
Okta
Octa
Introduction
Auth0 records administrator operations and user authentication processes as logs. This time, I will describe how to output the log to the outside.
<Purpose of log output>
- Long-term storage of Auth0 logs externally (because they are only stored within Auth0 for up to 30 days on the Enterprise plan)
- Use for analysis in cooperation with log analysis products, etc.
<Main output method
- Log Streams function
- Log output function in Webhook format
- Supports Splunk, Amazon EventBridge, Datadog, etc.
https://auth0.com/docs/customize/log-streams#supported-log-streaming-services
- Export Log Events with Extensions
- External log output function by batch processing using Auth0 extension
- Currently deprecated, scheduled for EOL in 2023
- Auth0 Management API
- Get logs by kicking the API from outside Auth0
- GET: /api/v2/logs
https://auth0.com/docs/api/management/v2/#!/Logs/get_logs
This page introduces the necessary settings and an example of log search and visualization on the Splunk Cloud side for Auth0 log storage using the Log Streams function with Splunk Cloud as the log output destination.
premise
The information on functions and settings described on this page is current as of November 2022.
In addition, Splunk Cloud uses the trial environment (Ver.9.0.2209.2) that can be issued from the following URL. In addition to the procedures on this page, additional settings such as IP address permission on the Auth0 side, which is the communication source, may be required when performing settings on the Splunk Cloud you are actually using.
https://www.splunk.com/ja_jp/download/splunk-cloud.html
Setting overview
The settings required for each of Auth0 and Splunk Cloud for storing Auth0 logs in Splunk Cloud are as follows.
- Add Log Stream configuration
- Log acquisition setting by HTTP Event Collector
- Splunk Cloud information settings for the output destination
- Auth0 log range setting for output target
From here, we will introduce specific setting methods and operation confirmation examples.
Setting Example
- On the Auth0 admin screen, click [Monitoring] > [Streams]
![Auth0管理画面において、[Monitoring] > [Streams]をクリック](/business/security/okta/image/okta_tech_auth0_log_dr01.png)
- Click Create Log Stream
- Click [Splunk] from the list
![Click [Splunk] from the list](/business/security/okta/image/okta_tech_auth0_log_dr03.png)
- Add any setting name and click [Create]
![Add any setting name and click [Create]](/business/security/okta/image/okta_tech_auth0_log_dr04.png)
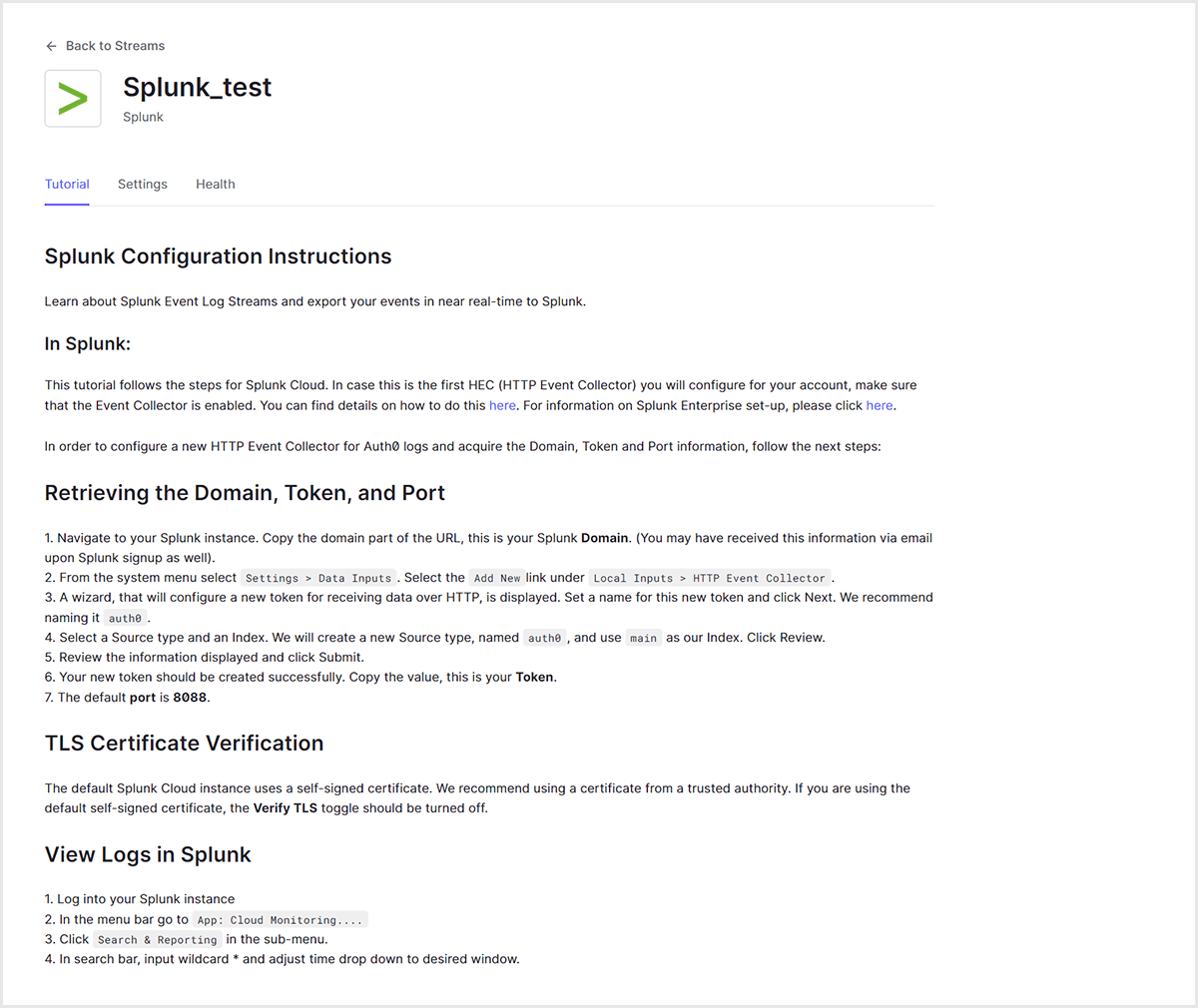
- Follow the setting procedure described in the Tutorial tab to set up Splunk Cloud (details are explained in 2. Splunk Cloud settings)
- On the Splunk Cloud screen, click [Settings] > [Data Input]
![Splunk Cloud画面において、[設定] > [データ入力]をクリック](/business/security/okta/image/okta_tech_auth0_log_dr06.png)
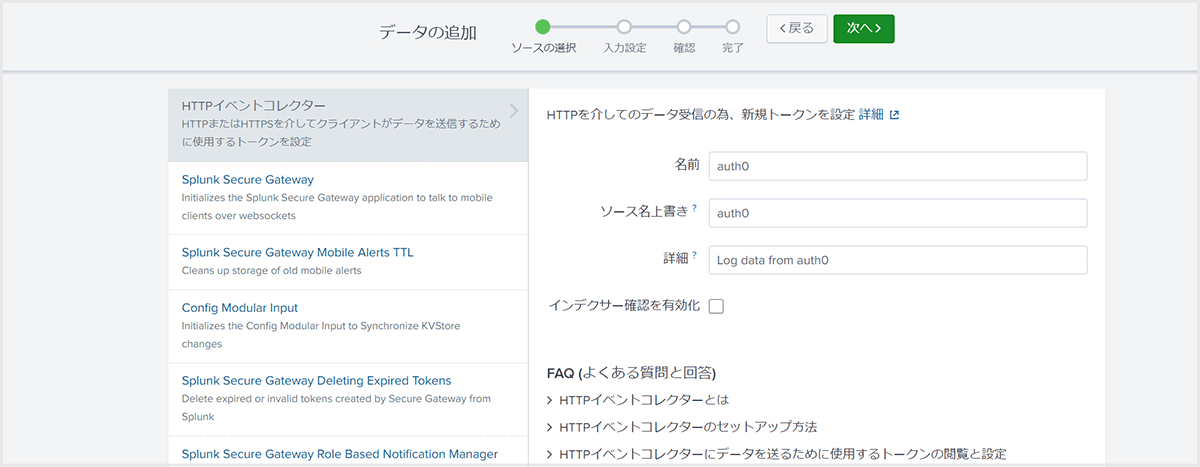
- Click [New] on the HTTP event collector
![Click [New] on the HTTP event collector](/business/security/okta/image/okta_tech_auth0_log_dr07.png)
- Specify setting name, source name, etc.
- Specify the source type name, storage destination index, etc.
*The applicable source type and storage destination index must be set in advance.
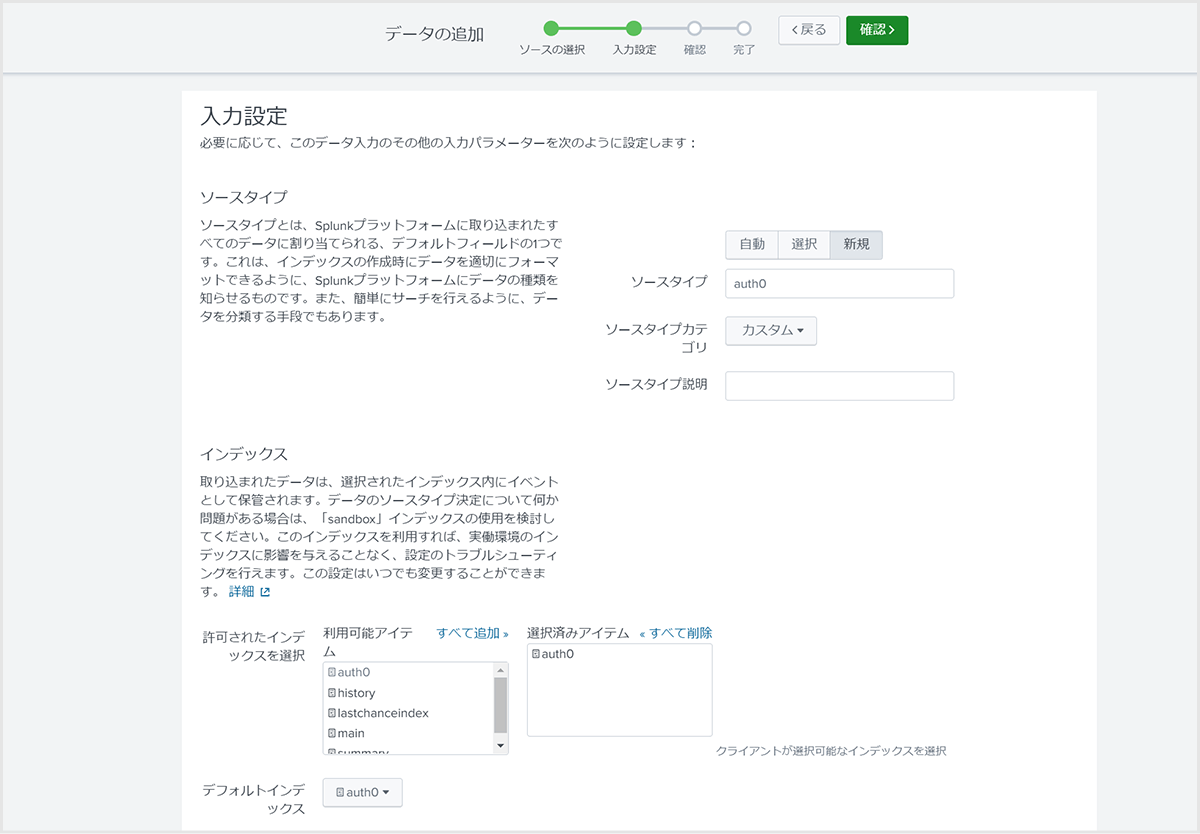
- After completing the settings, copy the displayed token value (used in 3. Auth0 settings (Part 2))
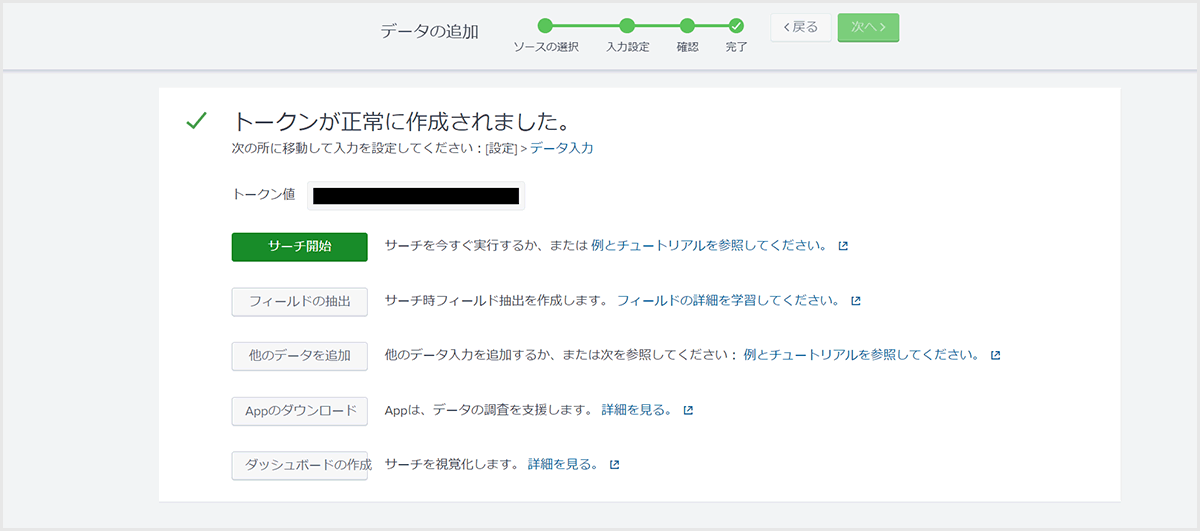
- After entering the necessary settings in the Settings tab of the Log Stream settings created in Auth0 settings (Part 1), click [Save].
- Domain: Splunk Cloud domain name to output to
- Token: Token value issued by Splunk Cloud
- Filter by Event Category: Select the filtering conditions for logs to be output from the default choices
*See below for options
https://auth0.com/docs/customize/log-streams/event-filters - Starting Cursor: If not specified, output will start from the log generated after this setting
![After entering the necessary settings in the Settings tab of the Log Stream settings created in Auth0 settings (Part 1), click [Save].](/business/security/okta/image/okta_tech_auth0_log_dr11.png)
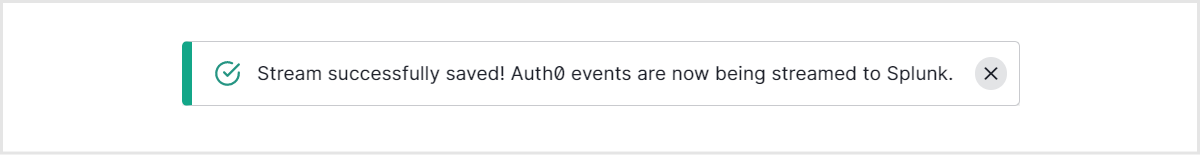
- Confirm that the settings have been saved successfully
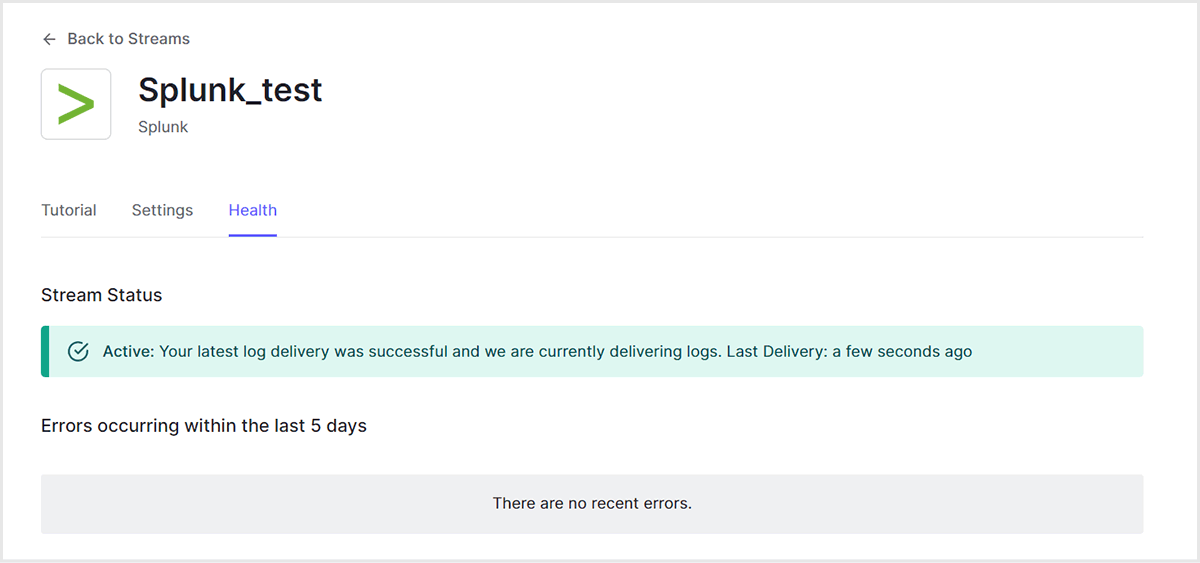
- Check that the Stream Status is Active and that no errors have occurred on the Health tab.
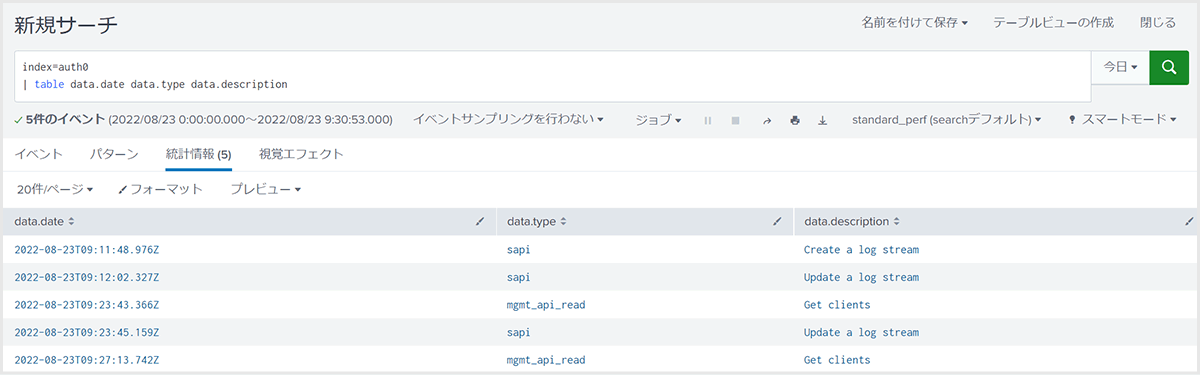
Operation confirmation example
Execute a search for the index that stores Auth0 logs on the Splunk Cloud search screen and confirm that search results are obtained.
Side note: Splunk App for Auth0 logs
Auth0 provides an "Auth0 app for Splunk" to visualize Auth0 logs in Splunk. See below for details.
https://splunkbase.splunk.com/app/5193
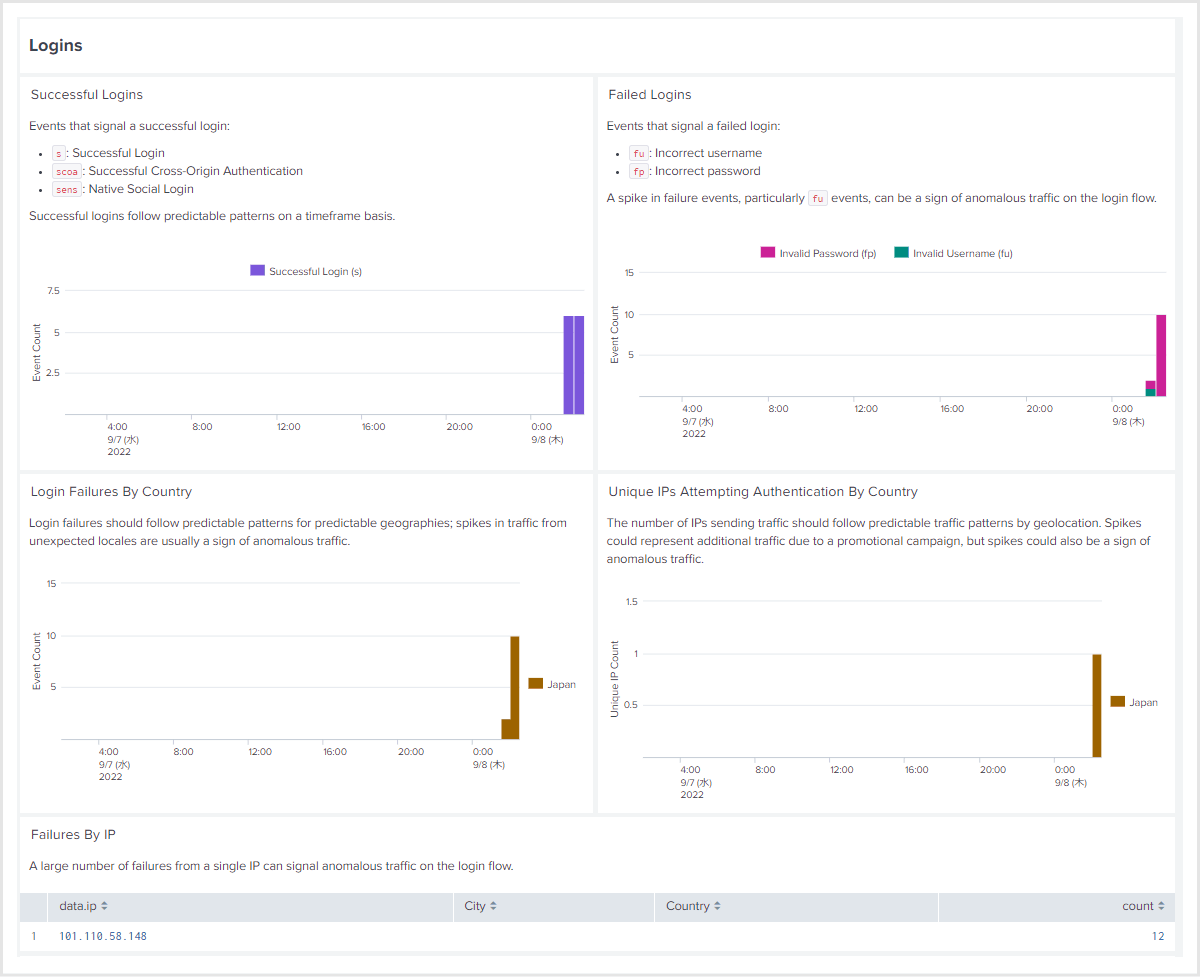
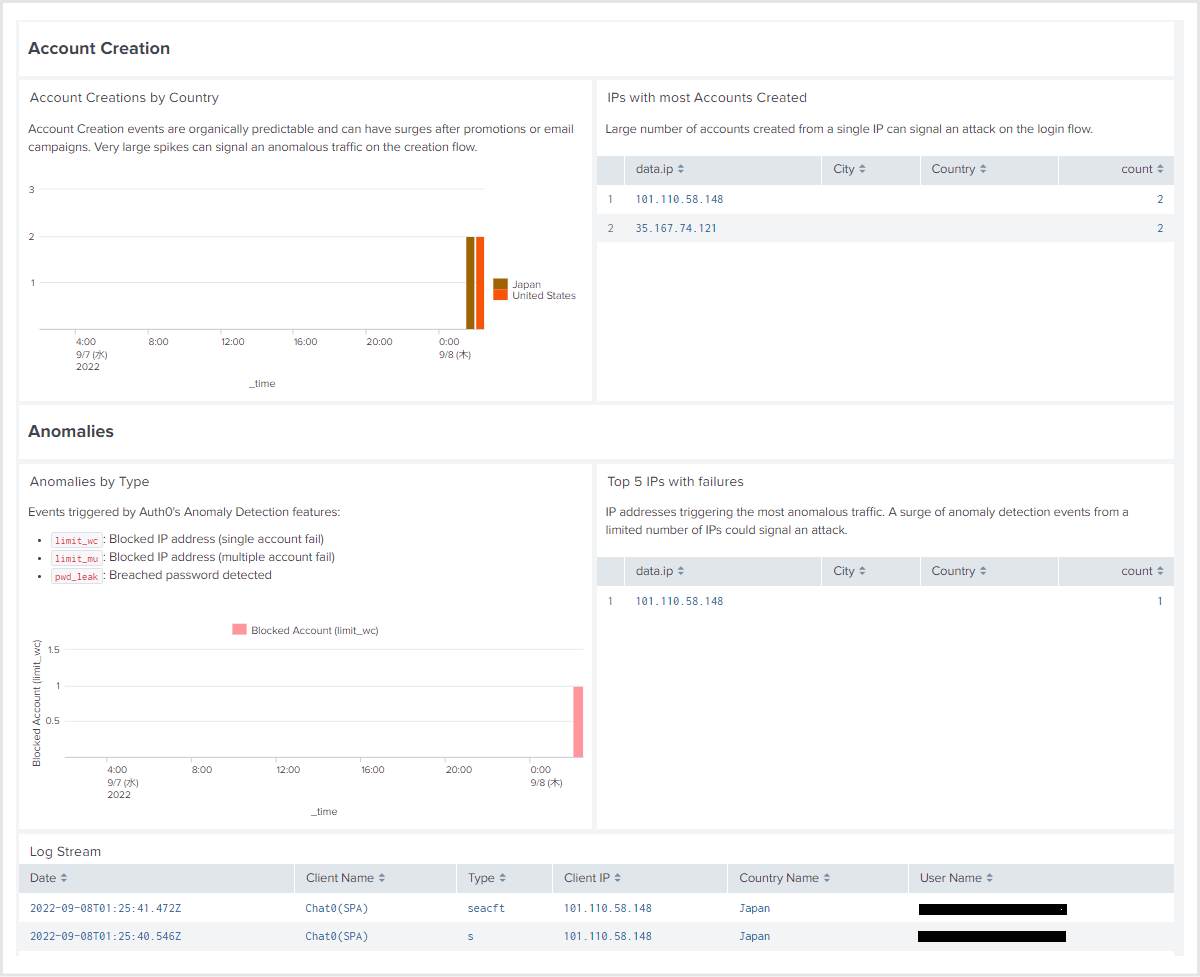
If you install the app on your Splunk, you can use the following dashboards.
Summary
Auth0 can output logs to various products and services other than Splunk Cloud introduced this time. If you are interested in linking with your existing log analysis product or using Auth0 logs, please contact us.
reference
Inquiry/Document request
In charge of Macnica Okta Co., Ltd.
- TEL:045-476-2010
- E-mail:okta@macnica.co.jp
Weekdays: 9:00-17:00