
Eclypsium
Eclypsium
Vulnerabilities Below the OS - The need to address firmware vulnerabilities
Eclypsium is a "vulnerability below the OS" (VBOS: Vulnerability below the OS) that visualizes vulnerabilities and signs of tampering in devices and servers managed by companies, firmware of network equipment, boot loaders, etc. This is a new area of security solutions.
What is Firmware Vulnerability - A New Target Area
Since 2019, many critical vulnerabilities in the operating systems and applications of terminals and network devices have been reported. If an attacker exploits these vulnerabilities, they may bypass perimeter-type defense in depth and monitoring to infiltrate the corporate network, steal information after the intrusion, and perform lateral expansion. Countermeasures against OS and application vulnerabilities are an urgent need. In addition to this, attackers are beginning to pay more attention to firmware vulnerabilities that have not received much attention in the past.
Why Firmware Vulnerabilities Are Targeted
Current security measures, as typified by EDR, focus on quickly discovering breaches that have occurred, rather than preventing 100% of breaches themselves against unknown threats. On the other hand, if the compromise extends to the firmware, it cannot be detected by OS-level security measures, giving the attacker time to operate without being detected by the attack target. Against this background, vulnerabilities in firmware have attracted the attention of attackers. Specific reasons why attackers target firmware include the following:
- By running malware before the OS boots, it can be compromised using admin-level privileges
- Since existing security solutions operate at the OS level, it is difficult to detect exploitation of firmware vulnerabilities and tampering with firmware.
- If the firmware is tampered with, it is difficult to restore by reinstalling the OS or replacing the hard disk.
- Corrupting the firmware can render the device permanently unusable
Such firmware vulnerabilities are attracting attention as a new security area called "Vulnerabilities Below the OS" (VBOS), and the need for countermeasures against them.
VBOS mitigation with Eclypsium
Eclypsium's VBOS countermeasure solution visualizes terminals, servers, network devices, etc. managed by companies, and provides a function to continuously check mainly firmware settings and compliance with various compliances. increase.
Features of Eclypsium
① Visualization
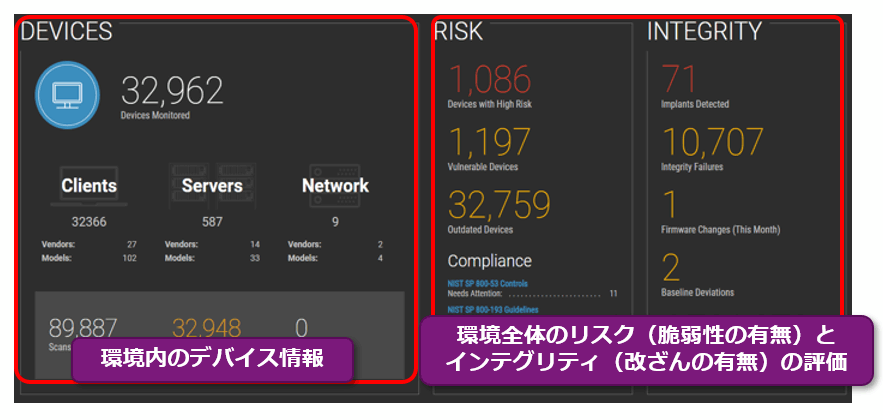
- Vulnerability (Risk) in firmware can be visualized, and the inventory of terminals and network devices and the status of their firmware can be centrally managed on a single dashboard.
- Vulnerabilities in firmware can also be visualized, and an overview of the vulnerabilities, attack cases, and repair methods can be presented.
② Detection
- It is possible to detect whether the firmware has been tampered with or changed (Integrity)
③ Coping
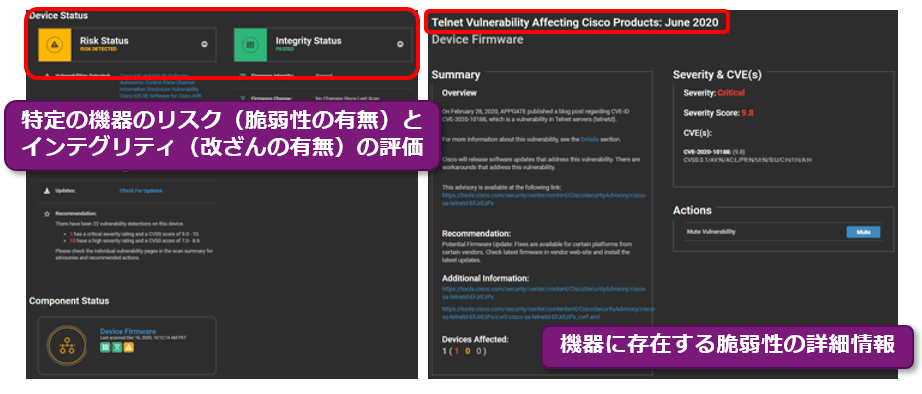
- If there is a vulnerability that needs to be addressed, it is possible to check the details of the vulnerability and apply a patch.
Simple and easy-to-understand UI
Eclypsium lists the terminals, servers, and network devices that exist in the environment, and scores their firmware status from the two perspectives of risk (presence of vulnerabilities) and integrity (presence of tampering). Also, if there is a vulnerability that needs to be addressed, you can check the details of the vulnerability and apply a patch.
Evaluation from a third party
Serving Global 2000 companies as well as state and federal government agencies, Eclypsium is the choice of many.
- Gartner Cool Vendor in Security Operations and Threat Intelligence
- 『TAG Cyber Distringuished Vendor』
- "Fast Company's World's 10 Most Innovative Security Companies"
Inquiry/Document request
Macnica Eclypsium
- TEL:045-476-2010
- E-mail:eclypsium_info@macnica.co.jp
Mon-Fri 8:45-17:30
