
Introduction
-Usage status of cloud services and issues faced by Box users-
Amidst the global shift to the cloud, cloud services that can be used anywhere and on any device are becoming more and more popular in Japan. According to the "Results of the Communication Usage Trend Survey" published annually by the Ministry of Internal Affairs and Communications, 70 % of companies use cloud services, and 80 % of companies plan to use cloud services in the future. In addition, file storage and data sharing are the top uses of cloud services, indicating the high demand for cloud storage represented by Box.
On the other hand, security incidents have also occurred, such as important information being taken out of storage or information leaks due to cloud service configuration errors. The Ministry of Internal Affairs and Communications has also issued a warning in the 5th edition of the Telework Security Guidelines, and the following is an excerpt of the content (coordination (in bold) is implemented by Macnica)
- “Because the boundaries of responsibility (demarcation of responsibility) between cloud service providers and users are not the same among services, it is important to confirm the scope of responsibility that your organization should bear for each service that you use.”
- “It is important to define the confidentiality level of information handled in business, determine the confidentiality level that can be handled on cloud services, and appropriately manage information on the cloud.”
- “There have been cases of inadequate access control settings in cloud services that mainly provide file sharing services, and confidential information has been accidentally disclosed on the Internet. In addition, it is recommended to strengthen access control by IP address restrictions, etc., if possible.”
Source: Ministry of Internal Affairs and Communications 2021 Communications Usage Trend Survey Results
(https://www.soumu.go.jp/johotsusintokei/statistics/data/220527_1.pdf)
Source: Ministry of Internal Affairs and Communications Telework Security Guidelines 5th Edition
(https://www.soumu.go.jp/main_content/000752925.pdf)
Under these circumstances, Box Users can be roughly divided into 3 I think you have one problem.
- “Intentional Fraud” or “Misuse” by Insiders
- Account takeover by an outsider
- Management of ever-increasing amounts of important and confidential data
Solutions for Box Content Protection
I think there are two general options for solving the challenges presented in the previous chapter.
The first is the "reporting function" available to all Box users. This function is a function to specify items on the GUI of Box and output them in CSV format. Since it is possible to specify items such as "user activity" and "external collaboration", I think that there are many users who regularly use the report function to check whether it is being operated according to the rules. In addition, a scheduling function has recently been added, making it possible to run automatically. On the other hand, if there are many users and many specified items, there may be many operational issues such as it takes time to output and man-hours to edit data after output.
The second is "Box Shield", which is a Box optional feature. Box Shield has two main functions: access control and threat detection. Access control for shared links can be controlled by creating rules on the user side. Furthermore, it is possible to automatically classify highly confidential content and control downloads for that content. Threat detection can detect and alert you to things like abnormal downloads. Box Shield is a very useful function, but there are issues that it can be expensive if you use all the functions, and regular maintenance of rules is required to prevent false positives.
In this blog, we would like to introduce our unique solution “MUCV for Box” as the third option.
Protection solutions provided by Macnica ~MUCV for Box~
This solution is a Box user activity visualization solution. As shown in the figure below, it can be introduced by setting the log output from the Box application to our platform.
[Introduction configuration]
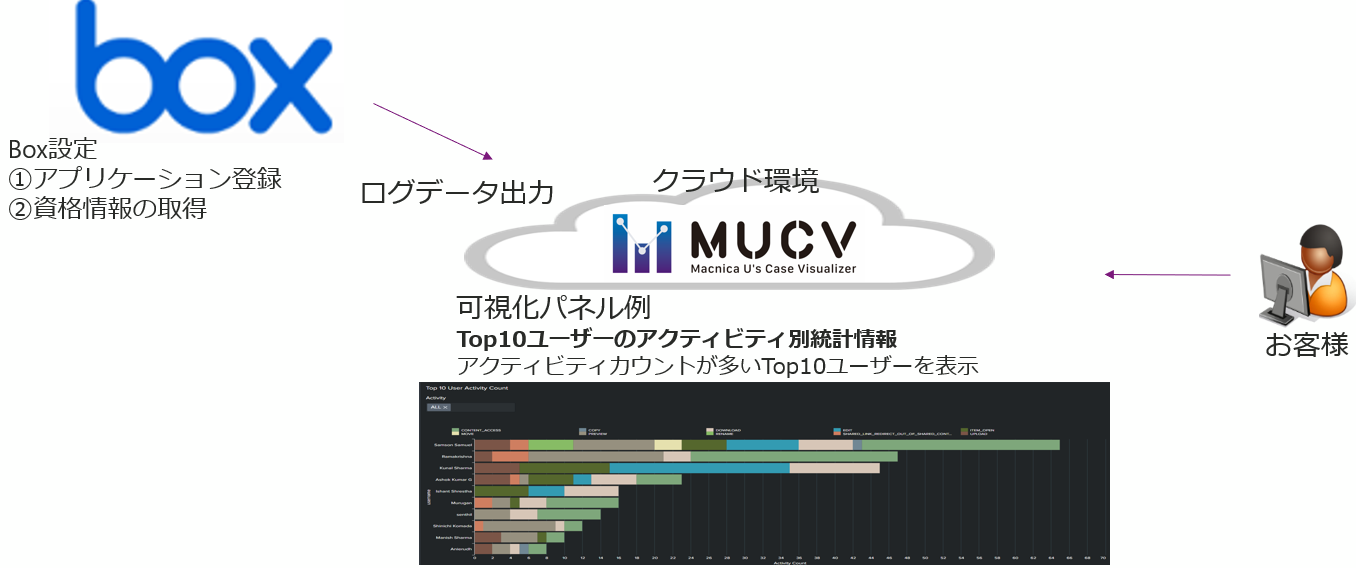
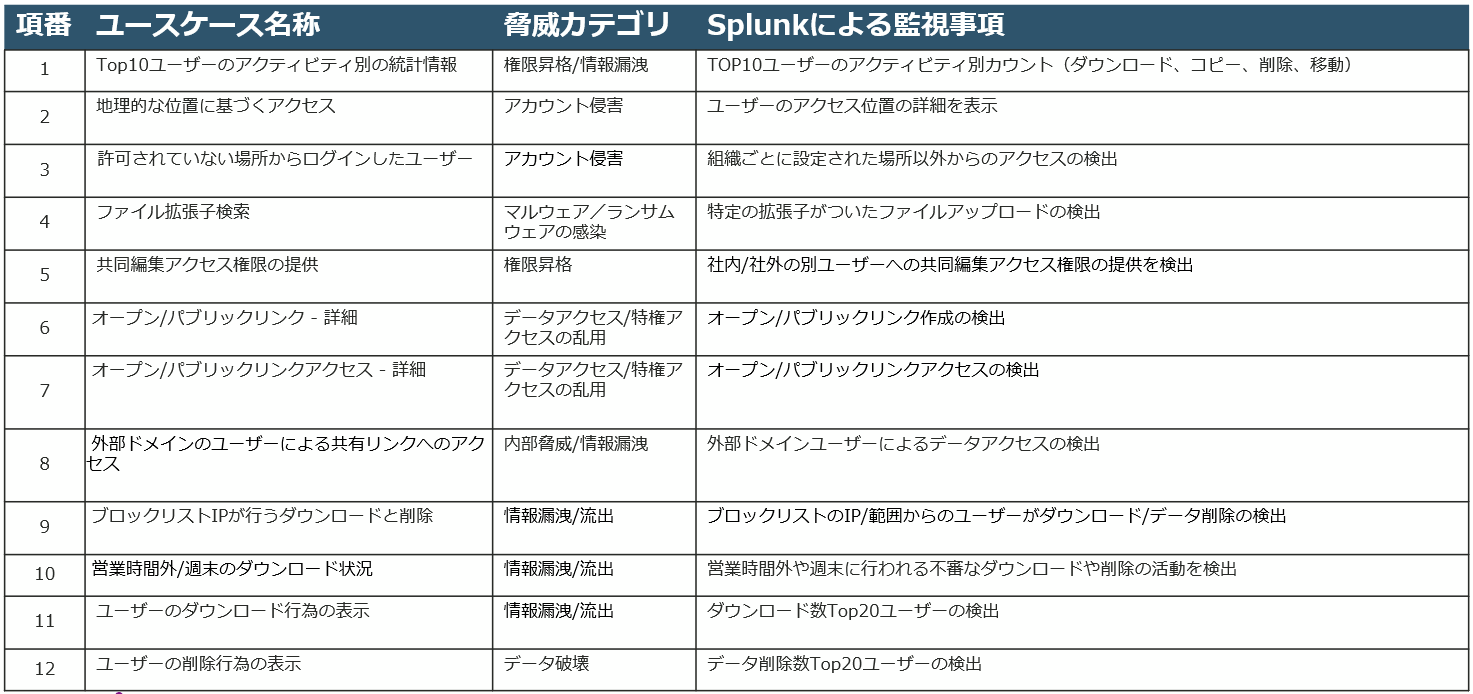
View user activity and monitor external collaboration from multiple perspectives on your dashboard. This solution is based on a dashboard developed individually according to the original customer's request, and has 12 large visualization panels as shown in the table below.
[List of visualization items]
In addition to visibility, administrators can also be notified when risky activity occurs.
By using this solution, you can check at a glance whether operations are being conducted based on internal rules, and when risky activities are performed, you can check the details on the dashboard to realize secure operations.
If you are interested, please see the details from the link below.