Fore Scout
ForeScout
Solution brief
feature
- Passive configuration without stopping critical systems
- Deep packet decoding of proprietary protocols for industrial control systems
- Mapping complex industrial networks
- Whitelist-based security detection with pre-learning
- Proprietary Industrial Threat Intelligence Delivery
Functions list
Use Case
- Identify devices and terminals in the system and manage information including vulnerabilities
- Graphical display of communication statistical data such as time series, type and rate, and volume during a specified period
- Categorize by device type and hierarchy, and graphically display the entire network
- Helps meet international and regional standards/guidelines (e.g. IEC 62443, NERC CIP, NIST Cybersecurity Framework, etc.)
- Real-time detection of external threats with a blacklist/whitelist in a passive configuration that does not affect plant operation
- By visualizing the communication direction, it is possible to grasp unwanted communication and find design mistakes.
- By visualizing the contents of communication at a deep level, it is possible to understand even the details of operations, and to detect operation errors in real time.
- Support for IT network protocols such as HTTP enables real-time detection of unauthorized access to important data/systems
Introduction image
Installation
- Easy deployment due to passive configuration


study period
- Learn communication content
- Enables ForeScout-defined security detections


Operation start
- Detects traffic that does not correspond to the profile set for each user by learning
- It is also possible to create scripts for each user.
Function introduction
Network map function
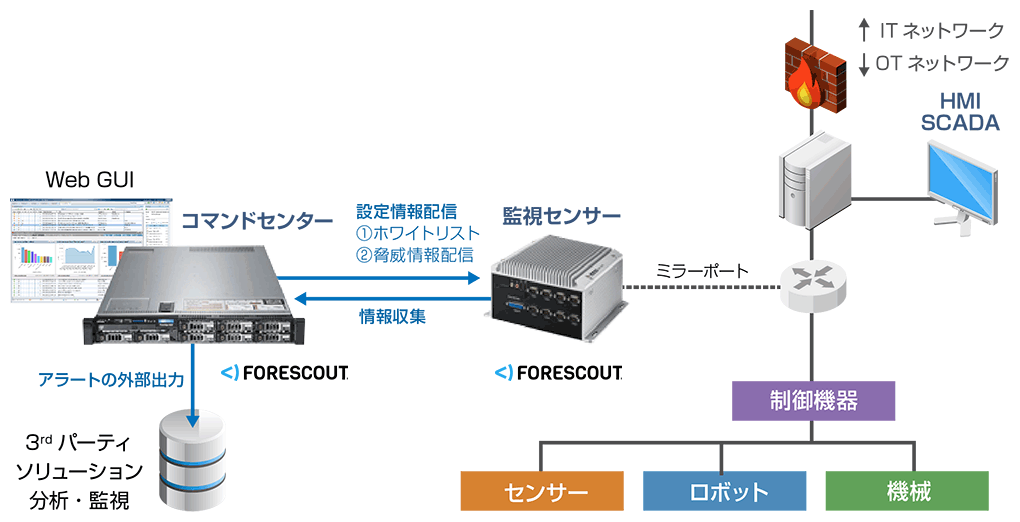
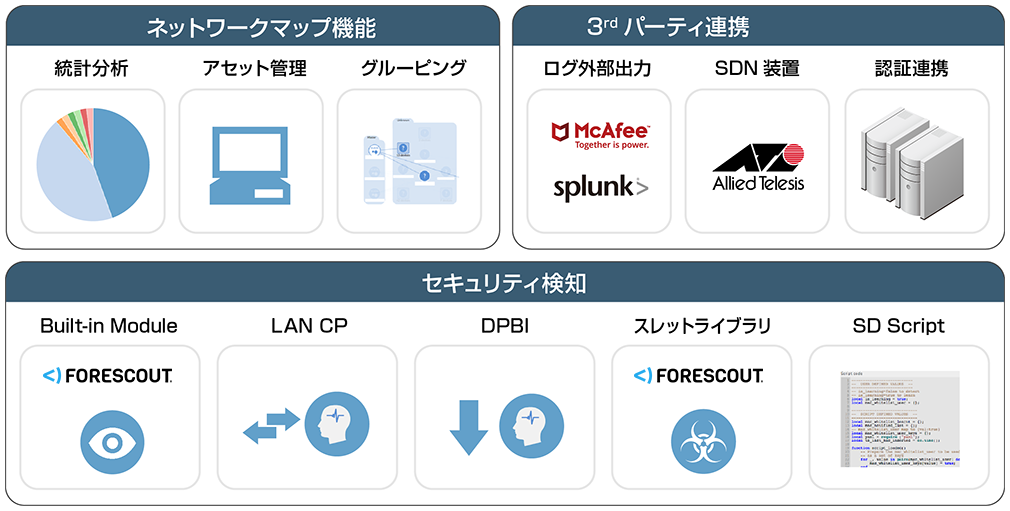
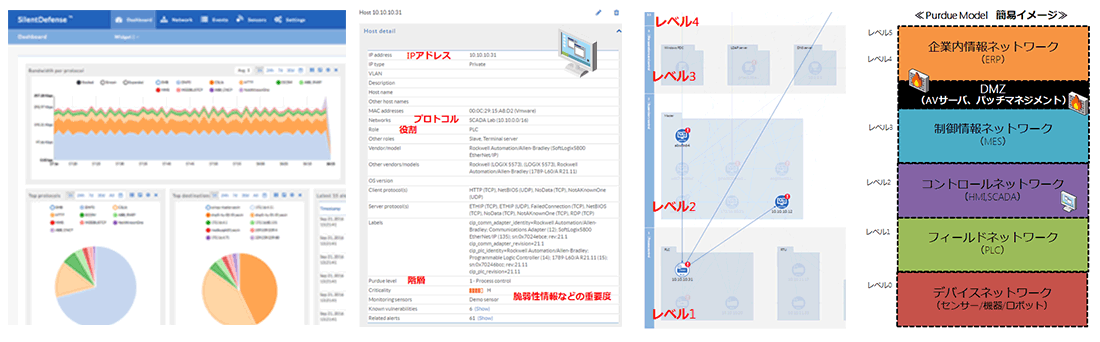
There is a network map function that graphically browses the network information collected by the monitoring sensors in the command center. With the network map function, what protocols are common in specific periods and specific communications? where is the contact? You can check network trends such as In addition, sniffed packets can provide detailed asset information such as model name, firmware version, vulnerability information, and inter-system protocols over the network to find inactive hosts and vulnerable PLCs. In addition, it is also possible to automatically group by role or network hierarchy. Assists in compliance with international and regional standards/guidelines (e.g. IEC 62443, NERC CIP, NIST Cybersecurity Framework, etc.).
security detection
There are detection logic implemented by ForeScout such as Built-in Module and thread library, and whitelist detection function by pre-learning such as LAN CP and DPBI. SD Script also allows users to write their own scripts in the LUA language. With this function, you can independently develop additional rules and implement rules for protocols and control devices that are not supported by SilentDefense.
| Function name | Overview | Usage | supplement |
| Built-in Module | Detect threats as defined by ForeScout |
|
|
| LAN CP | Whitelist detection based on communication direction |
|
|
| DPBI | Whitelist detection based on communication content |
|
|
| Thread library features | Detect threats as defined by ForeScout |
|
|
| SD Script | Detected by additional development by the user |
|
|
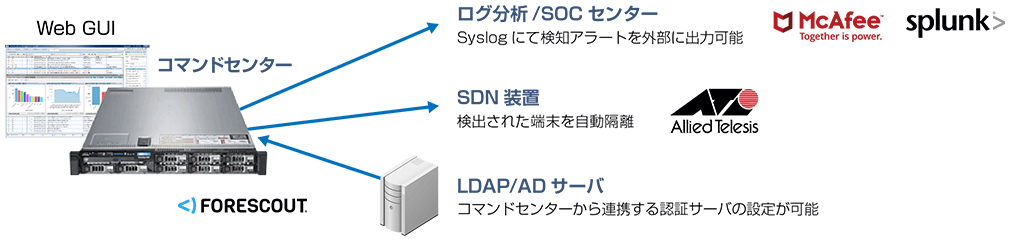
3rd party cooperation
Information obtained by SilentDefense can be output as a log. It is possible to output alert logs with Syslog to analysis tools such as ArcSight, Splunk, McAfeeSIEM, QRadar, etc., and output communication channels and status logs to Syslog servers. In addition, it is possible to import information from existing in-house authentication servers such as AD and LDAP for analysis based on user names.
movie
GUI operation image
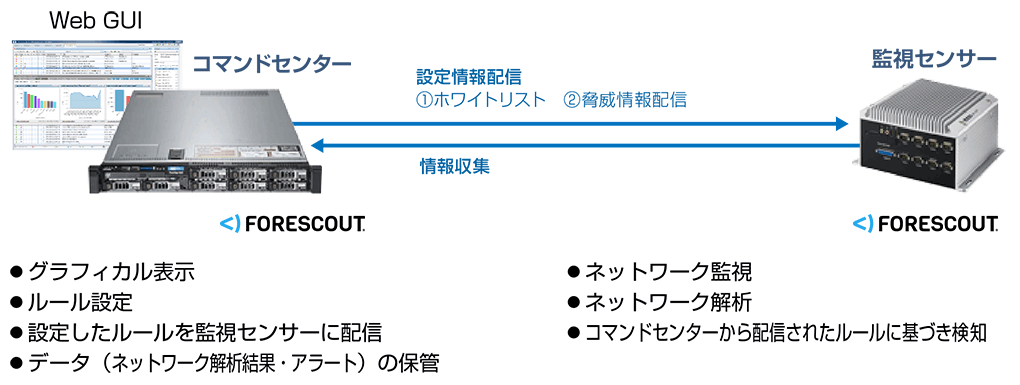
You can graphically view the network information collected by the monitoring sensor using the command center GUI, and configure the monitoring sensor settings using the command center GUI.
Security Detection: Built-in Module
The Built-in Module enables low-layer behavior detection and can be used without a learning period. Detection logic defined by ForeScout allows SilentDefense monitoring sensors to detect and alert.
Functions of Built-In Modules
- Detecting Man-In-The-Middle Attacks
- ARP spoofing
- ICMP redirect
- DHCP spoofing
- Detection of attacks that exploit low-level vulnerabilities
- Malformed Packed
- Discovery activity detection
- port scan
Security detection: LAN CP
LAN CP (The LAN Connection Profiler) is capable of detecting communication direction whitelist, and it is a function that requires prior learning. Create a profile of information such as the IP addresses and protocols (port numbers) of the systems that communicate during the learning period. After the learning period ends, you can monitor communications and detect anomalies based on the created profile.
Security Detection: SD Script
With SD Script, customers can write their own scripts in the LUA language (LUA language is used in game development and various industrial applications). With this function, detailed analysis and detection can be performed by independently developing additional protocols and control devices that are not supported by SilentDefense.
Threats in industrial control systems
Product offer
| command center | surveillance sensor | |
| role |
|
|
| Form of provision |
|
|
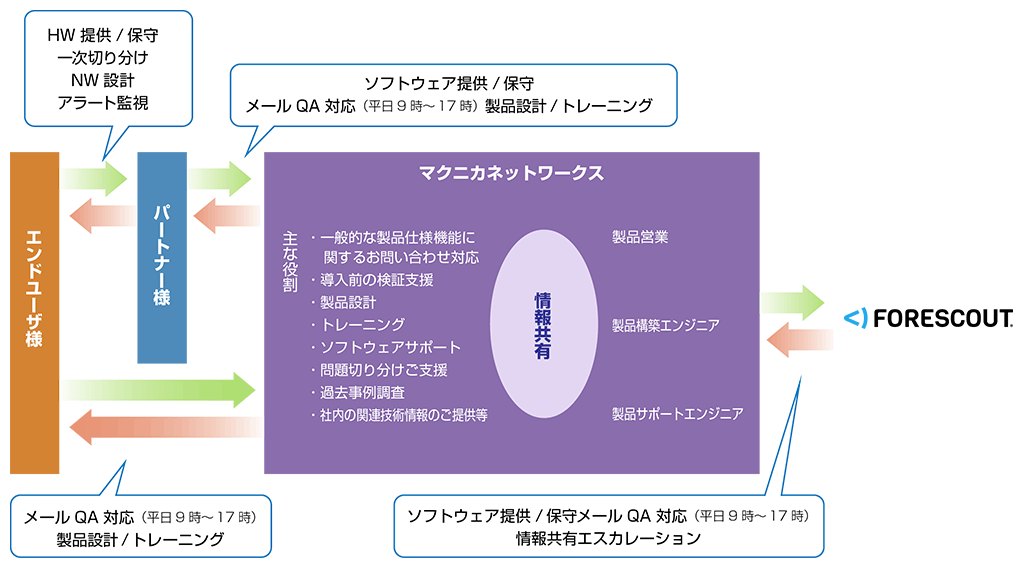
Product provision scheme
The product provision scheme for SilentDefense is as shown below. Macnica provides verification support before installation, product design and training during installation, software support and related information via email from 9 a.m. to 5 p.m. on weekdays.