Macnica Networks Corp. (hereinafter referred to as Macnica networks, head office: 1-5-5 Shin-Yokohama, Kohoku-ku, Yokohama, Kanagawa Prefecture, President: Jun Ikeda) analyzes threats targeting Japanese organizations on a daily basis and provides security solutions. ), which is headquartered in Taiwan and has threat intelligence for cyber espionage activities conducted in the Asia-Pacific region, and Team T5, Inc. (hereinafter referred to as TeamT5, CEO: Sung-ting Tsai), which is headquartered in Taiwan and has threat intelligence for cyber espionage activities conducted in the Asia-Pacific region, and Continuing from last year, we will be co-authoring and publishing a research report on attacks titled ``Actual Status of Targeted Attacks and Countermeasure Approaches.''
In fiscal 2020, telework was promoted, and many security incidents took advantage of this gap. Among them, targeted attacks (cyber espionage) that land in Japan for the purpose of information theft threaten to deprive Japanese companies of their competitiveness and reduce their international industrial competitiveness. Many organizations are unaware of this. Japanese companies need to obtain information on attack campaigns that attempt to steal sensitive information (personal information, policy-related information, manufacturing data, etc.) and prevent information leakage through early detection.
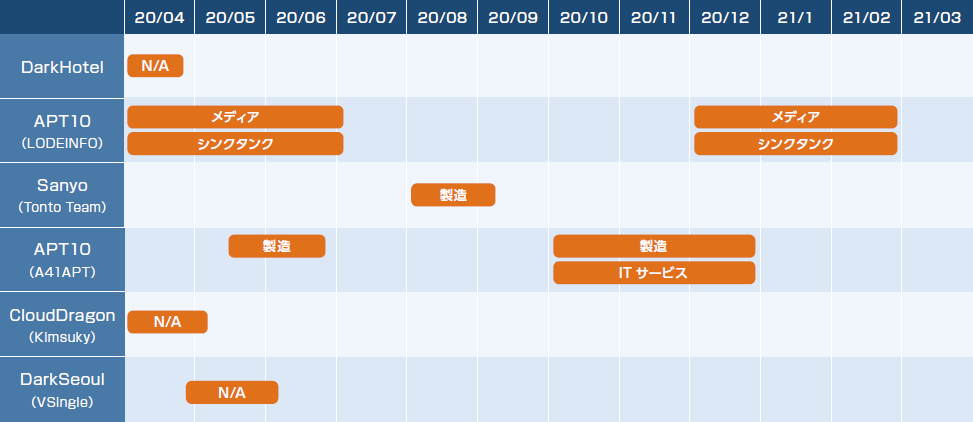
In terms of attack trends in FY2020, compared to the observations of the previous year, the activities of the Tick and BlackTech attack groups targeting domestic organizations, which were relatively active in FY2019, declined, and the APT10 attack group using LODEINFO malware, Actively observed attacks by the reported APT10 threat group of the A41APT attack campaign.
Time chart
As with previous observations, there was an observation of attack activity believed to be carried out by the DarkHotel attack group in the first half of the year, and we analyzed that new attacks using the CloudDragon (Kimsuky) and DarkSeoul attack group's VSingle* malware were being carried out against Japan. increase. Throughout the year, we also saw active attacks targeting media and think tanks of the APT10 threat group using the LODEINFO malware. On the other hand, we also observed the A41APT attack campaign in which several different payloads (SodaMaster, P8RAT, Cobalt Strike Stager Shellcode, xRAT) were deployed in memory from the same type of loader (DES_Loader) of the APT10 attack group. Many of the targets observed in the A41APT attack campaign were multiple manufacturing industries and IT services, and according to public information on the A41APT attack campaign, other industries such as the government, medical care, and clothing-related industries were also targeted. Our analysis suggests that this was the most active attack group targeting Japan.
*At Macnica networks, the attack group using the VSingle malware is analyzed based on its characteristics as an attack group related to DarkSeoul within the Lazarus attack group.
Pie chart of target organizations (FY2020)
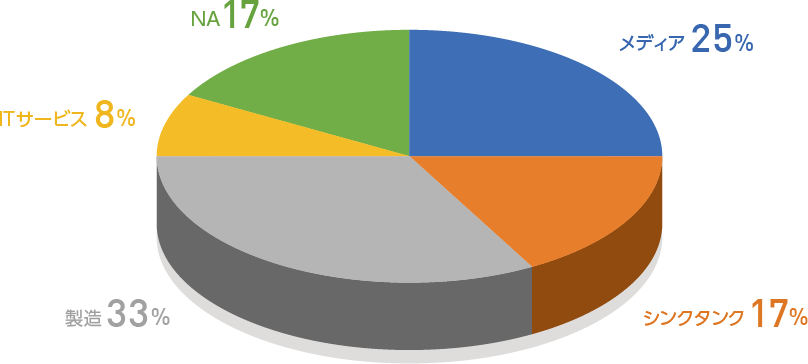
In terms of target organizations, the ratio has increased as attacks using APT10's LODEINFO malware targeted media and think tanks throughout the year. APT10's A41APT attack campaign has many observations in the manufacturing industry, but it is a fairly difficult category to detect among targeted attacks, and industries such as government, healthcare, and clothing that are not included here also need to be careful. . In this attack, there was no intrusion from spearfish emails, and most of the terminals infected with malware were the server OS of domestic companies, including overseas affiliated companies, and the number of infected devices was small, and the IP address of the C2 server was different for each infected host. Therefore, it is difficult not only to intrude into bases where countermeasures are weaker than the headquarters network of domestic companies, but also to detect static IOCs such as hash values and IP addresses.
Details are explained in the report, so please check it. The second half of the report includes detection methods, so please refer to them when checking your own organization. Macnica networks will continue to persistently analyze and educate people about targeted attacks that are gradually eroding the industrial competitiveness of Japanese companies, and strive to contribute, however small, to the development of the Japanese economy.
“Targeted Attacks and Countermeasure Approaches 5th Edition-Trends of Cyber Espionage Targeting Japan 2020-” Table of Contents
- Introduction
- 攻撃のタイムラインと攻撃が観測された業種
- Attack summary
-
- April 2020 (media, think tank, N/A)
- May 2020 (N/A)
- June 2020 (Manufacturing)
- August 2020 (Manufacturing)
- October-December 2020 (multiple manufacturing industries, IT services)
- December 2020-February 2021 (media, think tank)
- New TTPs, RATs, etc.
-
- Cloud Dragon (Kimsuky)
- A41APT Attack Campaign Post-Intrusion Attack Tools
- Attacks that appear to target security officials
- Collaboration of attack groups based in Chinese-speaking countries (Sanyo, Tick, Winnti Group)
- LODEINFO Evolving Attack Campaigns
- About attack groups
- TTPs (tactics, techniques, procedures) by threat group
- Threat Detection and Mitigation Considered from TTPs
-
- Malware Delivery/Attack
- Installed RAT, remote control (about C2 server)
- Expansion of intrusion/purpose execution
- indicator of detection
Report download destination
https://www.macnica.co.jp/business/security/manufacturers/mpressioncss/feature_07.html/
Macnica networks also provides information on other attacks, vulnerabilities, and security solutions. The Macnica Security Forum 2021 is currently being held from May 17th ~ 21st. We hope you will join us as well.
Inquiries regarding this matter
株式会社マクニカ
セキュリティ研究センター
TEL:045-476-2010
E-Mail:mss@cs.macnica.co.jp
TeamT5 Company Profile
TeamT5 is one of the world's leading malware analysis teams and the best solution provider for cyber espionage in the Asia Pacific region. We monitor, analyze and track cyber threats to help protect our clients' systems and networks from attack. We also offer threat intelligence, analytical reports, anti-APT solutions, threat analysis and incident response services. Members have presented their research results at numerous global security conferences.
| company name | Team T5, Inc. |
| Head office location | Taiwan Taipei No. 46, Ln. 11, Guangfu N.Rd., Songshan Dist., 105Taipei City, Taiwan |
| CEO | Sung-ting Tsai |
| website | https://teamt5.org/ |
| Business content | Providing services such as threat intelligence services, development of targeted attack countermeasure solutions, and incident response services |
Media contact information
Macnicahttps://www.macnica.co.jp/
TEL: 045-476-2010
〒222-8562 横浜市港北区新横浜1-5-5
広報担当 磯崎(いそざき)
メールアドレス:macpr@macnica.co.jp
*Company names mentioned in the text are registered trademarks or trademarks of their respective companies.