Exabeam
Exabeam
Security measures and operation problem solving! What is UEBA?

What is UEBA?
UEBA is an abbreviation for User and Entity Behavior Analytics, and is a method of collecting logs from multiple security products and network devices to analyze the behavior of each individual user.
In the past, there was a method called UBA (User Behavior Analytics) that analyzed the behavior of individual users. From the point of view that everything should be covered, it is mainstream to refer to it as "User and Entity" rather than just "User".
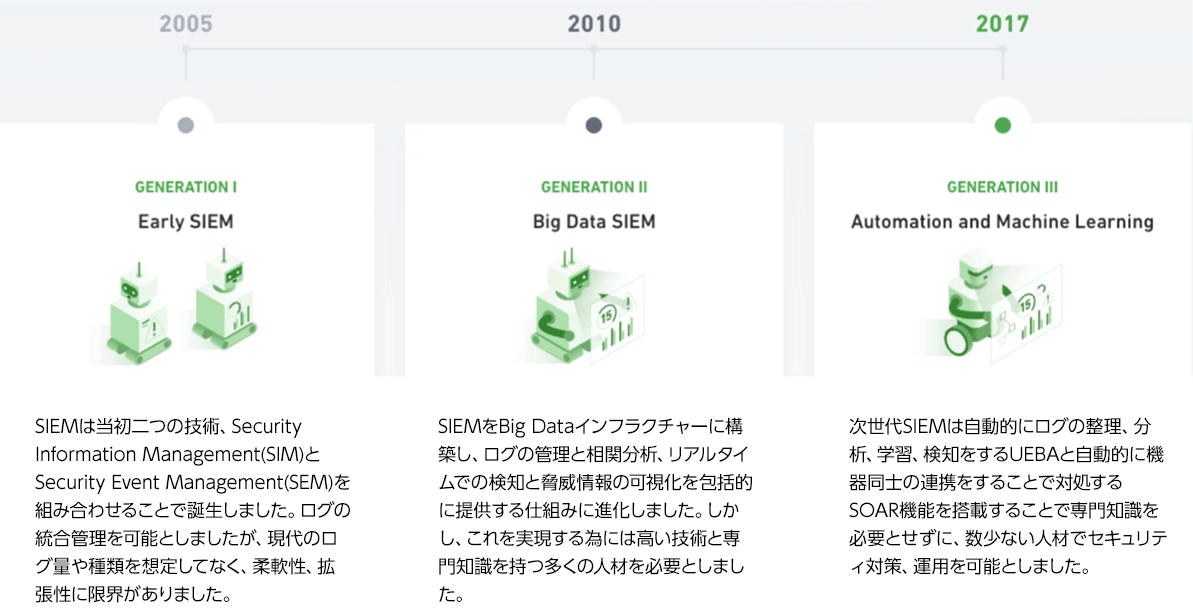
History of SIEMs
SIEM Challenges Solved by Exabeam
SIEM customers suffer from sharing challenges. A large amount of information, difficulty in detecting advanced insider threats, and a shortage of security experts. A next-generation SIEM that utilizes UEBA will solve these issues.
- lots of logs
- Expensive log collection and storage
- Advanced analysis and reporting are not possible

- Sophisticated Attacks, Missing Insider Threats
- A lot of noise due to inefficient rules
- can't associate

- Inability to deal with a large number of alerts
- Shortage of human resources
- Inability to standardize operations

Security operations that anyone can do with Exabeam's UEBA - Easily visualize and analyze risks that you wanted to achieve with SIEM! ~
Exabeam automatically learns the user's business patterns using Exabeam's intelligence, and detects and visualizes abnormal behavior such as targeted attacks and internal fraud. Traditionally, SIEM has been used to collect and analyze logs, but in order to analyze logs aggregated by SIEM, comprehensive knowledge of each device and security is required. Furthermore, it is said that it is difficult to master the SIEM itself because it requires technical skills to master it.
By utilizing Exabeam's UEBA solution Advanced Analtyics, it is possible to automatically collect, analyze, and visualize logs, and easily visualize risks without difficult knowledge or operational skills.
Collect logs from all devices
Logs can be collected from anything!

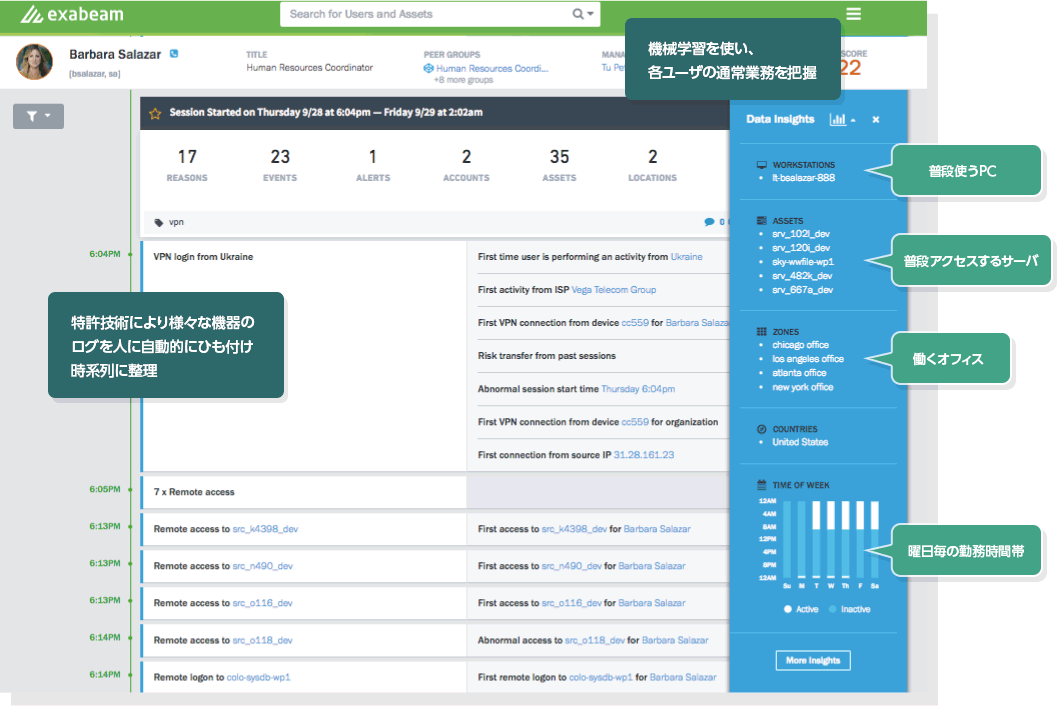
Understand the normal work of each user
Exabeam patented technology automatically links target logs to humans or machines and organizes them in chronological order. All device logs, including not only abnormal behavior logs (alerts, etc.) but also normal behavior logs (access logs, etc.), are automatically linked to people and machines and arranged in chronological order.
Normally with a SIEM or other logging solution, this work would have to be done by a human. When an incident occurs, people gather logs of various devices, search, understand relationships, dig deeper, and spend time and effort to organize events. increase. This work requires knowledge of each product, knowledge of security, and knowledge of the internal environment. In addition, the current IT environment has multiple terminals, authentication information, IP addresses, etc. that people use, and it is fluid, so it is not possible to reuse it once it is created, and it is necessary to create it each time.
Exabeam uses patented technology to recognize changes in devices, authentication information, IP addresses, etc., and automatically creates a timeline by linking logs from various devices to people or machines. This timeline is created not only when an incident occurs, but also every day, for each person, and for each machine, so customers can quickly perform not only detection but also operations such as understanding the situation, investigating, and making decisions.
Behavior detection by machine learning
Exabeam leverages data science, behavioral analytics and machine learning to perform advanced analytics. Exabeam learns the normal behavior of each person or machine from various logs on a daily basis and creates a baseline of correct behavior patterns for each person or machine.
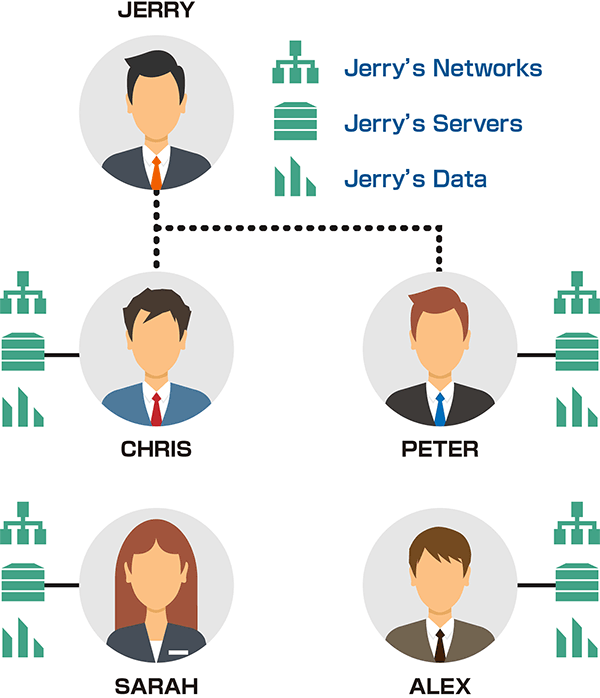
Exabeam learns from two main perspectives to create a baseline. singular and collective. Taking a person as an example, Exabeam learns from two points: the profile of the individual (single) and the group profile of attributes similar to that person (collection). By learning at two points in this way, even if abnormal behavior is included in the data, it can learn and detect it appropriately. Specifically, if a sales person has access to personnel data from the first day, it is not possible to learn that there is an abnormality from the perspective of that person alone, but by comparing with other sales departments We can detect anomalous behavior by detecting that only this person is accessing data even though the other person is not accessing HR data.
When doing group profiling, you need to understand people's attributes. Exabeam can use the provided attribute information, including personnel information, to understand the attributes of a person. In addition, we use a technology called Dynamic Peer Grouping. This technology uses machine learning to automatically create groups of similar attributes from human behavior analysis and compare them.



video on demand
The threat is in full view! Realizing effective log analysis with machine learning
~What is Exabeam, the next-Next-Gen SIEM Platform Exabeam?~
As targeted attacks and internal fraud continue to increase in recent years, an increasing number of companies are building mechanisms (such as SIEM) to correlate and analyze logs from multiple security products in order to implement appropriate security operations. . This is because it is difficult to visualize the impact of each incident using only the logs of security products that have already been installed, and threats may be overlooked. However, building such a system requires security-related knowledge, analytical know-how, and ideas. In this seminar, we will introduce “Exabeam” which realizes log analysis by UEBA (User Entity Behavior Analytics) technology and efficiency of conventional SIEM operation.
Inquiry/Document request
In charge of Macnica Exabeam Co., Ltd.
- TEL:045-476-2010
- E-mail:exabeam-sales@macnica.co.jp
Weekdays: 9:00-17:00