Introduction
What is Confidential Computing
A technology for protecting sensitive data in an Application during processing.
Sensitive data is usually stored in memory in plaintext during processing, so there is a risk of exfiltration of sensitive information in the event of an attack on memory. Confidential Computing uses Intel SGX to encrypt data in memory even during processing to reduce the risk of leaking confidential information.
The Importance of Confidential Computing
Data exists in three states: at rest, in use, and in transit. Data being stored is "at rest", data being processed is "in use", and data passing through the network is "in transit".
Encryption of data at rest and in transit over a network has become commonplace, but encryption of data "in use" is still relatively uncommon. Data is vulnerable to unauthorized access and tampering at runtime. Therefore, it is important to protect data “in use” with Confidential Computing to provide complete security throughout the data lifecycle.
Product Summary
Confidential Computing Manager™
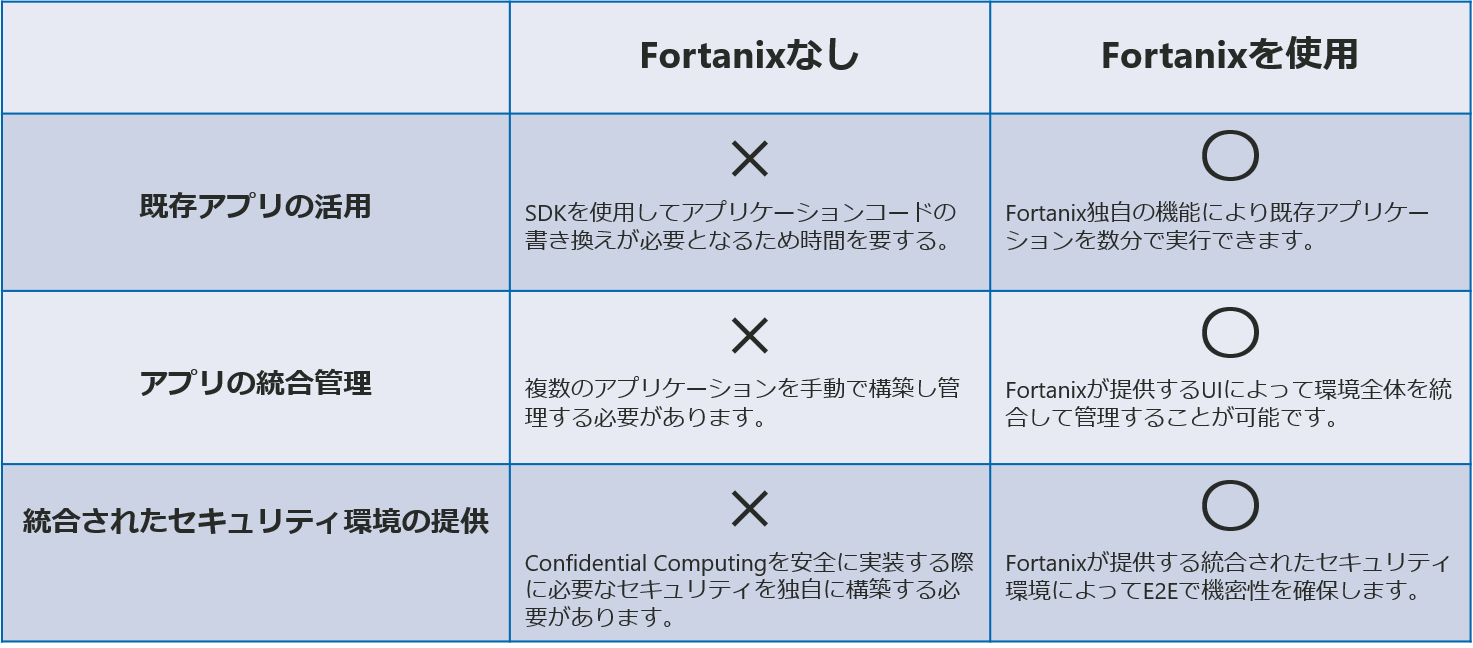
● Confidential Computing Manager is the easiest solution to provide application protection.
● We also provide an integrated platform for batch management of apps.
● Also, existing applications can be used without modifying, rewriting, or recompiling.
Use Case
- Protecting Healthcare AI
Inquiry / Quotation
If you have any questions about this product or would like a quote, please contact us using the form below.
Fortanix Manufacturer Information Top
If you want to return to Fortanix manufacturer information TOP, please click below.
