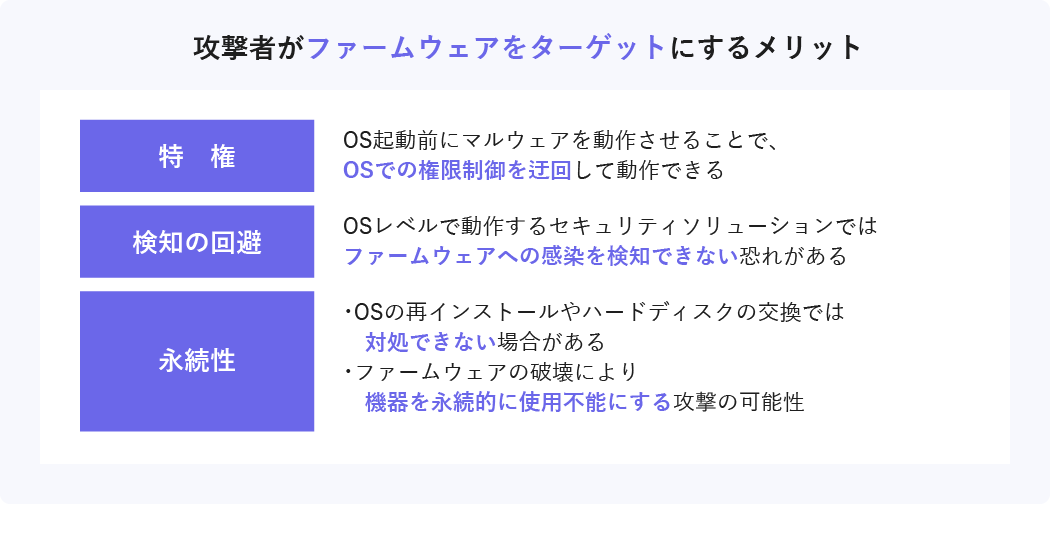
EDR is powerless when firmware is tampered with
Recently, there has been an increase in attacks targeting vulnerabilities in firmware. The trouble with firmware attacks is that EDR is useless. EDR works after OS boot, but firmware works before OS boot. If the firmware is tampered with, it becomes possible to attack before EDR is activated, and the damage spreads without being detected by EDR.
Now, let me explain what the risks of firmware tampering are.
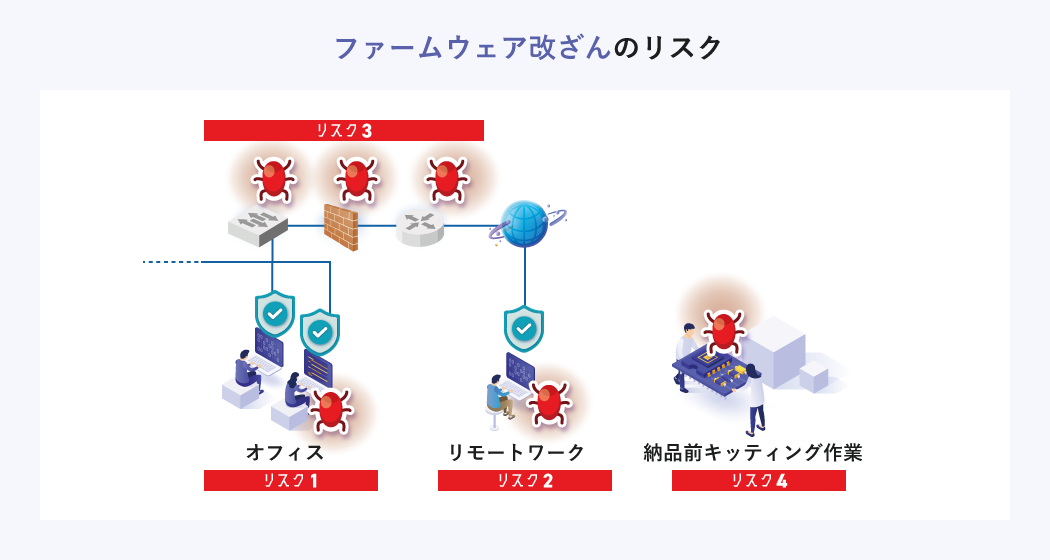
Risk 1 Risk that cannot be detected by EDR
Firmware is the basic software for operating the OS and software. Malware infected with firmware may not be detected by EDR because it runs before the OS boots.
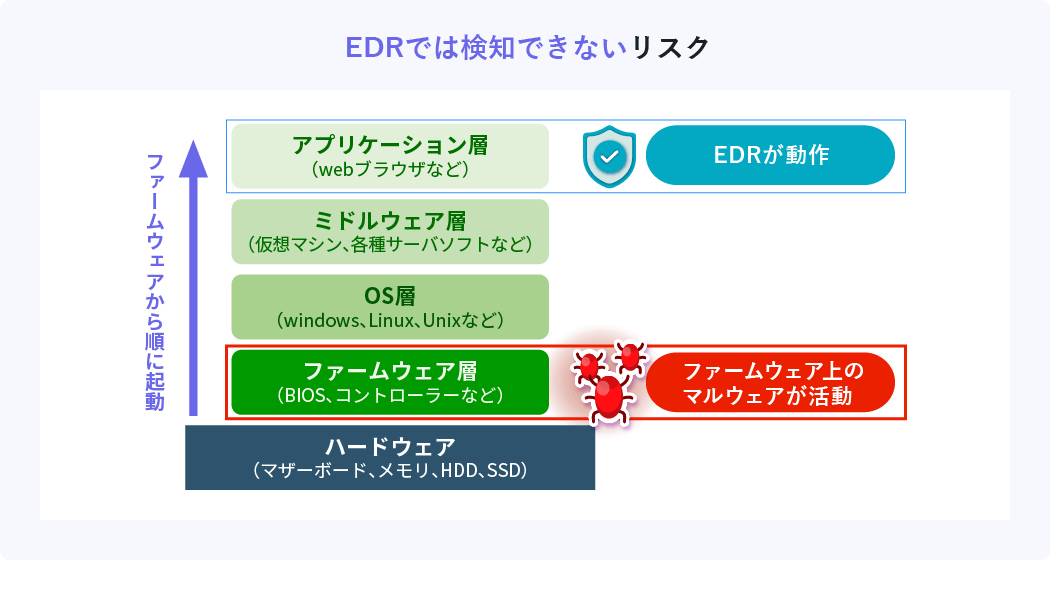
In addition, the firmware is written in an area separate from the hard disk called SPI flash memory. Therefore, even if you reinstall the OS or replace the hard disk, the malware remains, and there is a risk that the malware will remain dormant for a long time.
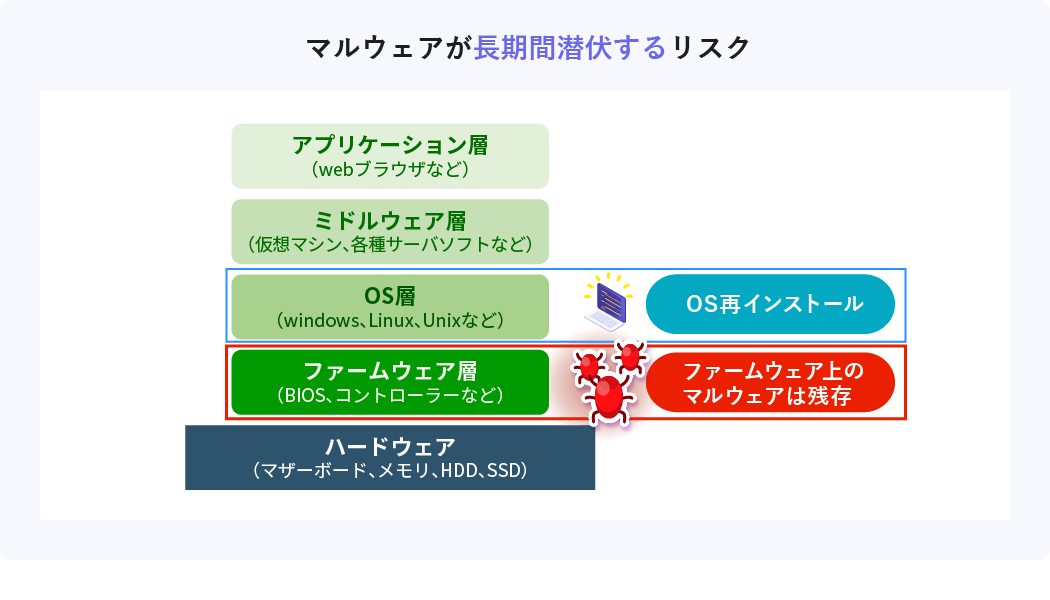
Risk 2 Risk of being able to attack a device that is powered off by physical contact
An attack on the firmware is possible even on a PC that is not powered on. If you connect a special device to a PC with the power off, you can directly rewrite the firmware and infect it. In other words, software defenses are powerless. In fact, there have been cases where notebook PCs were taken away from home and their firmware was tampered with.

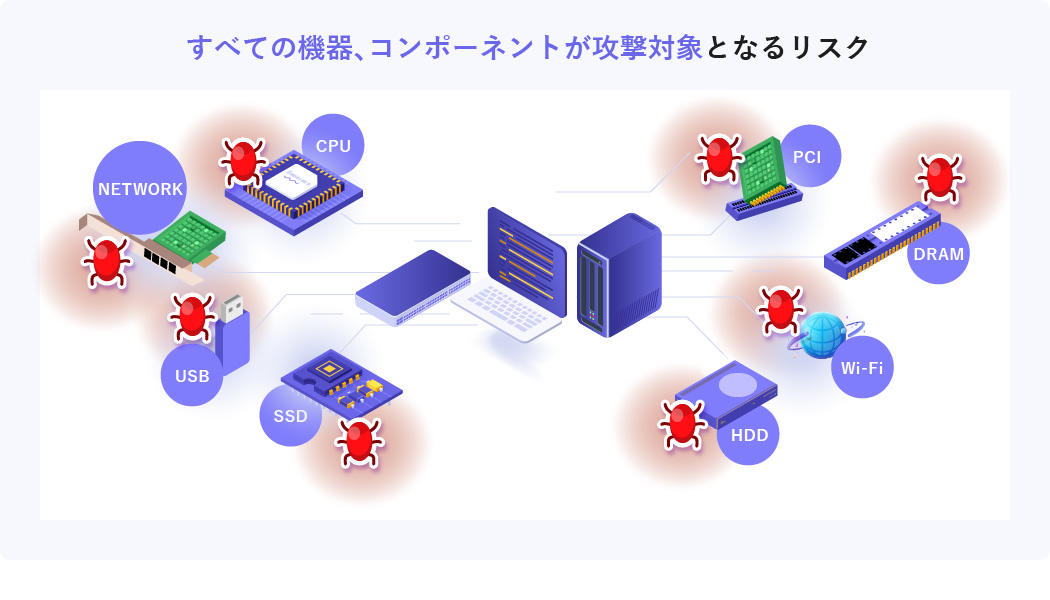
Risk 3 Risk that all devices and components become targets of attacks
Firmware exists not only in PCs and servers, but also in all devices connected to the network such as switches and routers. Also, even within a single device, vulnerabilities exist in each component such as CPU, SSD, network interface, etc., so it is extremely difficult to deal with all risks.
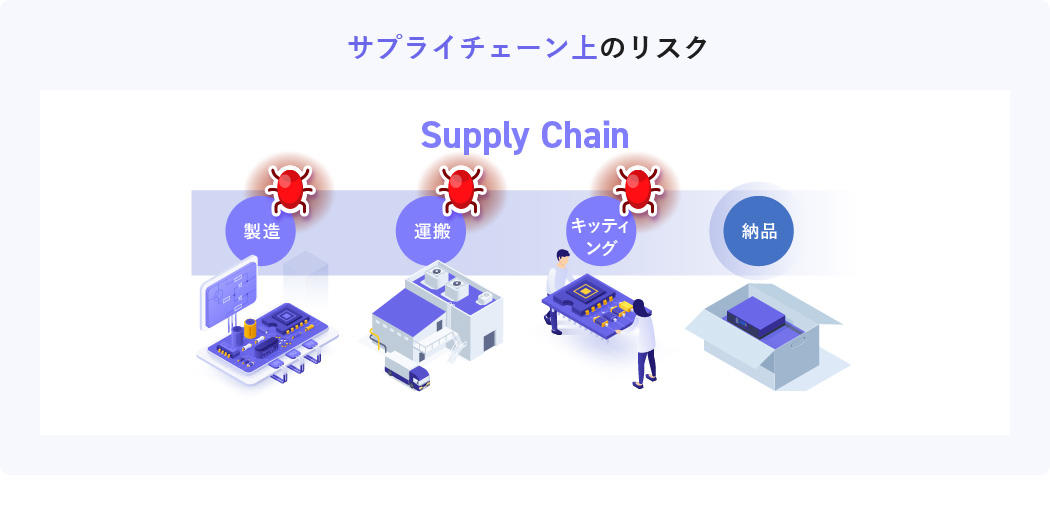
Risk 4 Risks in the supply chain
Even if your company's security is solid, is security before delivery okay? It is conceivable that security is weaker at the part manufacturing stage than after delivery. There is a risk of being attacked during manufacturing, transportation, and kitting before delivery, and infected devices being brought into the company without anyone noticing.
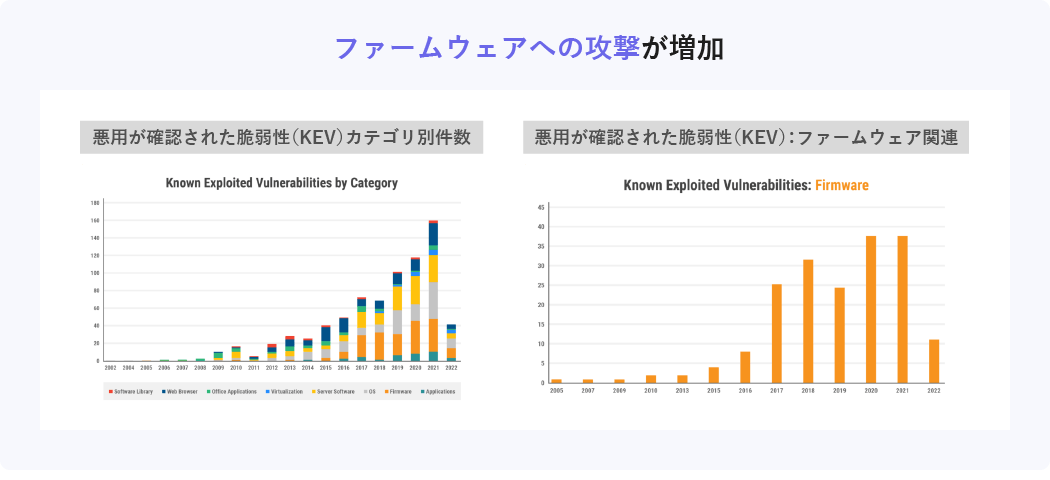
Firmware Attacks on the Rise
Reports of exploitation of firmware vulnerabilities have skyrocketed in recent years. Some data show that around 30 firmware vulnerabilities have been used in attacks every year since 2017. This is a high level compared to vulnerabilities in OS, browsers, virtualization infrastructure, etc.
Why are attacks on firmware increasing?
Firmware tampering is difficult to detect with existing EDRs, and threats are often persistent compared to OS and application infections. In fact, there are cases where the existence of malware targeting certain firmware was discovered more than seven years after the firmware was distributed. Attacks on firmware, which are highly profitable for attackers, have recently attracted the attention of criminals.
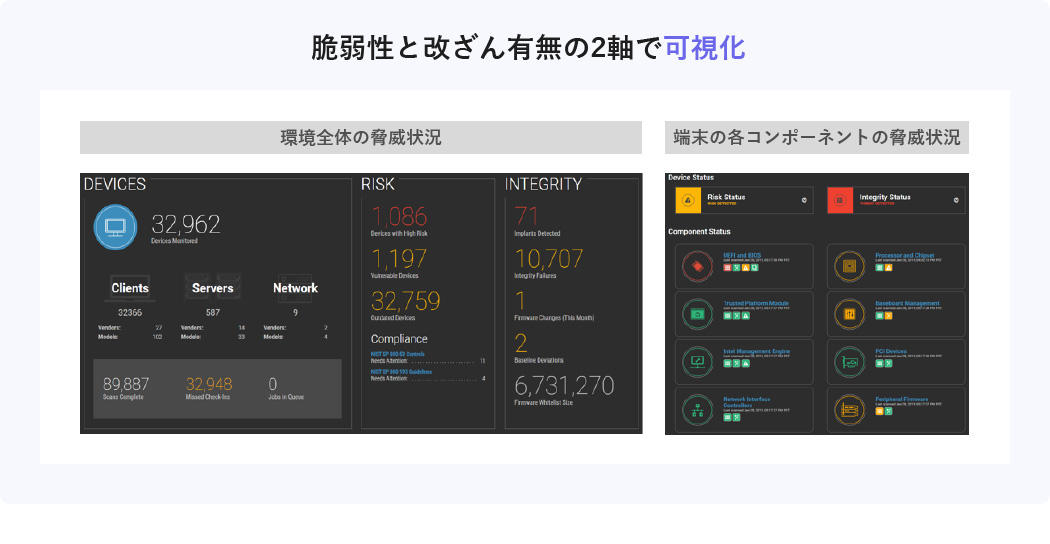
Firmware Vulnerability Countermeasures Eclypsium
Eclypsium is a firmware security solution. Scan the firmware of PCs, servers, network devices, etc., visualize vulnerabilities and tampering, and present countermeasures.
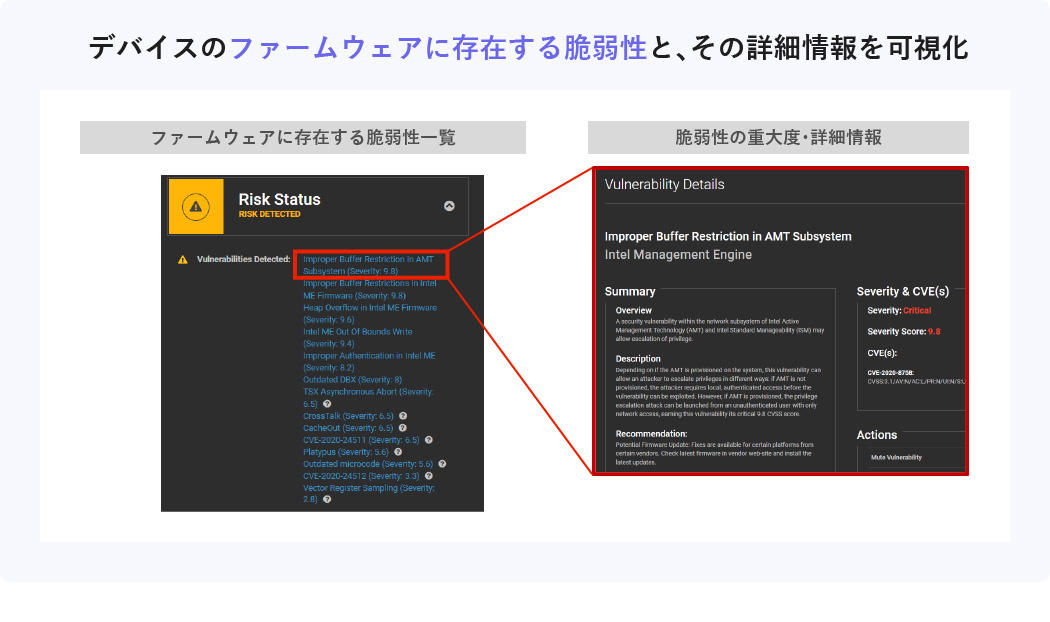
Features of Eclypsium 1 Vulnerability display
Lists vulnerabilities present in the firmware of each device.
You can also check detailed information and severity for individual vulnerabilities.
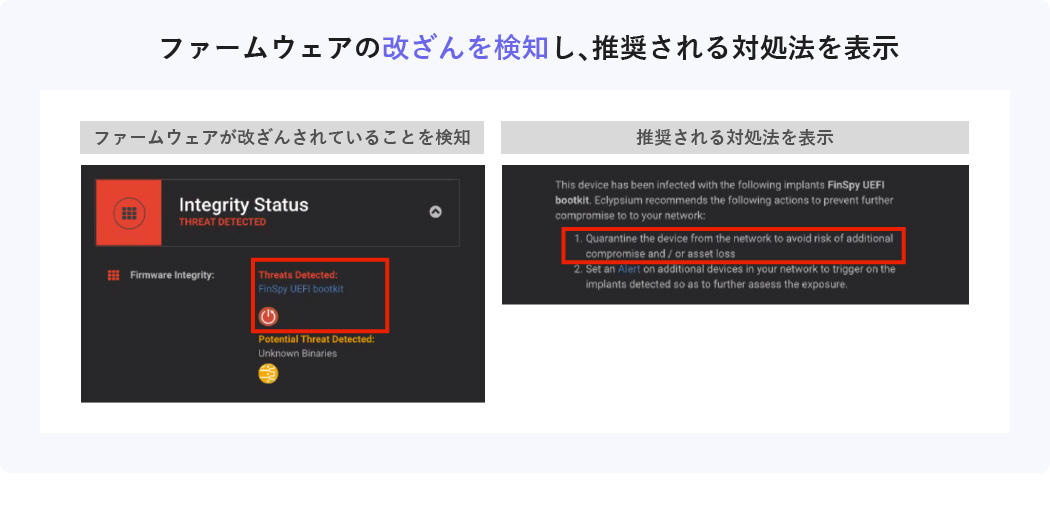
Features of Eclypsium 2 Detection of falsification
If the firmware has been tampered with or attacked, it will detect the tampering and display recommended countermeasures.
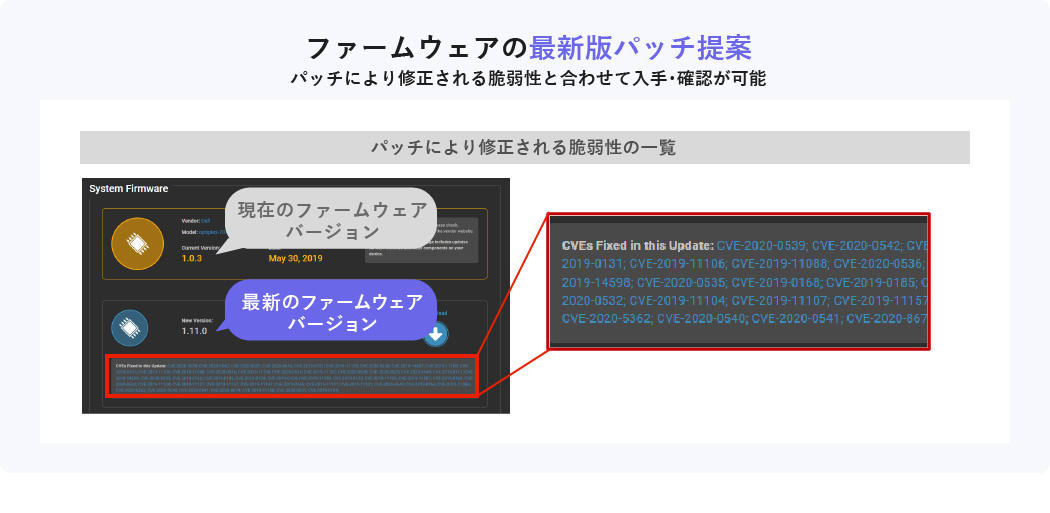
Features of Eclypsium 3 Proposal of the latest patch
You can propose the latest patch for the firmware where the vulnerability is found, obtain it from the Eclypsium screen, or apply it directly to the terminal/server. You can also check the vulnerabilities fixed by patches, so you can use the information to determine the priority of patches to be applied.
Free diagnostic service now available!
With our free diagnosis service, we will install an agent on the device provided by the customer and diagnose the firmware. All you have to do is prepare the equipment to be diagnosed. After the diagnosis, we will give you a report that includes the presence or absence of tampering, the degree of risk of vulnerability, and the priority of response.
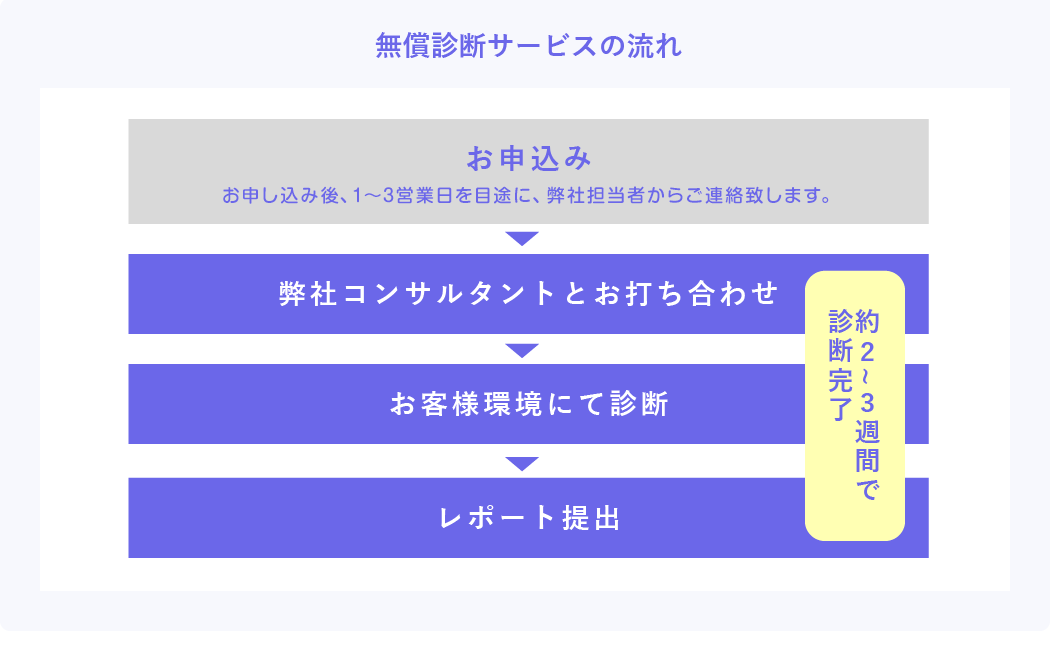
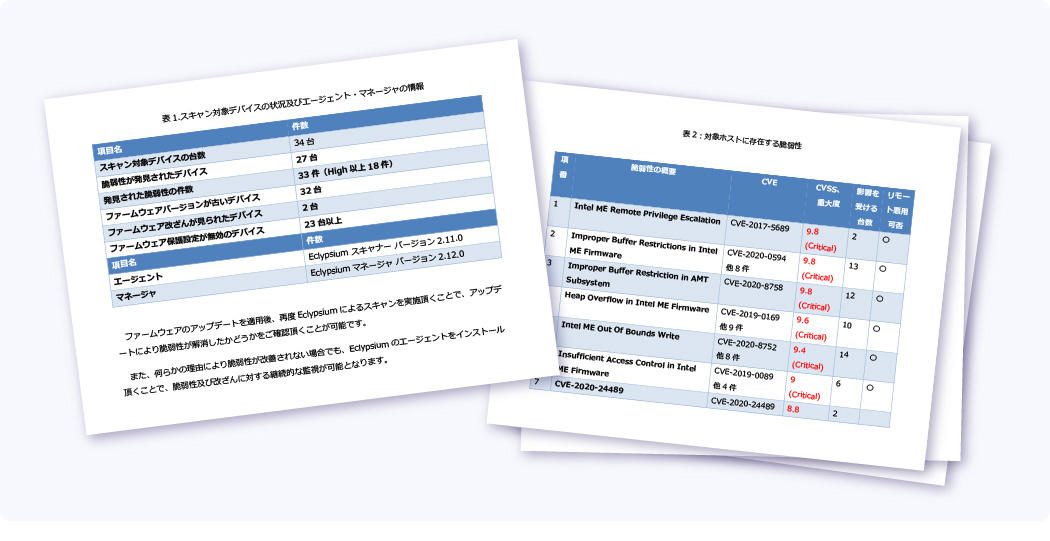
* Distribute the agent to the customer and perform the diagnosis.
*With the free diagnosis service, up to 10 devices can be diagnosed.