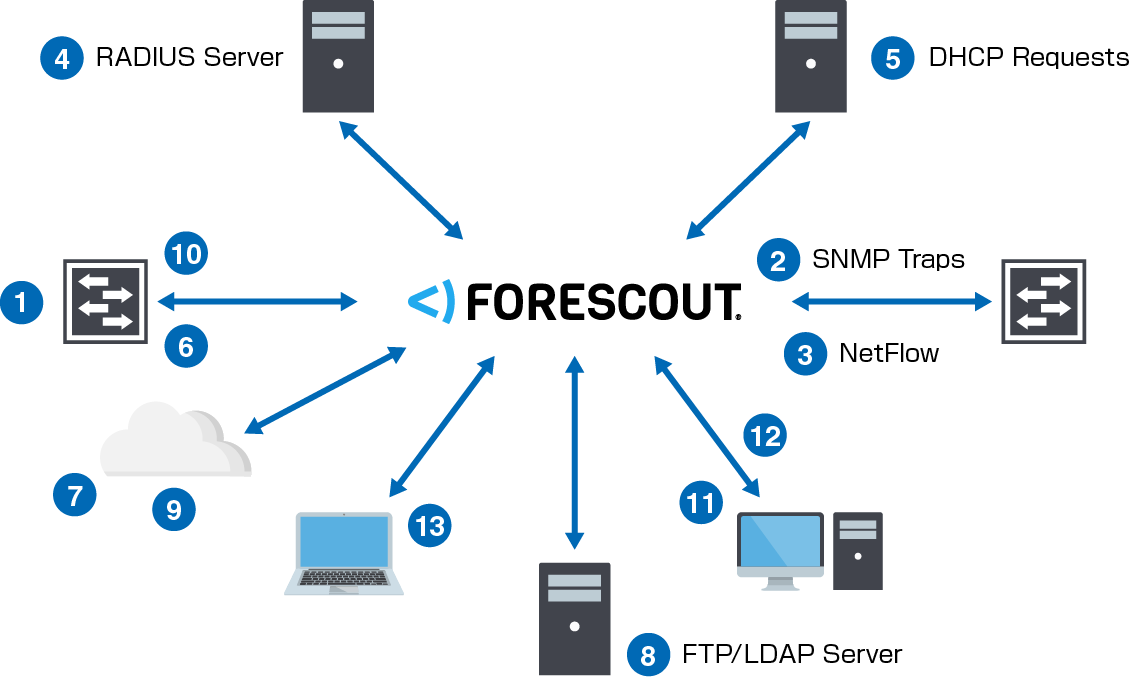
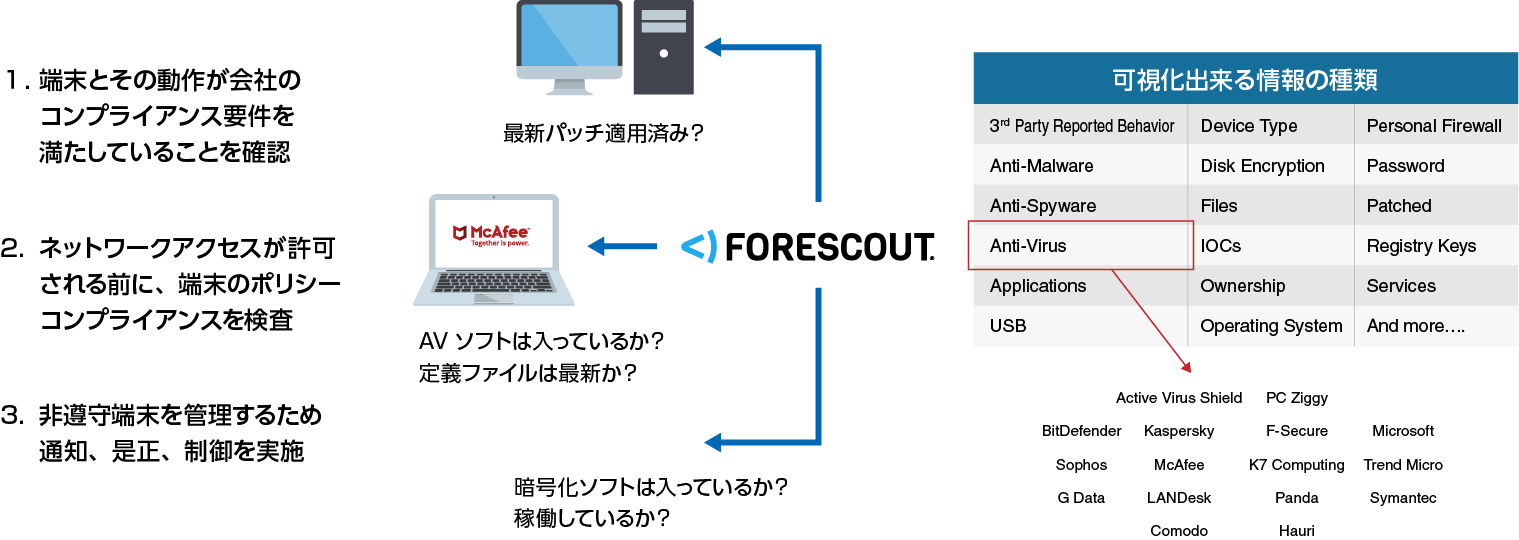
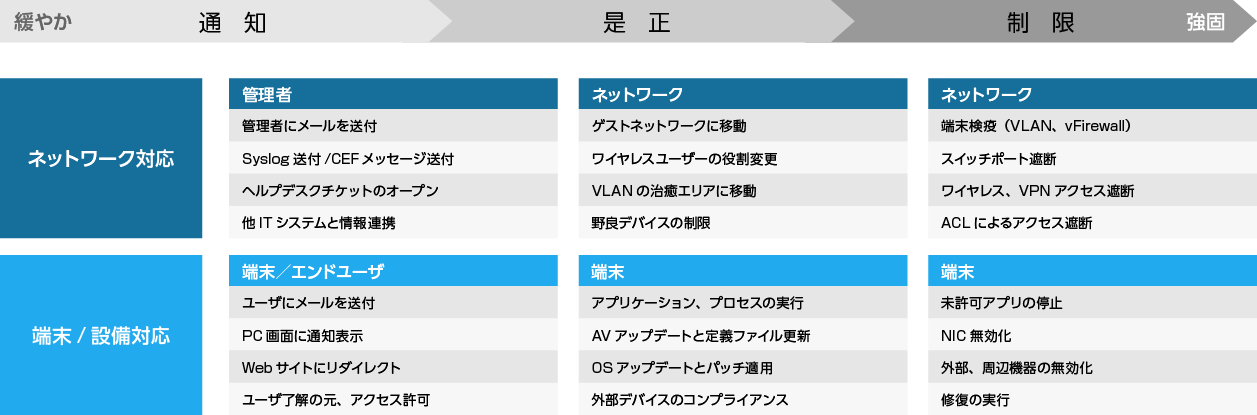
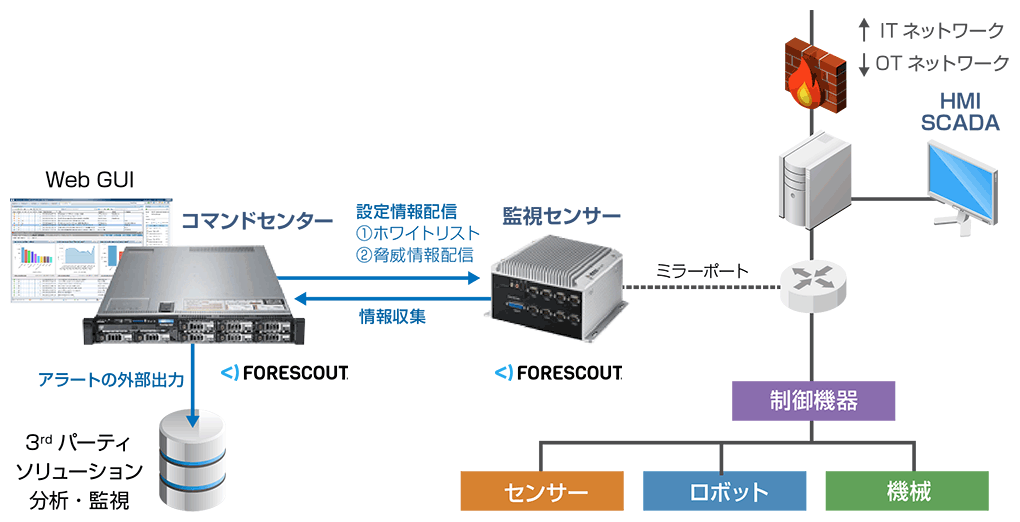
| Targeted attack countermeasures |
check points |
Forescout eyeExtend for Checkpoint Threat Prevention |
Forescout discovers terminals infected with threats detected by Checkpoint. Isolate terminals, including unmanaged terminals, until countermeasures are taken. |
| FireEye |
Forescout eyeExtend for FireEye NX |
Forescout receives zero-day threats and outbound calls detected by FireEye and quarantines the affected devices. Other devices will be quarantined until they have the same threat or countermeasures are taken. |
| Palo Alto |
Forescout eyeExtend for Palo Alto Networks Wildfire |
Forescout discovers terminals infected with threats detected by Wildfire. Isolate terminals, including unmanaged terminals, until countermeasures are taken. |
| privilege management |
CyberArk |
Forescout eyeExtend for CyberArk |
Unmanaged privileged accounts are not used by users, or if there are old or isolated accounts with high risk, they are disabled or managed. |
| Terminal management |
HCL (IBM) |
Forescout eyeExtend for IBM Big Fix |
Check whether the Big Fix agent is running or not, and if it violates the policy, correct it or quarantine it. In addition, if Big Fix managed device security conflicts with policy, cooperate with Forescout and isolate the relevant device |
| SIEMs |
IBM |
Forescout eyeExtend for IBM Qradar |
Security devices such as Firewall send alerts to SIEM, add device information visualized by Forescout to determine the degree of risk, and implement actions such as isolation according to the policy. |
| Micro Focus |
Forescout eyeExtend for Micro Focus ArcSight ESM |
| Splunk |
Forescout eye extender for Splunk |
| Device management |
Airwatch |
Forescout eye extender for Airwatch |
Forescout checks if the device is registered on the MDM server, corrects devices that are not registered, and prompts self-registration. Also, in the case of mobile devices, when a terminal that violates the policy is detected, the data is automatically erased. |
| IBM |
Forescout eyeExtend for IBM MaaS360 |
| Mobile Iron |
Forescout eyeExtend for MobileIron |
| Microsoft |
Forescout eye extender for Microsoft Intune |
| Vulnerability research |
Qualys |
Forescout eyeExtend for Qualys Vulnerability Management |
Share vulnerability scan results with Forescout and implement isolation etc. according to the results. In addition, if there is a device that has not been patched in the device information visualized by Forescout, the vulnerability can be quickly dealt with by sharing the data. |
| Rapid7 |
Forescout eyeExtend for Rapid7 Nexpose |
| Tenable |
Forescout eye Extend for Tenable |
Endpoint security
EDR |
carbon black |
Forescout eye Extend for Carbon Black |
Forescout checks for the existence of agents and whether they have stopped functioning, and implements isolation etc. if policy conflicts occur. Also, based on IoC data, all devices, including unmanaged devices, are scanned and dealt with. |
| CrowdStrike |
Forescout eyeExtend for CrowdStrike |
Forescout checks for the existence of agents and whether they have stopped functioning, and implements isolation etc. if policy conflicts occur. Also, based on IoC data, all devices, including unmanaged devices, are scanned and dealt with. |
| FireEye |
Forescout eyeExtend for FireEye EX (email security) |
Forescout discovers terminals infected with threats attached to emails detected by FireEye. Isolate terminals, including unmanaged terminals, until countermeasures are taken. Also, if the agent is not installed, it is possible to prompt the installation. |
| FireEye |
Forescout eyeExtend for FireEye HX |
Forescout discovers terminals infected with threats detected by FireEye. Isolate terminals, including unmanaged terminals, until countermeasures are taken. Also, if the agent is not installed, it is possible to prompt the installation. |
| McAfee |
Forescout eyeExtend for McAfee ePO |
Forescout checks whether there is an agent or whether McAfee has stopped functioning, etc., and implements isolation etc. if it conflicts with the policy. |
| Symantec |
Forescout eyeExtend for Symantec Endpoint Protection |
Forescout checks whether there is an agent and whether the SEP has stopped functioning, and if it violates the policy, it will be quarantined. Also, based on IoC data, all devices, including unmanaged devices, are scanned and dealt with. |
| Configuration management |
Service Now |
Forescout eye Extend for ServiceNow |
Forescout detects the device and provides the acquired device information to ServiceNow. Realized to maintain real-time CMDB information. |
| Next generation firewall |
check points |
Forescout eye extender for Check Point NGFW |
Forescout links information such as tag information and device status linked to devices with Firewall, and applies appropriate security policies based on device attributes and context information to automate isolation. |
| Palo Alto |
Forescout eyeExtend for Palo Alto Networks NGFW |
| Fortinet |
Forescout eyeExtend for Fortinet FortiGate NGFW |