Macnica and TeamT5 publish a trend report on targeted attacks targeting Japan in 2021 - Contributing to preventing the theft of confidential information from Japanese organizations by sharing the methods and objectives of attack groups such as APT10 and BlackTech -
Macnica (Headquarters: Yokohama City, Kanagawa Prefecture, President: Kazumasa Hara, hereinafter Macnica), a total Services & Solutions provider in semiconductors, networks, cybersecurity, and AI/IoT, conducts cyber espionage activities in the Asia-Pacific region. Team T5, Inc. (Headquarters: Taiwan, CEO: Sung-ting Tsai, hereinafter referred to as TeamT5), which has threat intelligence of We will co-author and publish the 6th edition.
Many organizations were hit by attacks that exploited ransomware and supply chain weaknesses last year, which made headlines. While such incidents have surfaced, the “theft of confidential information through targeted attacks” *, which is listed as the second most important threat to organizations in the “Top 10 Information Security Threats 2022”, has been compromised for a long period of time. Many organizations go unnoticed, and there are not many cases that surface. However, this threatens to deprive Japanese companies of their competitiveness and reduce their international industrial competitiveness.
Under these circumstances, clarifying the TTPs, objectives, intentions, skill levels, etc. of each attack group through strategic information sharing and sublimation to intelligence beyond organizations will be effective against these attacks. lead to countermeasures. In addition, since targeted attacks (cyber espionage) are highly dependent on geopolitical risks and tensions between nations, it is very meaningful to analyze and write jointly with Taiwan's TeamT5 under the unstable world situation these days. and meaningful.
This report provides an analysis of attack campaigns that attempted to steal confidential information (personal information, policy-related information, manufacturing data, etc.) from Japanese organizations observed in fiscal year 2021 (April 2021 to March 2022). is described for the purpose of calling attention. In addition, we introduce new attack methods and detection of their threats, focusing on incidents using remote-controlled malware (RAT) with high stealth. At the end of the report, we also include the indicators used in the attack campaigns mentioned in the text so that you can check your organization.
Macnica will continue to persistently analyze and raise awareness of the targeted attacks that are gradually eroding the industrial competitiveness of Japanese companies, and strive to contribute, however small, to the development of the Japanese economy.
*Information-technology Promotion Agency "Information Security 10 Major Threats 2022"
https://www.ipa.go.jp/security/vuln/10threats2022.html
■ Attack timeline and industries where attacks were observed
Regarding the attack trends in FY2021, attacks using the LODEINFO malware of the APT10 attack group and the A41APT attack campaign using the SodaMaster malware continued to be actively observed since FY2020. In the A41APT attack campaign, the two main payloads used in the attack were SodaMaster and the newly observed Jackpot. In addition, attacks by the BlackTech attack group were observed, although their activity had declined during last year's observations. However, it appears that the BlackTech group's initial targets were domestic companies and their Chinese bases. The BlackTech attack group has so far observed many attacks in Japan using PLEAD and TsCookie malware, but malware such as Flagpro and SpiderRAT have also been observed. In addition, it is believed that an attack using the backdoor of the APT38 attack group occurred in Japan. Overall, the number of attack groups has decreased from 6 groups to 4 groups, and the number of attack campaigns has decreased from about 10 campaigns to 7.
【Time chart】
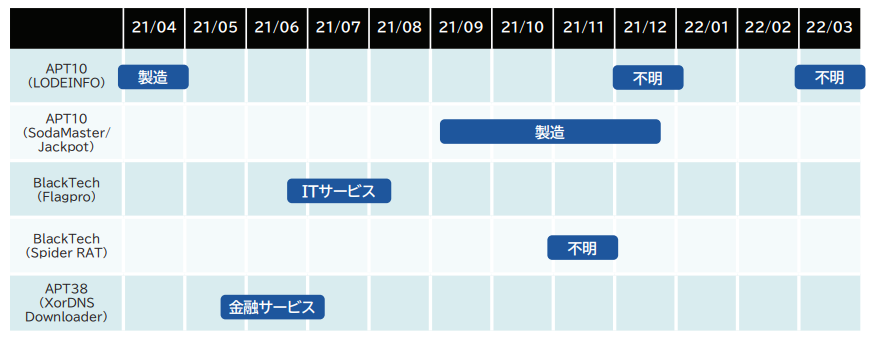
[Biochart of target tissue]
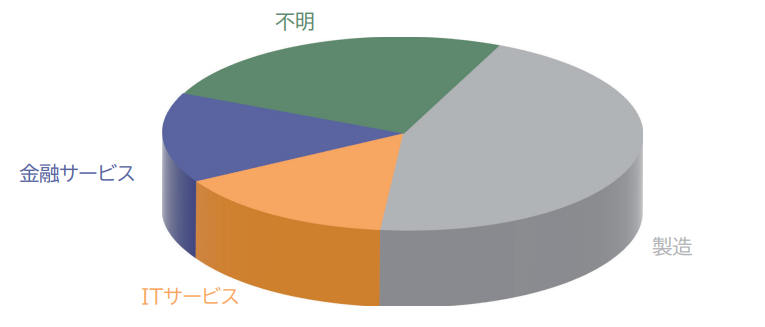
Throughout the year, we observed attacks using APT10's SodaMaster in manufacturing. In addition, since attacks using LODEINFO, which has mainly targeted the media, were also observed in the manufacturing industry, the observed ratio of targeted attacks in the manufacturing industry has increased significantly. Among other industries, IT services and financial services accounted for about the same percentage. In addition, although we obtained samples, the targets of APT10 LODEINFO etc. are not clear, and the proportion of unknowns is increasing. In the attack campaign using SodaMaster, the hosts where malware was installed were all Windows servers located overseas. The BlackTech attack group has seen attacks on IT service-related sites, etc., and it is believed that these activities were active with the aim of infecting bases in China. As a result, intrusions from overseas bases of domestic companies are on the rise. Regarding the attack method, there are two basic methods, such as Office macro files attached to spear phishing emails aimed at infection, and payloads used as remote control malware communicate with C2 and perform arbitrary commands and operations. There is no change or novelty, and with current security technology it is already not difficult to detect. However, it is believed that attackers are attempting to steal intellectual property and information from domestic companies by attacking weakly-protected bases such as overseas where the detection technology is not applied.
■ Contents
・Introduction
・Timeline of attacks and industries in which attacks were observed
・Overview of attack
April 2021 (Manufacturing)
June 2021 (financial services)
July 2021 (IT service)
October 2021 (multiple production)
November 2021 (Unknown)
December 2021 (unknown)
March 2022 (unknown)
・New TTPs, RATs, etc.
APT10 (SodaMaster/Jackpot)
Attack campaign using LODEINFO
Attack campaign targeting BlackTech China base
・About the attack group
・TTPs (tactics, techniques, procedures) for each attack group
・ Threat detection and mitigation measures considered from TTPs
Malware Delivery/Attack
Installed RAT, remote control (for C2 server)
Expansion of intrusion/purpose execution
Pyramid of Pain
・Detection indicator
■ Report download destination
https://www.macnica.co.jp/business/security/2022/report_02.html
*Company names and product names mentioned in this text are trademarks or registered trademarks of Macnica and each company.
*The information published in the news release (including product price, specifications, etc.) is current as of the date of announcement. Please note that the information may be subject to change without prior notice.
About Team T5, Inc.
TeamT5 is one of the world's leading malware analysis teams and the best solution provider for cyber espionage in the Asia Pacific region. We monitor, analyze and track cyber threats to help protect our clients' systems and networks from attack. We also offer threat intelligence, analytical reports, anti-APT solutions, threat analysis and incident response services. Members have presented their research results at numerous global security conferences. See the website (https://teamt5.org/) for details.
About Macnica
Macnica is 1972 Since our establishment in 2013, we have provided cutting-edge semiconductors, electronic devices, networks, and cybersecurity products with added technological value. Based on our traditional strengths of global cutting-edge technology sourcing and technology planning capabilities, AI/IoT We are developing new businesses in fields such as , autonomous driving, and robots. "Co.Tomorrowing'', we will create social value and contribute to the development of future society as a company that provides unique services and solutions by connecting cutting-edge technology and Macnica 's intelligence. the Company is headquartered in Yokohama and is a worldwide twenty four countries 80 We are developing global business based on our bases. Detail is Web site(https://www.macnica.co.jp)Please refer to the.
Inquiries from the press regarding this matter
株式会社マクニカ https://www.macnica.co.jp
コーポレートマーケティング統括部 広報室 宮原、磯崎 e-Mail:macpr@macnica.co.jp
〒222-8561 横浜市港北区新横浜1-6-3 マクニカ第1ビル