We will explain several times about security, which is often asked in the support of Bluetooth product development.
In the first installment, I will explain the relationship between security and pairing, and the differences between BLE (Bluetooth Low Energy) BT4.1 and earlier and BT4.2 and later.
Security and pairing
In order to perform secure communication (encryption/signature) with Bluetooth (BT), an operation called pairing, which is familiar to everyone, is required, such as connecting a smartphone to a BT earphone for the first time. Key information required for encryption and signature is exchanged in the pairing operation.
By the way, in Classic BT, pairing is required for data transmission and reception, but in BLE, it is treated as an option, and it is possible to connect and transmit data without pairing.
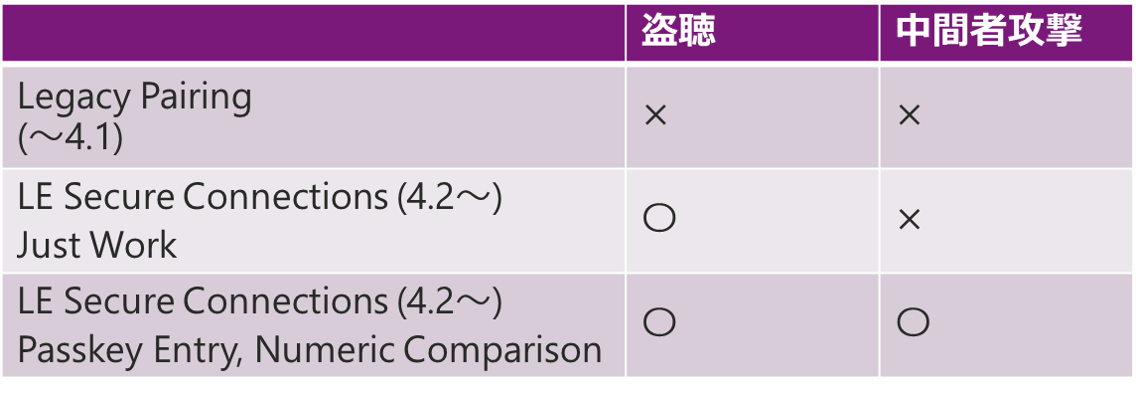
Difference between before BT4.1 and after BT4.2
Regarding BLE security, the strength of security is completely different between BT4.1 and earlier (Legacy Paring) and BT4.2 and later (LE Secure Connections Paring), so care must be taken during product design and development. LE Secure Connections Paring (LESC) uses a new public-key cryptography mechanism to improve security against eavesdropping in the BLE wireless section.
Below is a table summarizing the contents of this article + α.
In the next article, I will explain the differences in security resistance to man-in-the-middle attacks and authentication methods (Association models) such as Just Works, Passkey Entry, and Numeric Comparison.
Inquiry
If you have any questions regarding this article, please contact us below.
To Microchip manufacturer information Top
If you want to return to Microchip manufacturer information top page, please click below.
Free online seminar
If you know this, you can develop Bluetooth products! Seminar for Bluetooth Beginners 2021/5/18 (Tue)
