
Falcon Shield
Falcon Shield
Top 4 SaaS Security Threats in 2023
Over the course of 2022, a spate of security breaches, attacks, and data leaks forced businesses to scramble to protect their SaaS fleet. In March alone, there were three separate security breaches at Microsoft, Hubspot, and Okta.
As SaaS usage grows rapidly and management becomes more complex, businesses need to focus on hardening and securing four areas of their SaaS environments:
Frequent setting errors
Employee SaaS apps can have as many as 40 million Box, toggles, and other settings across an enterprise. The security team is responsible for securing all these settings, user roles, and permissions and ensuring compliance with industry and company policies.
The obvious risks and inconsistencies of these configuration items with security policies alone require a significant amount of effort to address, but manually securing misconfigurations is a difficult task. These settings are subject to change with each update, and many compliance and industry standards further increase the complexity of configuration. Adding to that challenge, SaaS app owners tend to be in business units that are outside the scope of security teams, are not trained in app security, and are not focused on security. .
Security teams should have a SaaS Security Posture Management (SSPM) solution like Falcon Shield that provides visibility and control over multiple SaaS requirements. The solution should be able to identify both global app settings and platform-specific settings within individual apps. Security teams should use the solution to understand the context of security alerts and ask questions like: who are the users most likely to misconfigure? Are they administrators? Do they have MFA enabled? With this knowledge, security teams can enforce company and industry policies and remediate potential risks due to misconfigurations.
Access between SaaS
The increasing number of apps connected to enterprise SaaS environments also poses a major security challenge. On average, thousands of apps are connected without security team approval or knowledge. Employees use SaaS apps to increase productivity, work remotely, and efficiently build and scale company processes.
However, when connecting an app to a workspace, employees are asked to grant permission to the app. While the app itself may be malicious, these permissions include the ability to read, create, update, and delete corporate and personal data. If you click "Allow," an attacker could use the permissions granted to access your company's sensitive data. Users are often unaware of the importance of the permissions they grant to these third-party apps.
Security teams must be able to reach into the shadow IT realm and discover third-party apps to identify those that pose a risk. From the scope of access these apps request to authorized users and cross-references, security teams must have the ability to measure the level of access to sensitive data across an organization's entire stack. SSPM solutions like Falcon Shield provide security teams with this discovery and control, along with advanced reporting capabilities that help with effective and accurate risk assessments needed to drive actionable countermeasures.
Risks posed by users accessing SaaS from their devices
Security teams must address the threat posed by users accessing SaaS applications from unsecured personal devices. Accessing SaaS apps from unmanaged devices poses high risk to enterprises, especially if the device owner is a highly privileged user. Personal devices are susceptible to data theft and can inadvertently introduce malware into corporate environments. Lost or stolen devices can also provide a gateway for criminals to access your network.
Security teams need a solution that can help manage the SaaS risk that comes from compromised devices. SSPM solutions like Falcon Shield can identify privileged users such as administrators and Member of the Board, calculate the level of user risk, and identify endpoint devices that need to be better secured.
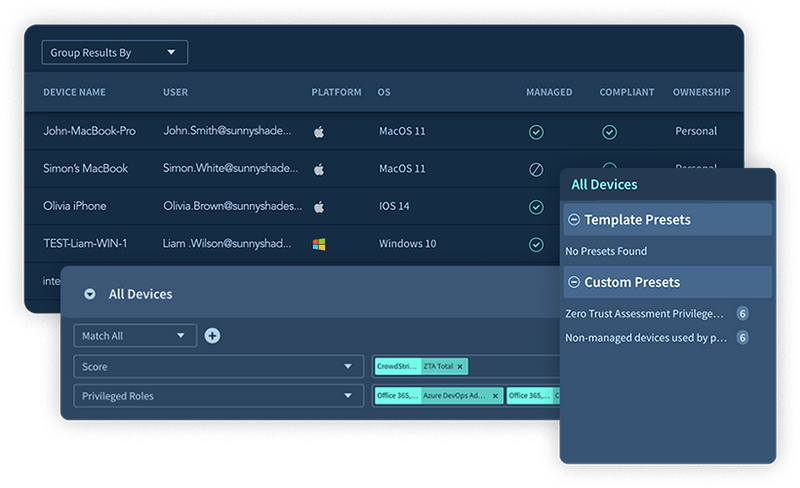
Figure: Falcon Shield device inventory
Identity and access governance
Users of all SaaS apps are a potential entry point for attackers, as seen in the recent MFA Fatigue attack on Uber. In addition to validating role-based rather than individual-based access management and establishing an understanding of access governance, processes for properly configuring user access controls and authentication are essential. Identity and access governance helps security teams ensure complete visibility and control of events occurring across all domains.
Security teams must monitor all identities to ensure user activity complies with the organization's security guidelines. IAM governance continuously monitors a company's SaaS configuration audit and access control implementation, enabling security teams to address issues as they arise.
At the end
Gartner recommends SaaS Security Posture Management (SSPM) as a solution to continuously assess security risks and manage the configuration audit security posture of SaaS apps in the Cloud Security Hype Cycle: 4 Essential Technologies for 2021. are listed. By using the SSPM platform, businesses can strengthen their SaaS security, identify and remediate issues faster, and prevent attacks before they occur. Security teams can implement SaaS security best practices that not only cover misconfiguration management, but also the governance of SaaS-to-SaaS access, the risk level of users accessing SaaS from their devices, and identity and access management.
Inquiry/Document request
Macnica Falcon Shield
- TEL:045-476-2010
- E-mail:crowdstrike_info@macnica.co.jp
Weekdays: 9:00-17:00