About reports
Please note the analysis of attack campaigns that attempted to steal confidential information (personal information, policy-related information, manufacturing data, etc.) from Japanese organizations observed in FY2021 (April 2021 to March 2022). It is written for the purpose of awakening. Focusing on incidents using remote-controlled malware (RAT) with high stealth, it describes new attack methods and detection of their threats.
The report concludes with the indicators used in the attack campaigns featured in the text.
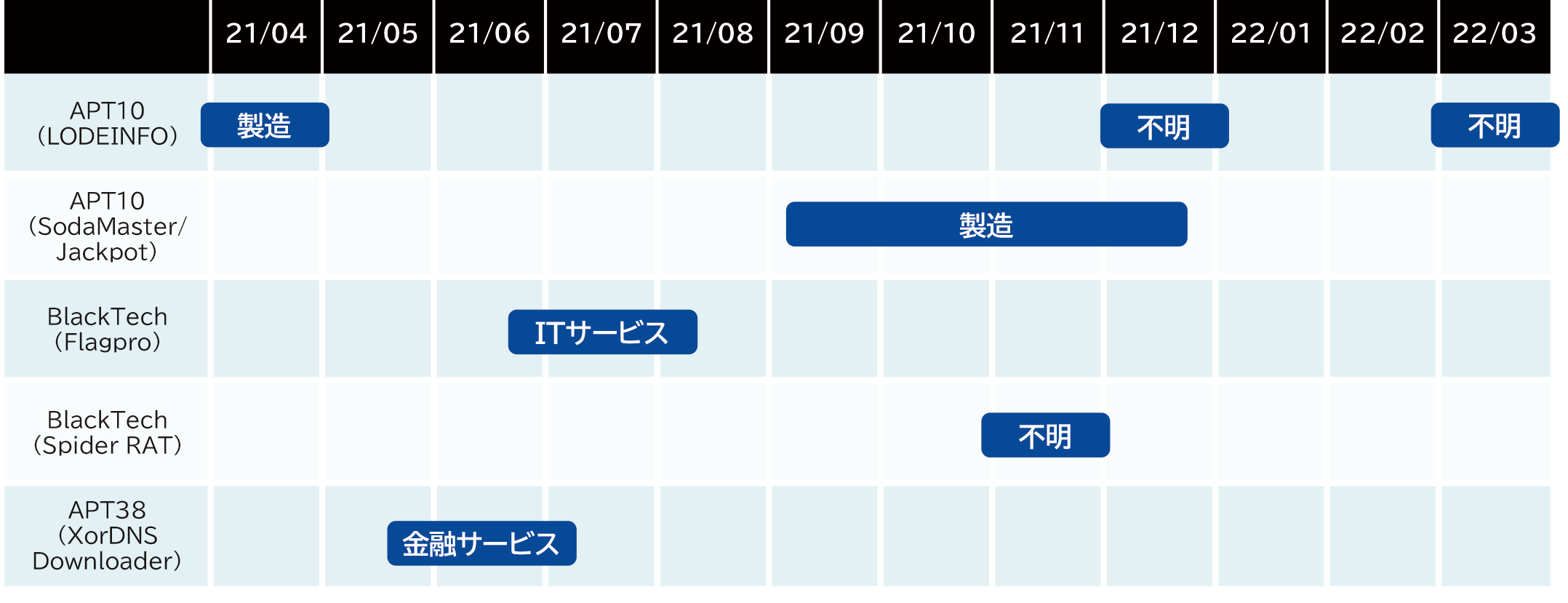
攻撃のタイムラインと攻撃が観測された業種
Attack trends in FY2021 are based on observations in FY2020. 1 LODEINFO malware of APT10 attack group continued from 2 attacks and the SodaMaster malware 3 4 A41APT attack campaign using 5 6 was continuously observed. In the A41APT attack campaign, SodaMaster and
There are two types of newly observed Jackpots. In addition, attacks by the BlackTech attack group were observed, although their activity had declined during last year's observations. However, it appears that the BlackTech group's initial targets were domestic companies and their Chinese bases. The BlackTech attack group has observed many attacks by PLEAD and TsCookie malware in Japan so far, but Flagpro 7 and SpiderR AT have been observed. In addition, the backdoor of the APT38 attack group 8 It is believed that attacks using . Overall, the number of attack groups has decreased from 6 groups to 4 groups, and the number of attack campaigns has decreased from about 10 campaigns to 7.
Table 1. Time chart
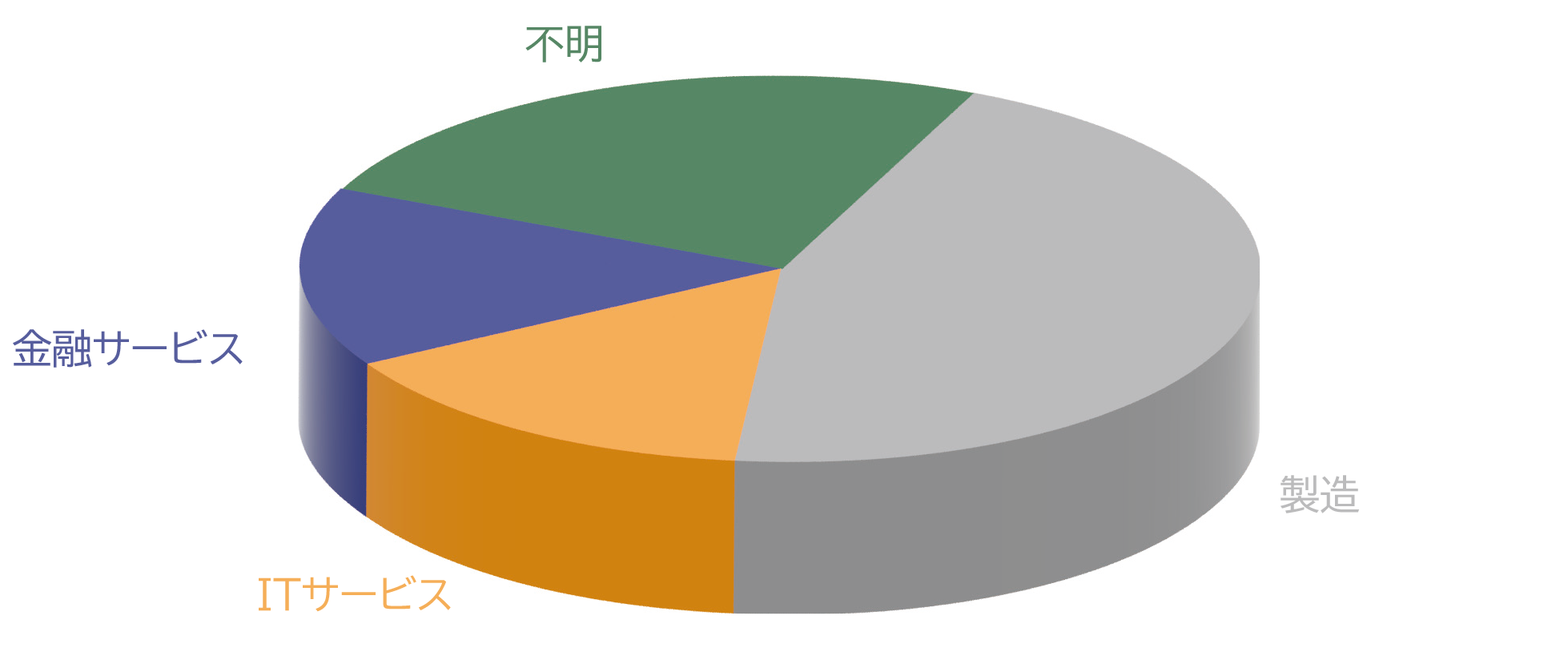
Throughout the year, we observed attacks using APT10's SodaMaster in manufacturing. In addition, since attacks using LODEINFO, which has mainly targeted the media, were also observed in the manufacturing industry, the observed ratio of targeted attacks in the manufacturing industry has increased significantly. Among other industries, IT services and financial services accounted for about the same percentage. In addition, although we obtained samples, the targets of APT10 LODEINFO etc. are not clear, and the proportion of unknowns is increasing. In the attack campaign using SodaMaster, the hosts where malware was installed were all Windows servers located overseas. The BlackTech attack group has seen attacks on IT service-related sites, etc., and it is believed that these activities were active with the aim of infecting bases in China. As a result, intrusions from overseas bases of domestic companies are on the rise. Attack methods include Office macro files attached to spear phishing emails aimed at infection, payloads used as remote control malware communicate with C2 and perform arbitrary commands and operations. There is no change or novelty in , and it is already not difficult to detect with current security technology. However, it is believed that attackers are attempting to steal intellectual property and information from domestic companies by attacking weakly-protected bases such as overseas where the detection technology is not applied.
In the industries described here, if possible, we would like affiliates and overseas bases to check and consider countermeasures by referring to the detection methods described in the latter half of this document. The statistics in this book are just the tip of the iceberg, so please refer to the attack methods described here and be vigilant.
- Introduction
- 攻撃のタイムラインと攻撃が観測された業種
- Attack summary
-
- April 2021 (Manufacturing)
- June 2021 (financial services)
- July 2021 (IT service)
- October 2021 (multiple production)
- November 2021 (Unknown)
- December 2021 (unknown)
- March 2022 (unknown)
- New TTPs, RATs, etc.
-
- APT10 (SodaMaster/Jackpot)
- Attack campaign using LODEINFO
- Attack campaign targeting BlackTech China base
- About attack groups
- TTPs (tactics, techniques, procedures) by threat group
- Threat Detection and Mitigation Considered from TTPs
-
- Malware Delivery/Attack
- Installed RAT, remote control (for C2 server)
- Expansion of intrusion/purpose execution
- Pyramid of Pain
- indicator of detection
1 https://www.macnica.co.jp/business/security/manufacturers/files/mpressioncss_ta_report_2020_5.pdf
2 https://blogs.jpcert.or.jp/ja/tags/lodeinfo/
3 https://blog.kaspersky.co.jp/apt10-sophisticated-multi-layered-loader-ecipekac-discovered-in-a41apt-campaign/30393/
4 https://blog.trendmicro.co.jp/archives/29842
5 https://jsac.jpcert.or.jp/archive/2021/pdf/JSAC2021_202_niwa-yanagishita_jp.pdf
6 https://jsac.jpcert.or.jp/archive/2022/pdf/JSAC2022_9_yanagishita-tamada-nakatsuru-ishimaru_jp.pdf
7 https://insight-jp.nttsecurity.com/post/102h7vx/blacktechflagpro
8 https://securelist.com/the-bluenoroff-cryptocurrency-hunt-is-still-on/105488/