web security
Web security provided by Macnica
In the past, many companies have introduced firewall, IPS, WAF, and DDoS countermeasure solutions as security for public services such as online services. On the other hand, in recent years, there has been an increase in threats that cannot be covered by conventional security, such as unauthorized logins by malicious bots, online fraud, web skimming, and phishing.
At Macnica, we offer a wide range of web security solutions that not only provide conventional countermeasures, but also take countermeasures against the latest threats mentioned above.
Traditional web application security
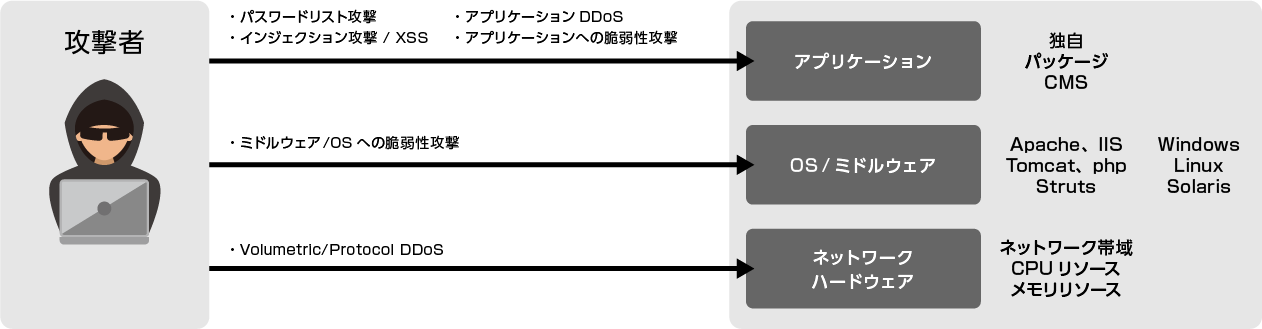
Mainly measures in three layers: (1) application, (2) OS/middleware, (3) network and hardware
Although there are changes in the form of provision, such as hardware type and cloud type, the basic contents have not changed for several years
Modern web application security
Characteristics of recent attacks
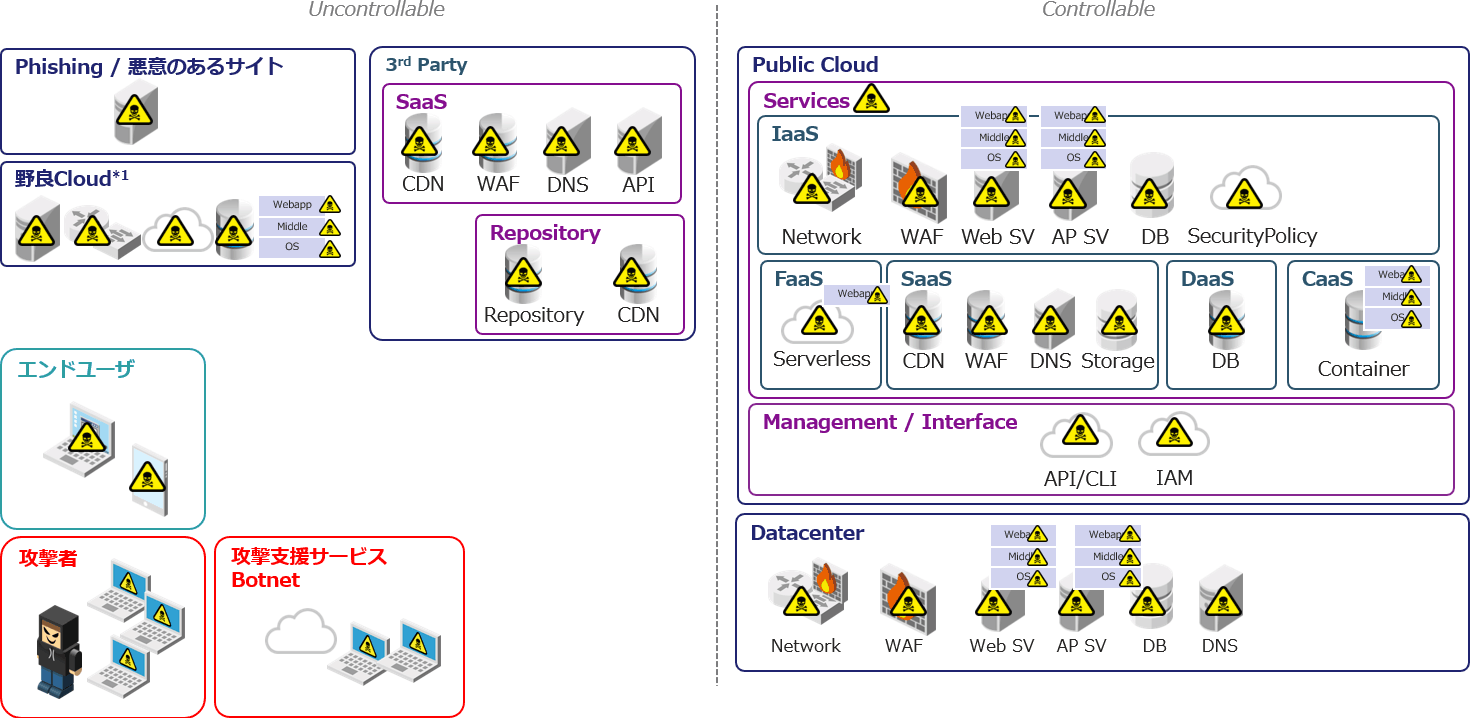
An environment and methods that are advantageous to attackers are in place

Diversification and compounding of attacks
- Popular attacks continue to be implemented in more sophisticated forms
- New threats emerge in areas beyond your control
- Targeting threats that were not traditionally regarded as IT threats
Polarization of attacks
- Small & Repeated Attack / Large Scale Attack
- Short-term decisive type / Long-term type
- A pattern that succeeds in attacking before being noticed, assuming that the attack will be noticed
- There are also attacks that have been devised so that the attack is not noticed
- The time between attack occurrence and attack success is short
Lower attack hurdles
- Cheaper and more sophisticated tools on the rise, very high ROI for attackers
Investment stance on future web application security
It is necessary not only to strengthen security with an eye to minimizing the amount of damage when an incident occurs, but also to consider how it can contribute to overall cost reduction.

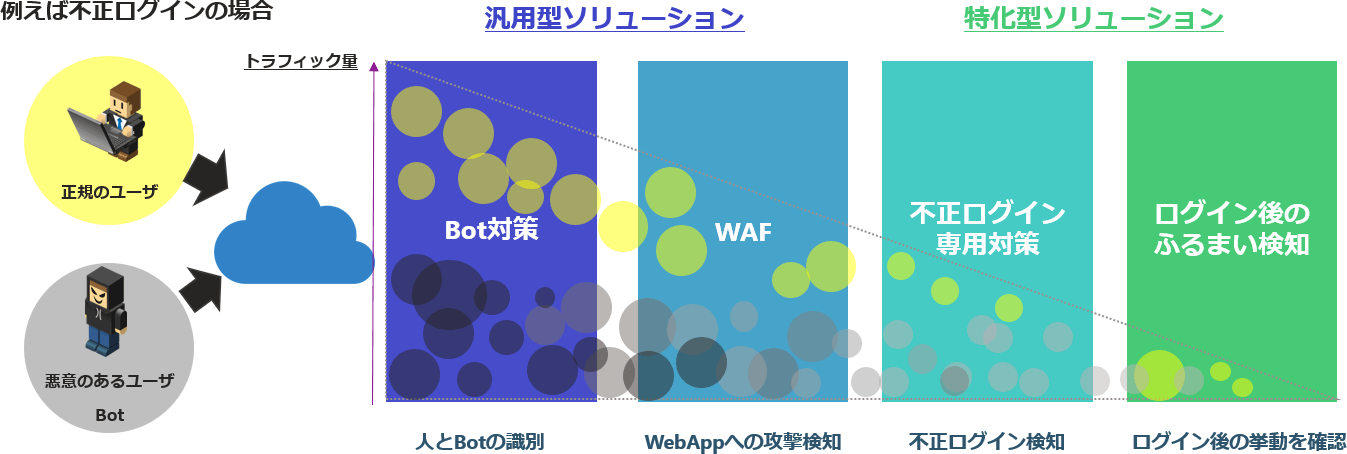
The concept of defense in depth
Efficient security measures and cost reduction by combining general-purpose solutions and specialized solutions!
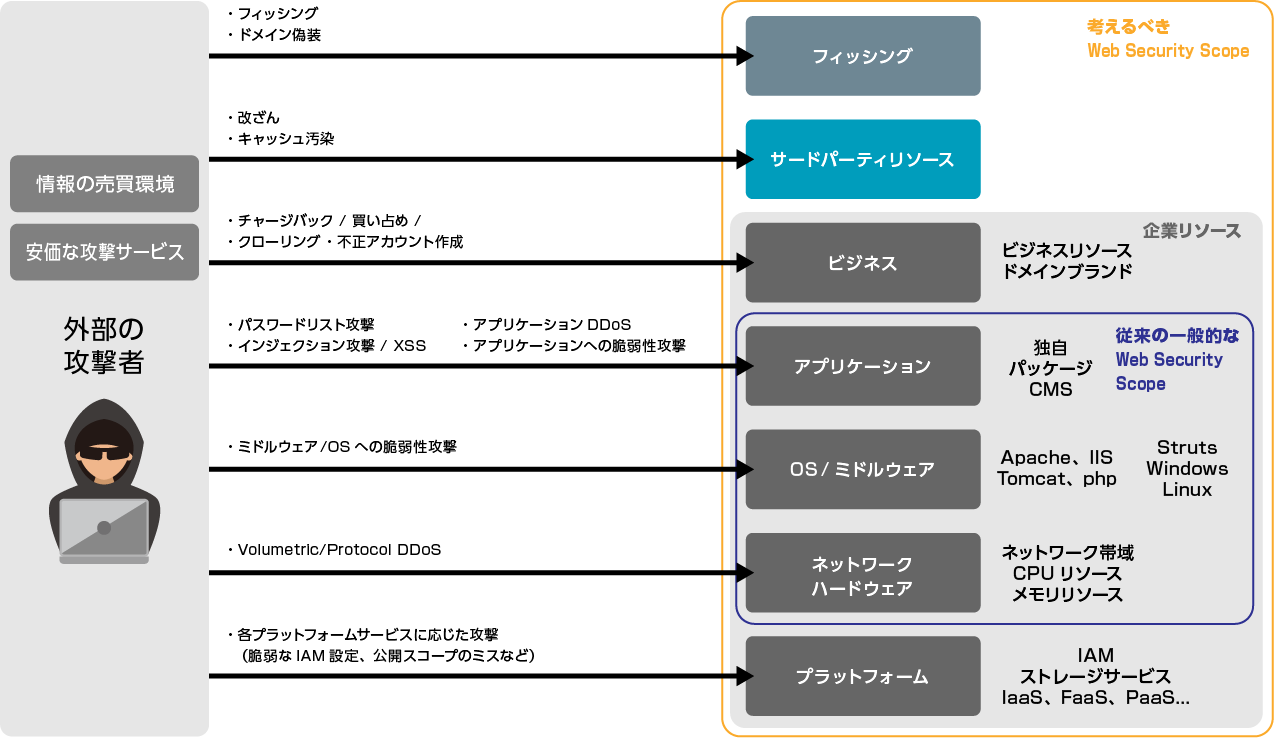
Web application threats
Points to consider in future web security
- Respond to new threats that may occur in areas that were generally considered to be outside the scope of web security
- Strengthening measures to protect businesses, such as hoarding, which was not considered a cyber threat in the past
- Aim to reduce not only damages such as information leaks, but also related costs that may have already occurred
- Like other security, multi-layered defense implementation (general-purpose type x specialized type) on the assumption that it will be intruded on the web
