Exabeam
Exabeam
Visualization of malicious internal fraud: Effectiveness of predictive detection by behavioral analysis (UEBA)

Ask the Experts blog series
According to an April 2018 Ponemon Institute study, the average annual cost of insider fraud detection and resolution in the United States is $8.76 million and rising. Larger organizations tend to spend more on mitigating insider fraud than smaller ones. Two-thirds of incidents are caused by negligence, with negligent employees or contractors generally causing the most problems.
The Ponemon report also found that 23% of incidents involved insiders with actual criminal intent, and 13% involved stolen credentials. Although the number of incidents is small, it is an incident type that causes a particularly large amount of damage.
The report states that the average time to contain an incident was 73 days, of which only 16% were contained within a month. Costs increase in proportion to the time taken for containment.
The Ponemon report confirms what you may already know: insider fraud of all kinds is skyrocketing in both frequency and cost.
However, these investigations reveal only known data on insider fraud. How many incidents are still undetected inside the 159 organizations surveyed? There is no way to know for sure, but cyber threats and incidents often go undetected and unreported, sometimes for years. What we do know is that any organization can be at risk of insider fraud, and the scale of that attack is bigger than we can imagine.
insider definition
Since there is no clear consensus on what insider and insider fraud mean, we will define them first. An insider is a person duly authorized to access one or more of an organization's network assets. For example, employees, contractors, vendors, partners, and former employees who have not revoked access. They may also include developers with backdoor access and employees of merged and acquired companies that migrate existing systems and integrate them into their networks.
Insider fraud is the negligent or willful criminal act against an organization's assets by an insider or an outsider impersonating an insider. An insider fraud incident is a loss resulting from one or more such frauds.
Common Indicators of Insider Fraud
まず、比較的よくある内部不正に注目しましょう。監視すべき予測可能な行動指標を以下に挙げます。
- Suspicious VPN Activity: Connections made at unusual times from unusual locations or IP addresses.
- An employee who has been informed of an unpleasant event, such as a layoff. It affects not only those directly affected, but also those who remain in the workplace, including demotivation.
- A retiring employee who has just submitted a letter of resignation. It's not uncommon for people to create new accounts and gain access before their credentials are revoked, often before they submit a letter of resignation.
- People downloading large amounts of data to external drives or using unauthorized external devices.
- People accessing data not related to their job.
- Emailing Sensitive Information to Personal Accounts.
- Anyone trying to circumvent security controls.
- People requesting higher levels of access when they don't actually need it.
- Former employees who have access to sensitive data even after leaving the company.
- Crawling the network, scraping data, or copying from internal repositories.
- Deviations from normal working hours patterns.
As you can see, insider threats are not just one event, but a series of events that ultimately threaten an organization. It is important to proactively identify these risky behaviors and patterns and alert the Security Operations Center (SOC) so that they can monitor for possible insider threats.
Traditional Approaches to Stopping Insider Fraud
Many organizations often focus on DLP (data loss prevention) in an attempt to stop unauthorized data transfer (data exfiltration). However, the results produced by many DLP solutions take time and resources to make use of. Typically, analysts must create rules for individual policies and violations, which can result in hundreds or even thousands of events each day. This makes finding real threats and incidents a “needle in a haystack” task.
Another problem with traditional insider fraud detection is the inability to understand the intentions of insiders. As mentioned above, most insider frauds are caused by negligence rather than malicious intent. If you notice that there is a lot of negligent fraud in your organization, you might consider education rather than punishment as a corrective action. But taking such appropriate action requires understanding the intent of the action.
Proactive detection of insider fraud with a behavior-based approach
The goal should be to stop internal fraud before it becomes an incident. Unlike external threats, insider threats typically evolve over time. To detect it, you need to be able to monitor user behavior that deviates from normal, such as copying and storing files for export or creating accounts for later use.
“It is extremely important that organizations understand the normal behavior of their employees as a baseline, and that employees also understand that they can be used to collect information about others.”
Combating the Insider Threat, US Department of Homeland Security
The tool you need to identify insider behavior is a UEBA (User and Entity Behavior Analytics) solution that applies data science to all your existing threat intelligence and IOCs (Indicators of Compromise). This methodology incorporates tactics, techniques, and procedures (TTPs) from past known attacks.
Exabeam's UEBA takes a behavior-based approach that analyzes user behavior on the network and applies advanced analytics to detect anomalies. Automatically stitch together related events to help identify indicators of malicious intent and quickly detect insider threats. Exabeam's Threat Hunter enables analysts to search for fraud based on identified behavioral artifacts and user context.
Examples of intellectual property theft
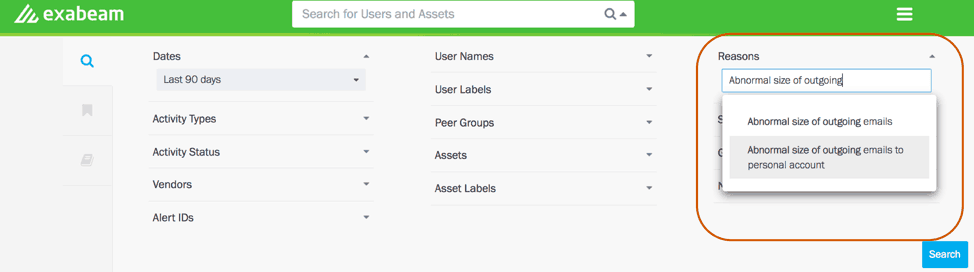
Consider the common scenario of a soon-to-retire employee trying to steal intellectual property (IP). The Advanced Analytics dashboard allows analysts to search for users exhibiting predictable malicious behavior by simply selecting a risk reason from a dropdown. This is one way to catch and watchlist users who aren't following the rules. This is just one example of the many insider fraud investigations analysts can conduct.
Figure 1: Using Threat Hunter to search for users who have sent an unusual number of emails to their personal accounts in the last 90 days
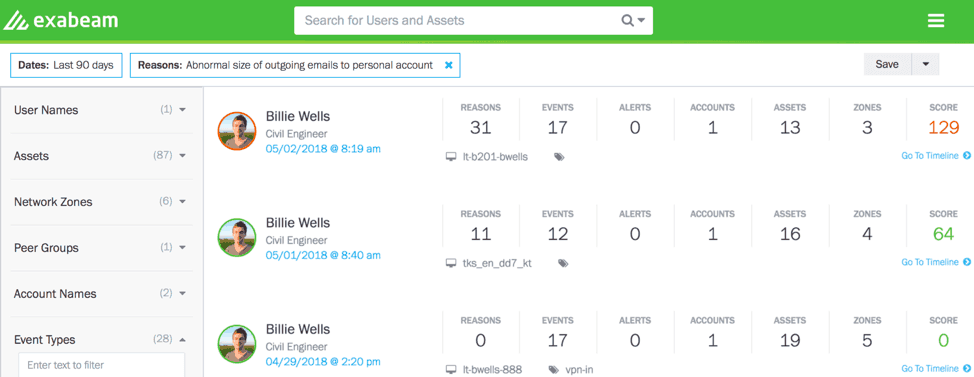
In Figure 2, a user sent a large number of emails to a personal account, resulting in a risk score of 129. Below the score, the UEBA timeline provides analysts with relevant events and malicious indicators to bring insider threats to light (Figure 3).
Figure 2: Threat Hunter view of a user with multiple events sending an unusual number of emails to a personal account
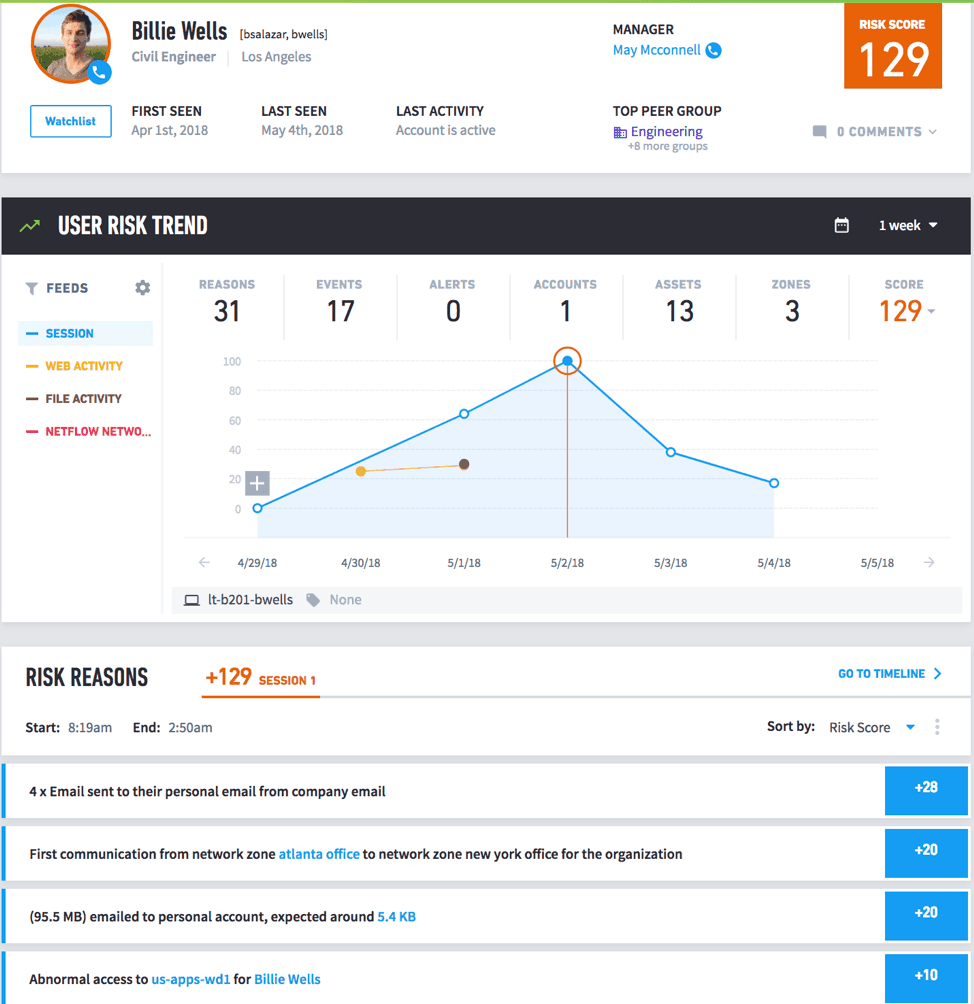
Click on a user's timeline to explore all events and track indicators of malicious intent. Now let's see how the UEBA timeline helps analysts bring insider fraud to light.
In this example, we found a user with a risk score of 129. Then you can check the timeline to see if there are other indicators of insider fraud. Looking for one metric usually finds not just one, but many other related events that lead to fraud. User Trends let you track all related events stitched together in one timeline. You can also filter by other activities like files, web, network, etc.
Figure 3: with filter option by user activity,
User card showing user trends for all malicious behavior
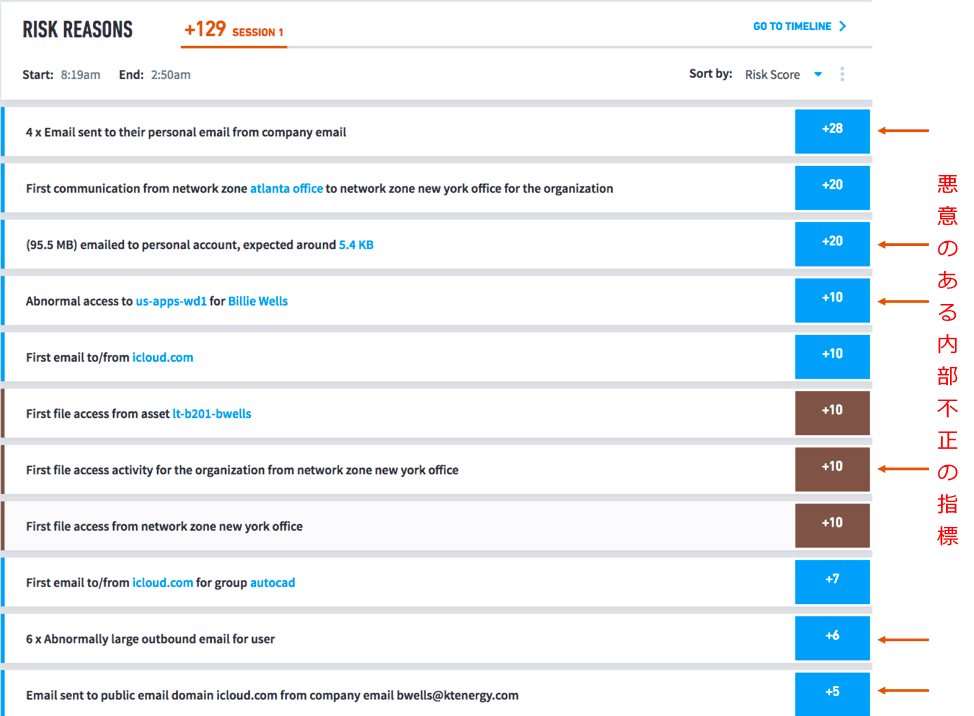
As you can see, a single indicator alone does not constitute an internal impropriety. A user uploading a single unusually large email to a personal account does not, by itself, raise the score to a level of concern. However, when combined with other anomalous behavior, this sequence of events is flagged as suspicious and high-risk. Looking at all the reasons for this user's risk, we can see that there are many behavioral artifacts that lead to insider threats.
Figure 4 combines data exfiltration (sending company data to personal accounts) with anomalous access to other systems (lateral movement). This reveals patterns of fraud in practice.
Exabeam provides a number of models to thoroughly profile user behavior. This works great for detecting unknown behavioral artifacts.
Figure 4: Various indicators of malice strung together in a timeline to point investigators to insider fraud
Based on the anomalous events uncovered by Exabeam Advanced Analytics (AA), analysts can easily monitor users and even terminate access if they exhibit anomalous behavior. Advanced Analytics provides enough evidence to confront suspicious users without the risk of guilt. Most importantly, Advanced Analytics is a robust tool that keeps investigators and SOC analysts in check for insider fraud.

Pramod Borkar
Exabeam, Inc. Technical Marketing
Inquiry/Document request
In charge of Macnica Exabeam Co., Ltd.
- TEL:045-476-2010
- E-mail:exabeam-sales@macnica.co.jp
Weekdays: 9:00-17:00