
Symantec製品
シマンテック製品
Zero Trust Network Access(ZTNA)侵入起点となるVPNを次世代のリモートアクセスへ

Zero Trust Network Access(ZTNA)とは、文字通りゼロトラストのネットワークアクセスで、ゼロトラストの基本原則である「何も信用しない」を実現しながら、ネットワークアクセスを実現します。これまではVPNを使用したリモートアクセスが主流でした。
特にコロナ渦中の2020年ごろに急速に普及し、これまで一部の従業員の利用のみだったのが全従業員がVPNを利用して社内システムにアクセスするようになると、もともとVPNの仕様上負荷が上がりやすいという問題があり、接続不良や遅延などの問題が発生しました。
セキュリティ面においてもVPN製品自体の脆弱性を狙った攻撃等も発生し、外部の攻撃者によるVPN経由での侵入を許すとすべての社内リソースにアクセスが可能になり大きなインシデントにつながります。
また、これまでマルウェアの侵入経路はWeb、メールが中心でした。昨今ではVPNからの侵入が6~8割を超えています。そのためVPNからZTNAに置換える企業も増えてきています。ZTNAの場合は、ポリシーに従い適切にユーザ毎のアクセス権に基づきアクセス可能なサービスやリソースに対して設計することができます。これによりVPNとは異なり社内リソースすべてにアクセス可能ということはなくなり、リスクの低減が望めます。
また、ZTNAはクラウド上で展開されており負荷の問題も解決しつつ、ZTNAのクラウドでリバースプロキシのように動作するため、直接社内のリソースにはアクセスできない構造のためより強固なセキュリティを実現します。
SymantecのZTNAの特徴
- Software Defined P erimeter(SDP)
- 柔軟なアクセス制限
Software Defined Perimeter(SDP)
ネットワークの境界(Perimeter)をソフトウェアによって仮想的・動的に構成する技術のことで、ソフトウェア上でユーザとアクセスするリソースとの間に1対1のネットワーク接続を動的に作成することを実現します。
また、通信確立のたびに認証を行い通信が終了すると、接続要求がない限り接続を再開しません。この仕組みはゼロトラストの原則に基づくものであり、境界線防御という概念がないゼロトラストにおいてもセキュアなネットワークを提供します。具体的には、サーバスキャン、DoS、オペレーティングシステムとアプリケーションの脆弱性の悪用などの攻撃に対して有効です。
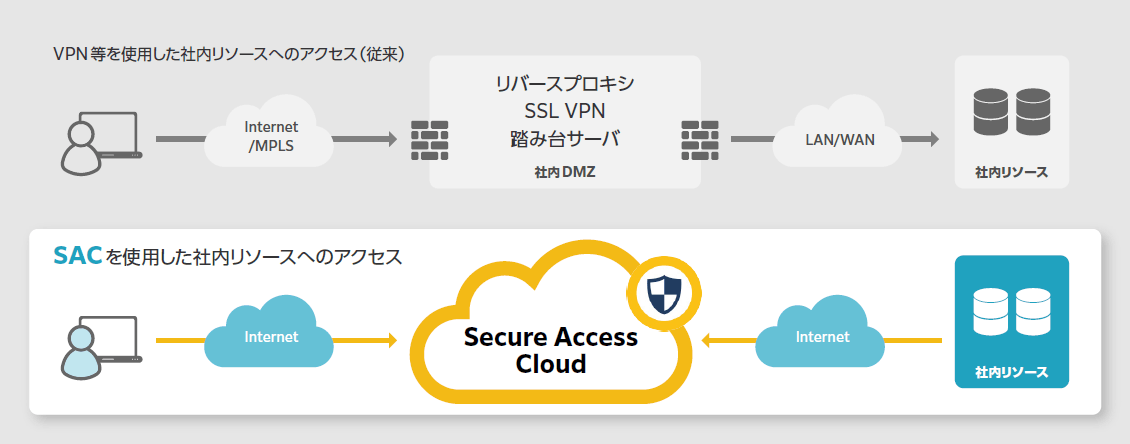
SymantecのZTNAでもSDPを採用しており、セキュアなネットワークを提供します。具体的にはZTNAを提供しているクラウドアプリケーションがリバースプロキシとして動作し、社内リソースやAWS、GCPなどのIaaSにDocker上で動作するコネクタを配備することにより実現します。
利用者はZTNAのクラウドアプリケーションにアクセスするとアクセス権に従い、社内リソースに安全にアクセスすることが可能です。また、ZTNA経由で社内リソースにアクセスした際の詳細なアクセスログも確認することが可能なため、何か問題が発生した場合においても調査を容易に行えます。
柔軟なアクセス制限
従来のVPN を用いたリモートアクセスでは柔軟なアクセス制限を行うことは難しく、1 度接続すれば社内リソースを自由にアクセスできることが可能でした。逆に言えば悪意のある攻撃者がVPN のアカウントを不正に入手し、なりすましした場合にはすべての社内リソースにアクセスできてしまいます。Symantec のZTNA では、ユーザ、サイト( コネクタの設置場所)、Application(個別の社内リソース)の3 要素を柔軟に組み合わせることにより、従業員に対して適切なアクセス権を与えることができます。また、エージェントレスでもZTNA を提供することは可能で、「HTTPS」「SSH」「RDP over HTTPS」「TCP over SSH」のプロトコルに対応しています。
エージェントを使用した場合は、プロトコルに依存することなくリソースにアクセス可能になります。このようにエージェントの有り無しにより動作が異なるため、委託会社や派遣社員などの外部の社員へのアクセス権に対しても柔軟に設計が可能です。
メンテナンス等で一時的に特定のリソースに対してリモートアクセスを許可したいといった場合でも、柔軟かつに安全にアクセス権を与えることも可能です。
資料の続きは、下記ボタンよりダウンロードください。


お問い合わせ・資料請求
株式会社マクニカ Symantec 担当
- TEL:045-476-2010
- E-mail:symantec-sales@macnica.co.jp
平日 9:00~17:00