
Symantec製品
シマンテック製品
SSEとは何か?SASEとの違いから導入ステップを解説

本書では、ゼロトラストに取り組む多くの企業で質問の多い「SSE」を徹底解説致します。
「SSE とは何か?」「エンドポイントや認証系のセキュリティは実施しているが次のステップが不明」、「SWG、CASB、ZTNAという用語を改めて理解したい」「各製品の選定ポイントを理解したい」といった疑問に対する解をお届けします。
ゼロトラストの基本
本題に入る前に、ゼロトラストのコンセプトや境界防御との違いをご紹介します。
ファイアウォールを中心とする従来型の境界防御は、「Trustbut Verify(信ぜよ、されど確認せよ)」が基本的なコンセプトでした。一度境界内部へのアクセスが許可されると、その後、通信の継続的なチェックは行われず、社内のデータ・リソースへ容易にアクセスが可能となってしまいます。
一方、ゼロトラストは「Never Trust, Always Verify(決して信頼せず、必ず確認せよ)」を原則とし、リソースにアクセスする際は常に明示的な検証を求めるのが特徴です。アクセスを許可する範囲は最小限にとどめ、一度アクセスを許可した後も、決して信頼せず、通信元の信頼性をさまざまな角度から検証し続ける非常に厳格なセキュリティコンセプトだといえます。
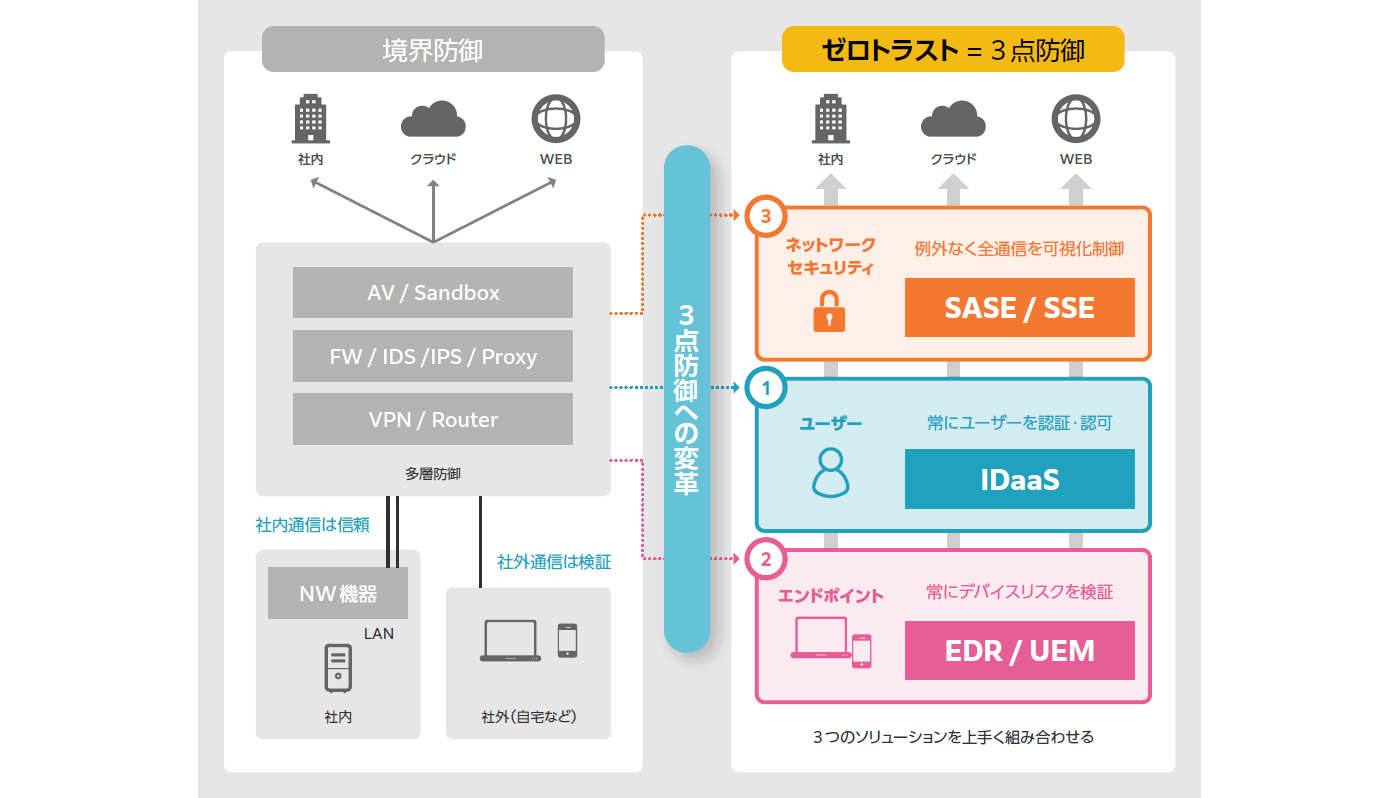
ゼロトラストを実現するためには、これまでの「境界型防御」から「3点防御」への変革が必要となります。
3点防御とは、ユーザがデバイスを使って社内リソースやクラウドサービス、インターネットにアクセスしようとした際に、以下の3つの観点で検証を行うことです。
SASEとSSEの違い
ゼロトラストの中でもネットワークセキュリティを実現する重要な柱がSASE(Secure Access Service Edge)やSSE(Security Service E dge)です。
ゼロトラスト実現の柱:SASE
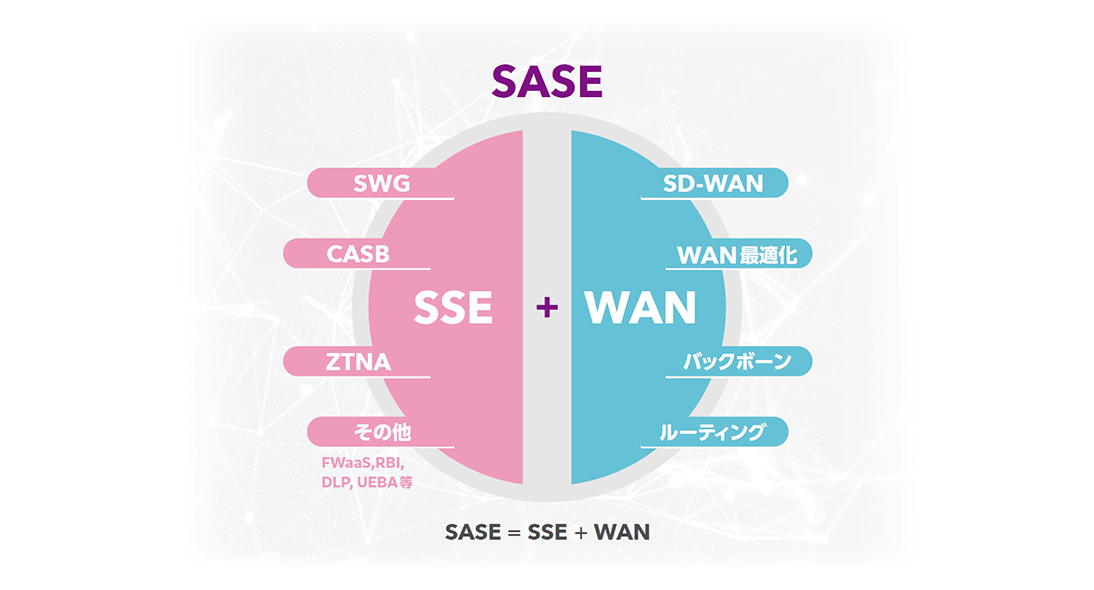
SASEはSecure Access Service Edgeの略で、「ネットワークサービス」と「セキュリティサービス」を1つのクラウドサービスに統合させるという、2019年に提唱された新たなネットワークセキュリティの概念です。「ネットワークサービス」と「セキュリティサービス」が切り離されている従来のデータセンタアーキテクチャとは対照的に、この2つを統合するクラウド提供のエコシステムがSASEです。
SASEを支えるセキュリティプラットホーム:SSE
SSE はSecurity Service Edgeの略で、SASEの一部です。具体的には、「セキュリティサービス」の統合を重点に置いているのはSSE部分です。
SSEは様々な統合されたテクノロジーを、クラウド上でセキュリティプラットホームを構築しユーザがどこにいても安全なネットワークを提供することが可能になります。
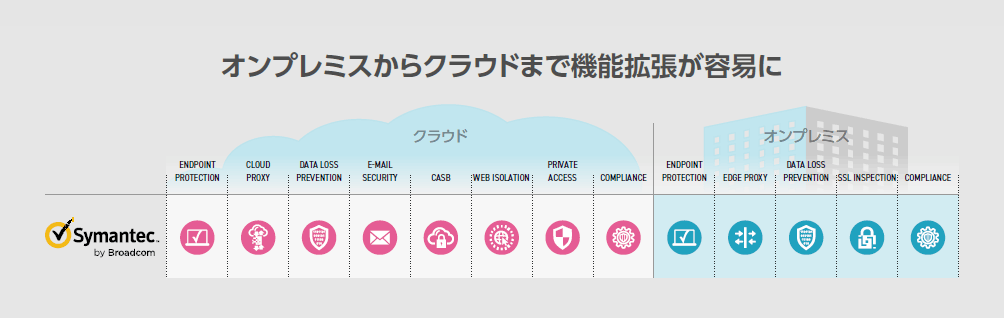
SSEプラットホームは、Secure Web Gateway(SWG)、CloudAccess Security Br oker(CASB)およびZero Trust NetworkAccess(ZTNA)の3つの主要なソリューションを統合することにより、包括的なセキュリティを提供します。
このようにしてそれぞれ、ユーザ、デバイス、データ、サービス、アプリケーションを保護できます。
この統合された包括的なセキュリティでITシステム全体のセキュリティが強化されると同時に、管理者の複雑な運用が軽減され、安全なネットワークの提供や高いユーザエクスペリエンス、運用コストの低減が実現できます。
SASE・SSE導入状況
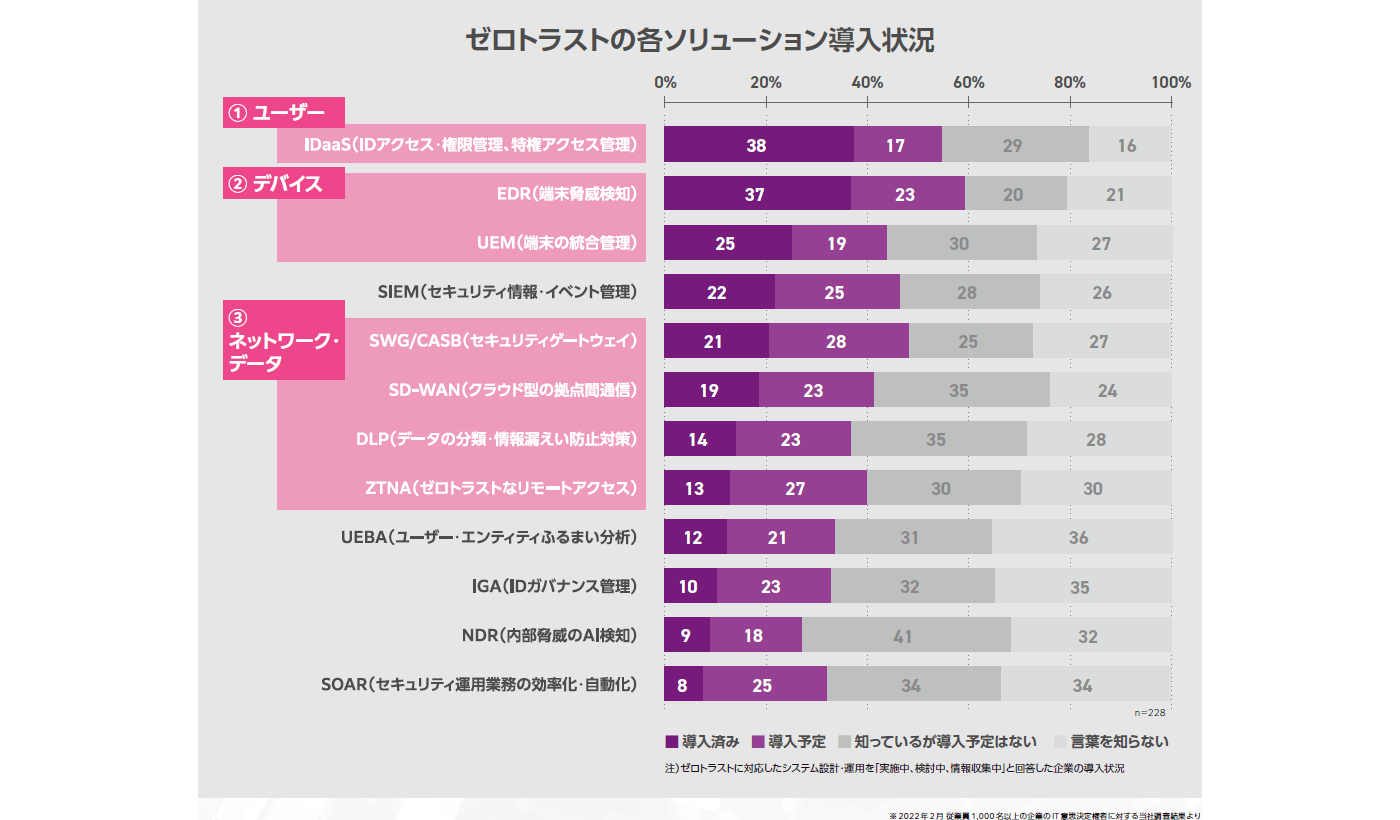
一方、IDaaS やEDRは導入済みだが、SASE やSSE領域の対策に取り組めていない企業も多いのではないでしょうか。
弊社が実施した従業員数 1000人以上の企業の IT導入の228名への調査において、「ゼロトラストに対応したシステム設計・運用を実施中、検討中、情報収集中」と答えた方の中で55%がIDaaSを導入済み・導入予定、60%がEDRを導入済み・導入予定と回答しているのに対して、SASEやSSE 領域の代表的なソリューションであるSWG・CASB は50%が導入済み・導入予定と答えています。
このようにIDaaSやEDRと比べても市場浸透率がまだ低い状況と言えます。次の章では、SSE の導入ステップや、SSEを構成するソリューションについて解説していきます。
SSEの導入ステップ
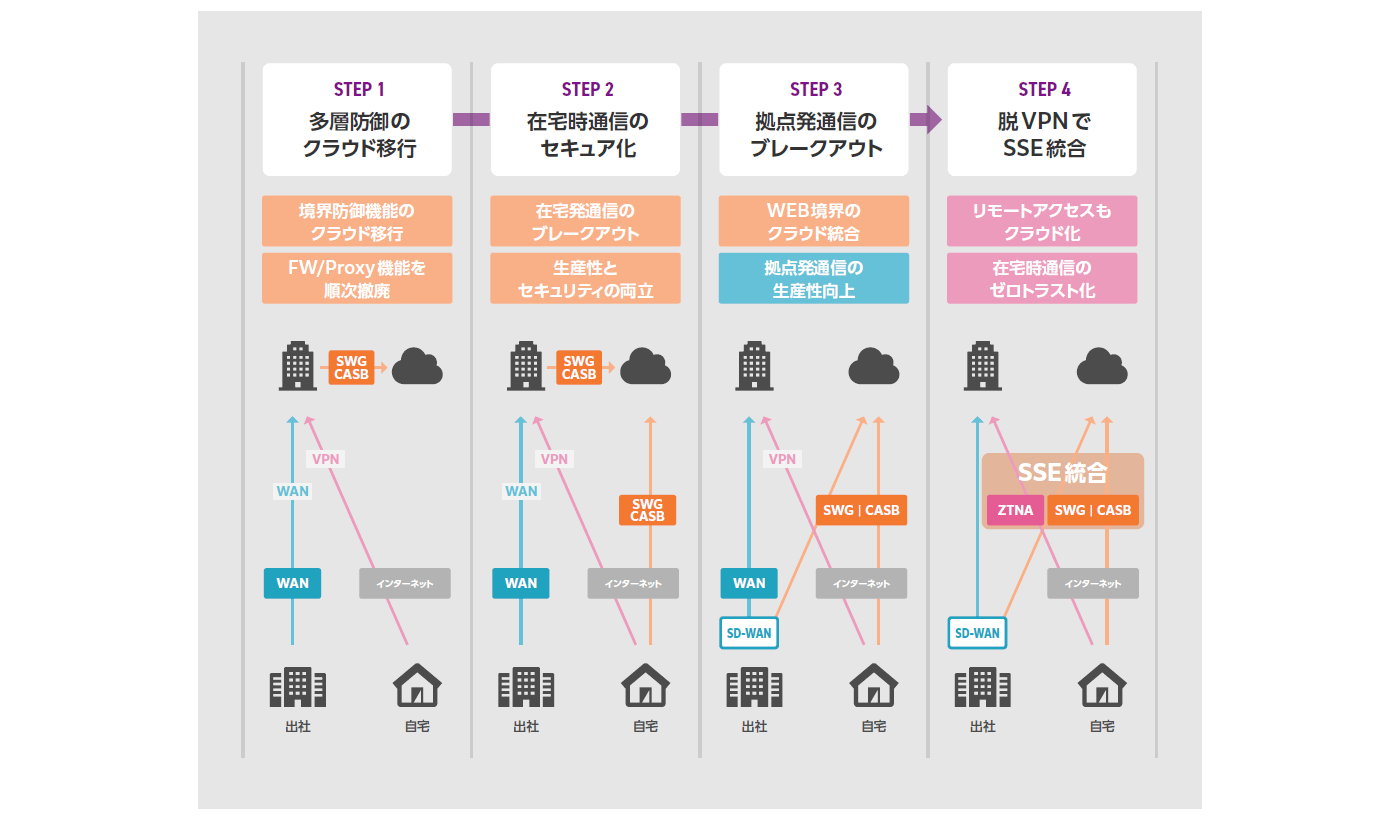
SSEを初期導入する場合には、SWG、CASB、ZTNAのすべてを構築することは難しいためSWG → CASB → ZTNAと下記のようなプロセスで段階的に導入することが一般的です。
- 従来から存在する典型的な脅威への対策として境界防御型で対応していたFirewall、プロキシ、アンチウィルス、サンドボックスをSWG へ移行。
- 近年大幅に増加しているSaaS サービスの増加に伴う脅威への対策としてCASB を導入。
- 従来は境界防御型のVPN で対応していたリモート環境(e.g., 在宅環境)からのアクセスをよりセキュアな接続方法であるZTNA へ移行。
SSEソリューション選定のポイント
One Vender でSSE を実現するリット
SSEプラットホームは、Secure Web Gateway(SWG)、CloudAccess Security Br oker(CASB)およびZero Trust NetworkAccess(ZTNA)のコンポーネントで構成されますが各コンポーネントを別のベンダーで構成することは可能です。ただし、One VenderでSSEを構成することのメリットについて知る必要があります。
One Venderであれば当然ながら容易に各コンポーネントの連携を行うことができるだけではなく、SSEとしての機能の重複や異なるポリシー設計思想などなく容易に設計・設定が行えます。また、何か動作上の問題等が発生した場合に、サポート問い合わせ先がわからないことが発生したり、ログの見方に一貫性がなかったり、最悪の場合には問題の擦り付け合いのようなことが発生し問題の長期化が想定されます。
世界最大規模脅威インテリジェンスネットワークを基にしたSymantecのSSE
IT業界に長く従事されている方であれば、Symantecのことはご存じの通りかと思いますが、長くセキュリティのトップランナーとしてセキュリティ業界をけん引してきました。現在ではBroadcom社のM&AによりSymantecはブランド名に代わりましたが、現在においてもキュリティのトップランナーであり、エンドポイントからクラウド、オンプレミスまで多くのセキュリティサービスを展開しています。
また、20年以上前からGlobal Intelligence Network(GIN)という世界最大規模の民間セキュリティ脅威インテリジェンスネットワークを有しており、現在では世界中で導入されているSymantec製品の1億7500万のエンドポイント、1億2600万以上の攻撃センサー、1億6000万人の電子メールアカウントユーザー、8000万のWeb プロキシからの情報を相関させています。さらに、90億ペタバイトを超すセキュリティデータを分析し、7500万件の悪意のある活動を分類し、1日に10億件ものセキュリティ要求を処理しています。
SASEにおける「セキュリティサービス」の統合を重点に置いているのがSSEですが、Symantec のSSEはGINで蓄積されたインテリジェンスが反映されており、よりセキュアなSSE環境を提供することが可能です。
次の章ではSymantec のSSEを中心に各コンポーネントおよび各機能について詳しく解説していきます。
資料の続きは、下記ボタンよりダウンロードください。


お問い合わせ・資料請求
株式会社マクニカ Symantec 担当
- TEL:045-476-2010
- E-mail:symantec-sales@macnica.co.jp
平日 9:00~17:00