
Speedy business creation using digital technology has become a major theme in various industries, and transforming human resources and organizations to adapt to this has become a management issue. However, is the company-wide security approach sufficiently optimized? Isn't a rigid security policy a hidden impediment? The key to achieving this is to create a "lean", future-oriented security culture that actively identifies risks such as vulnerabilities, led by business departments that utilize digital technology, while minimizing wasteful responses.
We will share the reality gap that many organizations will face if they aim for this, and Macnica 's ideas for overcoming it, based on actual examples from both technology and organizational aspects.
Business development speed accelerated by technology and "waste" of security measures
Lean Startup, a universal method of business development, gives shape to ideas as quickly as possible and provides them to customers as MVP (Minimum Viable Product). We measure the results, learn the data, and brush up by reflecting new ideas. In business development, it is important to fill in the uncertainty that accompanies new businesses by turning this cycle quickly.
Advances in technology have made it easier to make this cycle faster. For example, PaaS allows users to focus on their applications and develop services without worrying too much about infrastructure. Also, with technologies like GitHub Copilot, where AI automatically generates code from natural language, ultra-high-speed development may become the norm in the future.
What will happen to security in those times? The code generated by GitHub Copilot mentioned above still contains security flaws, and GitHub recommends the use of CodeQL, which automatically detects code flaws. In other words, in the future, it is expected that code will be automatically generated by AI, and at the same time, security risks will be automatically detected and correction methods will be presented.
On the other hand, back to reality, development must comply with a plethora of security guidelines and approvals. If hundreds to thousands of vulnerabilities are detected in the vulnerability inspection, or if many vulnerabilities are classified as "high" risk, determine countermeasures for each vulnerability and report to the security department. is needed. If a problem is pointed out just before the release, a big rework will occur on the development team side. In this way, issues other than technology are common to many companies. Isn't there a lot of "waste" that hinders lean and efficient security?
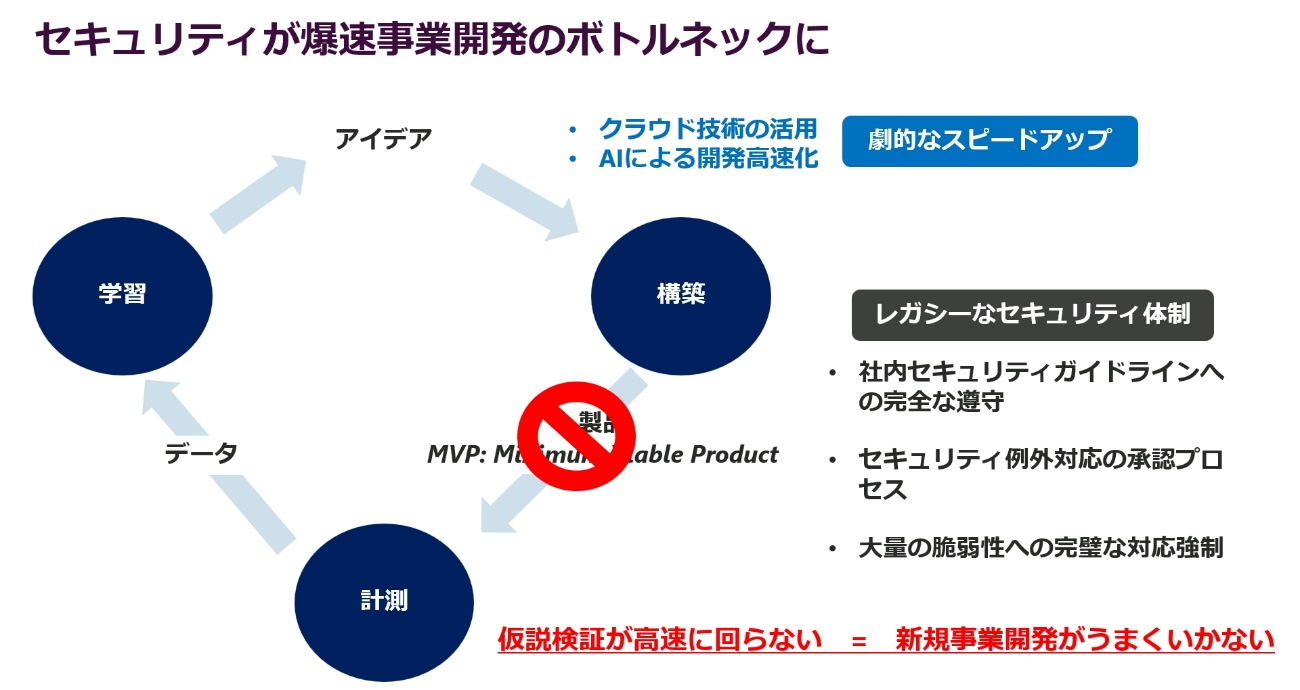
The evolution of technologies that give form to ideas in business development, such as the cloud and AI, will continue to increase the speed of business development exponentially. Maintaining a legacy security system will become a bottleneck in business development. , there is concern that the business development cycle will not run smoothly.
Causes of "waste" explored from technology and organizational culture
Why does this kind of "waste" occur in security measures? Looking at the organizational structure of a company, conventional security teams have worked to ensure integrated governance and standardized risk management from the perspective of "corporate security" as seen by the entire organization.
On the other hand, the new business development team must win customers and markets and beat the competition amid various uncertainties, so speed and change are extremely important factors. Especially for new digital services, security risks are an important issue. Recently, there have been incidents in which services immediately after release have been forced to terminate due to security incidents, making it essential for development teams to face security risks.
Such a gap between development and security can be attributed to "relationship between business and security," "correct recognition of security risks," and "organizational structure and responsibility model." We actually see the following scenarios at our customers' sites.
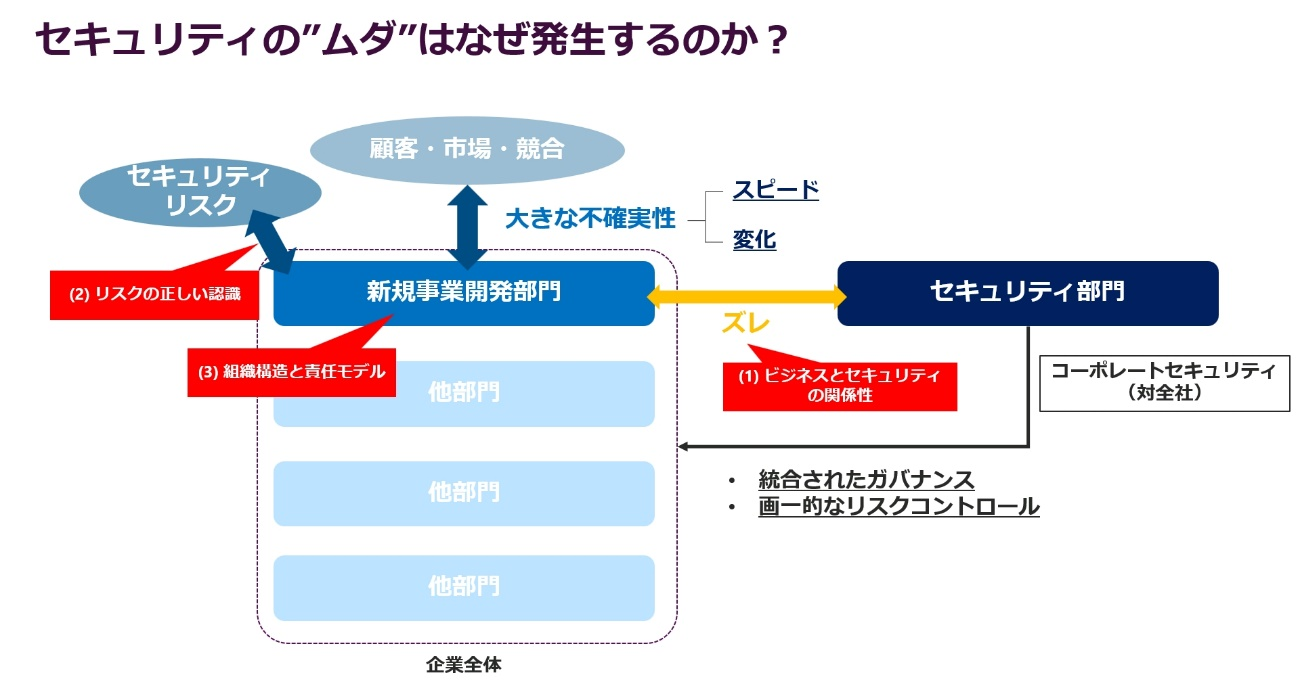
In the case of Company A in the "relationship between business and security", if the priority of the vulnerability discovered in the security inspection is "medium" or higher, it will be dealt with without fail. The reason was explained at a meeting that included the team, and the process was always to obtain the approval of the general manager.
Also, in the case of Company Z, all open sources used for development were to be recorded in a prescribed Excel file, and it was a rule not to use open sources that did not comply with the guidelines. If this is done thoroughly, the development team will have a huge amount of confirmation work. In such cases, the idea is that the security team controls and controls the development team, and the current situation is that an excessive burden is being placed on the development team.
In the case of Company S in "Correct Recognition of Security Risks," it was determined that vulnerabilities classified as "Critical" with a CVSS score of "9.8" should be fixed. At one point, 50 vulnerabilities classified as "Critical" were found in the entire system, and it was decided to create explanatory materials on these scrutiny and countermeasures in one week. There is also the opposite case. Company B postponed responding to vulnerabilities classified as "Middle" with a CVSS score of "6.5" because they judged the risk level to be low.
At first glance, the cases of Company S and Company B appear to be appropriate measures, but by applying public scores such as CVSS as they are, problems such as overestimating risks or overlooking risks arise. There may be It is important to have the knowledge and tools to make accurate risk judgments here.
In the case of Company A in "Organizational Structure and Responsibility Model", the role of the development team is to contribute to business development, security is the responsibility of the security team, and the development team is not involved in the responsibilities and rules of the security department. and the reporting lines were different. On the other hand, in the case of Company H, the environment was such that the security team could not get involved with the development team. This was because they did not have authority, and there was concern that they would be held accountable if development efficiency declined.
Currently, DevSecOps-related tools that incorporate security from the development stage and ensure safety are widespread, but even if they are good tools, if the organizational structure and responsibilities do not change, efficiency will change greatly. there is no. Most companies will operate with development responsibility on the development team and security responsibility on the security team. The situation where the organization is divided in the development process leads to division, and as mentioned earlier, if a problem is found in the security audit conducted immediately before the release, the process will be pulled back to the development side.
Realization of "lean" security led by development
In the first place, what does it mean to be in a state where there is no "waste" in security (= lean)? Simply put, lean security is a balance between business risk and security response burden. For example, if the security measures are excessive even though the business risk is small, the balance is not balanced and waste is generated.
Therefore, from the current situation where the development team and the security team are operated separately and implement security, it is desirable to assign a person (security champion) who can fulfill the responsibility of development and security in the development team and demonstrate security leadership. can be said.

Even in the world, it is a challenge to incorporate security into business development without making it a bottleneck. The concept of Security Champion has now become a global standard, and many guidelines and documents have been developed, and the practice of the program is recommended.
According to Veracode, a static application analysis service, a security champion is defined as "a developer who cares about security." The "I care about security" part is important, you don't have to be a security expert by any means. Become a person who can take an interest in potential problems in development and solve them, or who can ask the CISO for guidance.
Mercari, Inc., which introduces a company-wide program for Security Champions, has published an initiative (https://mercan.mercari.com/articles/19140). Here, content and educational opportunities are prepared to acquire security knowledge and skill sets, and human resources equivalent to security champions in the development team use these, ultimately being able to solve security problems on their own and speeding up development. We aim to be able to make decisions according to business risks.
In addition, at an online service company, at least one member of the development team has an interest in security and conducts their own research to determine security risks. We have created a channel in Slack for core members of the security team and development team to share various information. A de facto security champion is acting as a bridge.

The cases of the two companies are partly possible because they are IT companies, but the US Department of Defense (DoD) is a huge organization practicing DevSecOps. The reference design released by the DoD requires that the senior leaders of the organization agree with the philosophy, transform the organizational culture into one that promotes development, operation, and security, share responsibility, and agree with all stakeholders. It shows that it is necessary to acquire new knowledge and to gradually change while working on a small start.
The rollout of the Security Champions program begins with a commitment to security leadership within the development team and agreement with senior levels. Then, assign talent, work with the security team, and decide what subjects security champions should learn. It is important that the theme is not too difficult and can be used in the field. The development team goes through a cycle of implementing and verifying the results while incorporating them.

Macnica recommends open source vulnerability management as the first topic for security champions to learn. Open source vulnerabilities pose a high level of risk in terms of being exploited in cyber attacks, and vulnerability management mechanisms and metrics are systematized, so it is relatively easy for security champions to tackle them.
As an example of what should be learned, there is the notion that all vulnerabilities are dangerous and must be dealt with, but in reality, only about 5% of all vulnerabilities are exploited in attacks, and among those 5%, there is a risk level. We will take appropriate action. The same is true for CVSS scores. We tend to think that vulnerabilities with a rating value of 7.0 or higher are particularly dangerous and should be dealt with proactively, but the CVSS rating is the severity of the vulnerability, not the security risk. is made clear. Getting this right will change the way you look at vulnerability management.
In Europe and the United States, the concept of risk-based vulnerability management is spreading. Here, the response is determined by combining the "property of assets", such as whether or not the compromised server handles personal information, and the "property of vulnerabilities", such as the possibility of an attack occurring and the actual situation. I will continue.
Summary
It is necessary for the security team to support the security champions of the development team, and for the security champions within the development team to be able to proactively decide how to respond to vulnerabilities and risks. As Macnica is also working on, in the future, if a system is realized that can automatically prioritize responses and perform risk analysis using technology, security champions with knowledge of the output will be able to make decisions to deal with issues quickly and correctly. Implementing such a concept will realize extremely lean security from both the organizational and technological perspectives, without impeding the speed of business development. Macnica will help make this a reality.
