Mandiant
Mandiant
Security measure effect measurement tool "Mandiant Security Validation"
Mandiant Security Validation is a product that visualizes installed security products and advises on optimal deployment.
You can optimize security measures by clarifying "visualization of problems in the existing security environment", "whether or not there is duplication of investment", and "mistakes in configuration/settings".
Benefits
- Understanding problems with existing security measures, security operations, and investment effects built in a multi-vendor environment
- It is possible to find holes in existing security countermeasure products and introduce and use optimal products.
- You can evaluate and confirm the effectiveness of your company's existing countermeasures when new threats are discovered or incidents occur at other companies.
- Since multiple security products can be evaluated using the same index, it is possible to standardize security standards.
- Existence of duplicate investment
- Contribute to cost reduction by grasping the presence or absence of duplication of investment.
- The effectiveness of each product is verified using actual malware, etc., and the effectiveness of security measures is measured. For products with overlapping effects, it can be used as a criterion for judging whether reduction is possible.
- Visualize configuration/setting mistakes
- You can check whether your existing security measures are compatible with changes in the IT environment (system expansion, cloud migration, etc.).
- Periodic checks make it possible to quickly identify configuration and setting errors that constantly occur, as well as operational deficiencies.
Product Summary
Mandiant Security Validation is a security product effectiveness measurement platform that provides "quantifiable evidence of security effectiveness."
feature
- Validated in the latest attack scenarios with Mandiant threat intelligence
Attack scenarios derived from Mandiant's latest threat intelligence are delivered regularly to validate effectiveness against the latest threats. Mandiant Threat Intelligence is positioned as a "Leader" by Forrester. - Test security products in the same environment as the production environment
You can conduct network traffic tests targeting gateway products such as firewalls, and tests sending attack emails targeting email security products. It is possible to test endpoint products such as EDR with real malware. Safely test real-world ransomware and other attacks that destroy your endpoints with FireEye's proprietary technology.
*Non-destructive attacks are executed only within actors and between actors, so you can safely try them as many times as you want.
* Destructive attacks require the purchase of an additional option (Protected theater) (the environment will be restored after the test). - Regularly conduct multiple tests in multiple environments
Since the tests are conducted according to unified standards, it is possible to unify the security standards of a wide range of security products. - Based on the attack detection results, reports on what changes should be made to existing security products and what improvements should be made
By supporting countermeasures against attacks, we help customers reduce the burden of security countermeasures. - Vendor-free operation
By linking with the intelligence of each company, we generate attack scenarios based on each intelligence.
*Additional option (TAAM) and purchase of each company's intelligence are required for intelligence linkage. The target of security verification is vendor independent. It can be used for systems built with security products from various vendors including SIEM.
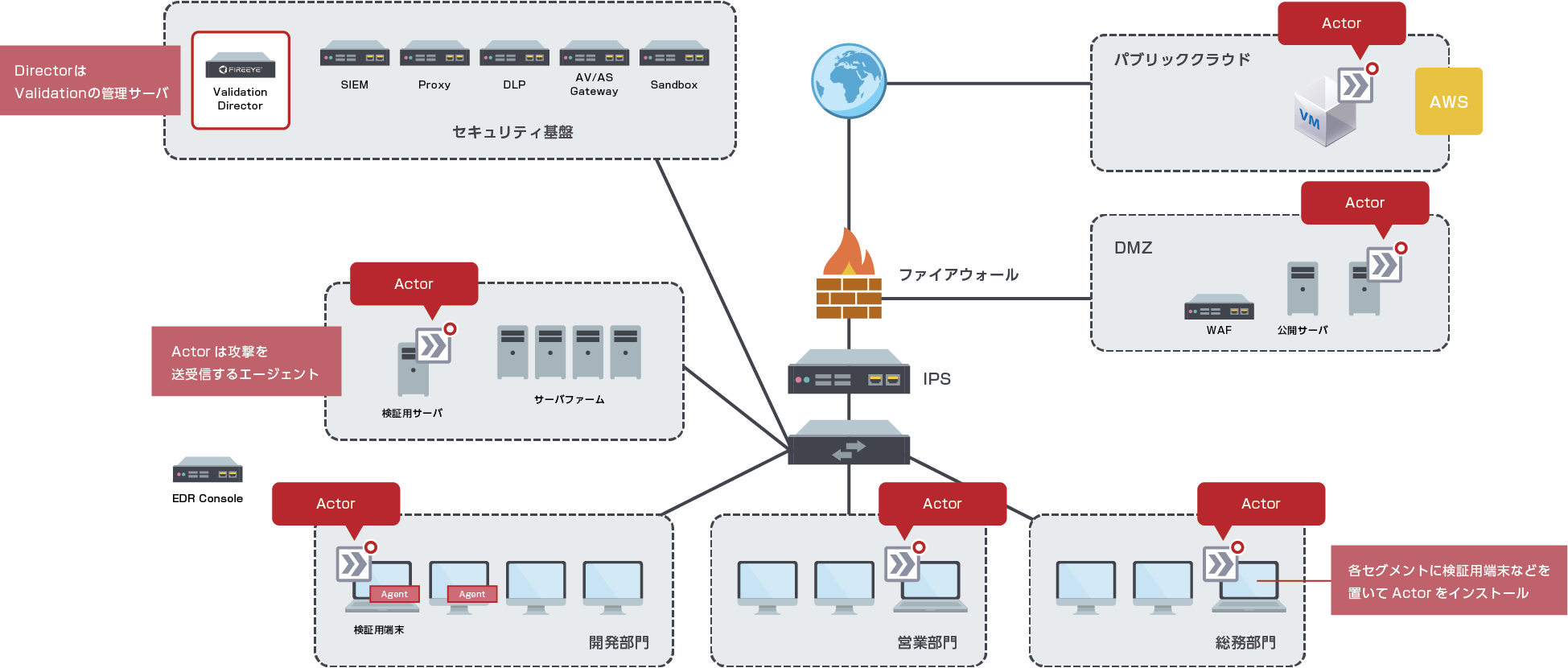
Product configuration
| Director | A management server responsible for collecting data, running tests, and generating reports. |
| actors | Software that performs attack behavior. Arranged for each security countermeasure product that launches an attack. Range that can be tested by Actor ⇒ Network, endpoint, email, cloud |
Introduction image
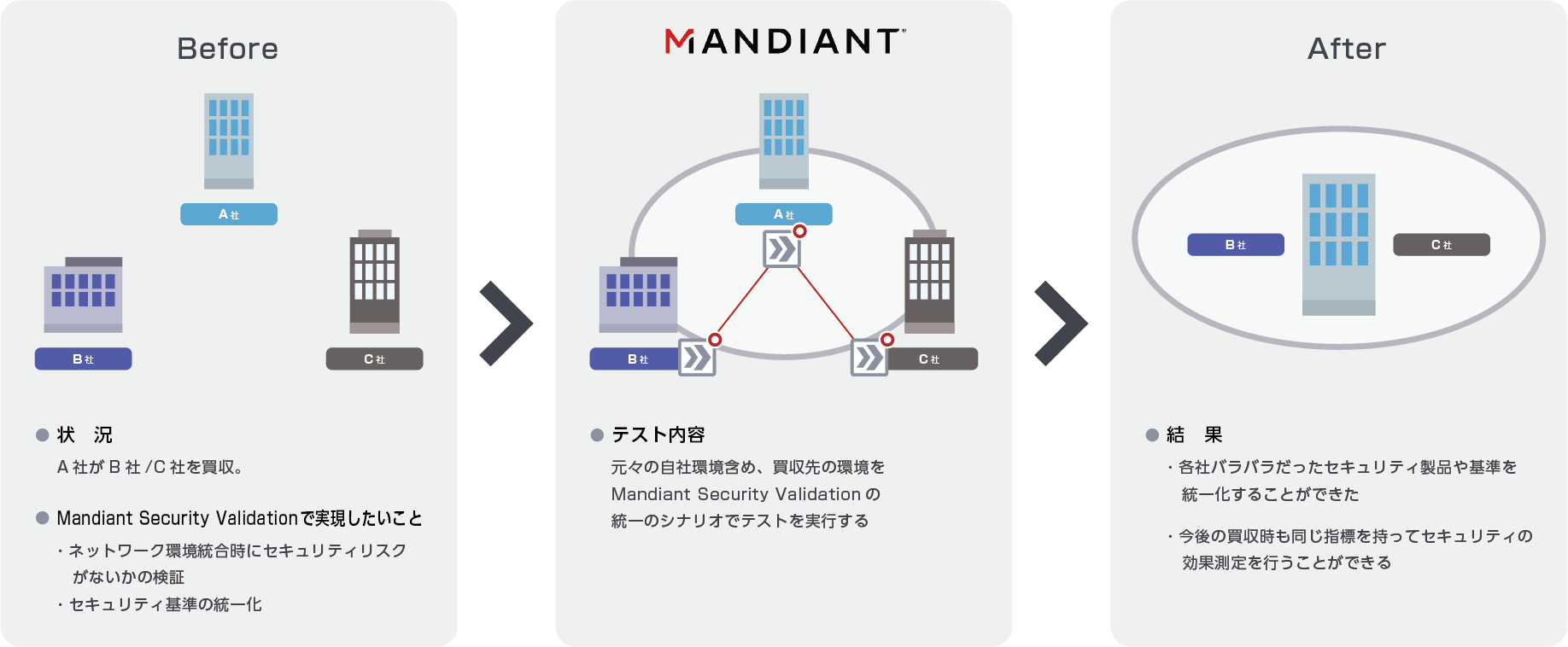
Adoption example
Verification of effectiveness of security products through corporate mergers
manufacturing industry
Inquiry/Document request
In charge of Macnica Mandiant Co., Ltd.
- TEL:045-476-2010
- E-mail:mandiant_sales@macnica.co.jp
Weekdays: 9:00-17:00