Application for evaluation machine

Josis
Josis
Automate analog business of corporate IT
Do you have a problem like this?
Inability to manage IT operations adequately due to a shortage of personnel in charge of information systems within the company
- Usage management of introduced cloud services
- New issuance and deletion of accounts when employees join and leave the company, and management of devices from purchase to disposal
- Countermeasures against information leaks caused by shadow IT and accounts that have not been deleted
Automate analog operations in corporate IT to reduce costs and improve security levels
With the spread of telework, the number of companies that take PCs out of the office is increasing, and PC procurement, management, and security construction work are also required to change urgently. In addition, the introduction of SaaS is progressing to improve operational efficiency, and the workload of account management is increasing. On the other hand, the person in charge of the information system department is often alone or concurrently working with other departments, so it is easy to fall into an overload of work. No security measures taken. A huge increase in costs is a challenge for companies trying to solve the shortage of human resources by outsourcing. “Josys” comprehensively supports IT devices and SaaS operations to solve these issues and promotes corporate DX.
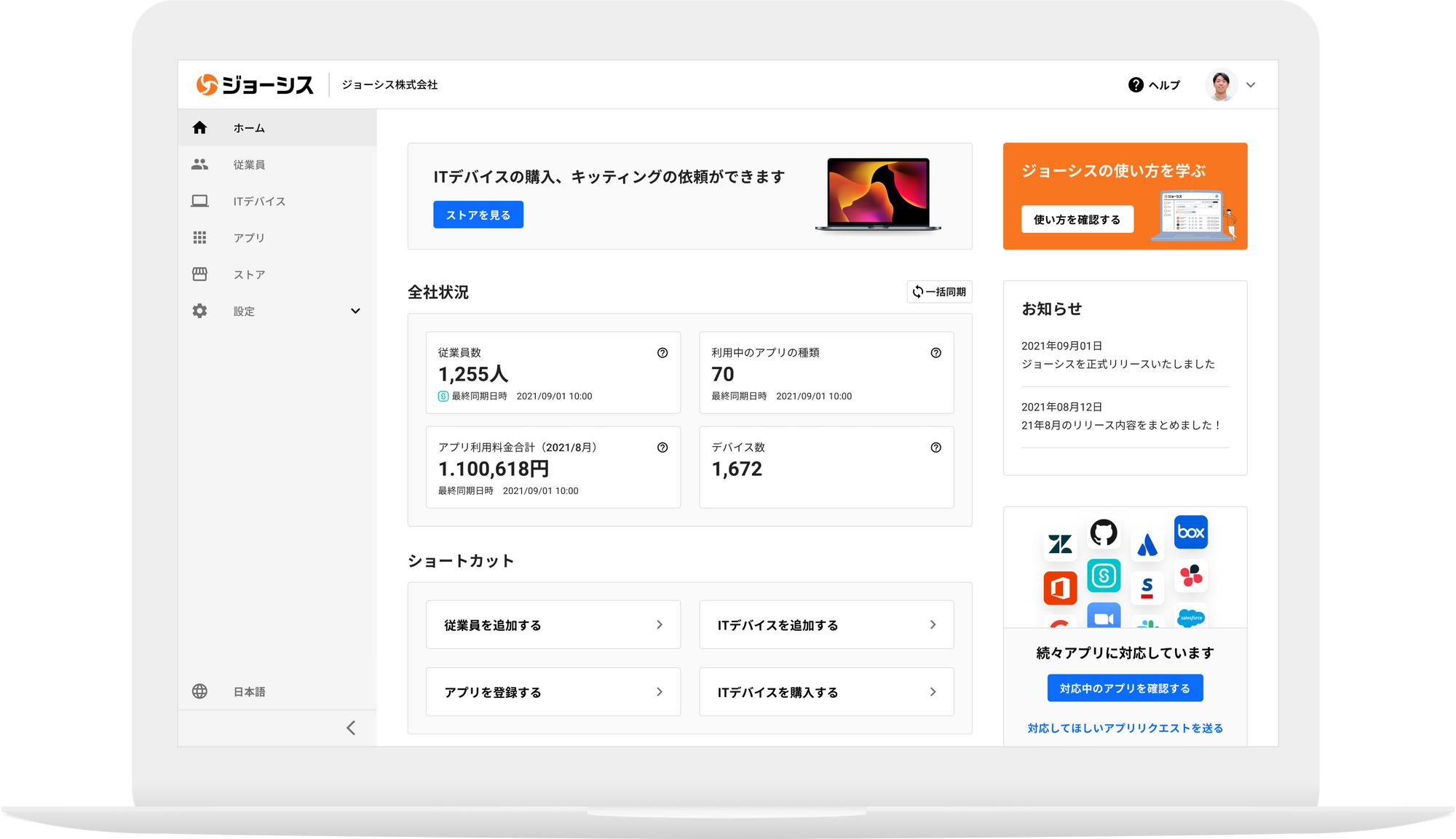
[Point 1] Reduction of man-hours required for visualization and management of SaaS/device usage status
Collectively grasp the usage status and usage charges of SaaS and devices. Since it can be managed in conjunction with employee data, it is possible to take inventory of unnecessary accounts that are not in use and useless IT costs.
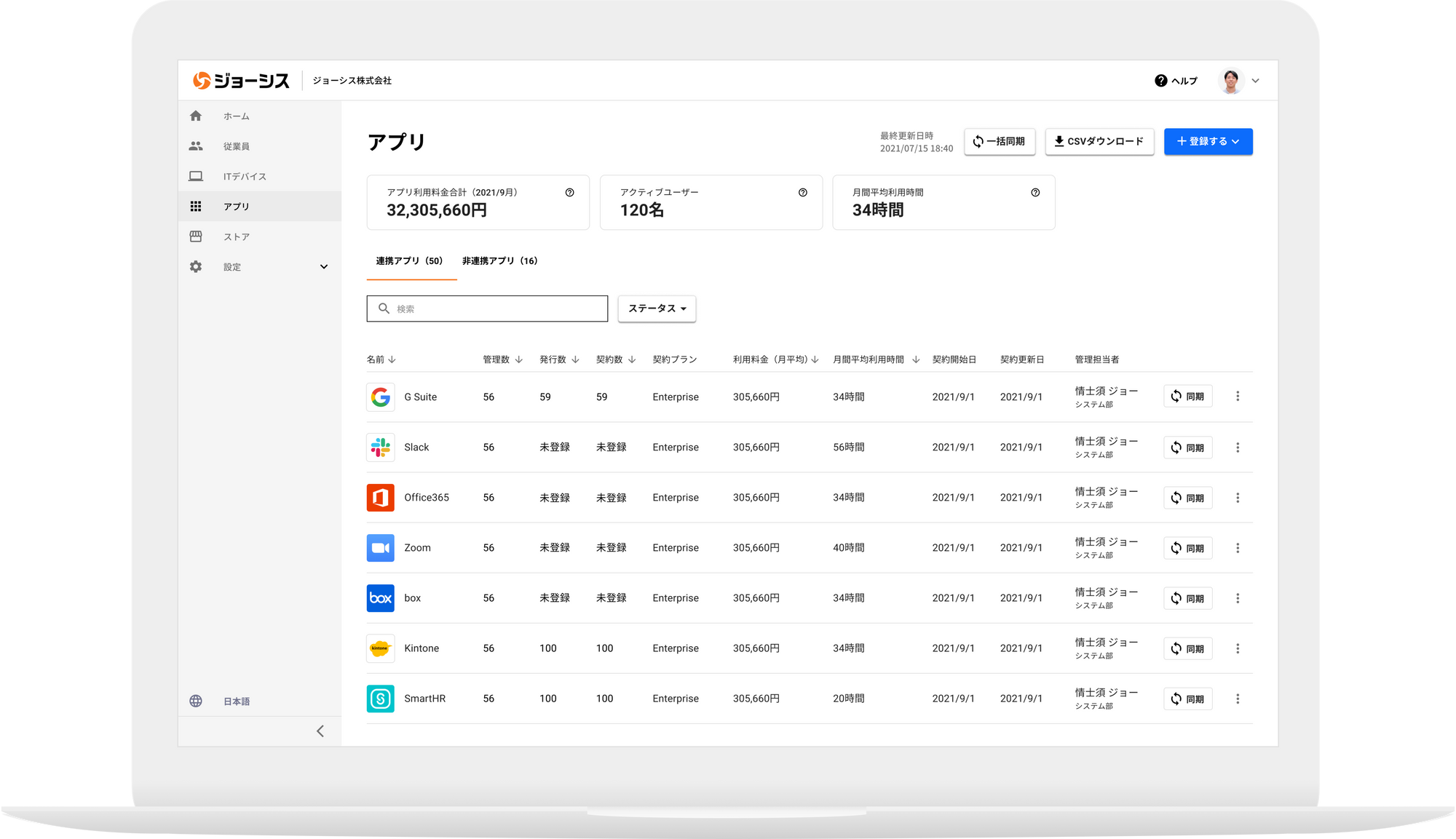
[Point 2] Automate the routine work associated with joining and leaving the company and surprisingly improve the productivity of the information system
We centrally manage the life cycle of information assets, from new issuance to deletion of accounts, purchase of devices to disposal. Since the ledger on the cloud is automatically created and updated, you can break away from inefficient analog management.
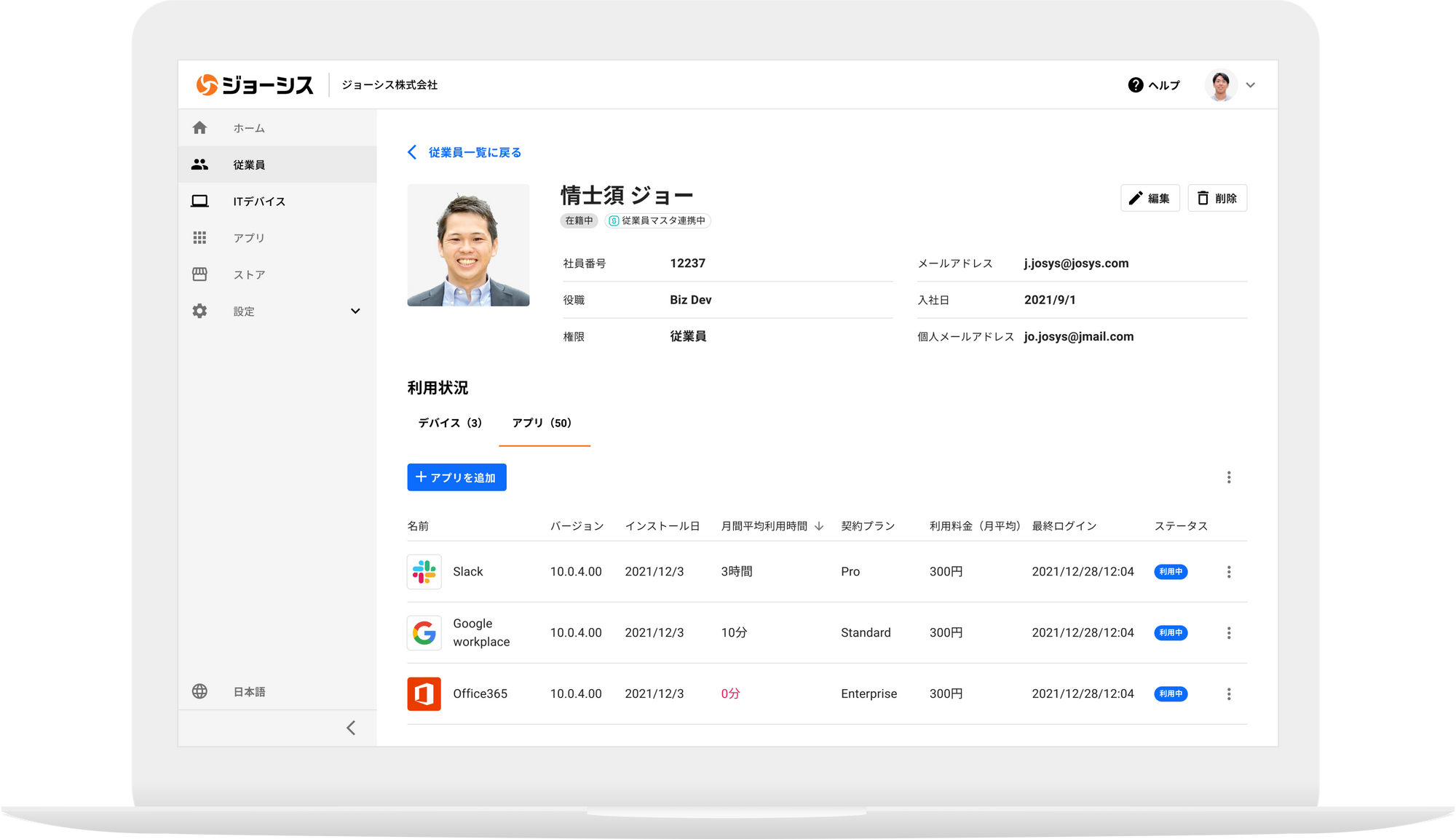
[Point 3] Improve IT security by detecting shadow IT and accounts that have not been deleted
In addition to applications (shadow IT) that the information system has not fully grasped, retiree accounts that are likely to be deleted are automatically detected to prevent information leaks.
Case study
Seminar
これから開催 開催終了 {{ item.title }}
{{ item.seminar_start_date__display_1 }} {{ item.seminar_place__display_1 }}
Inquiry/Document request
In charge of Macnica Joshis Co., Ltd.
- TEL:045-476-2010
- E-mail:digital-it-sales@macnica.co.jp
Mon-Fri 8:45-17:30





