Specifications/Technical Information
Application for evaluation machine
- FAQ
I tried the latest version of Prisma Cloud (as of January 2024), which has undergone a major update.

There was a major upgrade in the SaaS version of Prisma Cloud on January 17, 2024.
With this upgrade, Code to Cloud: Security of the application lifecycle from development (code) to operation (cloud) for cloud-based applications has been significantly enhanced not only in terms of conventional functionality but also in useful functions for operation. . With this update, by linking various alerts with various information, the priority to be responded to is also clear, and the previous issue of ``I installed CSPM, but there are too many alerts and I can't keep up with operations'' can be eliminated. Much improved. Prisma Cloud describes itself as a "next generation CSPM" due to these expanded functions.
1. Detection of misconfigurations in real time
Regarding configuration changes in Amazon AWS, in the past, configuration deficiencies were detected from the results of periodically executing APIs.
Now, by linking with Amazon EventBridge and importing audit logs, it is now possible to determine triggers for configuration changes.
Change settings from the settings confirmation screen. (Figure 1)
Enabling this feature has the following two benefits.
- Changes are detected in real time, so it is possible to detect in almost real time whether the changed content contains any configuration deficiencies.
- Since changes are triggered instead of regular scans, there is no need to execute APIs other than when changes are made, reducing the number of API executions.
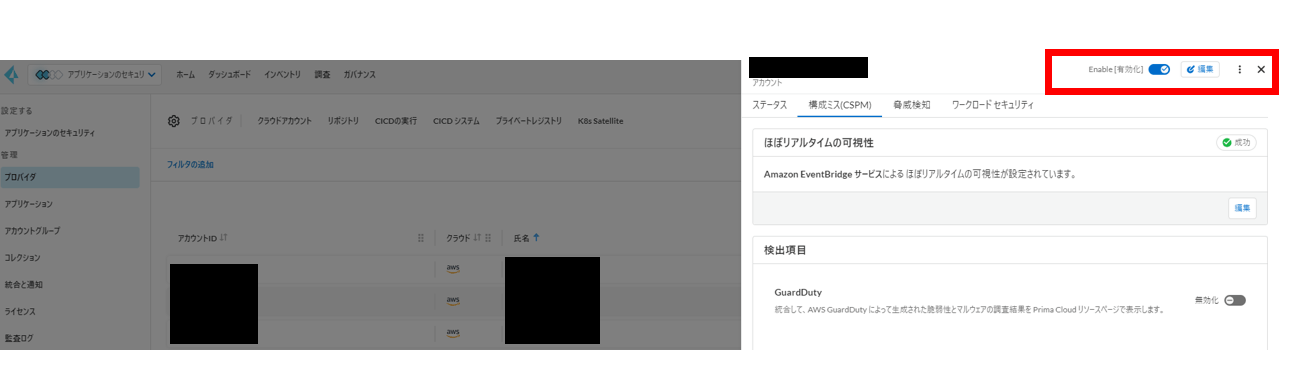
Figure 1. Enabling Amazon EventBridge
2. Visualization of related risks
As before, it displays configuration deficiencies for a specific resource, but by combining it with multiple functions such as flow logs and Runtime Security function (CWPP), related risks can be visualized.
"Risk" here refers to the presence or absence of elements that could cause an application to be attacked or compromised.
By combining multiple risks, it is now possible to see which resources are in a more alarming state, making it easier to determine which resources require more urgent attention and what kind of fixes should be taken.
For example, instance A (detected by the CSPM function) is open to the public without restrictions on connection sources, and instance B (detected by the CSPM function) is not disclosed to the outside but has no internal communication restrictions. Detection), there are events such as communication occurring from the outside to B via A (flow log), and furthermore, an image with a Log4j vulnerability is running on B (Runtime Security's vulnerability detection function) It is possible to see all the information in one place, such as whether an attack was actually carried out and malware was embedded (Runtime Security's malware detection function and forensics function). (Figure 2)
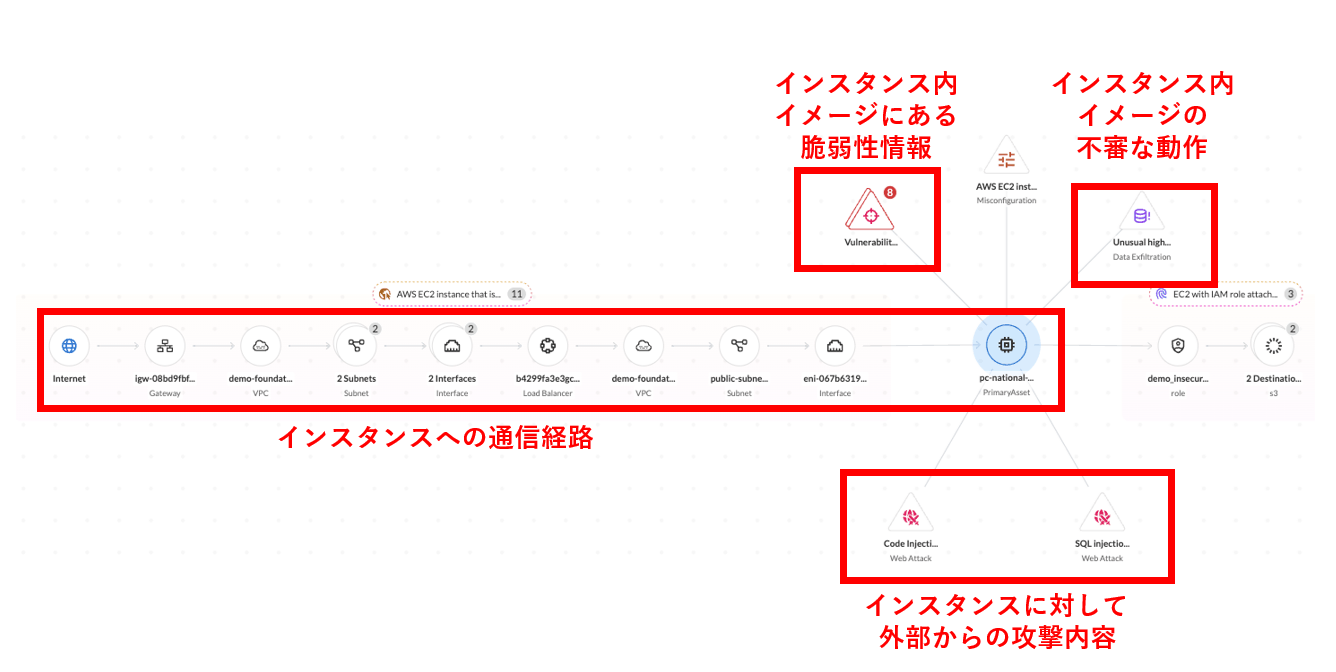
Figure 2. Visualization of associated risks
3. Machine learning-based threat detection
In addition to misconfigurations and container image behavior abnormalities, it can learn what is normal from flow logs and audit logs, and can detect attacks from behaviors that do not normally occur. (Figure 3)
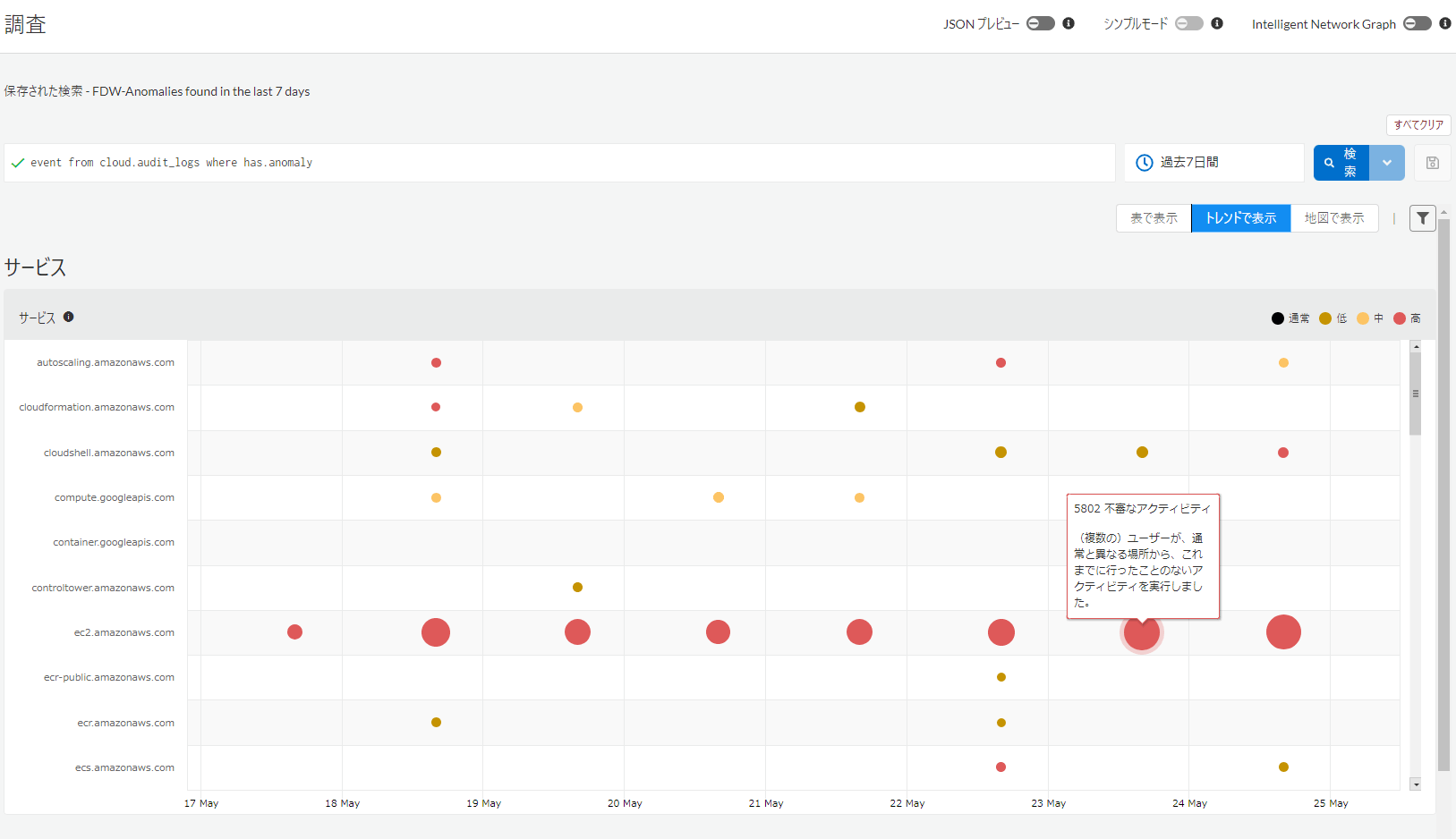
Figure 3. Suspicious behavior not found in machine learning
For example, in the above example, you can see that the network interface deletion API is executed continuously. In some cases, we cannot deny the possibility that this behavior is due to an external attack. These alerts can be used as triggers to identify the ID of the network interface that is actually targeted for deletion from Resource Config, allowing for more detailed behavior confirmation and investigation.
4. IaC security
Application Security's IaC security was able to detect template configuration deficiencies, but you can also check the template modification history. (Figure 4)
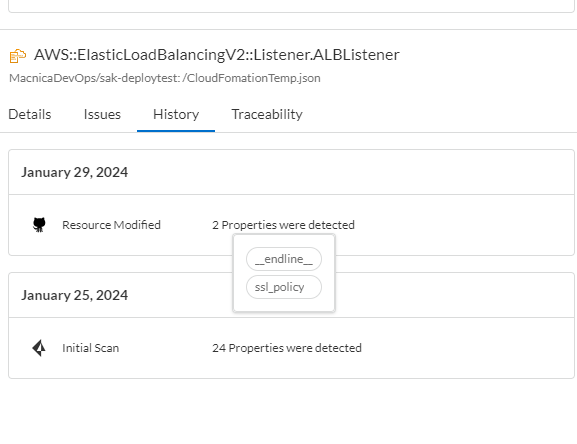
Figure 4. Summary of modifications
IaC is a code-based technology that automates tasks such as environment construction and rollback when a problem occurs. IaC is currently attracting a lot of attention as a solution to problems such as worker assignment, work man-hours, and human errors, and many organizations around the world are starting to use it.
On the other hand, in situations where all work is completed in a code base, the code itself defines all resources and settings, so traceability of what changes were made, by whom, and when is an extremely important element.
In addition, even if you automate with IaC, if you perform operations such as changing the cloud configuration from the GUI during operation, "drift" (a state where there is a discrepancy between the actual operating configuration and the IaC definition) occurs. If drift is left unaddressed, necessary settings may be missing in subsequent deployments, which could lead to a major incident. Prisma Cloud will also be able to provide the ability to detect these drifts.
5. summary
I tried some of the features of Prisma Cloud after the major update, but this article does not cover all of them.
We also have further improvements planned in the near future, so we hope to introduce them at the next opportunity.
As mentioned in this article, we provide comprehensive security for applications on the cloud from pre-development to operation, such as vulnerabilities in the application itself, inadequate settings for instances in which the application runs, and templates for generating instances. It has also been greatly improved.
In particular, the function introduced in ``Visualization of related risks'' is a function that directly deals with the problem of ``CSPM has been installed, but there are too many alerts, making it difficult to operate'', which was mentioned at the beginning, and it clarifies priorities. What's more, the information necessary for various judgments and decisions when considering response plans can now be accessed from a single screen, evolving into a "next generation CSPM" that provides great value to users. I did.
Please look forward to future updates.
Please also check out the related articles below.
We also provide related free on-demand videos, so please take a look.
Inquiry/Document request
In charge of Macnica DevOps
- TEL:045-476-1972
- E-mail:twistlock@macnica.co.jp
Weekdays: 9:00-17:00




