Skyhigh Security
sky high security
How to prevent the risk of information leakage due to AWS user setting mistakes? CASB is effective in preventing information leakage in the cloud

Confidential information leaked due to AWS S3 user setting mistake! What are the causes and countermeasures? ~Select a CASB that has monitoring items in AWS-specific settings~
AWS (Amazon Web Services), an enterprise cloud service (IaaS) provided by AWS, is used by many companies in various industries and business types around the world for its convenience and cost performance. Recently, an incident was discovered in which confidential information stored in Amazon S3 (Amazon Simple Storage Service: hereinafter referred to as S3), the core object storage of AWS, was made "public" due to a user misconfiguration of administrator privileges. Do you know what the problem is?
In this article, we will organize the causes of user setting errors in S3, the risks posed by weak settings, and effective preventive measures. think about
Benefits and Security Risks of Amazon S3
S3 is cloud-based storage and one of AWS' flagship services, released in 2006. Designed for ease of use by developers, it is widely used for storing all types of business data due to its high scalability, security, high speed, and cost performance. Among them, there is a lot of data that is treated as "confidential information", such as important personal information related to purchases of user customers. Many sites have been found where such information can be viewed from the outside due to incorrect user settings, and it is regarded as a problem.
In fact, at a major Japanese retail company, personal information on an online shop, including credit card information, was leaked from S3. A major risk that could affect corporate activities has been pointed out, such as the fact that a certain automobile manufacturer had disclosed its customer information. These risks are growing on a global scale, with RiskIQ, a US cybersecurity company the Company contract with, that as of July 2019, more than 17,000 domains had their websites compromised via misconfigured S3 buckets. (*Note 1).
Why Do S3 User Misconfigurations Occur?
AWS, which is an IaaS, has built important systems that are directly linked to corporate business and is widely used around the world, making it an easy target for attackers. On the other hand, it cannot be denied that there are unique circumstances in which user setting errors are likely to occur.
Factor 1: Users cannot keep up with the speed of AWS service releases
AWS has updated 1,957 new services and features in 2018 alone. The inability of developers to keep up with this speed and the lack of understanding is considered to be a major factor in creating security-vulnerable user configuration mistakes.
Factor 2: General vulnerability diagnosis does not consider AWS-specific user settings
When deploying a system on the web, most companies probably have a system in place to check their system using a vulnerability diagnosis service. And we release the service after receiving the diagnosis that there is no problem. However, many vulnerability assessment services do not include check items for AWS-specific phenomena. This is a pitfall of overlooking a mistake in the S3 user configuration.
Factor (3): Due to factors (1) and (2), administrators (users) do not notice vulnerable user settings in S3.
System developers are not necessarily security savvy. In some companies, the cooperation between the development department and the system management (security) department is weak. Emphasizing developer operability, if excessive privileges are granted to accounts and systems, they will continue to operate at the risk of information leakage.
Cloud Vendor Responsible for Security?
In addition, it has been pointed out that in Japan, where cloud culture is inexperienced, there is a misconception about security on the part of users. That is the assumption that "it is okay because the cloud vendor has taken all possible measures for security".
In the AWS shared responsibility model (Note 2) provided by AWS, AWS is responsible for the security of the cloud, but clearly states that the user is responsible for the security of the system in the cloud. Although the scope of responsibility is clearly defined, there are passages where users assume that the vendor is responsible for all security, which may lead to weak user settings.
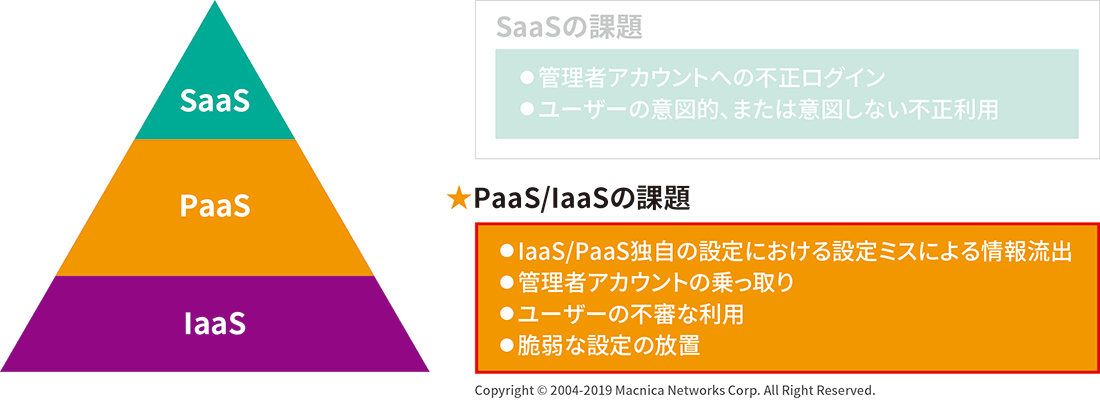
Information leakage incidents due to AWS user configuration errors are negligence on the part of users, and users themselves need to work on security to prevent such incidents. For example, cloud-specific security measures are required against misconfiguration, neglect of weak settings, hijacking of administrator accounts, and inappropriate use of users behind the scenes.
What kind of security is necessary in the cloud era?
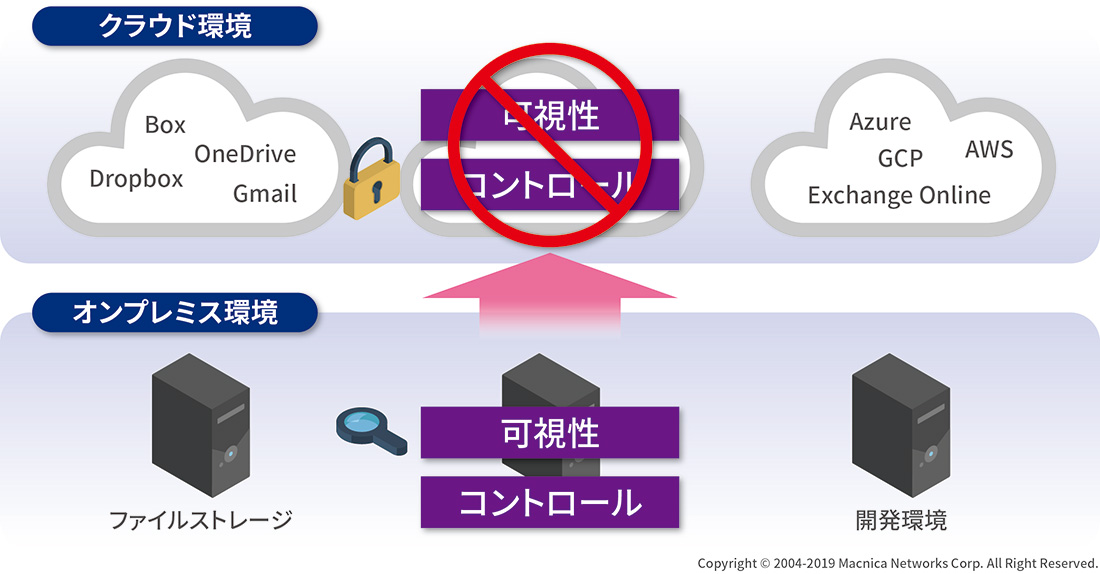
As a result of migrating various systems to the cloud by taking advantage of the benefits of the cloud, the conventional security measures taken in the on-premises environment no longer make sense. The on-premises system had high visibility and could be controlled in-house, but this was only possible because of the "closed environment". In the cloud, both systems and data are "external" in the first place, making it difficult to visualize and control. Security in a cloud environment is therefore a completely different approach. In particular, IaaS security requires expertise to keep up with IaaS updates with a sense of urgency.
"MVISION Cloud" with monitoring items that follow AWS updates
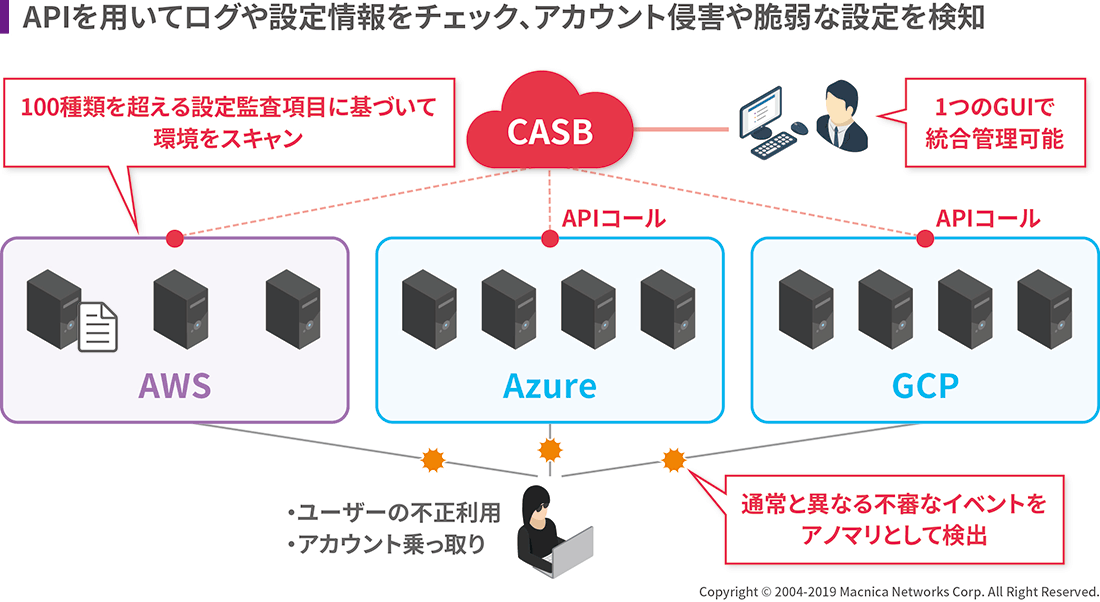
CASB (Cloud Access Security Broker) is attracting attention as an effective security solution for solving cloud-specific issues. CASB is a solution that visualizes the usage status of the cloud using technologies such as APIs and has control functions such as controlling access. There are more than 100 monitoring items related to AWS-specific security risks, and it is recommended for companies building systems on AWS. In addition, McAfee is the first CASB vendor to obtain AWS Security Competency, and MVISION Cloud updates monitoring items while following AWS updates to ensure top security.
Not limited to AWS, when building a system on IaaS/PaaS, it is important to configure settings correctly according to IaaS/PaaS rules. To that end, it is effective to utilize specialized tools that can not only check whether there is an attack from the outside, but also whether the recommended settings and the company's settings match. We can set up a system that works.
Summary
In the on-premises era, security for internal information infrastructure and internal systems was important. However, now that business systems and services that cannot be stopped are already running on cloud environments such as AWS, security suitable for the cloud is essential. Why don't you review whether your company's security is ready for the "cloud era"? We recommend using MVISION Cloud, which follows the evolution of AWS, for vulnerabilities that you cannot detect on your own. Please feel free to contact us regarding POC.
*Note 1: RiskIQ blog July 10, 2019
*Note 2: AWS Shared Responsibility Model
*Information at the time of interview.
Inquiry/Document request
In charge of Macnica Skyhigh Security
- TEL:045-476-2010
- E-mail:mfe-info@macnica.co.jp
Weekdays: 9:00-17:00