product
- About Cato Networks
- About Cato SASE Cloud
- Unification of shadow IT countermeasures by Cato CASB,
- Information leakage countermeasures with Cato Smart DLP
- Safe website browsing with Cato RBI
- CATO socket Easily connect existing LAN environment to SASE. Migration to SASE made easy
- Cato SASE XDR
- Cato DEM(Digital Experience Monitoring)
service
Application for evaluation machine
- FAQ

Cato Networks
Cato Networks
Cato CASB (Cloud Access Security Broker)
Increasing use of cloud in digital transformation and countermeasures against shadow IT
Corporate applications are migrating to the cloud environment due to corporate digital transformation, telework measures, etc. However, due to the spread of remote work, the number of cloud services that information system departments are not aware of is increasing further.
Cato SASE Cloud provides the fastest and easiest CASB (Cloud Access Security Broker) solution to manage cloud service risk.
“CASB addresses the critical visibility and control created by an organization's migration to the cloud, but must be integrated into the global SASE platform to be truly effective across the business,” said Cato Networks. Co-founder and CEO Shlomo Kramer)
By incorporating CASB into the Cato SPACE engine on the cloud, you can take advantage of the strengths of the Cato SASE Cloud: global access bases, abundant system information, cloud scalability and self-healing/maintenance functions. Cato CASB is quick to deploy, easy to operate, and provides visibility into cybersecurity risks.
CatoCASB demo video (5 minutes): Instant access to the CatoCASB menu from the easy-to-use CatoSASE cloud portal.
4 steps to manage cloud application risk
Cato SASE Cloud supports all four stages (Visibility, Assessment, Prevention, and Protection) for managing data risk in cloud applications.
1. Visualization: New Shadow IT Dashboard
Cato traditionally has a shadow IT dashboard that lists the total number of risky applications, the list of the most risky applications, the number of users accessing them, and the total traffic usage including distribution by risk. Deployed in the SASE admin portal from.
There is no need for additional installation of gateway devices or user agents for data transmission and reception for CASB. If you apply for Cato CASB, you can immediately use Cato CASB functions by simply turning on the button from the CATO SASE cloud management menu.
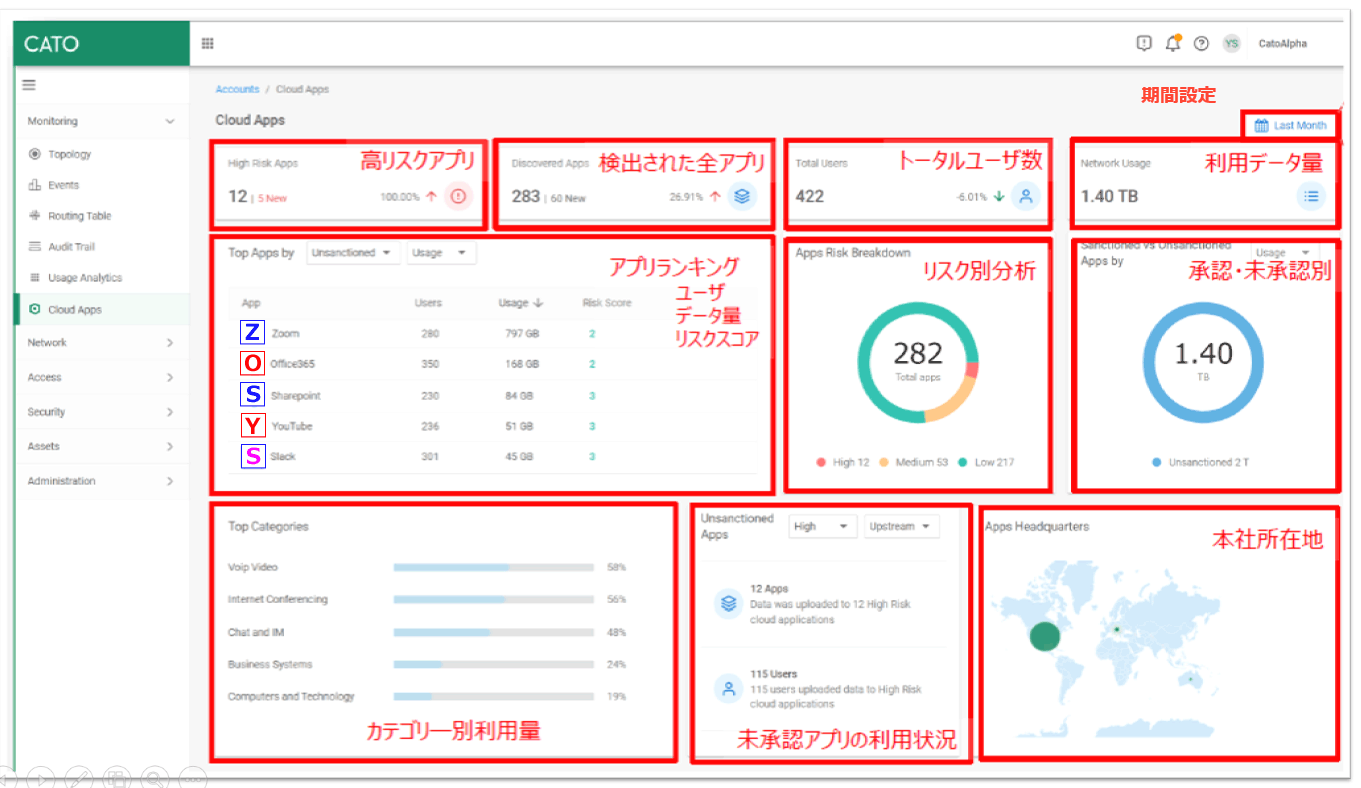
Shadow IT Dashboard: Enterprises can get a snapshot of the status of sanctioned and unsanctioned applications.
2. Rating: Cato Application Trust Engine (ACE)
Once an unsanctioned application has been identified, IT leaders should assess the risk before deciding whether it should be blocked, controlled, or allowed.
Cato CASB has built its own Application Credibility Engine (ACE - Application Credibility Evaluator) that automates data collection from multiple sources and enables fast and accurate evaluation of each application. Three metrics are aggregated for comprehensive analysis (general enterprise information, compliance readiness information, and security readiness information).
Analyzing real-world applications as they appear on the network are machine learning algorithms that operate against Cato's vast data lakeflow metadata. Cato's regulatory compliance validations currently include HIPAA, PCI, and SOC 1-3. Validation of security features includes multi-factor authentication, encryption of data at rest, and SSO.
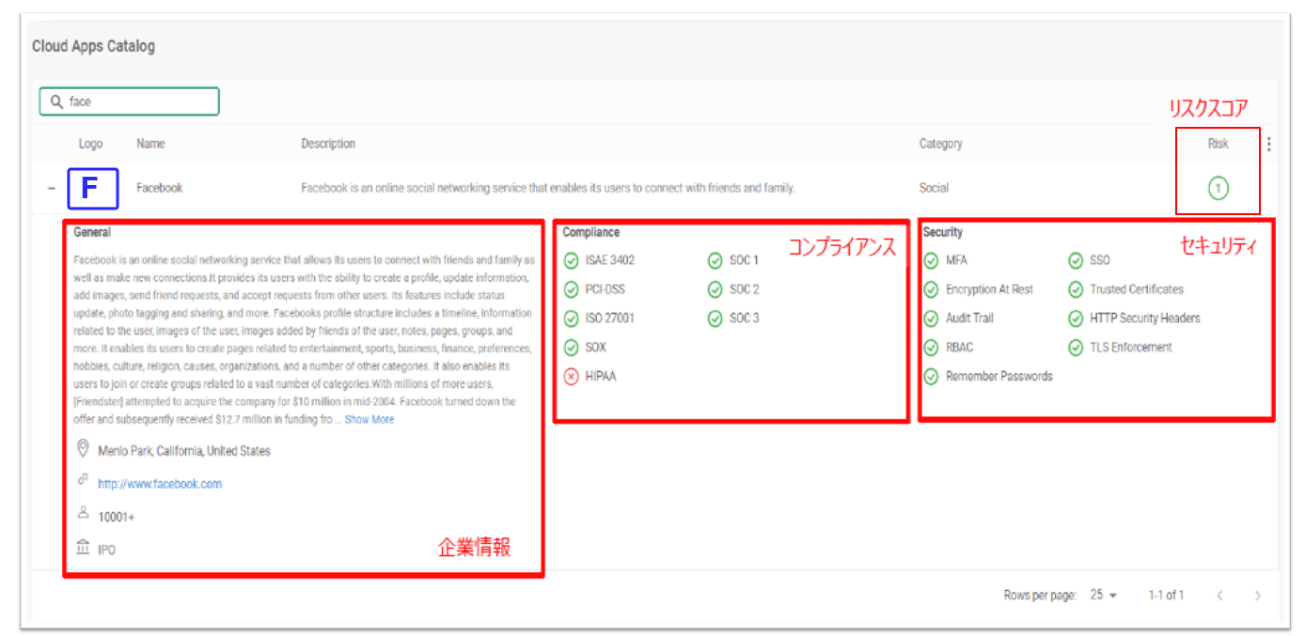
Cloud Application Catalog: Uses Cato's ACE data mining to provide continuously and automatically updated corporate, compliance and security readiness information for all applications.
3. Control: Define access policies with Cato CASB rules
After discovering rogue applications on the network and assessing the risks, IT leaders must decide how to respond. Cato CASB gives you granular access on your applications. A rule allows you to define the matching conditions, the specified action to take when the rule is applied, the associated severity level, and whether to generate an alert or event.
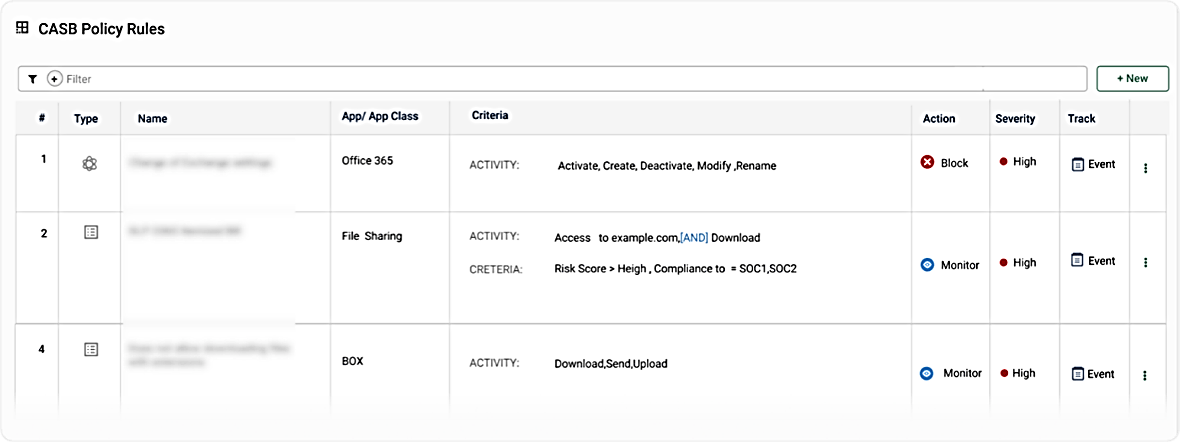
Cato CASB Policy Rules View: Allows granular control of applications across the enterprise
4. Defend: Cato detects and blocks threats and breaches.
The final step is to ensure that SaaS usage is protected. This can be achieved by integrating the security tools of the Cato SASE Cloud.
All SaaS traffic is handled by multiple security tools: Next-Generation Firewall (NGFW), Security Web Gateway (SWG), Intrusion Prevention System* (IPS), and Next-Generation Anti-Malware* (NGAM). Together, these tools provide comprehensive protection from a wide range of threats. *option
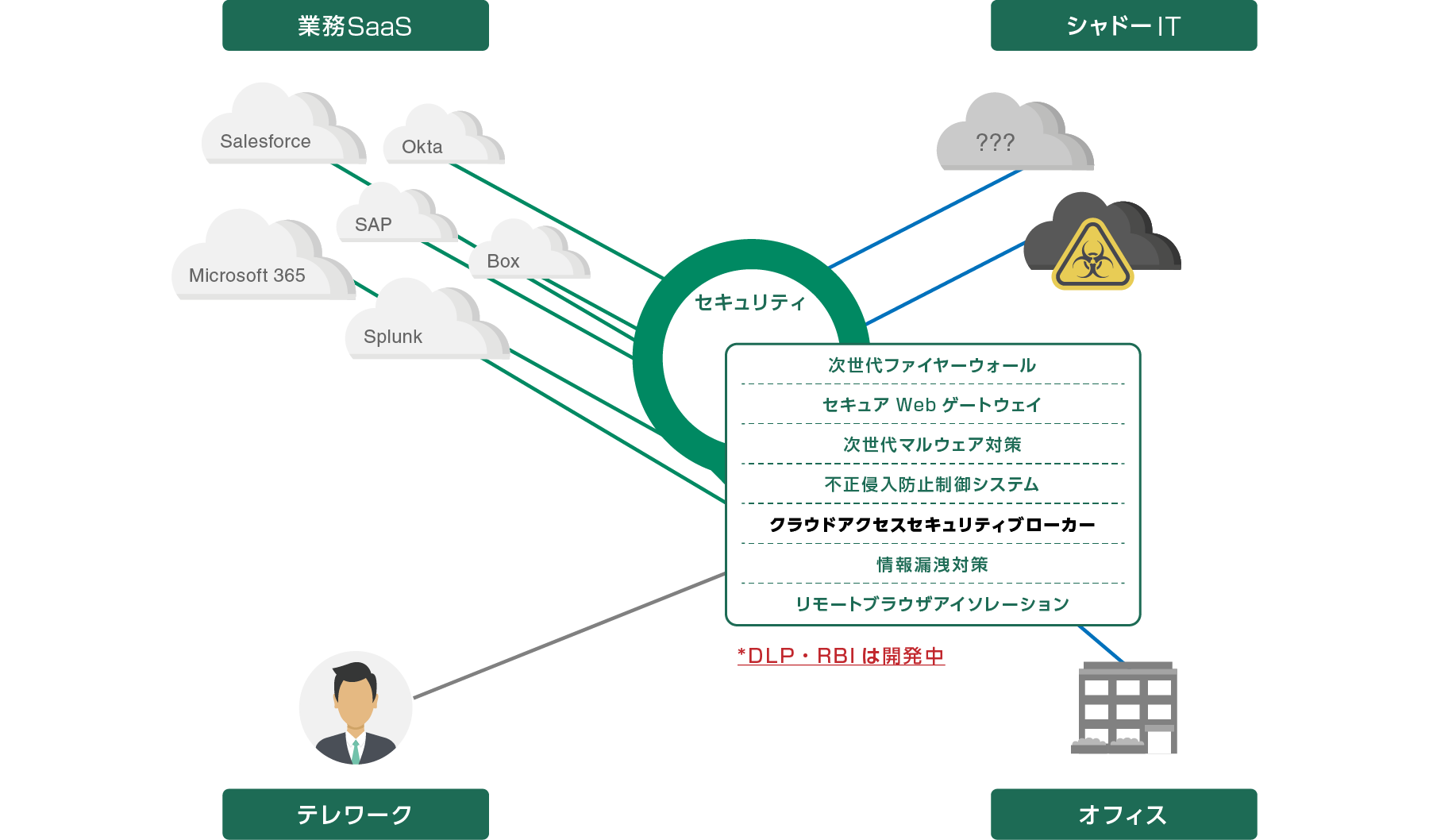
Advantages of Cato CASB
Cato CASB brings the benefits of a true SASE platform into your cloud application risk management practices. Traditional stand-alone CASB solutions require extensive planning and build times of months. Cato CASB, on the other hand, is built into the functionality of SASE, so there is no need for data acquisition servers, equipment, or connection settings, and you can immediately use the ability to fully visualize and control access to cloud applications. .
As part of the Cato SASE cloud, Cato CASB can be used from any location, such as data centers or mobiles, via over 70 PoPs around the world. Since the SDP/ZTNA function is also implemented, shadow IT countermeasures for telework employees from their homes are also possible at the same time.
With this wide range of service deployment, corporate policies can be centrally managed for all cloud access, even when cloud applications are accessed by overseas offices or group companies. The coverage of legacy CASB solutions varies in implementation depending on location and available functionality.
And Cato CASB can leverage the full power of Cato SASE Cloud 's multi-layered threat defense. Cloud-based file access is inspected by Cato's advanced next-generation anti-malware* and IPS* (intrusion prevention system) engines. Access control to locations and information resources is restricted through Cato Next Generation Firewalls (NGFW) and Security Web Gateways (SWG). With conventional CASB, all these components must be combined with other vendors and additional functions must be added, requiring connection work, verification, and construction work. *option
| Standalone CASB | Cato built-in CASB | |
| Build/Introduce |
long and complex CASB projects require network mapping and planning to ensure all use cases are covered. |
fast and simple No planning, network changes, deployments or configurations are required to enable CASB for Cato. Once the CASB feature is enabled, it can be implemented immediately with no additional learning period required. |
| Scope of big data for inspection |
Partial Usually only internal information such as communication history logs. |
all Gain rich insights from various SaaS data and all protocol and network security features as part of a complete SASE service. |
| Application coverage |
Narrow Usually, SaaS is the main, and IaaS is limited. |
wide For all SaaS, IaaS and WAN usage. |
| Granularity in inline mode implementation |
low Granularity in inline mode is coarser, higher granularity application must use APIs in out-of-band mode, real-time protection is not possible. |
high Even in inline mode, very detailed rules are available. |
Inquiry/Document request
Macnica Cato Networks
- TEL:045-476-2010
- E-mail:cato-sales@macnica.co.jp
Weekdays: 9:00-17:00


