
Okta
Octa
Introduction
Auth0 supports various authentication and authorization flows such as Authorization Code Flow, Authorization Code Flow with PKCE (Proof Key for Code Exchange) and Implicit Flow defined in OAuth2.0 (RFC6749). By using Auth0 and the SDK provided by Auth0, you can easily implement each flow.
On this page, we will use Authentication Code Flow (RFC6749 4.1) as an example to confirm the sequence of obtaining a refresh token when using Auth0 and re-obtaining an access token/ID token using the refresh token. For confirmation, we will introduce the necessary Auth0 settings and the specific procedures for reacquiring access tokens/ID tokens.
premise
The information on functions and settings described on this page is current as of January 2023.
For access token/ID token acquisition in Authorization Code Flow, please refer to Authorization Code Flow in Auth0 (Access Token/ID Token).
preset
The pre-settings required on the Auth0 side for confirmation of refresh token acquisition in the Authorization Code Flow are shown below.
In this procedure, "https://example.com" is specified as a resource server, but it does not actually provide resources.
- Application settings
- On the Auth0 admin screen, click Applications > Applications
- Create a new Application
- Select Single Page Application
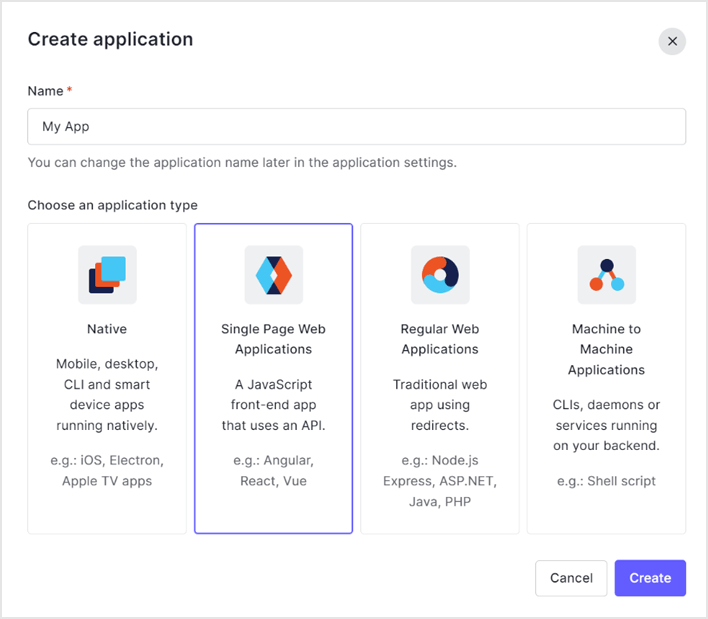
- Register resource server URLs as Allowed Callback URLs
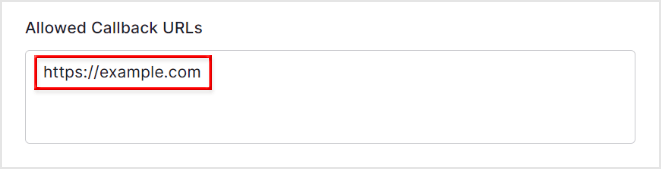
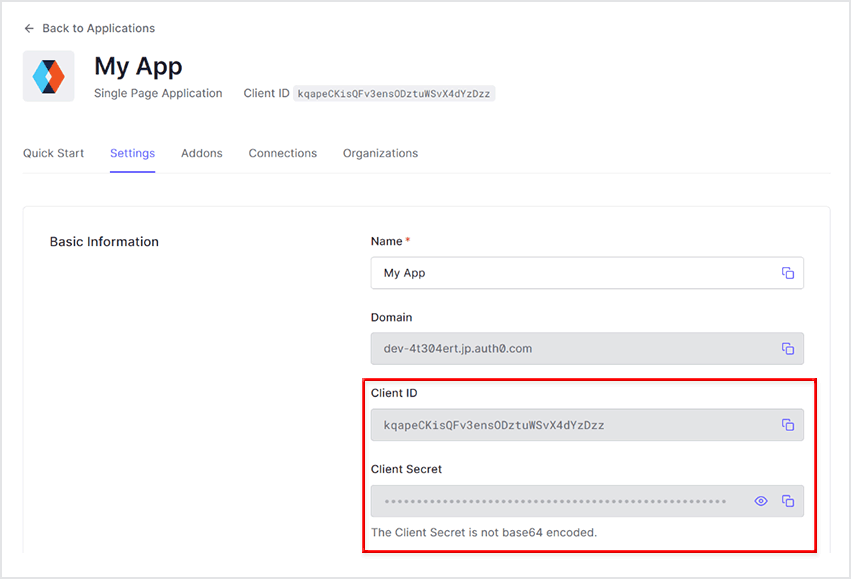
- After creation, check the issued Client ID and Client Secret values
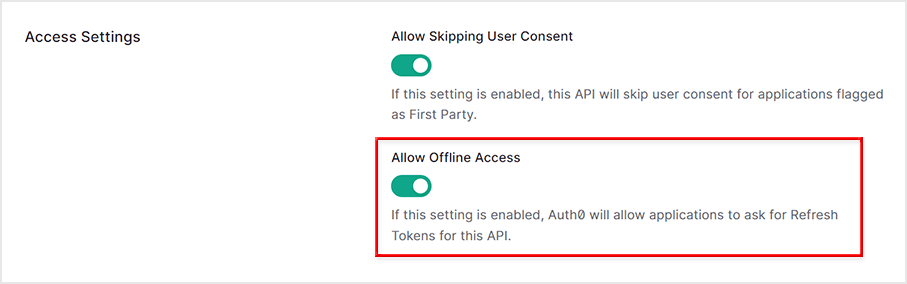
- API settings
- On the Auth0 admin screen, click Applications > APIs
- New API
- Register resource server URL as Identifier
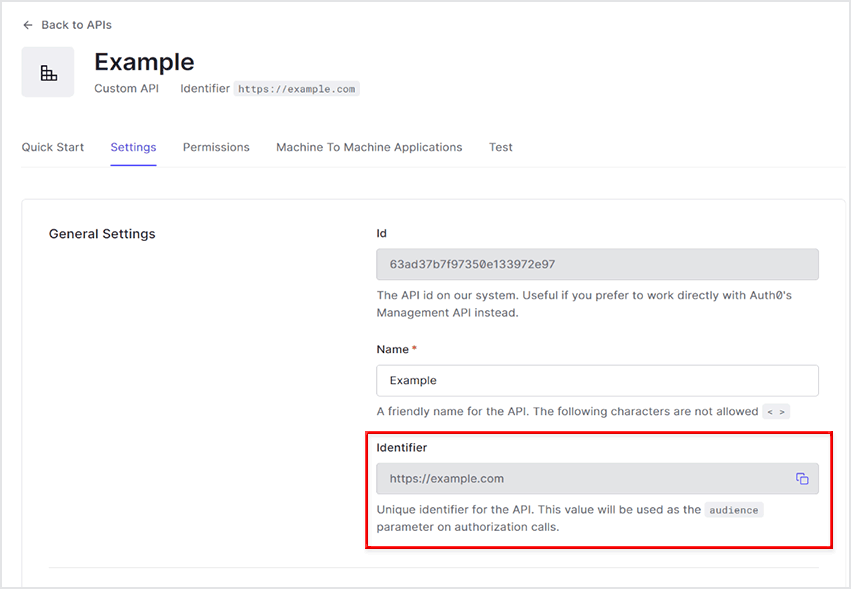
- Enable Allow Offline Access for refresh token issuance
Confirmation procedure overview
Check the sequence of Authorization Code Flow and refresh token acquisition in Auth0. The overview of the confirmation procedure is as follows.
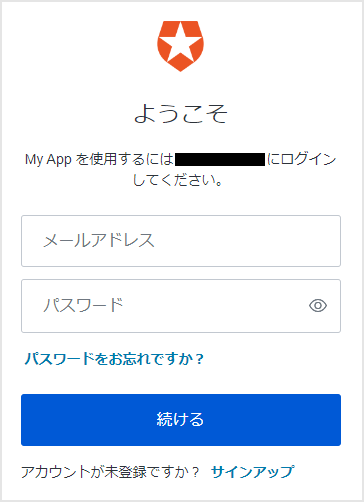
- Request an authorization code from the Auth0 /authorize endpoint
- Authentication screen display by Auth0: Perform user authentication
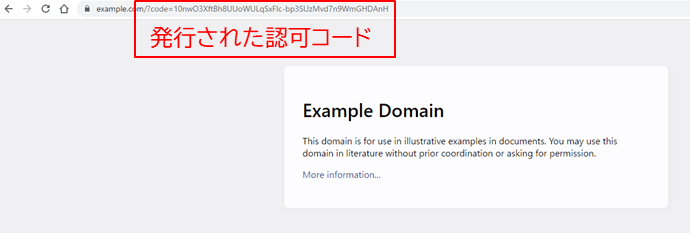
- Transition to the redirect destination specified in 1.: Check the authorization code from the URL
- Access Auth0 /oauth/token endpoint and get access token, ID token and refresh token
- Check the acquired access token and ID token
- Access the Auth0 /oauth/token endpoint using the refresh token obtained in 4. and reacquire the ID token and access token
- Check the reacquired access token and ID token
Confirmation procedure
Access the following URL with a web browser
supplement
- <YOUR_AUTH0_TENANT_NAME>: Auth0 tenant name
- <REGION_DOMAIN>: Auth0 tenant region name
- audience=https://example.com: Identifier of the API setting in the pre-configuration
- response_type=code&scope=openid: use Authorization Code Flow + get ID token
- scope=offline_access: get refresh token
- client_id: Client ID of Application settings in the preset
- redirect_uri: Redirect destination URL after authentication is completed
supplement
- grant_type=authorization_code: use Authorization Code Flow
- client_id: Client ID of Application settings in the preset
- client_secret: Client Secret of the Application setting in the pre-configuration
- code: Authorization code obtained in 3.
{
"access_token":"eyJhbGciOiJSUzI1NiIsInR5cCI6Ikp...(略)...qvVPSppORhoOjSQLj170Q",
"refresh_token":"v1.MbSfbtTXtsjmFCtSpWdRLHgd...(略)...QRLQ-89EZS_oPicJy2zChr0",
"id_token":"eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCI...(略)...Bwf8epG61vPgTk5oQ9p7A",
"scope":"openid profile email offline_access",
"expires_in":86400,
"token_type":"Bearer"
}
Decode access token and ID token at jwt.io
{
"iss": "<your_auth0_tenant_name>.<region_domain>.auth0.com/",
"sub": "auth0|63914fc35f596748bf001439",
"aud": [
"https://example.com",
"https://<your_auth0_tenant_name>.<region_domain>.auth0.com/userinfo"
],
"iat": 1672298378,
"exp": 1672384778,
"azp": "kqapeCKisQFv3ensODztuWSvX4dYzDzz",
"scope": "openid profile email offline_access"
}
{
"nickname": "xxxxxxxx",
"name": "xxxxxxx@xxxxxxxx.co.jp",
"picture": "https://s.gravatar.com/avatar/24b5f30a0fe65625e5afb...(略)...%2Fim.png",
"updated_at": "2022-12-27T10:50:42.856Z",
"email": "xxxxxxx@xxxxxxxx.co.jp",
"email_verified": true,
"iss": "https://<your_auth0_tenant_name>.<region_domain>.auth0.com/",
"sub": "auth0|63914fc35f596748bf001439",
"aud": "kqapeCKisQFv3ensODztuWSvX4dYzDzz",
"iat": 1672298378,
"exp": 1672334378,
"sid": "SqBjbek-b0pWC5zmampoHm4M3Rnl_pVL"
}
supplement
- grant_type=refresh_token: Token reacquisition by refresh token
- client_id: Client ID of Application settings in the preset
- client_secret: Client Secret of the Application setting in the pre-configuration
- refresh_token: Refresh token obtained in 4.
{
"access_token":"eyJhbGciOiJSUzI1NiIsInR5cCI6Ikp...(略)...LhQUVepobZLF3pNP3hsoZw",
"refresh_token":"v1.MrSfbtTXtsjmFCtSpWdRLHhIl0...(略)...P8RAU1himNqVxlISqtjn3HQ",
"id_token":"eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCI...(略)...9BpmhD3KWFyVMgR0hGQ",
"scope":"openid profile email offline_access",
"expires_in":86400,
"token_type":"Bearer"
}
supplement
- By enabling the refresh token rotation function (default: enabled), a new refresh token will be returned when the access token is reacquired using the refresh token.
Refresh Token Rotation - Auth0 docs
Decode the access token and ID token on jwt.io and confirm that the issuance (iat claim) and expiration date (exp claim) are different from the confirmation result in 5.
{
"iss": "https://<your_auth0_tenant_name>.<region_domain>.auth0.com/",
"sub": "auth0|63914fc35f596748bf001439",
"aud": [
"https://example.com",
"https://<your_auth0_tenant_name>.<region_domain>.auth0.com/userinfo"
],
"iat": 1672298551,
"exp": 1672384951,
"azp": "kqapeCKisQFv3ensODztuWSvX4dYzDzz",
"scope": "openid profile email offline_access"
}
{
"nickname": "xxxxxxxx",
"name": "xxxxxxx@xxxxxxxx.co.jp",
"picture": "https://s.gravatar.com/avatar/24b5f30a0fe65625e5afb...(略)...%2Fim.png",
"updated_at": "2022-12-27T10:50:42.856Z",
"email": "xxxxxxx@xxxxxxxx.co.jp",
"email_verified": true,
"iss": "https://<your_auth0_tenant_name>.<region_domain>.auth0.com/",
"sub": "auth0|63914fc35f596748bf001439",
"aud": "kqapeCKisQFv3ensODztuWSvX4dYzDzz",
"iat": 1672298551,
"exp": 1672334551
}
in conclusion
As a movement of Authorization Code Flow in Auth0, we introduced the reacquisition of access token/ID token by refresh token. We hope this will help you understand how Authentication Code Flow works and how Auth0 implements it.
reference
Inquiry/Document request
In charge of Macnica Okta Co., Ltd.
- TEL:045-476-2010
- E-mail:okta@macnica.co.jp
Weekdays: 9:00-17:00