Authenticity determination using security IC
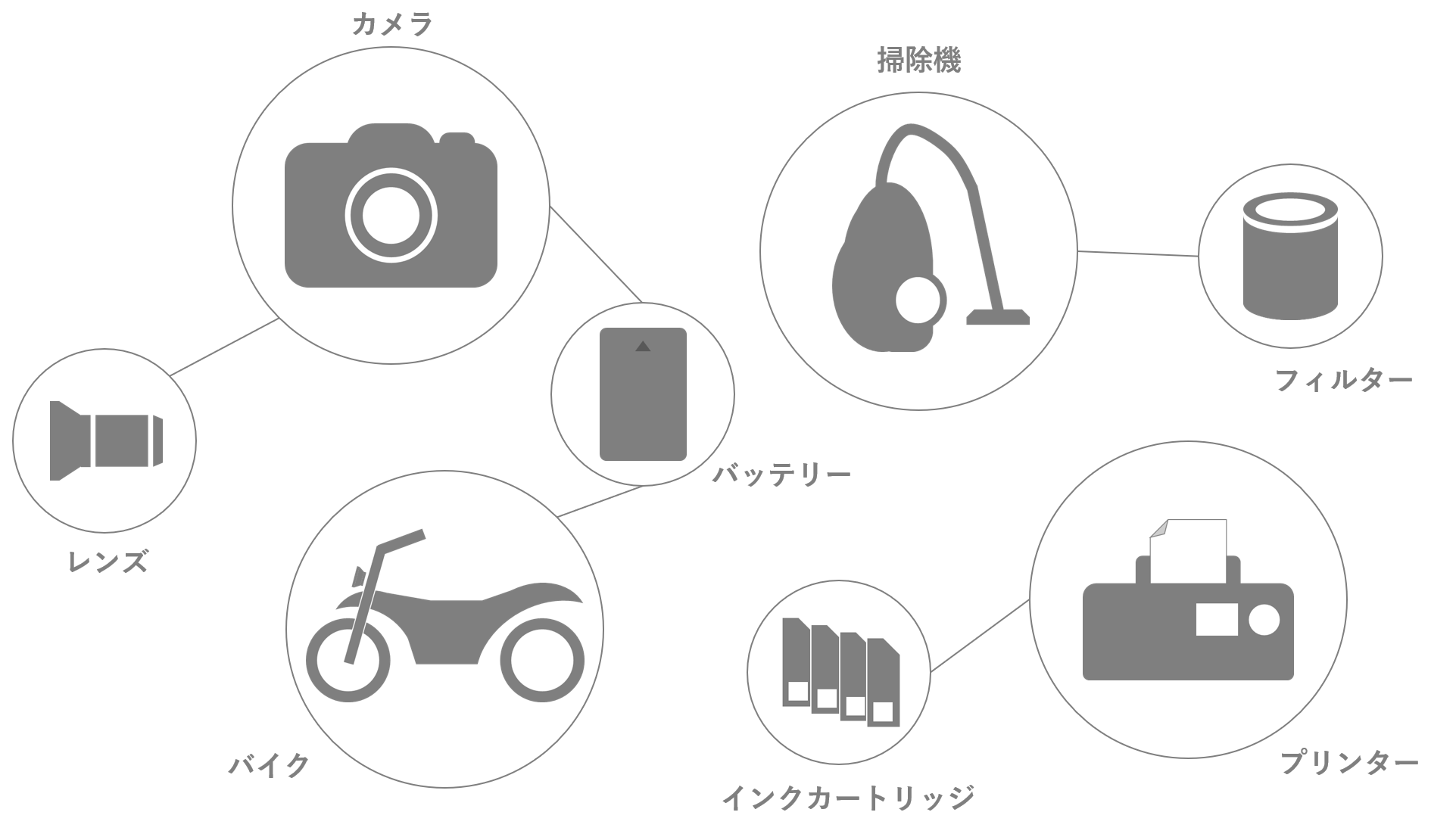
Various consumables and accessories exist in the world, such as batteries, ink cartridges, filters, and camera lenses. However, it is also true that there are many counterfeit products. It is also important for companies to protect their brand image from counterfeits that can cause malfunctions or compromise customer safety.
Infineon provides OPTIG A™ Authenticate S, the optimal security IC for authenticity determination, based on the security knowledge accumulated over many years.
Certification examples for various products
OPTIG A™ Authenticate S measures 1.5 x 1.5 x 0.38 mm and can be connected to the host with two terminals, making it easy to mount on various consumables/accessories.
Features of OPTIGA™ Authenticate S
OPTIGA™ Authenticate S has the following features.
- Distinguish between genuine and counterfeit products - when using counterfeit products, it is possible to limit functions
- Two interfaces to choose from (SWI or I2C)
- Notification of replacement/maintenance time by down counter
- Disable authentication function for used products (Kill function)
- Counter reset by authorized recycling vendor
- In addition to device-side authentication, host-side authentication is also possible (one-way authentication or two-way authentication)
demo video
Connection Example Block Diagram ~Camera and Battery~
An example of connection between the camera and the battery is shown on the left.
OPTIGA™ Authenticate S is embedded in the battery, which has a connection point with the camera, and authentication challenge and response is performed by SWI or I2C communication to determine the authenticity of the battery.
authentication sequence
OPTIGA™ Authenticate S employs a two-step authentication method that uses a 193-bit digital certificate ODC (OPTIGA™ Digital Certificate) and a 163-bit ECC (Elliptic Curve Cryptography).
The one-way authentication sequence is performed in the following procedure.
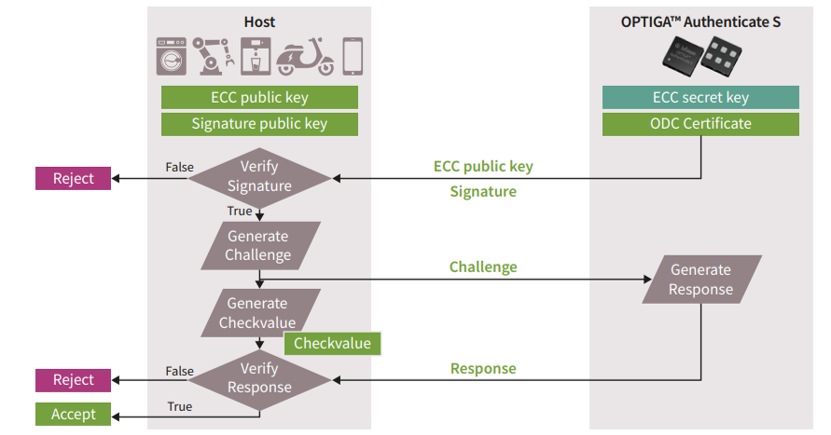
- Have the ODC public key on the host side (securely passed from Infineon's factory to the customer)
- Have an ECC key pair on the device side (ODC is attached to the ECC public key)
- Pass ECC public key from device to host
- Verify the ODC attached to the ECC public key on the host side (use the ODC public key that you already have)
- If the ODC verification succeeds, the generated random number is encrypted using the ECC public key and passed to the device (challenge)
- The device side decrypts using the ECC private key and returns it to the host (response)
- Check the response on the host side and determine if the device is genuine
Evaluation and development kits (NDA required)
The evaluation kit allows you to check the operation of OPTIGA™ Authenticate S using the GUI for Windows.
For the development kit, we can provide an SDK that can be used on the integrated development environment "ModusToolbox™" provided by Infineon.

Product detail page
Inquiry
Infineon manufacturer information TOP
If you want to return to Infineon manufacturer information TOP, please click below.
