Prisma Cloudのアンチマルウェア機能が進化しました(WildFire連携が可能に)

コンテナセキュリティを検討する上での1つの要素として、悪意のあるイメージを利用してしまうことをいかに防ぐかという点があります。コンテナの性質上、Docker Hub等の公開レジストリに配置されているイメージを容易に利用できてしまうため、このような利用を制限する・またイメージにマルウェアが含まれていないかの監査を行うことは重要な考慮点になってきます。今回は、Prisma Cloudで提供するアンチマルウェア機能において2021年6月に注目すべきアップデートがありましたので、ご紹介します。
コンテナセキュリティにおけるアンチマルウェア機能の必要性
上述したように、Docker Hubのような公開レジストリ経由で利用するコンテナイメージにクリプトマイナーやマルウェアといった脅威が含まれてしまっている可能性があり、実際にPalo Alto Networks社のリサーチ機関であるUnit42では、2000万回以上ダウンロードされている悪意のあるクリプトジャッキングイメージが30個見つかったと発表しています。(記事:https://unit42.paloaltonetworks.jp/malicious-cryptojacking-images/)
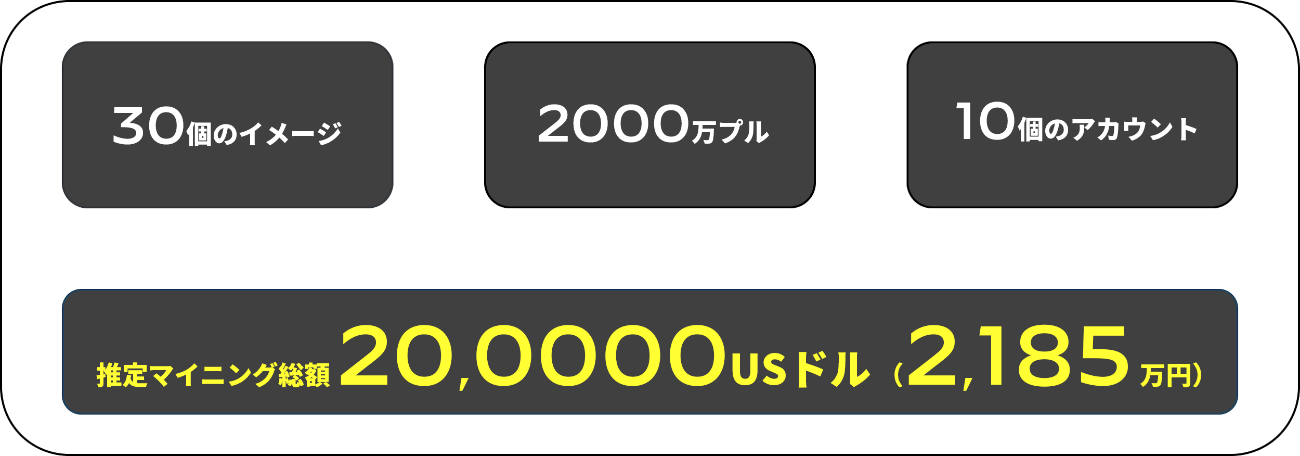
画像:https://unit42.paloaltonetworks.jp/malicious-cryptojacking-images/から引用
Prisma Cloudではこれまでも脅威インテリジェンスフィードを通じて、コンテナイメージ内のマルウェアをハッシュ値ベースで検出・保護することが可能でした。今回、これがWildFire連携を通じてより強化されています。
WildFire連携が可能になったことによるメリット
WildFireはPalo Alto Networks社が次世代ファイアウォール製品等と連携させる形で以前より提供している、ゼロデイエクスプロイトや高度な回避技術を駆使する未知のマルウェアを検出・防御することのできる技術です。
今回、Prisma Cloudのアンチマルウェア機能がWildFireとネイティブ連携されたことにより、未知のマルウェアを含むより高度な悪意のあるイメージの検出が可能になりました。更に、WildFireはPrisma Cloudだけでなく、世界中の次世代ファイアウォール(NGFW)やCortex XDRといった他のPalo Alto Networks社製品を通じて検出されたゼロデイのマルウェアが、Prisma Cloudにおいても検出可能となるといったメリットも生みます。
WildFireが動作する2つのポイント
WildFireによる分析は2つのポイントにおいて実行されます。ローカル/CIパイプラインでの実行とランタイムでの実行になります。
- ローカル/CIパイプラインでの実行
ローカル/ CIパイプラインでの実行においては、従来より提供されているtwistcliというコマンドラインツールを利用します。すでにPalo Alto Networks社にて特定されているファイルハッシュ値を保有するイメージについては、ローカルにてほぼリアルタイムでチェックされますが、これまで特定されていないファイルハッシュ値については、WildFireとの連携によりファイルがサンドボックス技術を含む高度なマルウェア分析にかけられ、未知のマルウェアかどうか特定されます。これにより、未知のマルウェアであったとしても、CIパイプラインの中で検出を行い、そのままデプロイが実行されてしまうことを防ぐことができます。 - ランタイムでの実行
実行中のコンテナにおいてもランタイム保護機能を通じて、WildFireによる未知マルウェアの検出が実行されます。実行中のコンテナに対して、ファイルシステムにマルウェアがダウンロードされた場合、そのマルウェアの実行をブロックし、自動的にフォレンジックデータのキャプチャが取得されます。同様に、仮にマルウェアを含むコンテナが実行されてしまったとしても、脅威を自動的に検知し、調査を開始することができます。
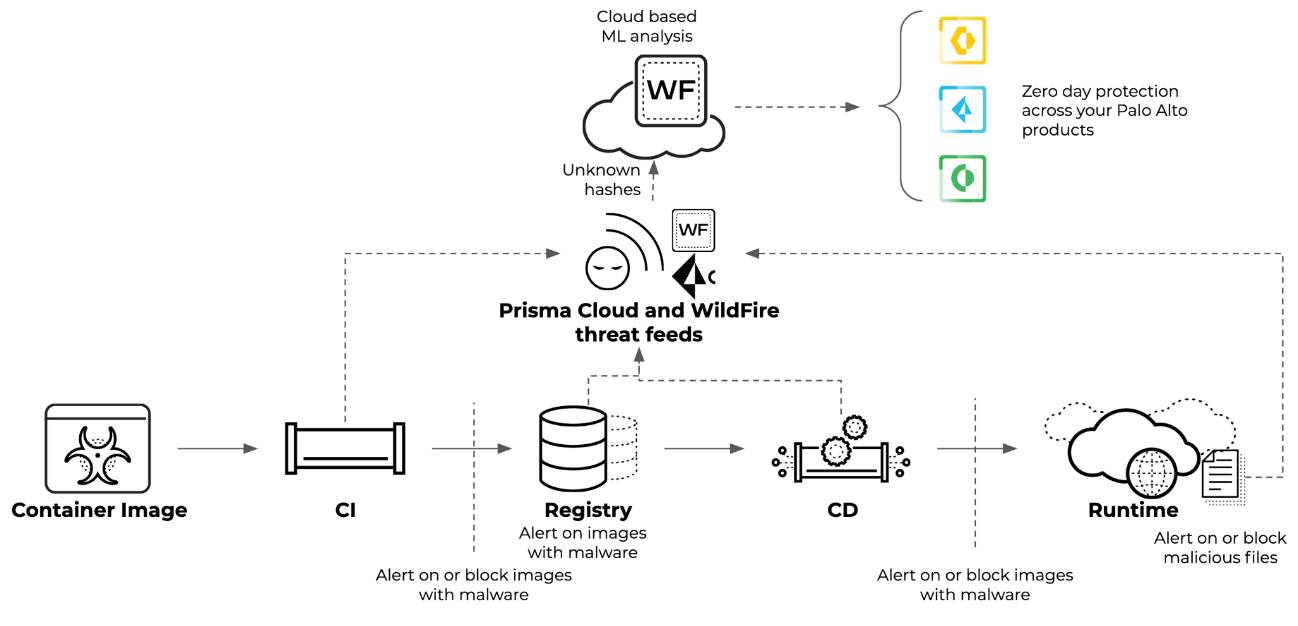
画像:https://www.paloaltonetworks.com/blog/prisma-cloud/prisma-cloud-and-wildfire-integration/ から引用
まとめ
今回のWildFire連携によって、アンチマルウェア機能として既知だけでなく未知のマルウェアも精度高く検出できるようになったことになります。これは、実績のある総合セキュリティベンダーであるPalo Alto Networks社が提供するPrisma Cloudの1つの強み・先進性だと思います。コンテナセキュリティをご検討中で、コンテナイメージ・実行中コンテナへのマルウェア検知にも関心がある方はぜひお気軽にお問合せください。
お問い合わせ・資料請求
株式会社マクニカ DevOps 担当
- TEL:045-476-1972
- E-mail:twistlock@macnica.co.jp
平日 9:00~17:00


