Next-generation antivirus (NGAV),
Protect your company from advanced cyberattacks!


CrowdStrike Falcon Prevent (NGAV) Free Trial
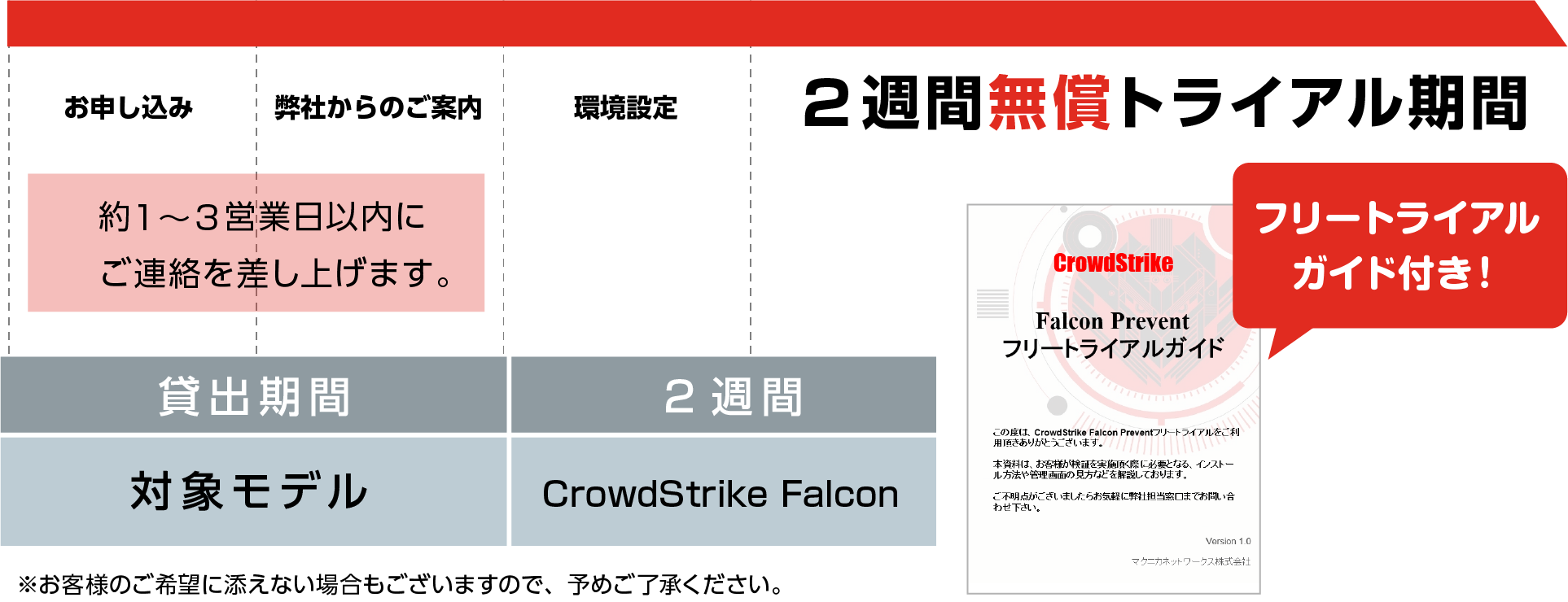
For customers who are considering purchasing CrowdStrike Holdings、Inc. 's CrowdStrike Falcon,
You can evaluate it in the production environment first before introducing it.
We will diagnose the customer's production network and propose an operation method for the detected event.
様々な分野の企業で導入実績多数




2019 “An endpoint protection platform
About
in the Magic Quadrant
Leader position
* In Completeness of Vision in Our Magic Quadrant Research
Rated as the highest position.
Gartner, Magic Quadrant for Endpoint Protection Platforms, Peter Firstbrook et al., 20 August 2019
Gartner does not endorse any vendor, product or service depicted in any Gartner Research publication. Nor does it advise technology users to select only those vendors with the highest ratings or other designation. Gartner Research publications consist of the opinions of Gartner Research and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Information system personnel have



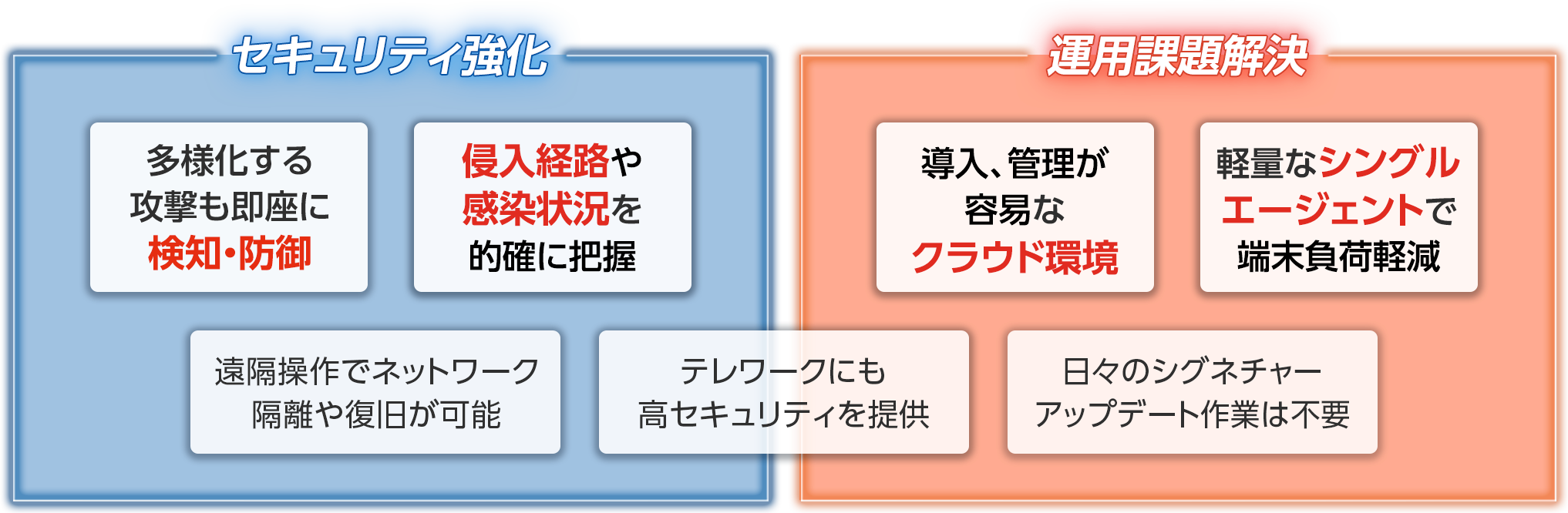
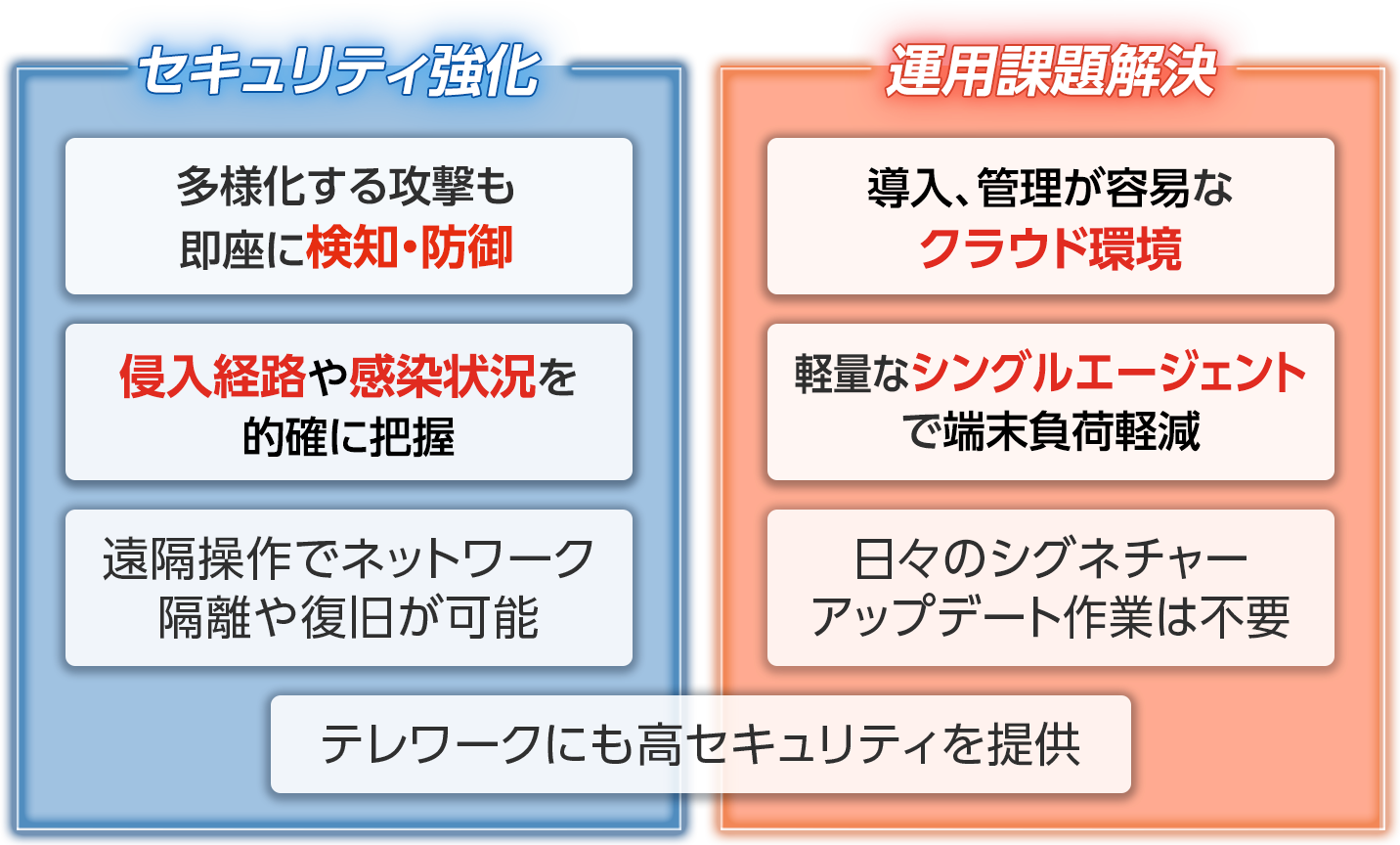
Attacks that are difficult to detect and defend against are on the rise, and countermeasures cannot keep up

The intrusion route is unclear and cannot be identified, making it difficult to deal with and prevent recurrence

Immediate response/restoration is not possible when an incident occurs

Periodic scans, pattern file updates, etc. put a load on the device

Server maintenance puts a lot of burden on administrators

All solved!
Task 1……
Attacks that are difficult to detect and defend against are on the rise, and countermeasures cannot keep up
Detect and block attacks with machine learning, AI, and behavior.
Since attacks are detected by machine learning, AI, and behavior, it is possible to detect not only malware but also fileless attacks. In addition to detection, it has blocking functions such as automatic quarantine of detected files and automatic termination of malicious behavior.
In addition, detection and blocking can be performed in an offline environment, and blocked malware can be immediately quarantined in a safe format.

Task 2……
The intrusion route is unclear and cannot be identified, making it difficult to deal with and prevent recurrence
It is possible to visualize the process before and after the attack and easily understand the intrusion route.
Not only can you detect and block attacks, but you can also investigate their alerts. Conventional anti-virus products do not know the intrusion route and cannot take countermeasures. .
Visible process activity
- Process detection time/execution user name
- Detection summary
(what was detected and why) - attack method used
- History of executed command lines
- File Path
- hash value
- Process start and end time
- Quarantined file details
- User details
(login time, login domain, etc.) - host details
(OS, local IP, MAC address, etc.) - Network communication history
- History of registry operations
- File read/write history

Task 3……
Immediate response/restoration is not possible when an incident occurs
When an incident occurs,
2 clicks from remote terminal
Enables network isolation and recovery
If you need to take action, you can isolate the terminal from the network with two clicks from the alert investigation screen. In addition, remote operations using commands such as obtaining/deleting files and checking/deleting registries can also be performed. Since the administrator can remotely deal with and restore the problem, there is no need to collect the terminal, and immediate action can be taken. *Please note that this function must be added as an option.

Task 4……
Periodic scans, pattern file updates, etc. put a load on the device
signatureless
With lightweight agents,
Reduced load on terminals
Since it uses a machine learning engine that does not rely on signatures, the data written to the disk is as light as several tens of megabytes, and the CPU usage rate during operation is less than 1%, which is a low load on the terminal.

Task 5……
Server maintenance puts a lot of burden on administrators
To provide a complete SaaS type,
Daily signature updates
No maintenance required including
Since it is provided as a complete SaaS type, there is no need to set up an in-house management server, eliminating the need for server maintenance. In addition, the signature-independent specification eliminates the need for daily signature updates.

Falcon Prevent
demonstration
In addition to being able to grasp the intrusion route and the series of process movements at a glance with the highly visible process tree,
We will introduce an alert screen that allows you to check the detailed information of each process according to the attack scenario.
CrowdStrike Falcon Prevent (NGAV) Free Trial
For customers who are considering purchasing CrowdStrike Holdings、Inc. 's CrowdStrike Falcon,
You can evaluate it in the production environment first before introducing it.
We will diagnose the customer's production network and propose an operation method for the detected event.

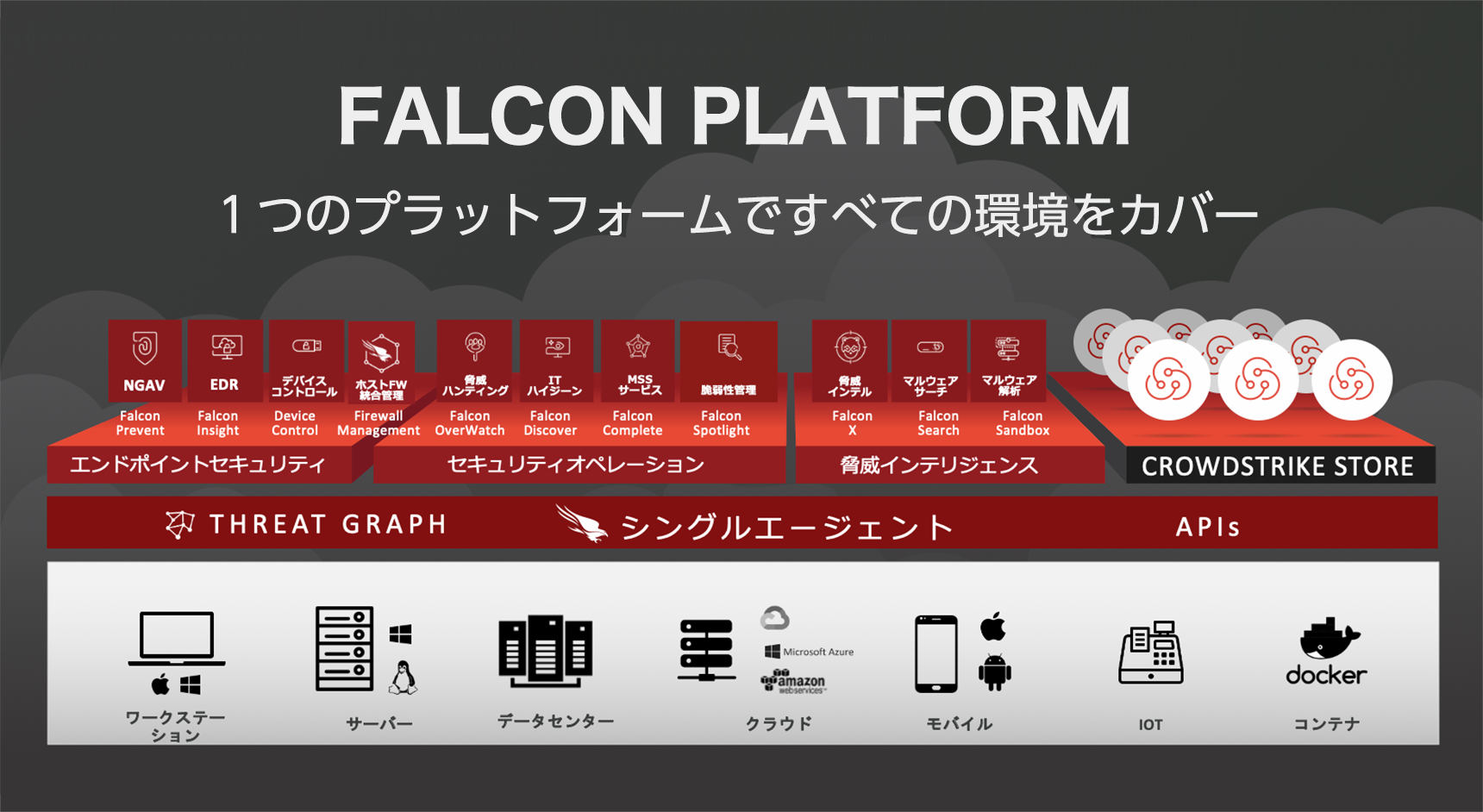
Provide comprehensive endpoint protection

No more multiple agents, multiple management consoles to keep you secure.
As a cloud-based endpoint security platform, it offers not only NGAV and EDR, but also threat hunting services, device control, and asset management by a professional group of cyber attack analysis with a single agent. Even if you want to add functions, there is no need for additional environment construction or work, so you can easily add functions. A simple architecture optimized for the cloud provides countermeasures against ever-evolving threats.
Industry-leading EDR that sees through all the actions of attackers
Operation logs are uploaded to the cloud in real time from the terminal, so even if the attacker erases the traces, it is possible to grasp all the actions.
In addition, we have many dashboards that visualize the behavior on the terminal that is necessary for incident response, so you can quickly find the information you want. In addition, it is possible to visualize a series of attacks by attackers, including lateral expansion activities, and alert investigations, including identification of the scope of impact and investigation of intrusion routes, are possible on a single screen.
24/7 surveillance with intelligence
We have our own intelligence, and our intelligence team monitors over 130 attacker groups around the world every day. We also collect 3 trillion event logs per week from Falcon sensors in 176 countries around the world, making our intelligence stronger by collecting them in one place. That intelligence is tied to Falcon, so you can always protect your customers with products that respond to the latest threats.
In addition, with Falcon Overwatch capabilities, CrowdStrike Holdings、Inc. 's threat hunting team is available 24/7 to proactively hunt and investigate threat activity in your environment. They can detect advanced attacks that machines cannot.
User case
- ・ Responds to unknown/known malware, ransomware, and fileless attacks
- ・ It is possible to reduce the initial investment and expand the functions in stages.

- ・By ranking each threat, the targets to be prioritized are clarified.
- ・When conducting a survey, you can quickly grasp the flow of the process

- ・ Realize EDR and NGAV with one agent
- ・ Supports external terminal monitoring such as business trips and remote work

- ・ It is possible to deal with unknown threats that could not be detected by conventional countermeasures.
- ・Because it is a cloud-based service, it has excellent scalability and frees you from the hassle of operation management.