Exabeam
Exabeam
Effective use of logs collected by SIEM (Splunk, etc.) with ExabeamUEBA
By combining a small amount of additional logs with existing SIEM (Splunk, etc.) logs and Exabeam's unique model rules, it is possible to achieve "internal fraud countermeasures" and "reduction of security operation burden". Become.

(1) Countermeasures against internal improprieties - information leakage across applications and systems -
Telework has become pervasive, and the number of situations where administrators cannot keep an eye on is increasing, and the threat of internal fraud is increasing.
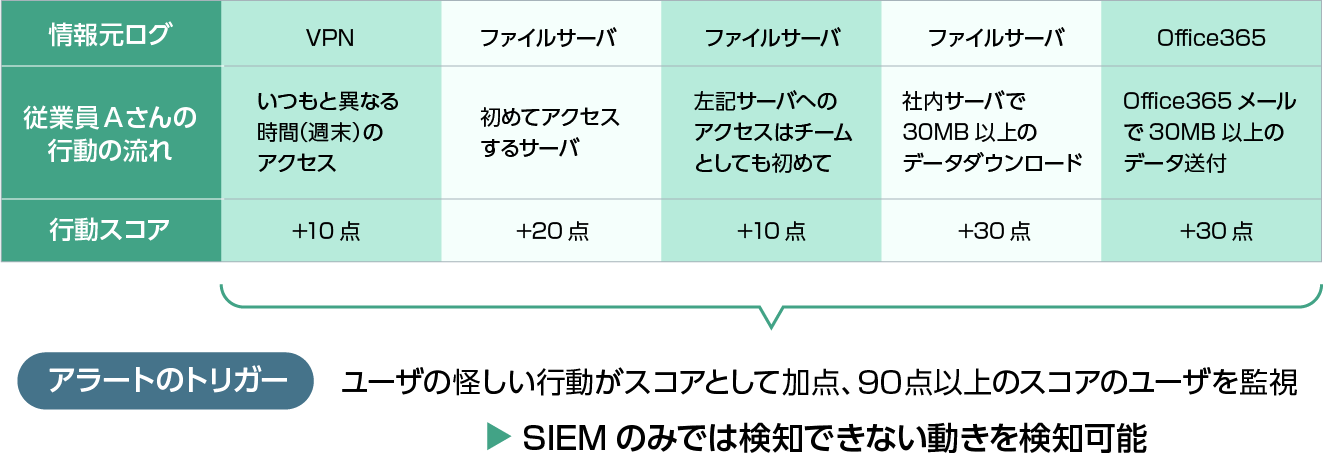
By combining normal behavior + abnormal behavior into a timeline, it is possible to grasp a series of employee movements.
Why UEBA (User and Entity Behavior Analytics) as an internal fraud countermeasure?
→Because the user (device) behaves “unusually” when information is stolen illegally.
Countermeasures against internal improprieties in other products
- CASB: It is possible to grasp what kind of data is uploaded on the contract SaaS. Monitoring is not possible once the data is outside the SaaS.
- Proxy: Category of access destination specified by the administrator: Possible if access is controlled by URL.
- DLP: Tag data defined as sensitive information and alert or control when tagged data is taken out.
- EDR: Asset management: It is possible to acquire and save the operation history on the terminal. Fraud is difficult to judge.
(2) Strengthening measures against external threats - (1) Improving the granularity of measures -

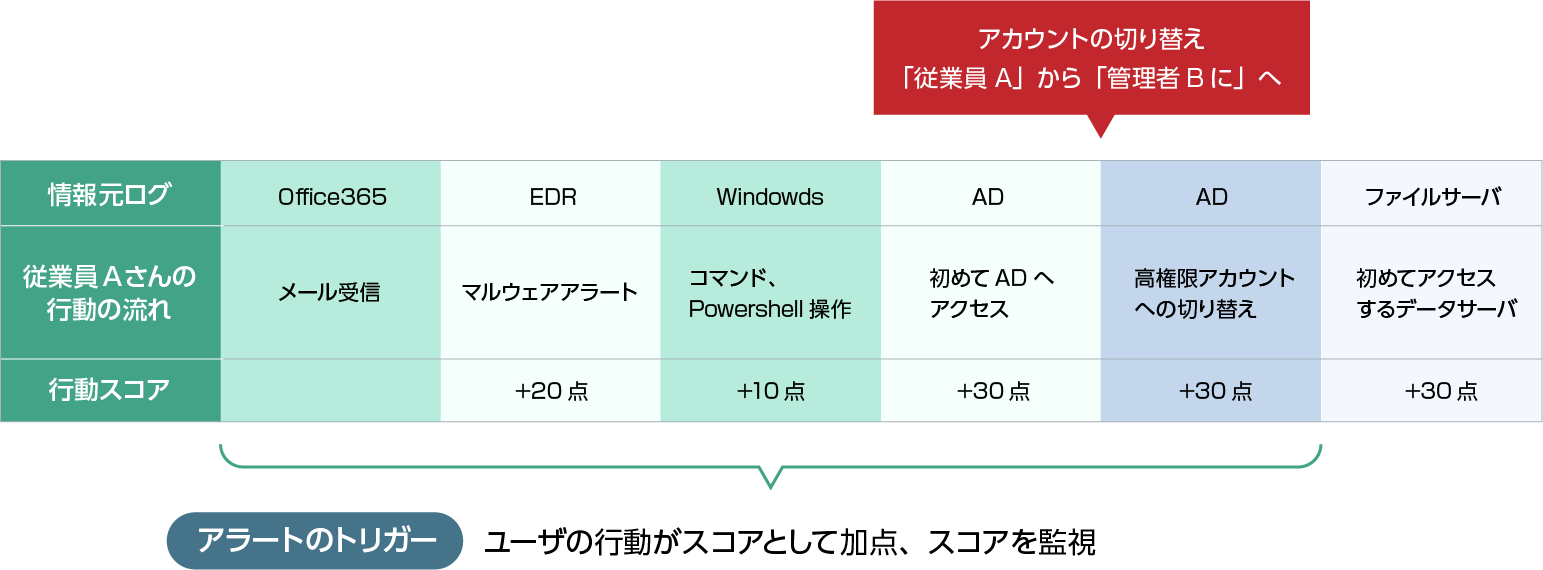
By combining normal logs other than security alerts into a timeline, lateral movement after an external threat has infiltrated can be detected at an early stage.
Exabeam can follow a series of flows even if authentication information and terminal information change.
(2) Enhancement of countermeasures against external threats - (2) Reduction of operational burden -
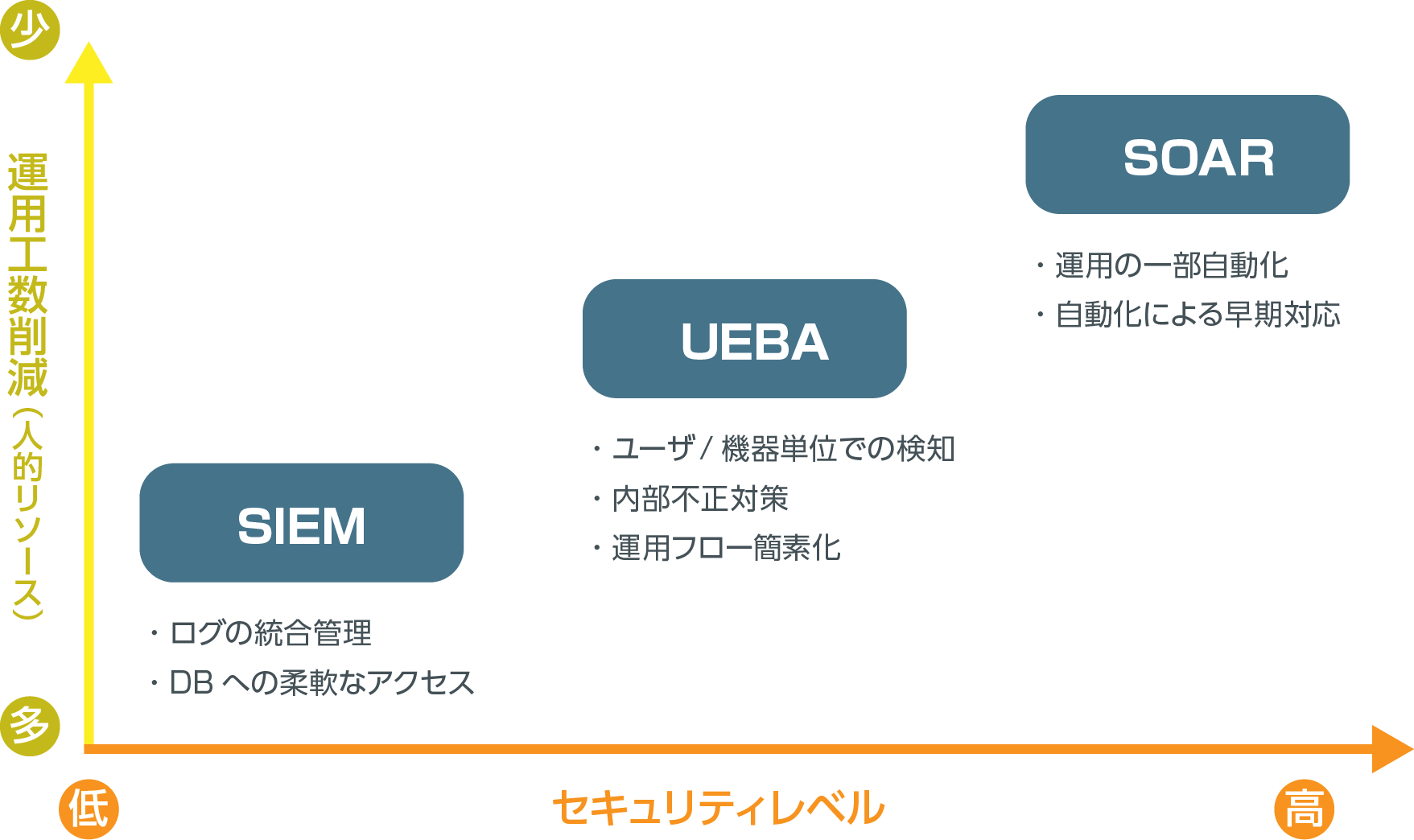
By introducing Exabeam, it becomes possible to partially automate the SIEM operation flow and allocate man-hours to more urgent tasks.

SIEM platform
In terms of cyber security, it is becoming increasingly important to manage and utilize logs to take preventative and post-incident security measures.
In order to grasp the contents of the log with limited human resources and analyze it in as short a time as possible, it is necessary to consider automation such as UEBA and SOAR.
Inquiry/Document request
In charge of Macnica Exabeam Co., Ltd.
- TEL:045-476-2010
- E-mail:exabeam-sales@macnica.co.jp
Weekdays: 9:00-17:00