product
- Web Protection Suite(SWG)
- Symantec Cloud SOC (CASB)
- Symantec Zero Trust Network Access(ZTNA)
- Symantec Endpoint Security(EPP・EDR)
- Symantec Email Security.cloud (Email Security)
- Symantec Ghost Solution Suite (kitting tool)
- SSL Visibility Appliance (SSL Composite)
- Macnica Cloud Security Security Package
- Other services/product information
Specifications/Technical Information

Symantec products
symantec products
Cloud Access Security Broker (CASB) Achieving secure cloud service usage

Cloud Access Security Broker (CASB) is a solution that enables users to use the Internet safely by realizing visualization, data protection, and governance of cloud services that are everywhere on the Internet. In addition, it can be divided into two functions: security measures for cloud services used by employees with which companies do not have contracts, called shadow IT, and security measures for cloud services that companies have contracts, called Sanctioned IT. .
Key features of Symantec's CASB
| function | detail |
| Shadow IT countermeasures |
|
| Sanction IT measures |
|
Shadow IT countermeasures
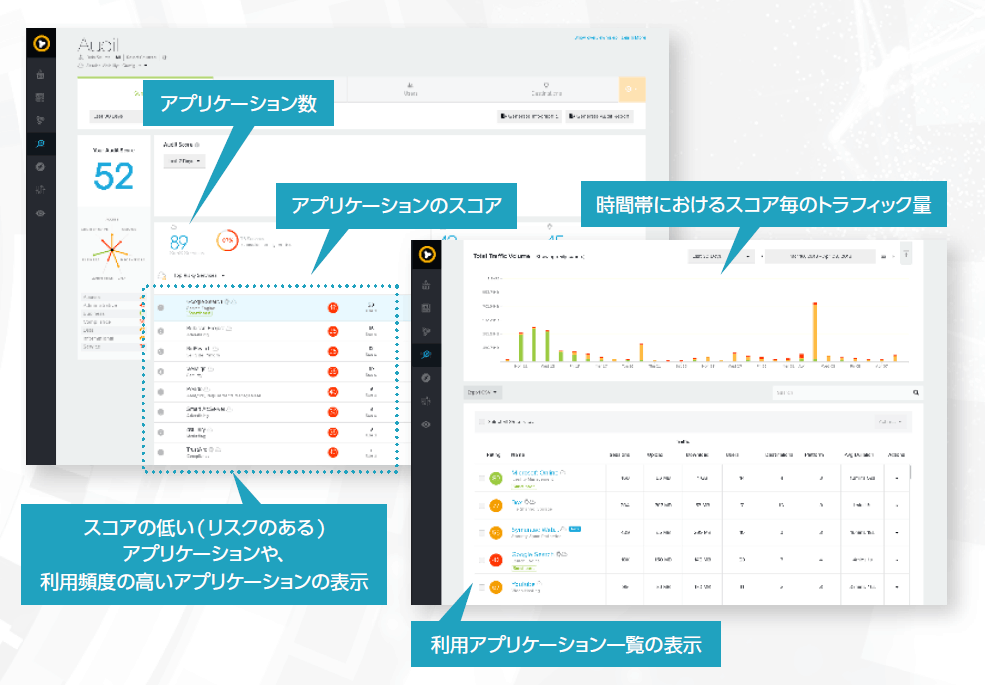
Visualization and evaluation of cloud application usage status
Risky cloud applications cannot be detected by web content filtering security categories. This is because a risky cloud service is not one that is deployed with malicious intent, but rather one that has insufficient supported authentication methods (SAML or multi-factor), unencrypted data, no backups, and no safe harbor rules. This is because it refers to vulnerable cloud services such as maintenance services.
Attackers target vulnerable cloud services themselves to acquire and destroy important corporate data. Therefore, it is necessary to visualize and evaluate the usage status of cloud applications and to limit the use of risky clouds.
Symantec's CASB is based on over 60 factors and seven categories: "Service," "Access," "Management," "Business," "Compliance," "Data," and "App Information." We score cloud applications based on various factors such as SSL protocol/cipher strength, file sharing, backup availability, ISO 27001 certification, safe harbor, SLA availability, etc. By linking with SWG's access logs, you can visualize the usage status and risks of cloud applications used by employees. The most important thing for visualizing the usage status and risks of cloud applications is how many cloud services are covered.
Symantec currently covers more than 40,000 cloud services compared to other companies' products. You can also request that cloud services that are not supported be supported.
Security assessment of cloud applications

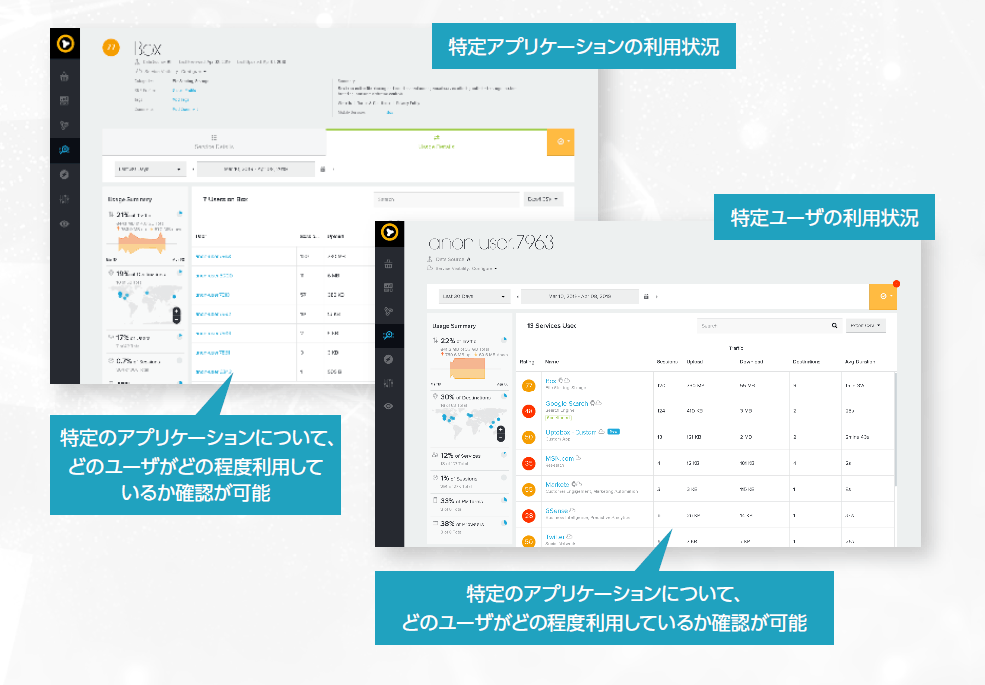
If an employee requests to use a cloud application that the company has prohibited, or if there is a request to use a cloud application that poses a risk, IT personnel cannot determine the risk. I think it will probably be banned. Appropriate use of cloud applications can improve employee productivity, so it is desirable to provide guidance on alternative services, but the reality is that it is not possible to actually judge the risks of cloud applications.
Symantec has the ability to investigate the evaluation results of cloud applications requested from the URL and the scores of multiple similar cloud applications, so if there is an application to use a risky cloud application, we will check the evaluation results of the cloud applications that have been applied for from the URL. You can guide your employees to secure cloud applications.
Realization of reliable web access control in cooperation with SWG
Even if shadow IT risks are properly visualized, the risk reduction effect will be diminished if appropriate controls are not implemented. Therefore, control through collaboration with SWG is required.
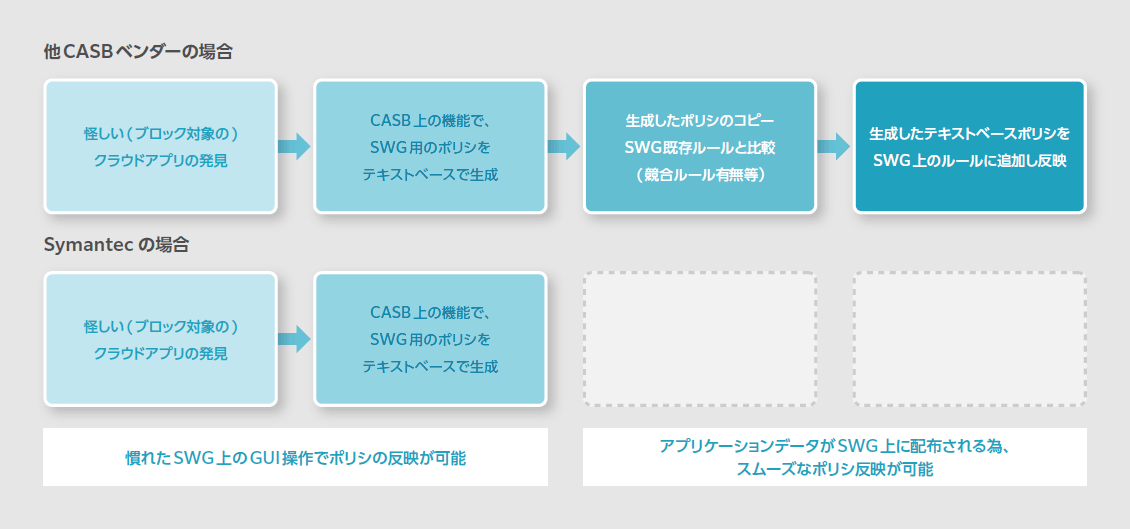
If the functions of CASB and SWG are not linked, or if the system is constructed using CASB and SWG by different vendors, you may need to go to ``Discover cloud applications to be blocked'' → ``With the functions on CASB, "Generate a text-based policy" → "Copy the generated policy and compare it with existing rules in SWG (existence of conflicting rules, etc.)" → "Add the generated text-based policy to the rules on SWG and reflect it" Is required.
In Symantec products, it is possible to link SWG and CASB, so if you "discover a cloud application to be blocked" → "check the cloud application to be blocked on the SWG GUI and reflect the policy", the application data of CASB will be transferred to SWG. Because it is distributed above, it is possible to smoothly reflect the policy.
Sanctioned IT measures
Visualize and control shadow data
Sanctioned IT visualizes whether employees are using the cloud services contracted by the company appropriately and takes control if inappropriate usage occurs.
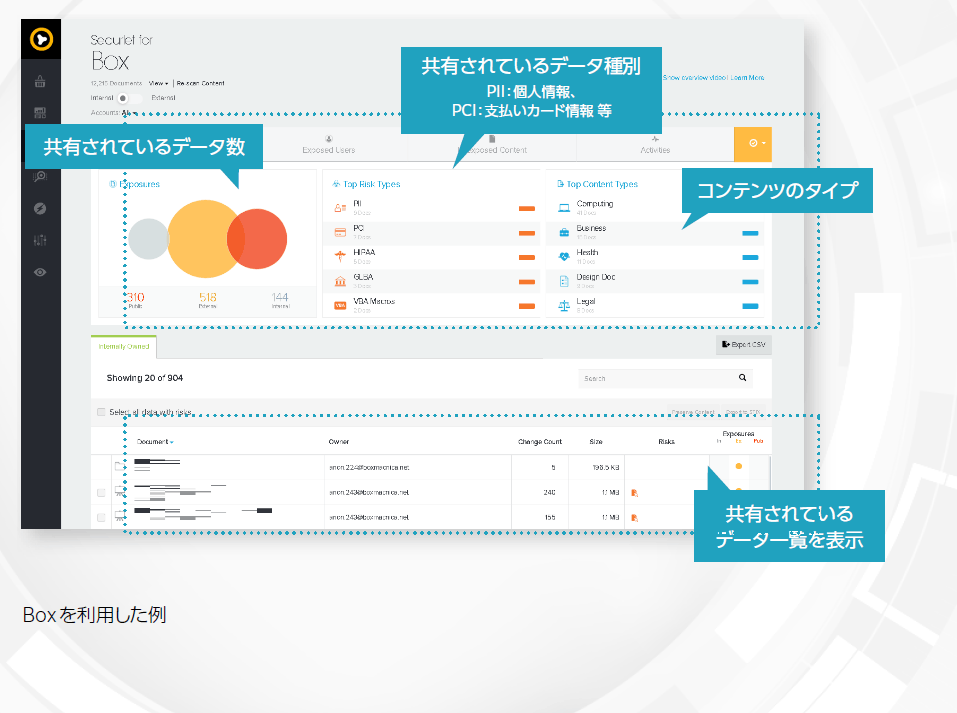
If cloud applications are operated inappropriately, there is a risk of important data being leaked (e.g., due to impersonation using malware), regardless of whether the employee's actions were intentional or not. At Symantec, we link CASB and cloud applications using APIs to achieve visualization and control. In the case of storage services such as BOX and SharePoint, it is possible to visualize data shared externally and internally.
Specifically, it not only graphically visualizes the number of shared data, the type of shared data, the content type, and the list of shared data, but also displays detailed information such as the data owner and size. Detailed information such as scan result details, presence or absence of shared links, and confirmation of access rights for shared links are also visualized.
With email services available in Microsoft 365, it is possible to visualize data attached to external emails, including details such as the sender address and subject, and details of data scan results (scan date and time, data type, etc.). ), confirmation of destination address, etc. can be visualized.
In addition, rules can be created using various visualized items, and manual or automatic control can be performed if usage is not in accordance with company regulations.
For example, you can create rules such as automatically deleting files when personal information that is prohibited to upload is uploaded to a cloud application, or when credit card information is uploaded and made public via a shared link. Controls such as deleting shared links are possible if conditions are met.
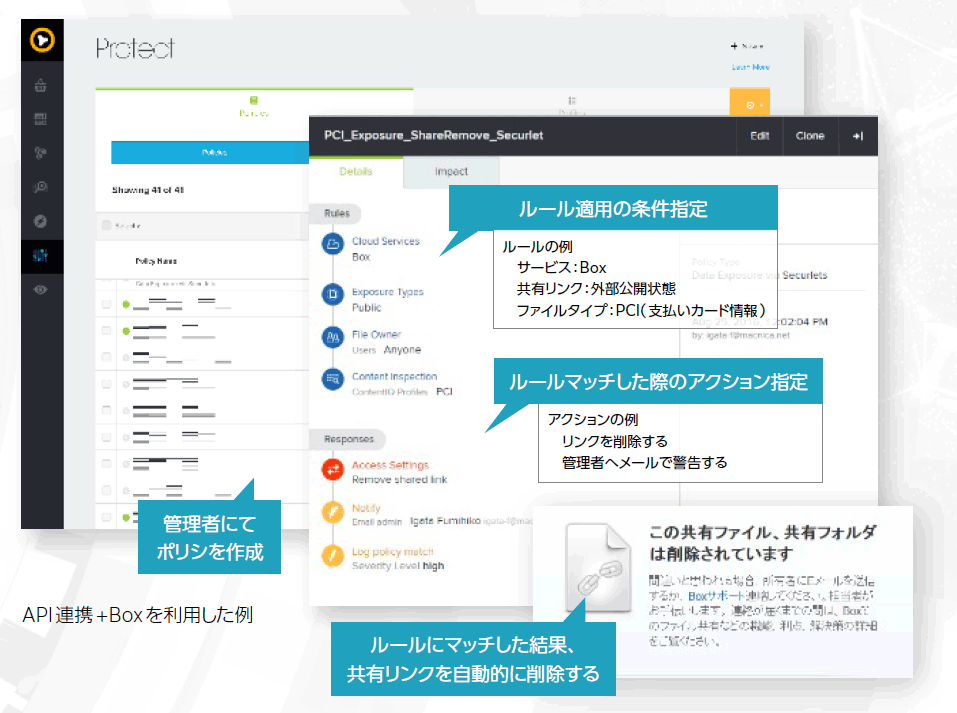
Data protection using DLP features
IT personnel need to know whether important data is being properly stored in cloud applications and whether it has been shared or exposed to external parties. However, it is not practical to open every file and determine whether it contains important data.
Symantec uses DLP technology to automatically detect whether files stored in cloud applications are important or not. Specifically, we can detect content types: FERPA, GLBA, HIPAA, PCI, PII, Business, Computing, Cryptographic Keys, Design, Encryption, Engineering, Medical, Legal, and Source Code.
File types include animation, communication, database, publishing, encapsulation, and executable files. You can also manually register blacklists/whitelists.
User behavior detection using thresholds and machine learning
In recent security, there is an increasing trend in the use of cloud applications by employees who commit internal fraud or who obtain important data for targeted attacks. To detect such risks, it is necessary to monitor employee behavior on cloud applications. This type of fraudulent behavior is difficult to detect without a system in place.
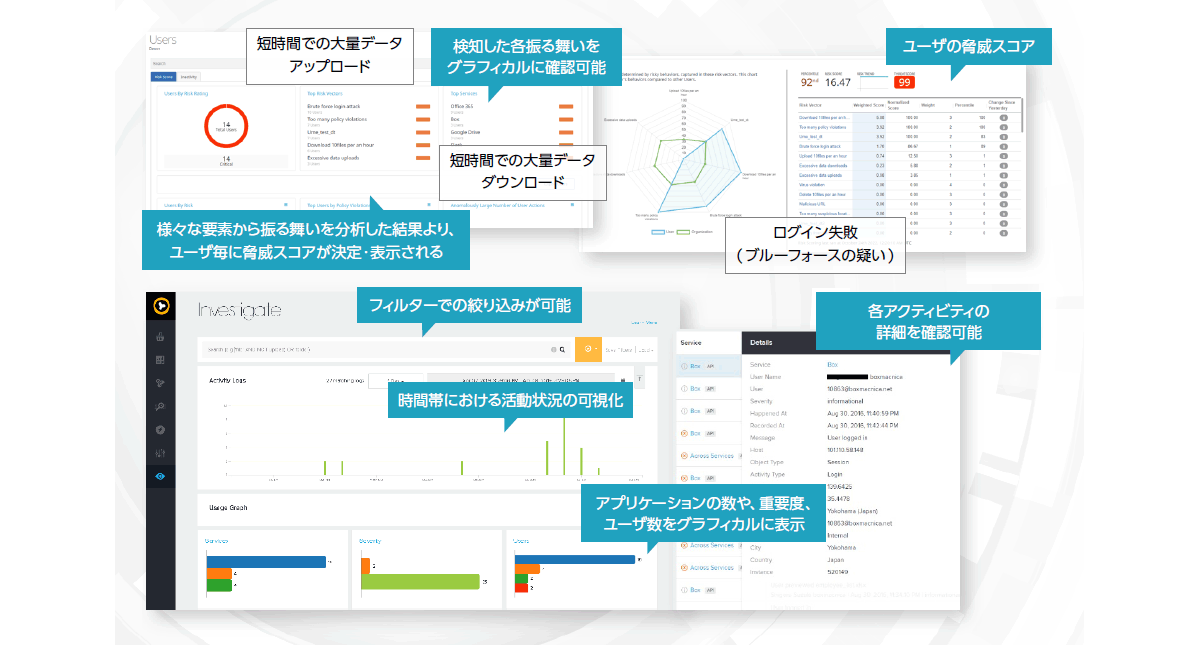
Symantec has a UBA (User Behavior Analytics) function that uses machine learning to internally create employee behavior models and detect information leakage risks when users behave in a manner that may lead to data leakage. It is possible to.
Additionally, each risky employee behavior is assigned a risk score, and each employee's malicious behavior determines the threat score, making it easier for IT professionals to identify at-risk employees. Become.
In addition, since not only risky behavior but also employee behavior is recorded, it is possible to check both risky behavior and normal behavior, making it easier to monitor behavior.
Cloud application control using SWG collaboration
So far, we have explained that various functions are effective for Sanctioned IT countermeasures by linking cloud applications and CASB via API, but there are also disadvantages to API linkage. In the case of API linkage, it only works from the stage when the file is actually saved in the cloud application. In other words, real-time performance becomes weaker.
By working with SWG, Symantec can perform real-time processing such as stopping a file before it is saved to a cloud application if it meets the conditions of a detection rule.
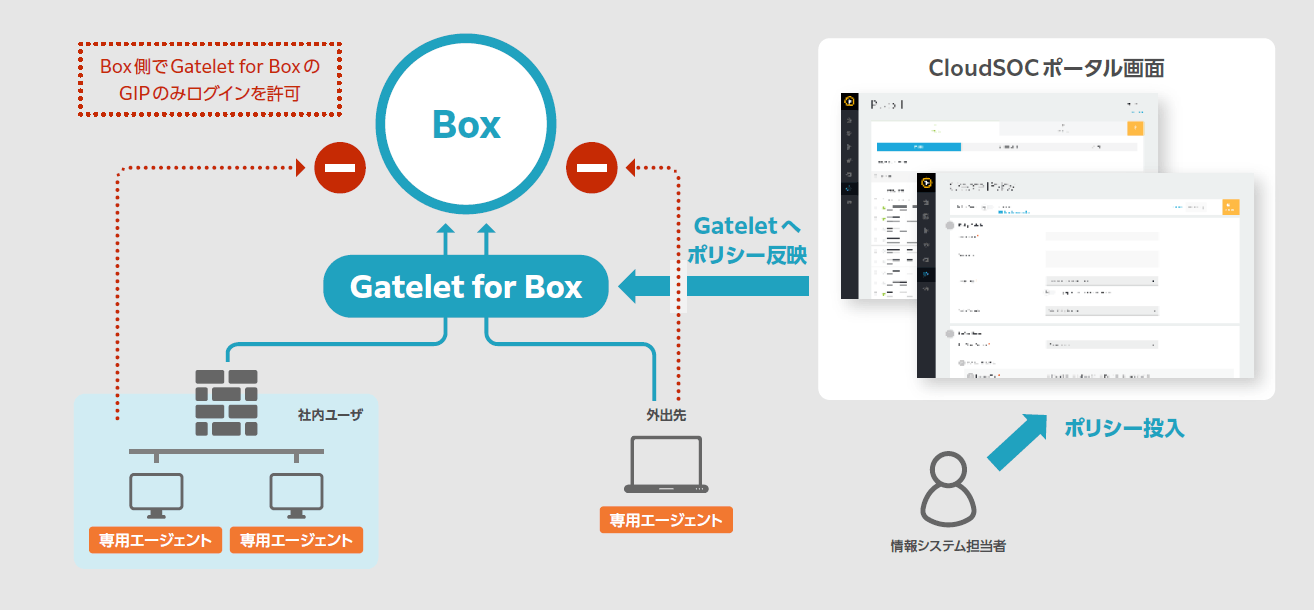
Please download the rest of the document by clicking the button below.


Inquiry/Document request
In charge of Macnica Symantec Co., Ltd.
- TEL:045-476-2010
- E-mail:symantec-sales@macnica.co.jp
Weekdays: 9:00-17:00