product
- Macnica SOC Service
- CrowdStrike Monitoring Operation Support Service
- Active Directory Diagnostic/Monitoring Service
- Trellix EDR Monitoring Service
- Threat Hunting & Incident Response Service
- Triage service
- security assessment
- security advisory
- CSIRT construction support
- CSIRT enhancement exercise
- Suspicious email training service
- platform diagnostics
- Website security monitoring service
- Web application vulnerability diagnosis
- Supports initial response to incidents. Responds smoothly from stopping the bleeding to neutralizing the attack and preventing damage from spreading.

Macnica Security Service
Macnica Security Services
Triage service
Expert analysts investigate suspicious files and assist CSIRTs in responding to incidents
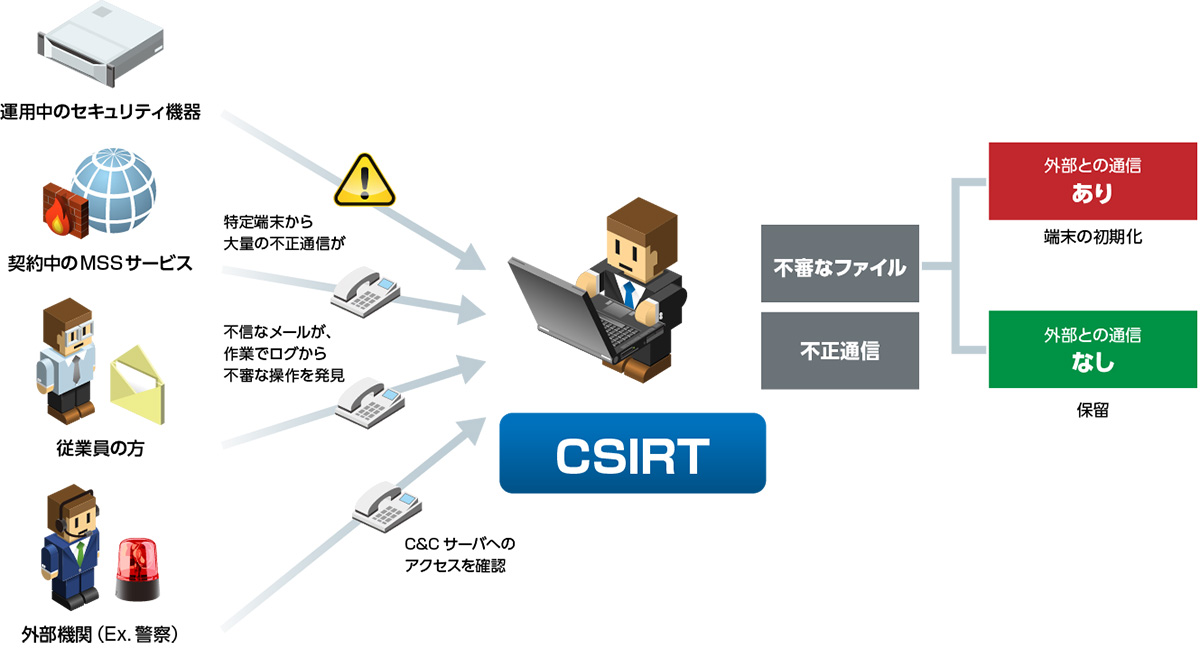
CSIRT (Ciesart: Computer Security Incident Response Team) receives suspicious traces (files, communications, operation logs) discovered during detection and work of security products in operation, contacts from external organizations, etc., and responds to incidents. We will investigate and respond. However, CSIRT resources are limited and it is necessary to triage (prioritize) each incident and respond.
In this service, expert analysts investigate suspicious files, report their degree of danger and traces of infection, and assist CSIRT in responding to incidents.
- case 1
I want to investigate what a file detected by a security product looks like. Ransomware aimed at stealing money, is it a distributed type like Emotet, or is it a targeted attack aimed at intellectual property? - case 2
The user may have executed a suspicious file attached to an email, and I would like to know the infection traces (communication destination, etc.) for investigation.
In this service, targeted attacks are judged by professional analysts who specialize in analyzing targeted attacks targeting Japanese companies. We support CSIRTs by utilizing our knowledge of threats with little information from overseas vendors.
Characteristics of targeted attacks and countermeasures
Targeted attacker groups have clear intentions and goals against specific individuals and organizations, and carry out persistent and long-term attacks. Therefore, it is important to quickly determine whether it is a targeted attack and take appropriate measures. In addition, it is important to proactively investigate and determine the possibility of a targeted attack, even if it could be prevented by security products and people's awareness.
Examples) Detection of attack emails written in natural Japanese, discovery of credential dump tools, detection of backdoor malware on servers, etc.
In the case of a targeted attack, even if the attack is blocked, another method will be used to persistently attempt to infiltrate the system. Threat hunting to investigate whether it is not is also effective.
Service features
This service has the following three menus.
| Service name | content |
|---|---|
| quick triage | Dynamic analysis (Box analysis) investigates file risk assessment and infection traces. |
| Specimen detailed analysis | Malware that does not work and is difficult to analyze by Box analysis is analyzed in detail at the code level of the file to be investigated using tools such as disassemblers. |
quick triage
In the case of unknown droppers (Office format files, etc.) and malware that encrypts code, there are cases where it is difficult to determine just by comparing threat intelligence. In this service, instead of CSIRT, expert analysts perform metadata analysis and dynamic analysis of files to determine the degree of risk. We will report the risk level and the infection indicators (IOC) such as dropped files, manipulated registries, communication destinations, etc. obtained during the investigation. In addition, we will use the IOCs obtained from the survey to our threat intelligence, OSINT (open source intelligence), and strive to make more accurate risk assessments. If the attacker is identified, we will also report a summary of the group.
Figure 1. Pivoting relevant information in OSINT
| Report format | Dedicated portal and email |
|---|---|
| contents of report |
|
| Survey target |
|
| target response time | 弊社営業時間内で、受付後6時間以内 |
Figure 2. Report content sample
Specimen detailed analysis
Specialized analysts use tools such as disassemblers to analyze target files in detail at the assembly code level for malware that does not work in dynamic analysis (Box) and are difficult to investigate, and identify the degree of risk, malware functions, and infection traces. Investigate.
Figure 3. Difference between quick triage and sample detailed analysis
| Report format | Report (about 10 pages on A4) |
|---|---|
| contents of report |
|
| Survey target |
*For Linux/macOS (x86/x86-64), please consult us separately. |
| target response time | 弊社営業時間内で、受付後7営業日以内 |
Figure 4. Report content sample