
Exabeam
Exabeam
Featured Gartner's 2021 "Magic Quadrant for Security Information and Event Management" places Exabeam as one of the Leaders in Ability to Execute!
*Magic Quadrant for Security Information and Event Management, Kelly Kavanagh et al., 8 February 2020
Gartner does not endorse any vendor, product or service depicted in any Gartner Research publication. Nor does it advise technology users to select only those vendors with the highest ratings or other designation. Gartner Research publications consist of the opinions of Gartner Research and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Background of the Need for More Efficient Security Operations
In recent years, due to the corona vortex and work style reforms, the spread of remote work and the use of cloud-based SaaS represented by Office365, etc. have increased, and the internal network has become more complex and extensive. In addition, cyberattacks have become more sophisticated and diversified, and each security product has come to notify a large number of alerts, including false detections.
It is difficult for operations administrators to respond to all of these alerts, and missing important alerts may lead to serious incidents. In addition, due to the complexity and widening of the internal network, it may take time to analyze the incident investigation, leading to a serious incident.
Using Exabeam's UEBA technology, we will solve the security operation issues that our customers face with new security operations centered on "people."
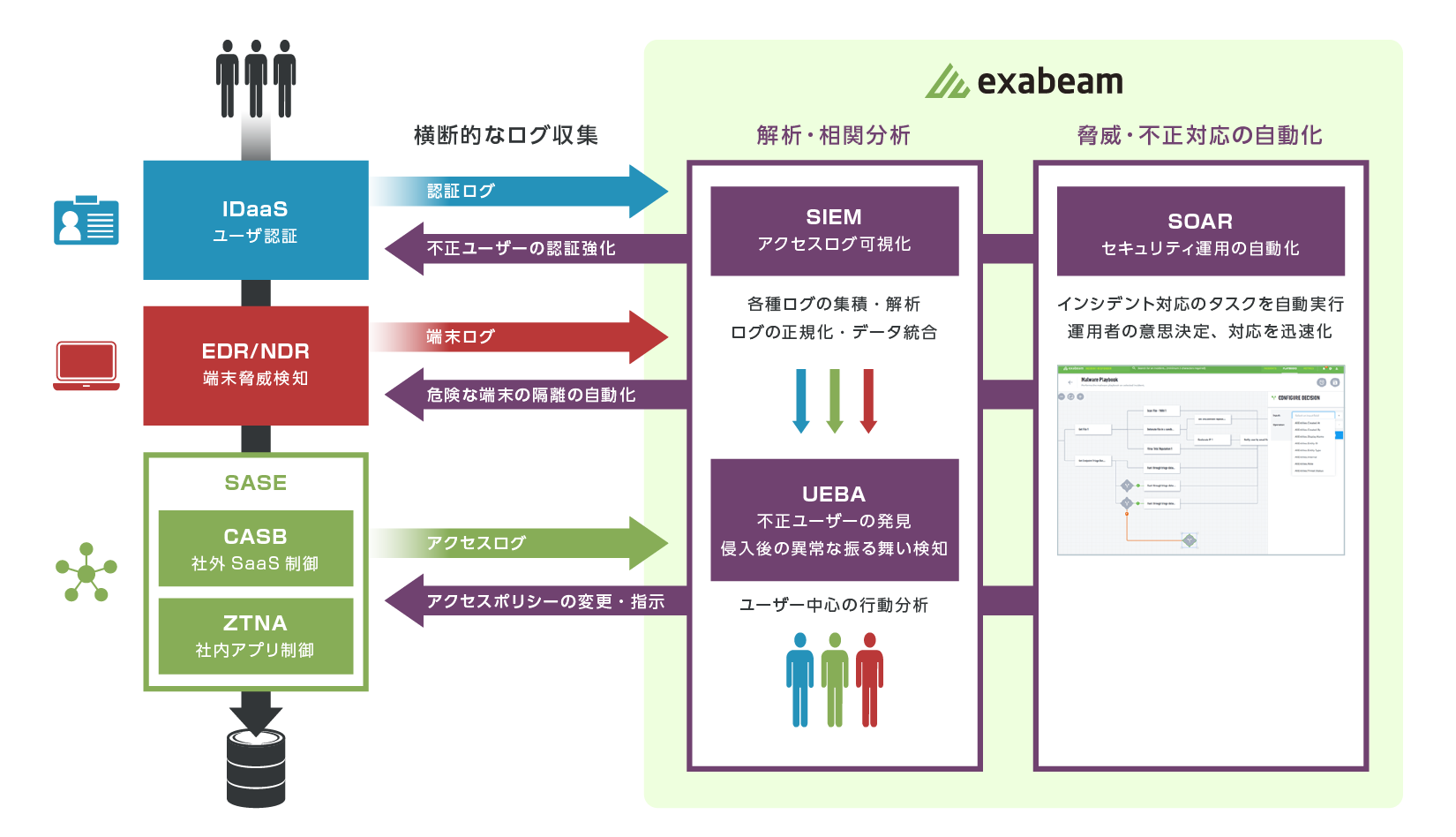
(1) Increased complexity of intrusion routes and expansion of targets for monitoring and investigation
Due to the mixture of on-premises, cloud, and home environments, the complexity of intrusion routes and the expansion of targets for monitoring and investigation
It has a SIEM function that enables log collection from on-premise environments, cloud services, and terminals, and can automatically visualize the behavior of each user and detect abnormal behavior.
In addition, the SOAR function can be used to automate incident response and reduce the operational man-hours of security operators.
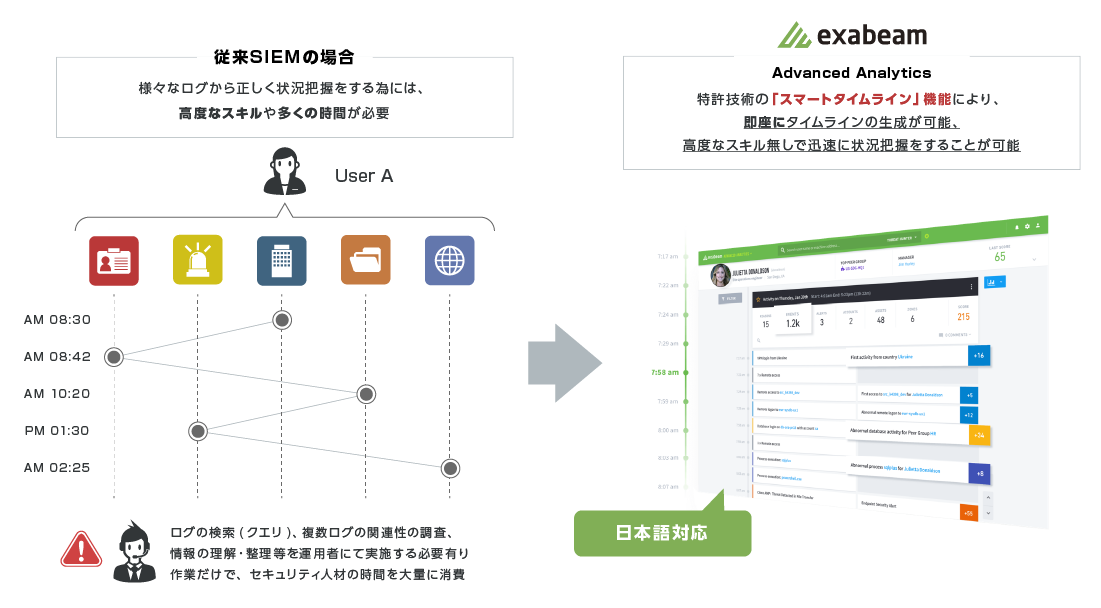
②ログ分析に高いスキルと膨大な工数が発生
複雑化した膨大なITシステムと、多数のセキュリティ製品の導入により、ログ分析に高いスキルと膨大な工数が発生
With conventional SIEM, even though it is possible to collect logs from multiple IT systems and security products, it was necessary to spend time manually creating rules to analyze the logs in a correlated manner.
Exabeam uses the Smart Timeline feature to automatically organize a wide variety of logs, allowing you to quickly understand the behavior of each user without advanced skills.
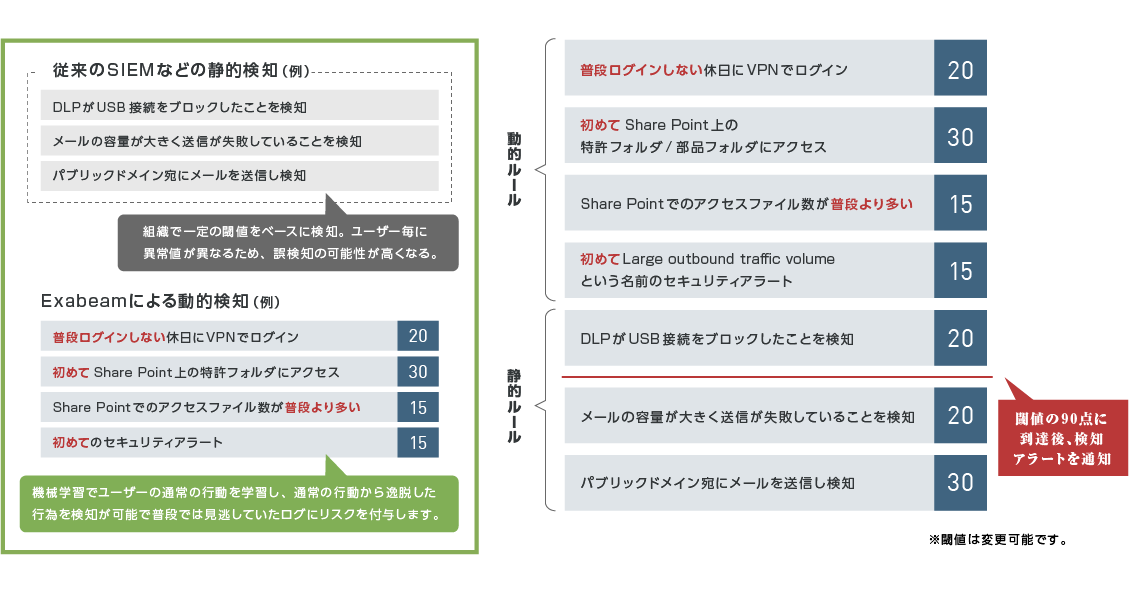
(3) Tight operation man-hours
Overwhelming operation man-hours due to a large number of logs and alerts from each management device
While traditional SIEM requires action for each alert, Exabeam combines dynamic and static rules based on machine learning, scores and alerts based on total risk. By notifying operators of alerts when preset thresholds are exceeded, there is no need to respond to individual alerts from each device, reducing the number of items to be investigated and reducing the burden on operators. mitigate.
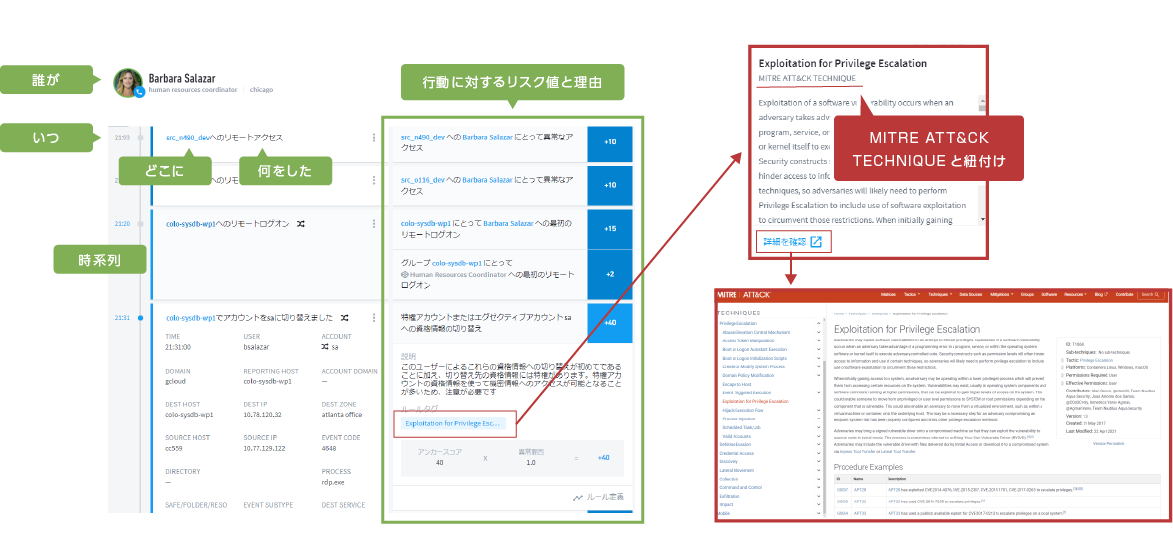
(4) Difficulty in quickly grasping the situation after intrusion
Due to the sophistication of threats, it is difficult to quickly grasp the situation after an intrusion
From the acquired logs, actions such as "who", "when", "where", and "what" are automatically visualized in chronological order, and actions and risks to actions can be judged in relation to each other. It is possible to immediately respond to lateral movements that used to take time. In addition, since each risk is linked to MITER ATT&CK TECHNIQUE, it is possible to grasp the progress of cyberattacks.
Please feel free to download it.
Inquiry/Document request
In charge of Macnica Exabeam Co., Ltd.
- TEL:045-476-2010
- E-mail:exabeam-sales@macnica.co.jp
Mon-Fri 8:45-17:30


