity in the future, including recent topics on cyberattacks.
The talk introduced several “numbers” that symbolize cybersecurity in 2018. For example, "29 million cases", this is the number of personal information in the information leakage case released by Facebook in September. Recently, cryptocurrency theft has also been viewed as a problem, and its US dollar equivalent was "$1.1 billion" in the first half of 2018 alone. WannaCry's total ransom is said to have reached "$4 billion".
Also, in terms of the figures for 2017, the number of incidents related to IoT devices increased "10 times" compared to the previous year. And the last thing I introduced is the number "45%". This is the percentage of Japanese who practice "do not open suspicious email attachments/do not click on suspicious URLs". Conversely, it can be said that 55% of people open suspicious email attachments or URLs.
These numbers suggest some important points in organizational cybersecurity. First of all, cyber security requires a correct attitude as an organization. However, there are many cases where there is a difference in enthusiasm due to differences in departments within the organization, and there are many cases where the organizational structure is characterized by the lack of governance for cyber security. There is also concern about the risk of hardware interdiction through the IT supply chain, which has become a black Box. Cryptocurrencies are a quick source of income for cybercriminals, and ransomware is already a common tool.
The final bastion, humans, is an eternal vulnerability. There are three possible countermeasures against this vulnerability: appropriate knowledge, appropriate training, and system assistance. As threats are changing from systems to people, it is necessary to properly assess the impact on organizations and respond accordingly.

A revolutionary way to clean malware from the web and email
The next speaker was Mr. Gautam Alteker, co-founder and chief architect of Menlo Security. He explained the origin, technological features, roadmap, etc. of Menlo Security's security solutions. Menlo Security's solution focuses on "system assistance", which was mentioned in the keynote speech as a countermeasure against human vulnerability.
The project, which began at the University of California, Berkeley in 2011, took a completely different perspective from the detection techniques used by previous security products. The project has also applied for a US patent for establishing a technology that ensures security even if everyone in the company is not a security professional. Menlo Security was established in 2013 to bring out the results developed in this project. Our first customer was JPMorgan Chase in 2014.
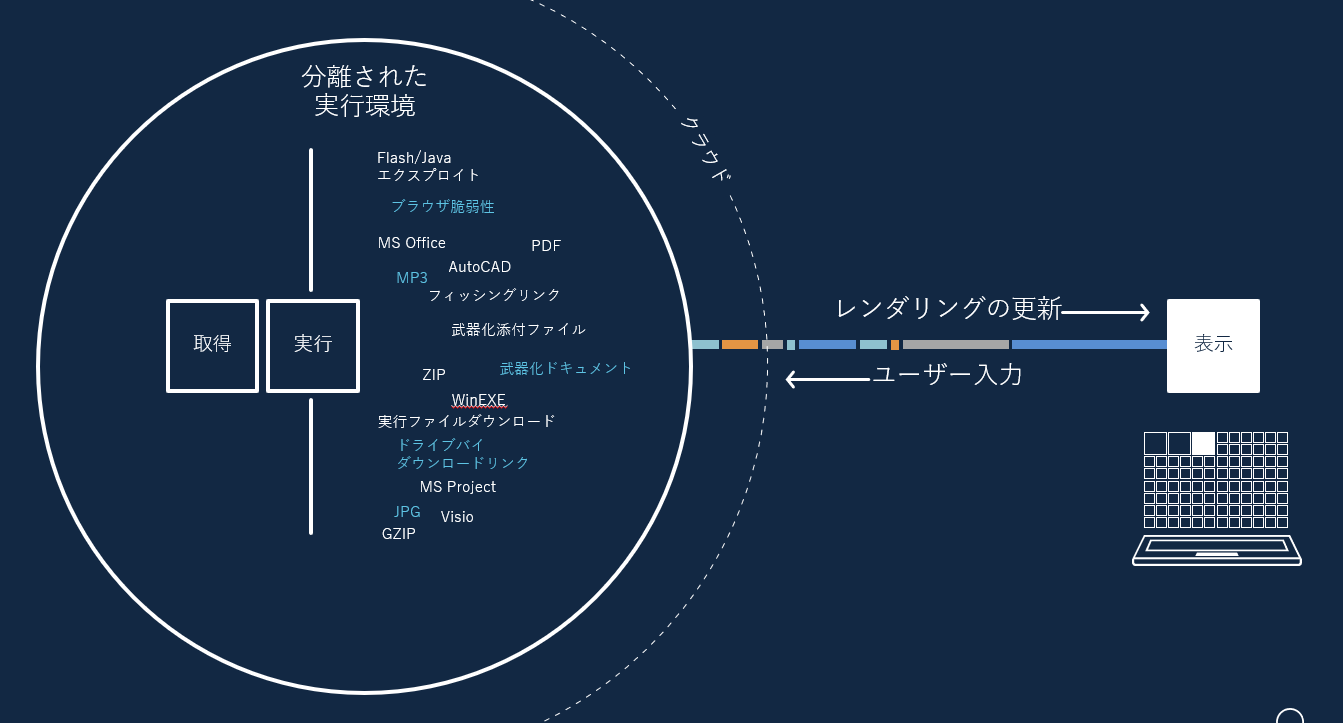
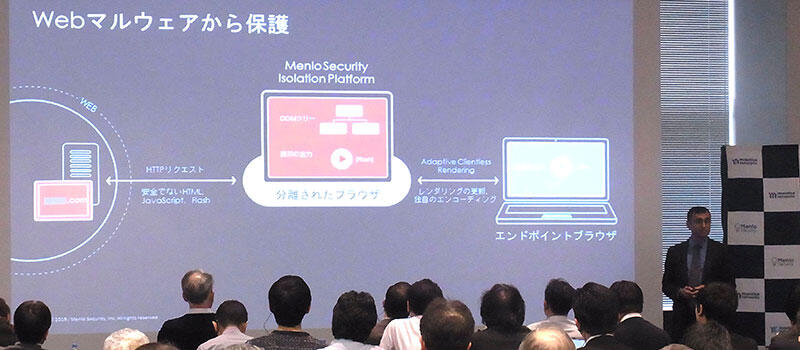
Antivirus, Box, content filtering, and other detection-reliant technologies have been widely used for years, but they are no longer able to completely prevent threats. In response to this current situation, Menlo Security's technology was conceived from the perspective of fundamentally reconsidering the method of preventing malware from the web and email. This is a new approach called "isolation". We set up an execution environment on the cloud that is completely separated from the endpoint, open all the content there, and then transfer only the rendering information to the endpoint. User input is also forwarded to the execution environment on the cloud and processed there. In other words, Menlo Security's solution provides complete isolation for all traffic and all devices, unlike security that relies on detection technology that only blocks "threats it sees."
Overview of Menlo Security's Isolation Technology
The technology is applied to three use cases: protection against web malware, protection from malicious URLs in emails, and protection from similarly malicious email attachments and web documents. You can use your existing browser without installing any software on your endpoints, just configure Menlo Security as a proxy on your endpoints to protect the web. Proxies and mail gateways also work with existing ones.
About 8 years after development, it is now used by many users, and the Company cloud platform handles 8 billion HTTP requests per month, but there are still no infections, and the service uptime of the cloud platform over the past 5 years is 99.99%. This is an achievement. In addition, we use a patented technology that transfers rendering information from the Company cloud and deploys it on the endpoint side. Compared to pixel-based transfers, network bandwidth can be utilized 10 times, and operation such as scrolling and copy and paste is the same as native operation.
New Countermeasures against Phishing and Targeted Attacks What is Email isolation?
In the presentation from Menlo Security, another solution architect, Mr. Daichi Terada, took the podium and introduced Email isolation a new solution that is now available in Japan. Threats from e-mail include “credential theft,” “drive-by downloads,” and “weaponized files,” and more than 90% of security incidents and attacks are triggered by e-mail. .

As pointed out in the keynote speech, 55% of Japanese people are likely to open suspicious email attachments and URLs, creating a headache for cybersecurity personnel in organizations. Menlo Security's answer to this challenge is Email isolation. In order to evade detection, attackers craft URLs in the text, use legitimate hosting services and URL categories, and even attack with attachments by exploiting logic flaws (Logic Flaws) without using scripts. ), etc., and cannot be completely prevented by existing security based on detection technology. It is believed that no matter how many layers of defense are built, only about 90% of threats can be blocked with detection technology, meaning that about 10% of threats cannot be prevented from intruding.
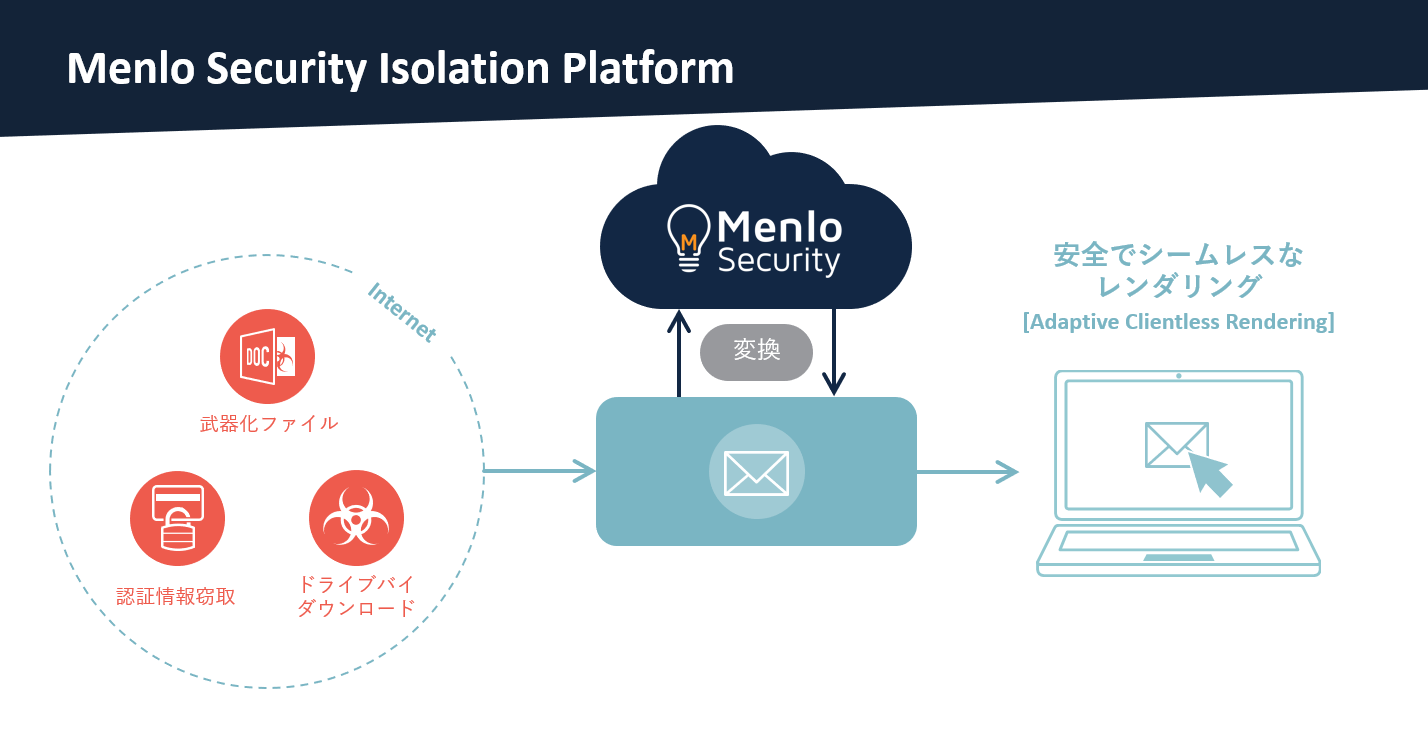
In response to this situation, Menlo Security offers "Menlo Security Email Phishing Links & Attachment Files", which applies the same isolation technology as the web to emails, and has started offering it in Japan. The basic idea is the same as web isolation, where URLs and attachments in the text are acquired and executed in an isolated environment on the Company cloud platform, and only rendering information is transferred to the endpoint. .
Overview of Menlo Security Email Phishing Links & Attachment Files
Let's take a closer look at how it works and how it works. First, when using it, set it so that all emails are received in your Box via the Company cloud infrastructure. All URLs in emails are rewritten on this cloud, and isolation is always applied when users access the links. This prevents malware intrusion through drive-by downloads. In addition, if the access destination is a phishing site that attempts to steal credentials, protection based on URL risk score using unique intelligence is applied. It is possible to configure settings such as blocking access according to the threat level, displaying read-only, and displaying a message on the endpoint.
Weaponized file threats are protected by encoding the attachment, wrapping it in an HTML file, and re-attaching it to the email. By wrapping in HTML, isolation is applied even when viewing attachments. Files opened in this way can be converted to a secure PDF and downloaded, or the original can be downloaded after parsing. Even if a compressed file is sent by sending a password separately, it can be processed without problems because the user can manually enter the password.
Compared to security that relies on conventional detection technology, email isolation can significantly reduce hidden costs such as false detection of malware, containment response, help desk, and PC reconstruction when infected.
The case of Sembcorp Industries, a Singaporean infrastructure company that operates around the world
Mr. Andy NEO from Sembcorp Industries in Singapore gave a presentation as a user company of Menlo Security. Sembcorp is engaged in energy business such as gas and electric power, as well as ocean development and urban development, and is expanding its business in 15 countries on five continents, mainly in Southeast Asia, including Australia and South America. With over a decade of cybersecurity hands-on experience, Mr. NEO is tasked with protecting this global enterprise against threats.

Sembcorp deploys Menlo Security web isolation and Email isolation. Cyber security is an important issue for the company, as it has a large social responsibility just because it is engaged in infrastructure projects such as energy and cities. Mr. NEO said that 94% of malware is transmitted via email, so email security is extremely important. It's the biggest vulnerability," he said. In response to this major vulnerability, they focused on Email isolation as a technology that can protect against threats even after emails have been delivered. That's how they installed Menlo Security's email security solution.
Mr. NEO mentioned that Menlo Security is a market leader, that it is a solution that does not depend on a specific vendor, that it can be quickly deployed company-wide because it is a cloud service, and that it can receive local support in each country where it does business. rice field. In response to a PoC request from Sembcorp, Menlo Security presented a perfect implementation plan, selected pilot users who hold the key to the project, defined requirements, communicated with users, transferred knowledge to Sembcorp, and provided a knowledge base. It gave me, NEO explains.
Mr. NEO listed the following points as the benefits of introducing Menlo Security's email security solution.
- Useful for evaluating the safety and reliability of URLs
- Automatically block malicious websites
- Protect or warn entering credentials to risky websites
- Separate all URLs in all emails
- Acts as the last line of defense for cybersecurity
In addition, as a position in charge of company-wide cybersecurity, he also mentions the fact that he can always grasp the latest information on threats to his company from the executive dashboard as an effect.
Inquiry/Document request
In charge of Macnica Menlo Security
- TEL:045-476-2010
- E-mail:menlo-sales@macnica.co.jp
Weekdays: 9:00-17:00