Specifications/Technical Information
Application for evaluation machine
Is it outdated to introduce SD-WAN alone? ~ Network optimization with SD-Branch x AIOps x Zero Trust Security ~
ImportantSilver Peak has been acquired and is now part of Aruba. Click here for details
SD-WAN is a technology that virtualizes wide area networks and controls them with software. Currently, rather than being deployed as a standalone solution, it is becoming mainstream to combine it with cloud security, zero trust security, AIOps (Artificial Intelligence for IT Operations), etc. to further optimize networks. Macnica networks uses HPE products to provide such solutions to its customers.
Acceleration of zero trust/identity movement
After its emergence in 2016, SD-WAN experienced a brief period of stagnation, but in 2018 it regained prominence with technologies such as hybrid WAN and internet breakouts. From 2020, there will be a trend of introduction for applications such as changing the L3 router between bases to SD-WAN to optimize communication, and breaking out specific SaaS communication to the Internet to enable direct access from bases. strengthened.
At the same time, Mr. Matsumoto pointed out that in 2020, due to the impact of the corona crisis, the mainstream is shifting from SD-WAN to zero trust networks. In the past, communication control was mainly used only for bases, but with the increase in remote work due to the corona crisis, it has become necessary to have the same control outside the company.
“The point is to decide on the network topology and security after considering both the base and the outside. such as moving
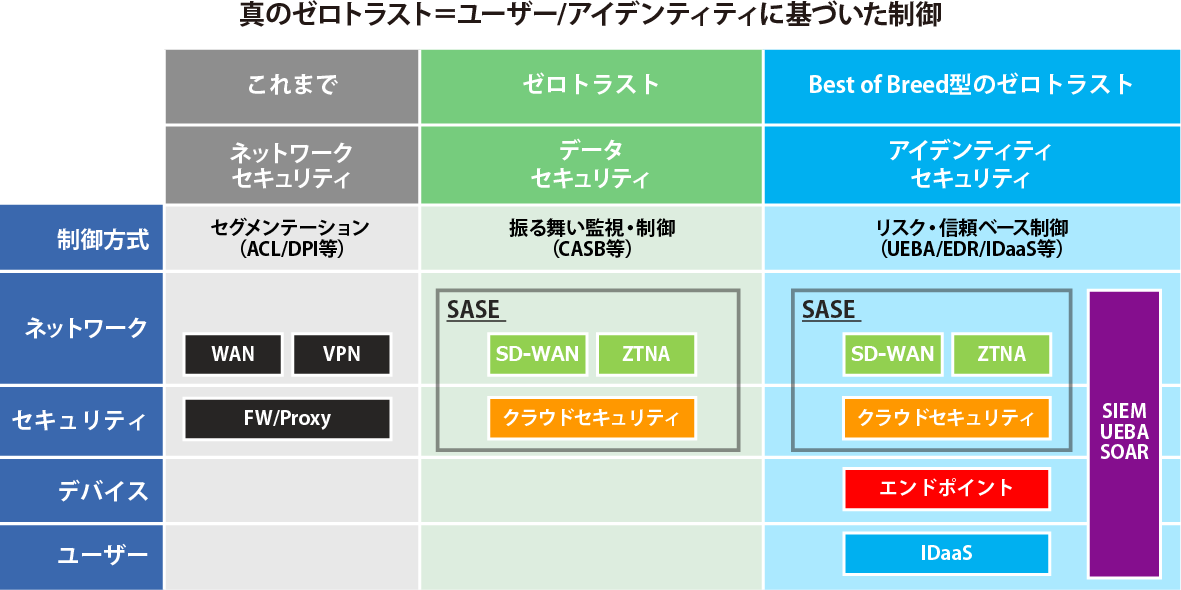
Until now, the direction of security has been a perimeter defense type in which the inside of the perimeter, such as inside the company, is defined as trust, and the outside as untrust. From now on, we will be in an age where we can access our information assets not only within the company, but also from any location, device, or network.
“Regardless of whether it is inside or outside the company, zero trust security, defined as untrust, is required for everything. There is an accelerating trend towards identity-based networks that place identity at the boundary as a common control point for accessing information assets. ”
SD-WAN is an integral part of SASE
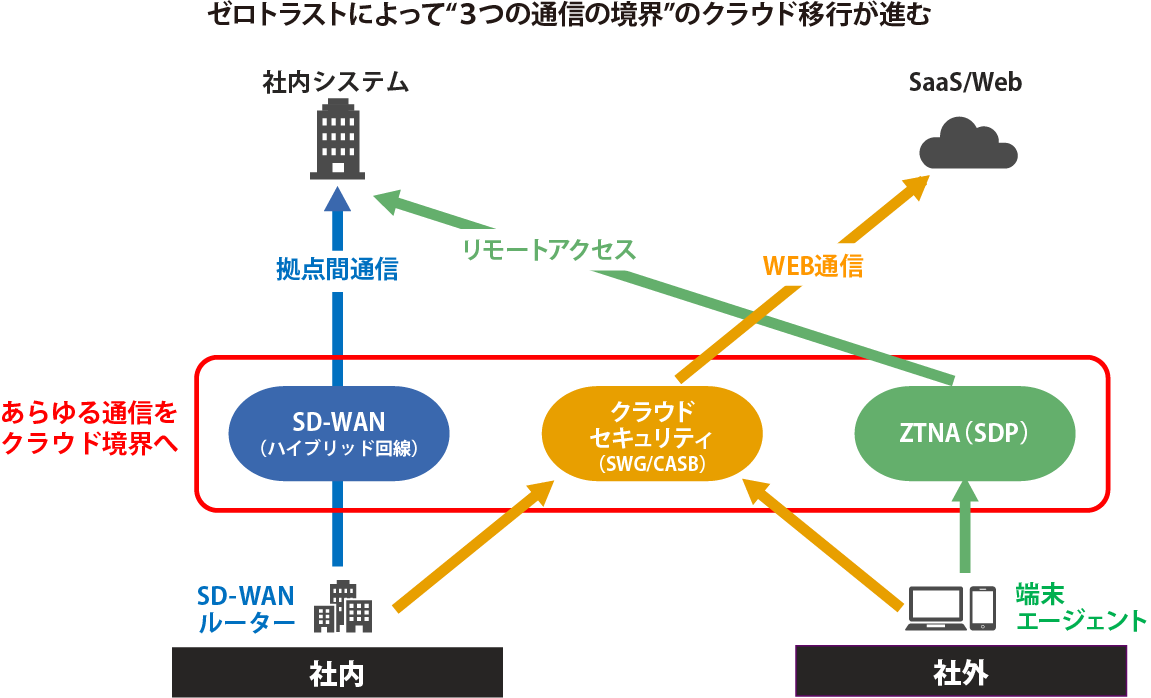
Next, Mr. Matsumoto said, "The big change brought about by Zero Trust is the migration of the 'three communication boundaries' to the cloud." The first is the shift from conventional routers to SD-WAN for intra-company communication from bases to data centers and IaaS.
Secondly, ZTNA (Zero Trust Network Access) will replace the traditional SSL-VPN remote access for communication from external PCs and smartphones to internal data centers. The third is the migration of all on-premises security equipment that was traditionally in data centers to the cloud. Cloud security such as CASB (Cloud Access Security Broker) that visualizes cloud applications and realizes data protection and governance, SWG (Secure Web Gateway) and DLP (Data Loss Prevention) is responsible.
“SD-WAN, ZTNA, and cloud security are collectively called 'SASE' (Secure Access Service Edge), which is the concept/framework for next-generation networks and security. It's the heart of change."
SASE brings network and security together in the cloud. The access source is not distinguished between inside and outside the company, and the same route is used to access internal information assets such as data centers and SaaS, and external sources such as the Web. To enable centralized management of different communications.
Beyond this Zero Trust is Best of Breed Zero Trust. In addition to SASE, advanced log analysis by SIEM (Security Information and Event Management) and UEBA (User and Entity Behavior Analytics) and operation automation by SOAR (Security Orchestration, Automation and Response) are also used. Devices are secured with endpoint security, and users are secured with IDaaS (Identity as a Service).
“In the medium to long term, we will evolve from the current Zero Trust, which is behavior-based monitoring and control based on data, to true Zero Trust, which is controlled based on risk and trust based on user/identity.”
Based on Zero Trust, Mr. Matsumoto once again emphasized the role and positioning of SD-WAN, saying, "It is an existence that adds new value as an indispensable component for SASE." He said SD-WAN deployment will be implemented at the same time as or after the security migration to the cloud.
Achieve SD-Branch, AIOps and Zero Trust at the same time
Mr. Matsumoto listed seven major trends for future SD-WAN, including SASE integration, and covered SD-Branch and AIOps in his lecture. The former is a network that integrates SD-WAN and SD-LAN, and the latter is network operation automation using AI/ML.
Macnica networks has a track record of focusing on SD-WAN since its inception, and provides customers with solutions that include products and services from HPE (including Silver Peak, which became an affiliate in 2020). There is. HPE offers the Edge Service Platform by combining three solutions: (1) Unified Infrastructure, (2) AIOps, and (3) Zero Trust Security.
SD-Branch is realized by (1) Unified Infrastructure. “The factors that differentiate us from other companies are the speedup of file servers and VDI communications, and the ability to work closely with a wide range of cloud security vendors.”
(2) AIOps leverages the strengths of HPE, which has been developing globally for many years. “HPE network equipment is used by various customers around the world. Information such as logs is aggregated in HPE’s center (Aruba Central) and used as training data for machine learning. By making use of the results, we will be able to detect early signs immediately after installation.”
Furthermore, in combination with SD-Branch, AI automatically detects abnormalities such as SD-WAN tunnel down and Wi-Fi performance deterioration comprehensively from WAN to LAN. It also automatically collects logs and generates trouble tickets, contributing to more advanced operational automation.
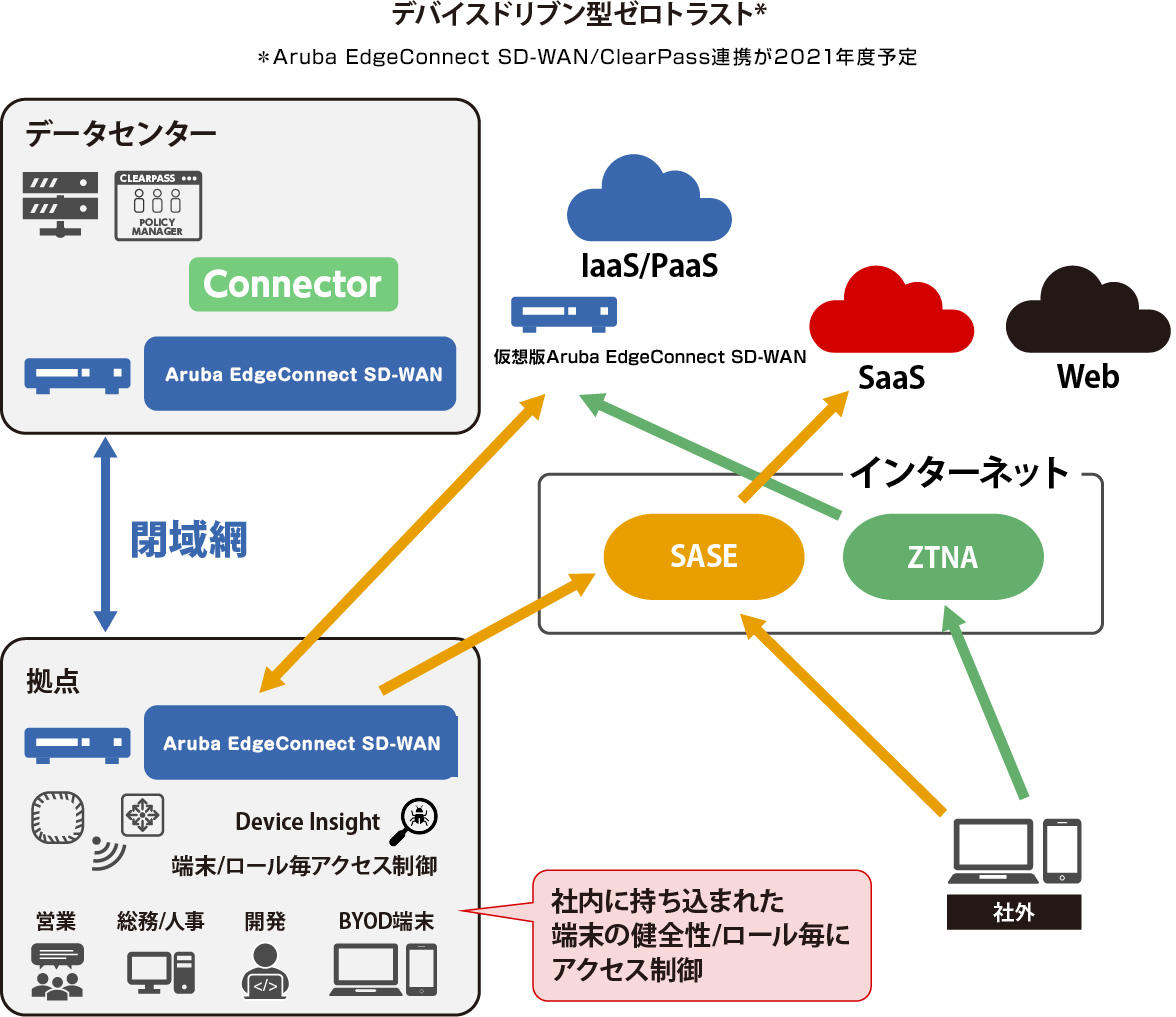
Also, with the spread of BYOD and IoT, devices are diversifying, and the number of devices that cannot contain agents will increase in the future, making it difficult to keep everything safe. HPE's (3) zero trust security solves this problem with RBAC (Role-Based Access Control). For example, when a user connects a device, the management server identifies the device based on the user ID, device vendor, date and time of connection, AP, authentication method, etc., and applies a policy (role).
“We control access in SD-WAN based on roles. This allows us to control access based on user/identity per device instead of traditional per VLAN or IP.”
Future-proof Zero Trust adoption steps
Mr. Matsumoto continued with an example of SD-WAN and Zero Trust in three steps. The first step is SD-WAN conversion only, and breakout and IaaS/PaaS simple direct connection are performed. Conventionally, IaaS/PaaS and cloud services were accessed from bases via data centers, but the base routers were replaced with Aruba EdgeConnect SD-WAN SD-WAN routers to break out only specific cloud services.
“In addition, in order to connect directly to IaaS/PaaS from the base, a virtual version of the SD-WAN router is installed on the IaaS/PaaS side. It will be possible to access directly by the shortest route.”
Proceed with zero trust from the second step. First, install an SD-WAN router on the data center side to optimize communication between sites. "Next, we will migrate the on-premises security equipment in the data center to the cloud. We will create a network configuration that allows access to information assets with the same security policy, both from the base and from outside the company," says Mr. Matsumoto. It is also possible to implement the security cloud first and then introduce the SD-WAN router.
The final step is to take a longer-term view and move towards either Best of Breed Zero Trust or Device Driven Zero Trust. Depending on the situation, the Best of Breed type may cause all communication to become tight due to SASE POP return or SPOF (single point of failure). Moreover, when the number of terminals is large, it becomes difficult to introduce an agent.
“In such a case, we recommend the device-driven type. Together with SASE, we combine a NAC (Network Access Control) type solution on the LAN side and control access to all terminals within the base for each role to ensure soundness. I will guarantee
Finally, Mr. Matsumoto said, `` Macnica networks is the only vendor that can fully provide and support SD-Branch (SD-LAN + SD-WAN) and SASE and has a rich track record. If you have any questions, please feel free to contact us,'' he concluded the lecture.
Inquiry/Document request
Macnica Aruba EdgeConnect SD-WAN
- TEL:045-476-2010
- E-mail:silverpeak-sales@macnica.co.jp
Weekdays: 9:00-17:00
