About reports
Targeted attacks (cyber espionage) against organizations in Japan are continuously being observed. Thanks to the efforts of the cybersecurity industry, including those overseas, analysis of the attack traces collected in Japan to date from the perspectives of attack methods, attack infrastructure, and details of damage reveals that the Chinese government was involved in the attacks. That is no longer in doubt. Of the targeted attacks observed from October 2018 to March 2019, this report details the attack activities by the Tick group and the DragonOK group, both of which are based in China. It has been with. In addition, attacks on Japanese companies by the OceanLotus group, which is believed to be based in Vietnam, have also been observed, and the details are also described.
Damage from ransomware (ransom-demanding viruses) and DDoS attacks (denial of service attacks) has an immediate impact on business operations, so it is inevitably easy to reach the ears of management, while damage from cyber espionage, which steals confidential information. In many cases, it does not have an immediate effect, and it is difficult for the causal relationship with actual damage such as technology theft to surface. However, if the stolen confidential information falls into the hands of the Chinese government and Chinese companies, the industrial competitiveness of Japanese companies will gradually decline as a result.
Targets of cyber-industrial espionage are not limited to space, aviation, marine, defense, and academic institutions, but also electronics, chemicals, machinery, semiconductors, medicine, agriculture, think tanks, and the media. We hope that you will use this report to raise awareness within your company and industry, and if necessary, investigate and take countermeasures on the assumption that your computer has been infiltrated by an attacker.
Observed attacks and their background
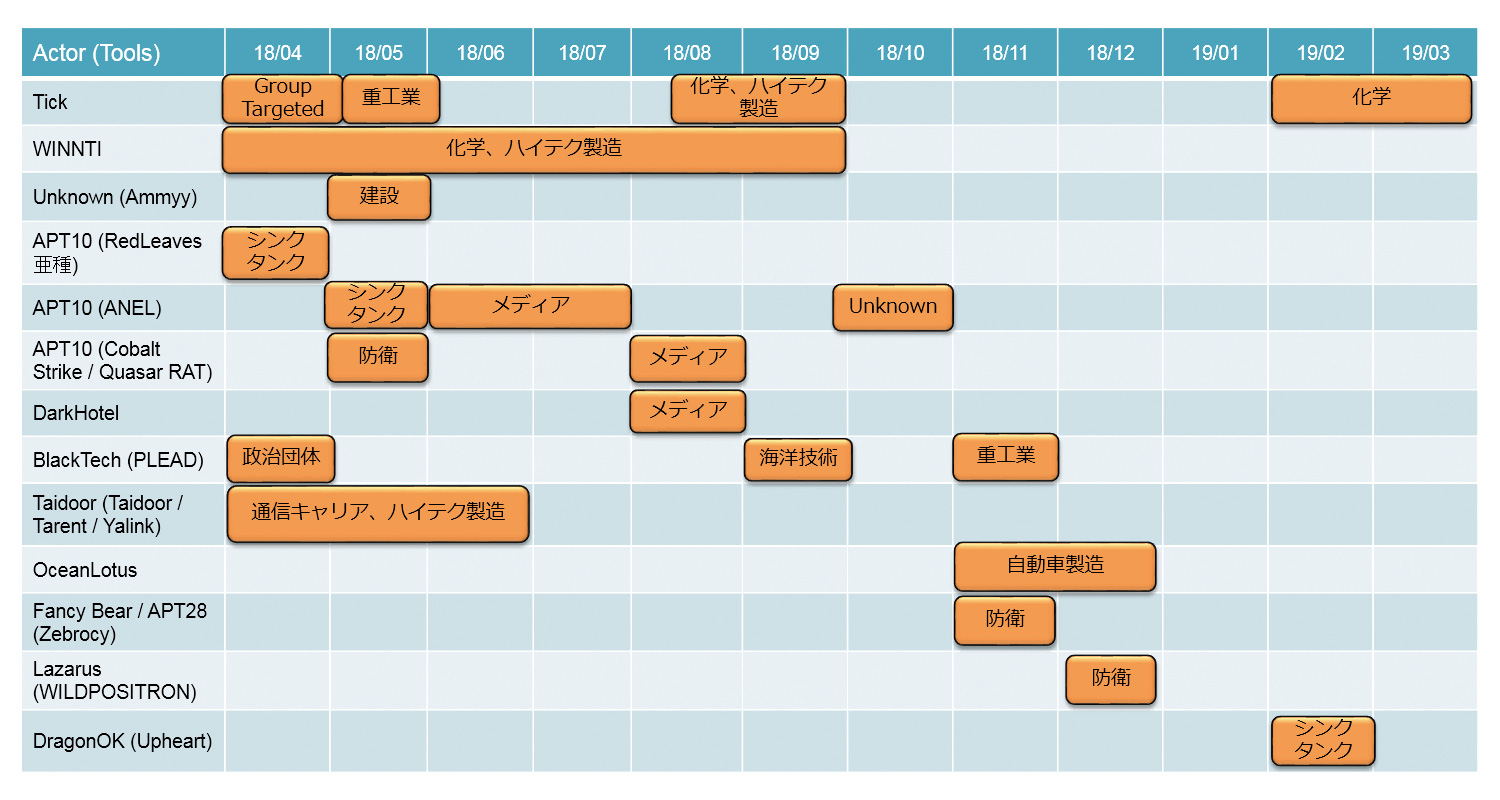
This is a time chart of targeted attacks observed from April 2018 to March 2019 and the industries targeted by them.
Table 1. Targeted attacks and target industries observed in 2018
Attack group APT10, which targets Japan as one of its main targets, launched ANEL in October 2018.one two threeNo activity was observed after an attack using . Two months ago, in August 2018, the IntrusionTruth blog posted an article implicating the Chinese Ministry of State Security (MSS) and its members in the APT10 campaign.FourPublished in Subsequently, in December 2018, the U.S. Department of Justice indicted APT10 for its attacking activities.Fiveand a statement by the press secretary from the Ministry of Foreign Affairs6has been announced. Due to this series of effects, APT10 may be slowing down the tempo of its attack activities. On the other hand, BlackTech has not been condemned or prosecuted by authoritative bodies.789, and Tick/BLONZEBUTLER10 continue to be active. Also Tick and OceanLotus11 group has been observed to attack the overseas bases of Japanese manufacturing companies.
1. https://blog.trendmicro.co.jp/archives/17280
2.https://www.fireeye.com/blog/jp-threat-research/2018/09/apt10-targeting-japanese-corporations-using-updated-ttps.html
3.https://www.macnica.co.jp/mpressioncss/report.html/
4. https://intrusiontruth.wordpress.com/category/apt10/
5. https://www.justice.gov/opa/pr/two-chinese-hackers-associated-ministry-state-security-charged-global-computer-intrusion
6.https://www.mofa.go.jp/mofaj/press/danwa/page4_004594.html
7.https://blog.trendmicro.co.jp/archives/15393
8.https://www.lac.co.jp/lacwatch/people/20180425_001625.html
9.https://blogs.jpcert.or.jp/ja/2018/03/tscookie.html
10.https://www.secureworks.jp/resources/rp-bronze-butler
11. https://www.welivesecurity.com/wp-content/uploads/2018/03/ESET_OceanLotus.pdf
Index
- executive summary
- Observed attacks and their background
- November 2018 (BlackTech, OceanLotus, FancyBear)
- December 2018 (Lazurus)
- February 2019 (Tick, DragonOK)
- Purpose and Background of Attacks Observed in FY2018
- New TTPs, RATs, etc.
- Evolution of Tick Group TTPs
- Attack on OceanLotus Manufacturing
- Dragon OK revival
- TTPs (tactics, techniques, procedures) by attack group
- Threat Detection and Mitigation Considered from TTPs
- Malware Delivery
- About attack
- RAT to be installed, remote control (about C&C)
- Expansion of intrusion/purpose execution
- Need for threat hunting
- indicator of detection