はじめに
最新のインテル® CPU には、従来よりさらに強化された Trusted Execution Environment (以下、TEE) と呼ばれる インテル® ソフトウェア・ガード・エクステンションズ (インテル® SGX) が搭載されます。TEE は 各CPU に実装されるセキュリティ技術で、メモリー上に暗号化領域(エンクレーブ領域)を生成してプログラムやデータを配置することでデータを保護しつつプログラムを実行することが可能な技術です。
昨今、AI や IoT への取り組みによりデータの重要性が増す一方でパブリッククラウドを活用したスピード感のある開発と効率的な運用が求められています。このような ITインフラの革新に伴って システム要件も変化しています。これまでは機密性の高いデータは暗号化してストレージに保存すればよかったですが、アプリケーションが使用する際も暗号化された状態で扱うことで、システムの安全性と堅牢性をさらに高めるという選択肢も取れるようになってきています。
Fortanix 社では、ウェブアプリケーションで使用するメモリーも暗号化した状態で動作させる「秘匿化」をコードの変更なしで変換するツール、コンフィデンシャルコンピューティングマネージャー(CCM)を提供しています。
本記事では、Fortanix 社の CCM を使用して、Flask を使用して構築されたコンテナベースのシンプルなウェブアプリケーションをコンフィデンシャルコンピューティングに対応させる手順について解説します。
事前準備
・Fortanix CCM アカウント
Fortanix CCM を始めて使う方は、使用を開始する前にサインアップしてください。
・Docker Hub のアカウント
Fortanix CCM で変換したイメージを保管するために Docker Hub のアカウントが使用します。
・Microsoft Azure の従量課金制サブスクリプションを有するアカウント
ここではプラットフォームとしてインテル® SGX に対応した Microsoft Azure の Confidential Computing 仮想マシン、 DCSv2 シリーズを使用します。
2021年12月時点で、DCSv2 シリーズの使用には従量課金制サブスクリプションが必要です(無料アカウントでは DCSv2 シリーズを選択できません )。
※ご不明点がございましたら下部の問い合わせフォームにてお問い合わせください。
手順
ここからはアプリケーションをコンフィデンシャルコンピューティングに対応させる手順について説明します。
1. Fortanix CCM へのサインアップとログイン
1. https://ccm.fortanix.com/ にアクセスしてサインアップをおこないます。
2. アカウントが管理者( 上記 URL のデモ版では Fortanix ) に承認されると、Eメールアドレスとパスワードでログインします。
2. Fortanix CCM 内でアカウントを作成して選択
1. Fortanix CCM にログイン後、Accounts のページに遷移するので、[+ ADD ACCOUNT] をクリックして、新しいアカウントを作成します。アカウントとは Fortanix 社 DSM 及び CCM におけるセキュリティオブジェクトのトップ階層に当たり、通常は個人ではなくお客様の会社もしくは会社内の1つの組織を紐づけます。全てのセキュリティオブジェクト、グループ、アプリケーションは1つのアカウントに属する形になり、異なるアカウント間では共有されないようになっています。
2. 新しいアカウントの名前を入力後、オプションでアカウントのロゴを追加することも可能です。
3. コンピュートノードがアテステーションの失敗に関係なく正常に登録できるように[This is a test-only deployment] をチェックし、Attestation Service for Intel® SGX (IAS) をバイパスしてアカウントを作成します。詳細はユーザガイド [ Disable Fortanix CCM Attestation ] を参照してください。
4. [ CREATE ACCOUNT ] を選択してアカウントを作成します。
5. アカウントが作成されたら、[ SELECT ACCOUNT ] を押下して新しく作成したアカウントを選択して、コンピュートノードを登録し、アプリケーションを作成します。
3. 変換するアプリケーションを追加 ( 例:Flask を使ったウェブサーバー )
ここでは CC に対応させるアプリケーションの情報を登録します。
1. 左側メニューから [Applications] を選択し Applications のページに遷移したら、[+ ADD APPLICATION] を選択します。本記事では Fortanix の Docker パブリックレジストリーに登録されている、Flask を使ったシンプルなウェブサーバーを Enclave OS 上で動作させます。
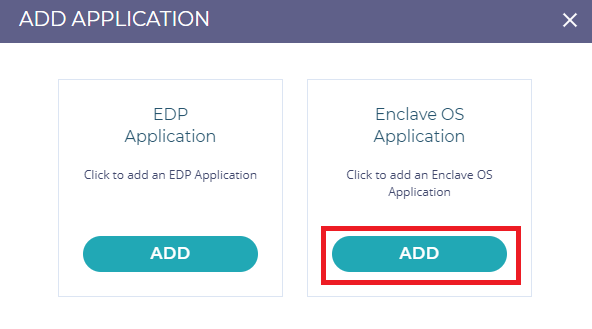
2. EDP Application と Enclave OS Application か選択するポップアップウィンドウが表示されます。
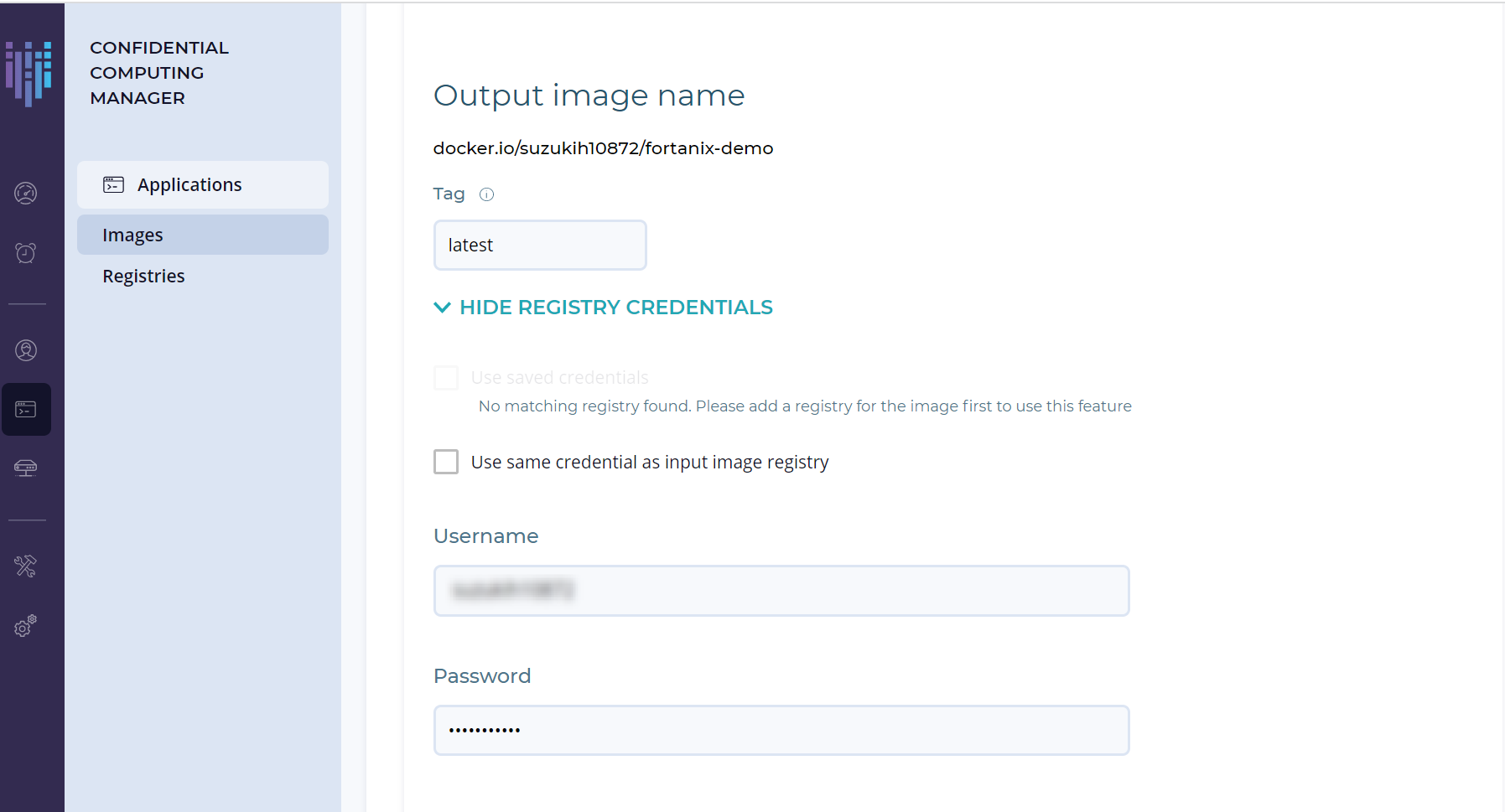
今回は Python Flask サーバーを実行する EnclaveOS アプリケーションを追加するので、EnclaveOS アプリケーションを選択します。設定は以下のように入力し[次へ]をクリックします。Output image name には、使用するプライベートレジストリー情報を入力してください。
※この記事では Enclave OS アプリケーションについて解説していますが、EDPアプリケーションについては EDP applications on CCM を参照してください。
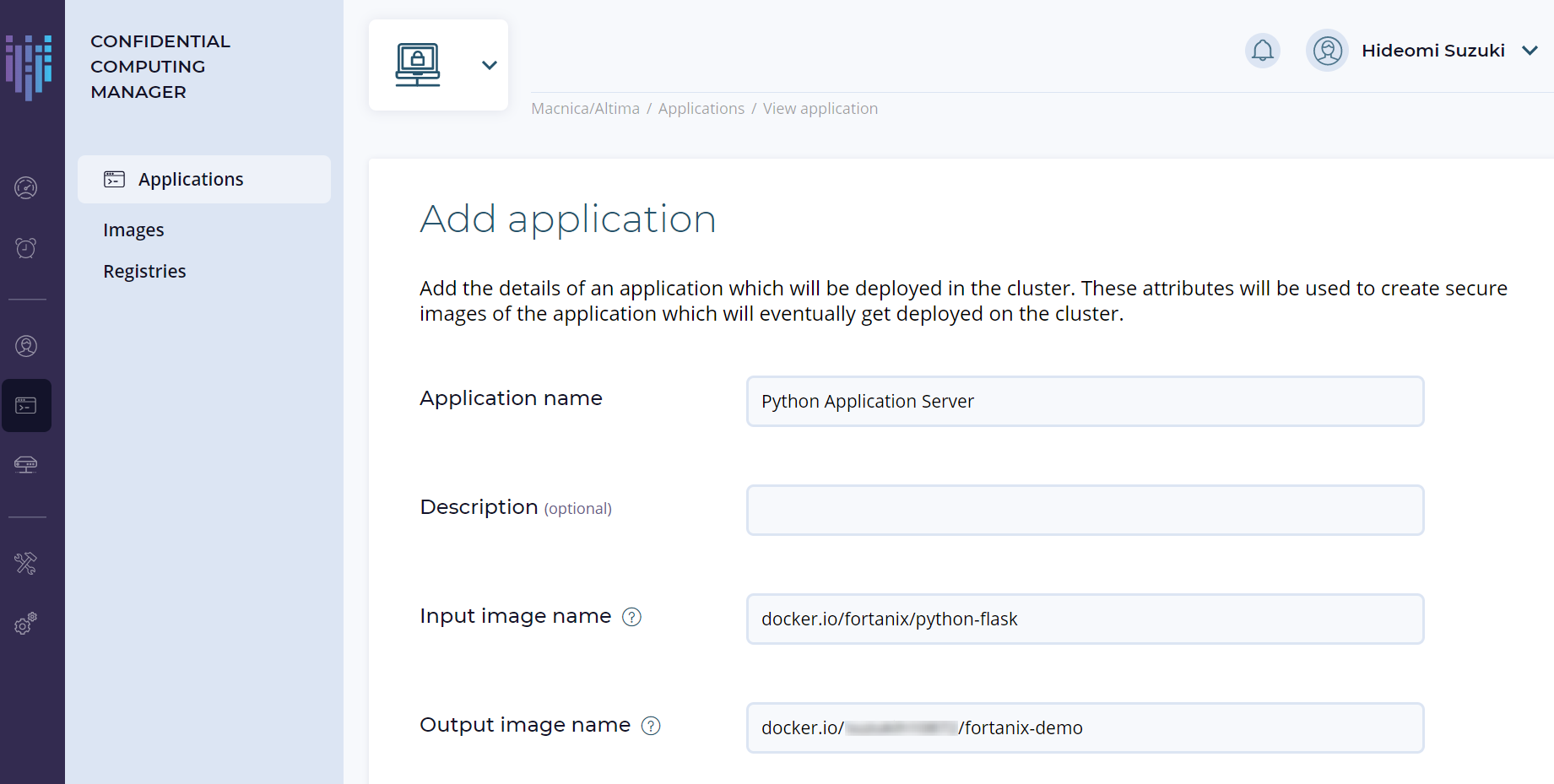
3. 以下のように関連する項目を入力し、NEXT をクリックします。本記事で使用するサンプルは、Fortanix 社の Docker Hub の公開レジストリーを使用します。
Docker Hub:https://hub.docker.com/u/fortanix
オプション:次のコマンドを使用して、オリジナルのアプリケーションを実行して確認できます。
sudo docker run fortanix/python-flask入力項目としては以下の通りです。
Application name : Python Application Server
Input image name : docker.io/fortanix/python-flask
Output image name : docker.io/suzukih10872/fortanix-demo #使用するプライベートレジストリー情報を入力
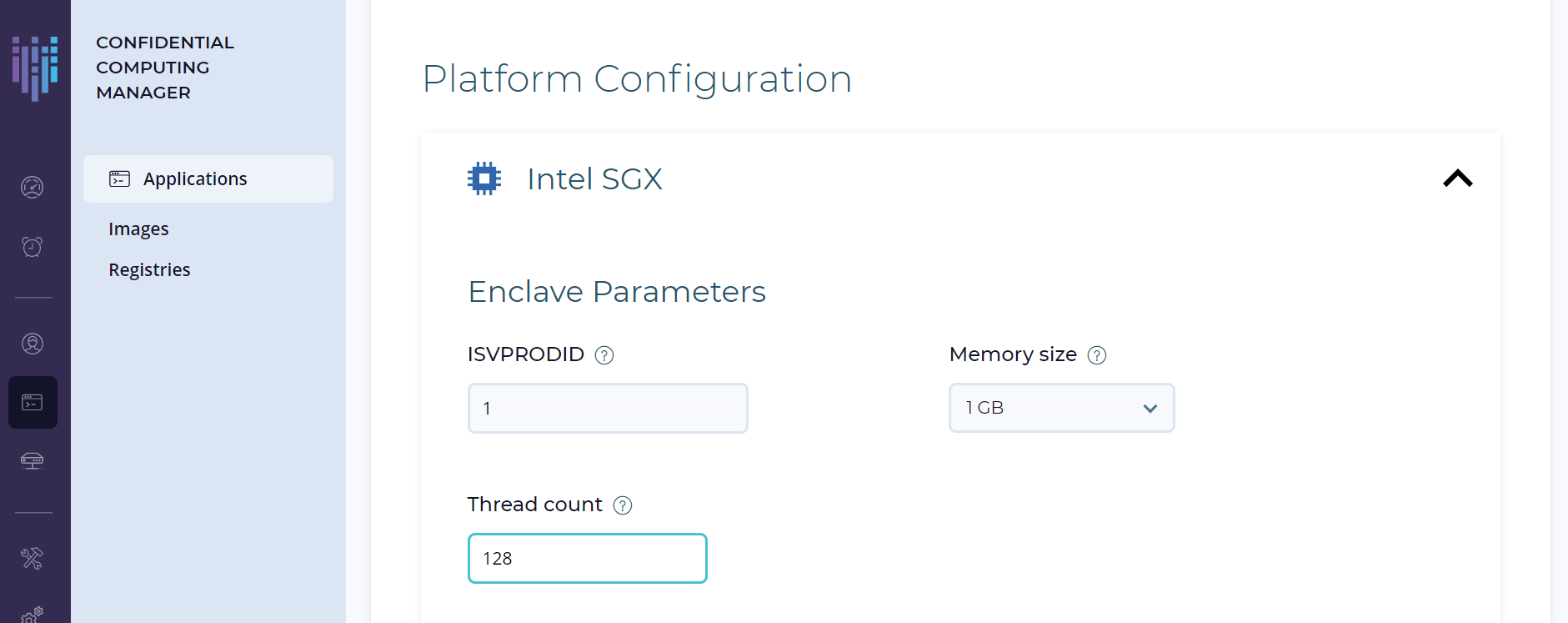
ISVPRODID : 数値の製品 ID です。 アプリケーションに対して 0〜65535 の範囲で一意の値を割り当てます。
ISVSVN : Enclave に割り当てられる数値のセキュリティバージョンです。
アプリケーションにセキュリティ関連の変更が加えられた場合は、この数を増やす必要があります。
Memory Size : ドロップダウンからメモリーサイズを選択して、Enclave のメモリーサイズを変更します。
Thread count : アプリケーションをサポートするためのスレッド数を変更します。
Output image name は、自分用のプライベートレジストリーを作成して使用するすることを推奨します。Enclave OS アプリケーションのイメージの設定に関するより詳細な情報は Adding an Enclave OS application を参照してください。
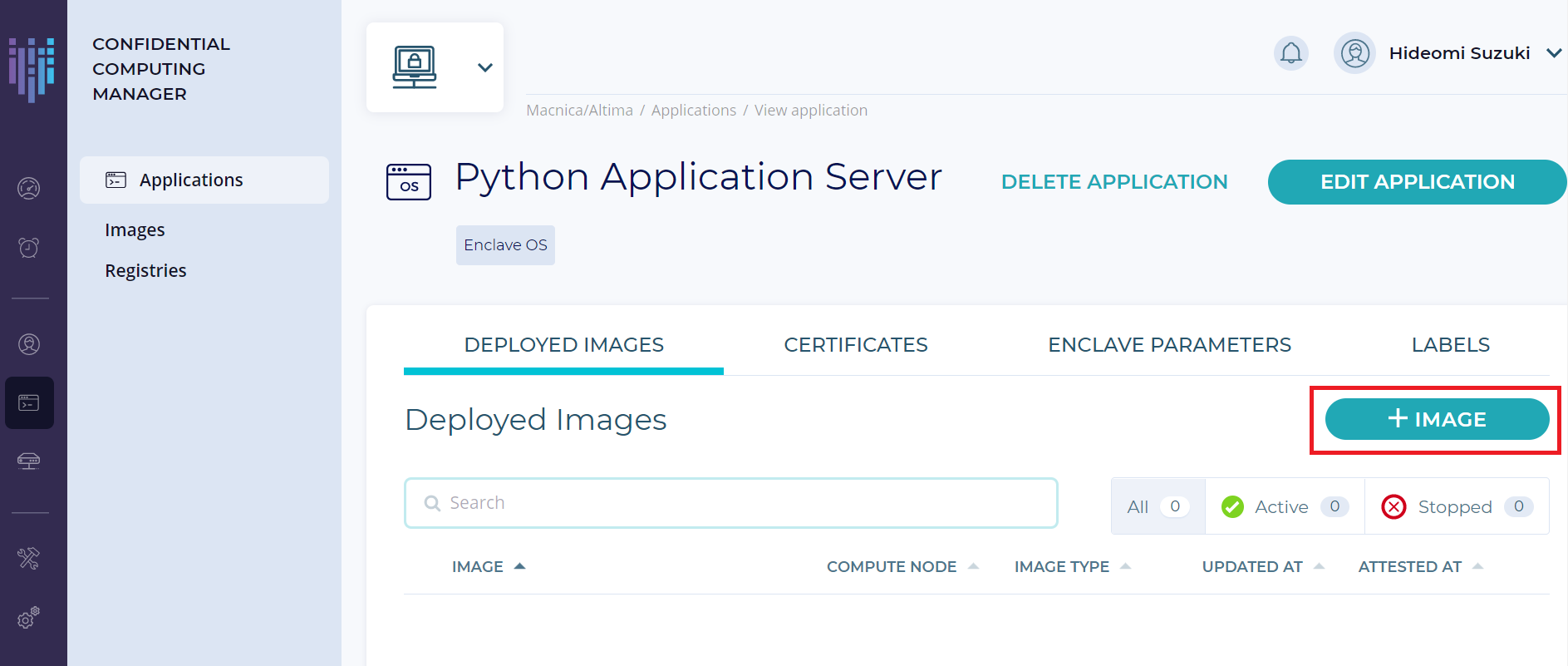
4. Fortanix CC 対応アプリケーションイメージを作成しプライベートレジストリーに保存
ここでは入力した情報をもとに CC に対応したアプリケーションイメージを作成します。
1. Fortanix CCM で作成したイメージは、特定のソフトウェアリリースまたはバージョンとなり、各イメージに1つのエンクレーブハッシュ(MRENCLAVE)がふられます。
2. Applications のページで前ステップで追加したアプリケーションを選択し、[+ IMAGE] ボタンをクリックします。
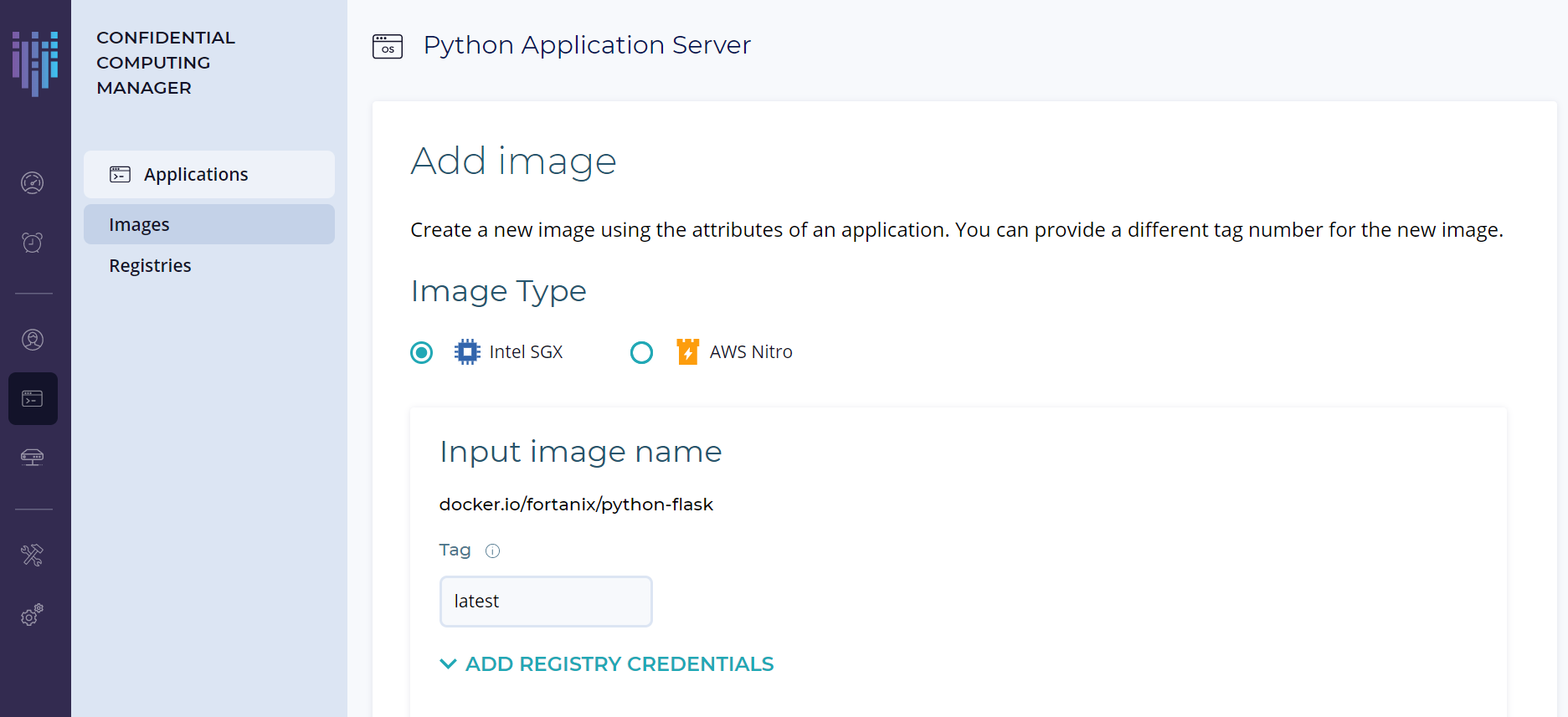
3. イメージタイプとしてインテル® SGX を選択します。
4. Input image name の [tag]フィールドは「latest」と入力して最新のビルドを指定します。
Fortanix のパブリックレジストリーに保存されるイメージを使用するため、クレデンシャルの入力は必要ありません。Output image name の [tag]フィールドも「latest」と入力し、ご自身の Docker Hub のプライベートレジストリーのクレデンシャルを入力します。
5. 入力後、[CREATE] を押下してください。
6. イメージの作成が完了すると、イメージが正常に作成されたという通知が表示され、アプリケーションが[Applications] タブに一覧表示されます。
イメージ作成に関するより詳細情報は以下の URL を参照してください。
・複数のイメージを追加する : https://support.fortanix.com/hc/en-us/articles/360048967971-User-s-Guide-Image-Registry
・Enclave OS アプリケーションイメージを作成する : https://support.fortanix.com/hc/en-us/articles/360043529411-User-s-Guide-Create-an-Image#CreateanImageforEnclaveOSApplications
5. アプリケーションイメージの承認
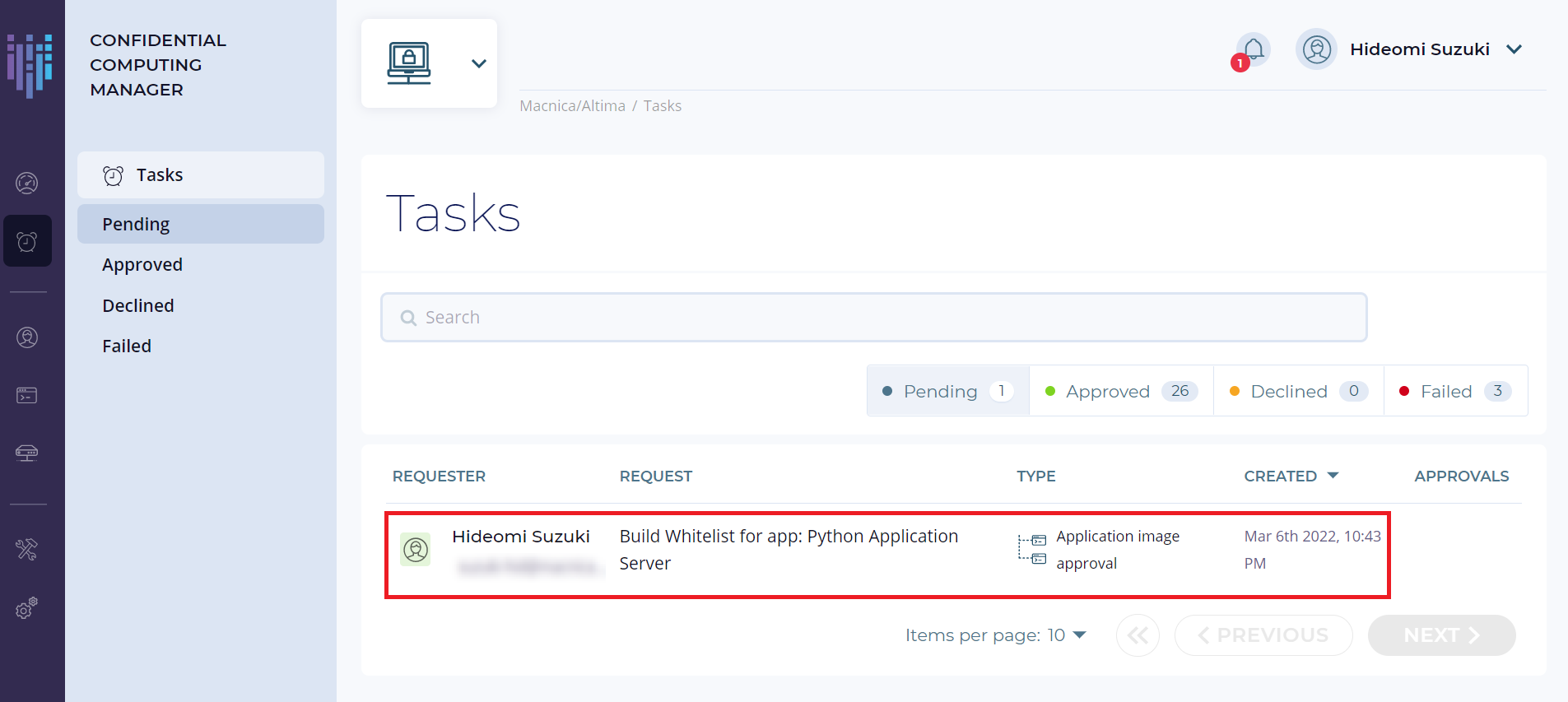
1. 左側メニューの Tasks タブを選択し、Pending となっている Task から「Build Whitelist for app: Python Application Server」をクリックします。
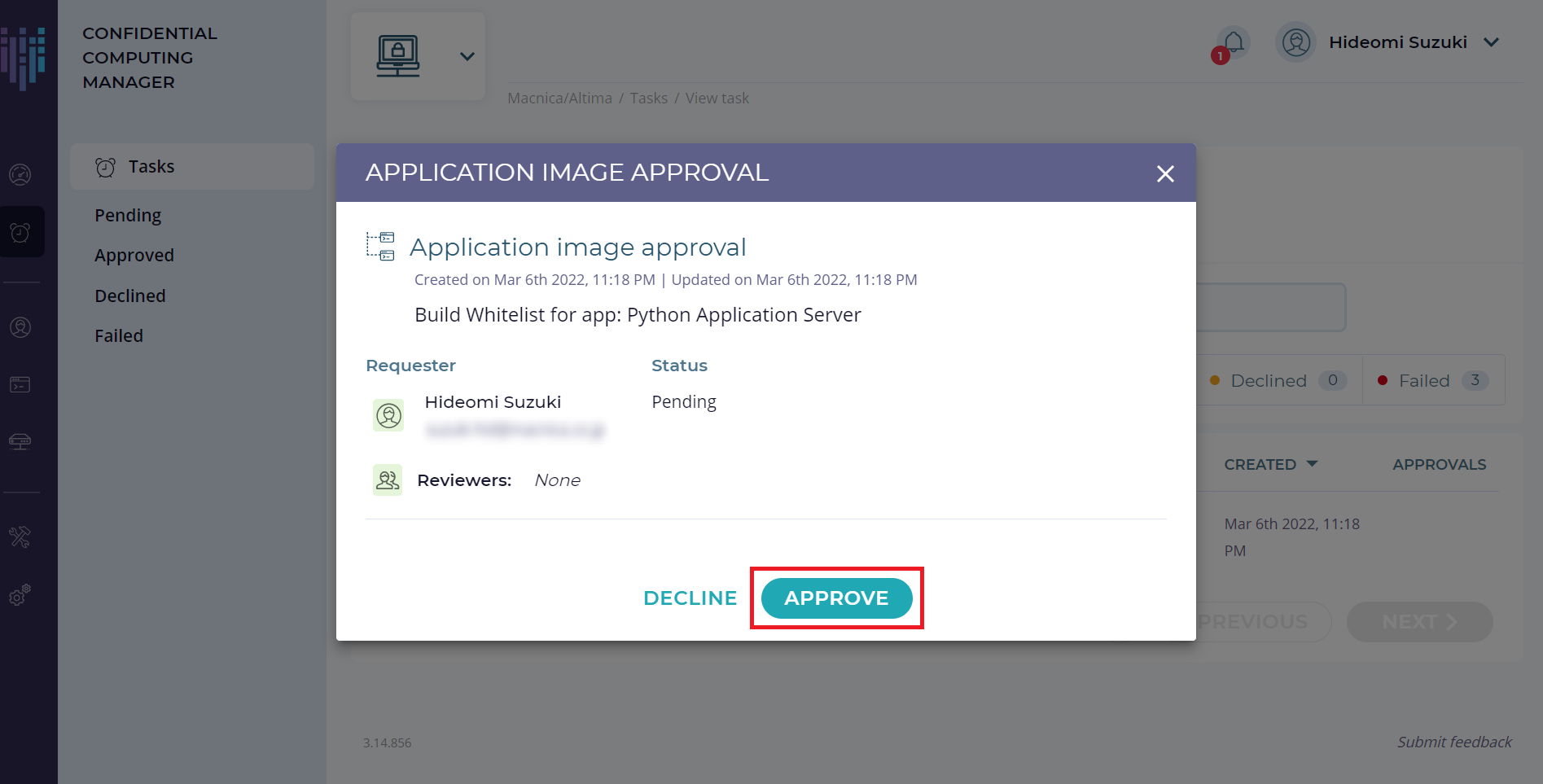
2. イメージをホワイトリストに登録するために「APPROVE」をクリックします。 これによって Pending の Task リストから消え、Images 一覧では APPROVAL が「Approved」に変更されます。
6. コンピュートノードエージェントの登録
ここでは作成したイメージの実行権限を与えるためのトークンを発行し、コンピュートノードエージェントに登録します。
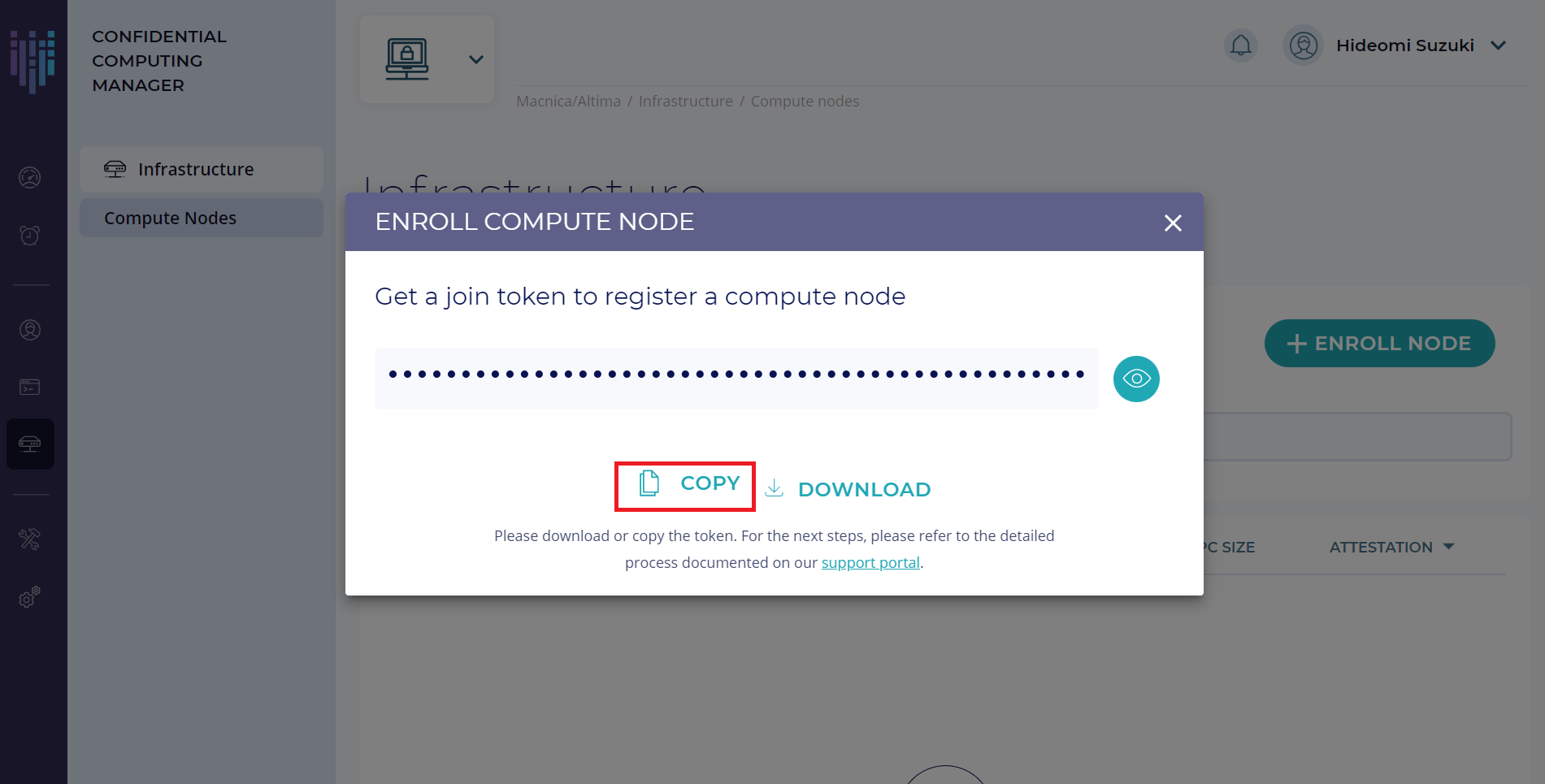
1. 左側メニューの Infrastructure タブを選択し、Compute Nodes のページで [+ ENROLL NODE] をクリックします。
2. ポップアップが表示されるので、[COPY] をクリックしてトークンをコピーします。このトークンは、コンピュートノードが認証用に使用します。
3. Microsoft Azure Portal にアクセスしてコンピュートノードエージェント VM を作成します。
検索ボックスに「Fortanix」とタイプするとリストされる「Fortanix Confidential Computing Node Agent」を選択して「作成」ボタンを押下します。もしくは、Fortanix社のウェブサイトで提供される Fortanix Node Agent ソフトウェアをインストールしてお手持ちのインテル® SGX マシンで動作させることも可能です。
4. 下記のように情報を入力して、「確認及び作成」を選択します。下記以外はデフォルトで入力される値のままでかまいません。
リソースグループ:新規作成を選択し名前をつけてください。 例) CCNAGRv1
Compute Node Name:適当に名前をつけてください。 例) ccna1
Username : 適当に名前をつけてください。 例) hoge
Password : 適当に設定してください。
Join Token : 「ENROLL NODE」押下時に発行されたトークンをコピーして貼り付けてください。
検証後、「作成」ボタンを押下すると Azure 上でコンピュートノードエージェントを起動します。
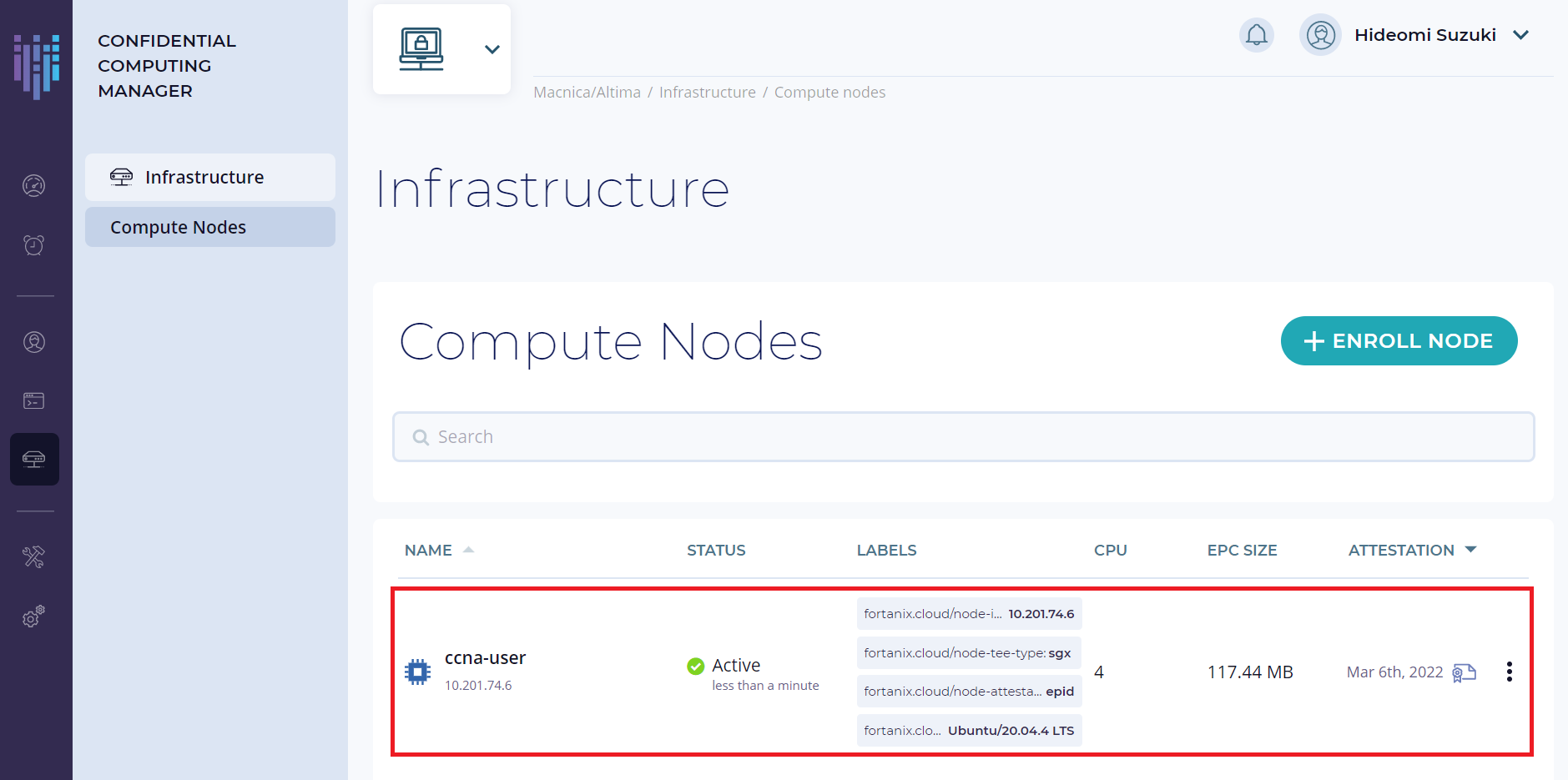
5. コンピュートノードエージェントのデプロイが完了すると、コンピュートノードが Fortanix CCM に登録され、Compute Nodes 一覧に表示されます。
コンピュートノードの登録に関するより詳細な情報は CCM Compute Nodes を参照してください。
7. 登録したコンピュートノードで CC アプリケーションを実行
1. 作成したコンピュートノードエージェントの VM を選択してパブリック IP アドレスを確認し、ssh でアクセスします。ログイン後、以下のコマンドをタイプして登録されたコンピュートノードエージェントに docker をインストールします。
sudo apt install docker.io2. 作成した CC 対応アプリケーションイメージを起動するために 以下のコマンドをタイプして Docker の アカウントにログインします。
sudo docker login3. 次のコマンドをタイプして、作成したコンピュートノードで CC 対応アプリケーションイメージを実行します。
sudo docker run --device /dev/sgx --device /dev/gsgx -v /var/run/aesmd/aesm.socket:/var/run/aesmd/aesm.socket -e NODE_AGENT_BASE_URL=http://20.124.109.247:9092 suzukih10872/fortanix-demo以下の部分はご使用環境にあわせて変更してください。
20.124.109.247 : コンピュートノードエージェントのパブリック IP アドレス
9092 : ノードエージェントがリッスンするデフォルトのポート
suzukih10872/fortanix-demo: 変換したアプリケーションイメージを格納するご自身の Docker Hub プライベートレジストリー
まとめ
今回は、Fortanix 社の CCM を使用して、シンプルなウェブアプリケーションをコンフィデンシャルコンピューティングに対応させる手順について説明いたしました。
Fortanix CCM のその他の機能については、次のガイドをご覧ください。
・Provision a TLS certificate using CCM: Certificate configuration
・Use identity and policy management on applications and compute nodes
- Application and compute node policy enforcement
- Compute node labels
・Build and deploy confidential computing applications in Rust using the Fortanix EDP platform: EDP applications on CCM.
お問い合わせ
その他のご要望やご質問があれば、以下の問い合わせボタンからお問い合わせください。
Fortanix メーカー情報Topへ
Fortanix メーカー情報Topに戻りたい方は以下をクリックしてください。
