
それって本当に「Detection & Response」のソリューション?
マクニカに勤務するセキュリティ対策のエキスパートでエバンジェリストの山田さんは、セキュリティ商材のセールスチームに勤務する吉川さんからまた相談を受けました。内容はXDR、EDRにおける「~DR」、すなわち「Detection & Response(検出&対応)」。の考え方について再確認をしたいとのこと。山田さんが吉川さんの質問に答えます。
登場人物

| 名 前 | 山田 耕平 |
| 年 齢 | 30代 |
| 性 別 | 男性 |
| 職 種 | プリセールスエンジニア |
| 所属部署 | 要検討 |
| 概 略 | セキュリティ商材のプリセールスエンジニアとして活躍。社内外にXDRの必要性を啓発するエバンジェリスト的な役割も担っている。 |

| 名 前 | 吉川 里奈 |
| 年 齢 | 20代 |
| 性 別 | 女性 |
| 職 種 | セールス |
| 所属部署 | フィールドセールス |
| 概 略 | マクニカのセキュリティ商材のセールスチームに配属された中途採用の新人。前職では5年間、IT製品のマーケティングとフィールドドセールスの職務に就いていた。ただし、セキュリティ商材のセールスは未経験。 |
それって本当に「Detection & Response」のソリューション?

山田さん、たびたびお時間を頂戴して恐縮です。
まったく問題ないですよ。今回は「Detection & Response(検知と対応)」について少し詳しく知りたいんだよね。


そうです。実は先日、お客さまから「XDR (eXtended Detection & Response)」のソリューションに関するお電話での問い合わせがあり、それにご対応している最中に「Detection & Response」の部分について、自分でも良く理解していないと気づいたものですから。
なるほど。そのお客さまは「EDR(Endpoint Detection & Response)」製品はすでにお使いなのかな?


ええ。ただし、お話しを聞いていると、その製品が本当にEDRのソリューションなのか怪しいと感じまして……。もし、EDR製品ではないとすれば、その製品は先日伺ったXDRのセンサー(データソース)として使えないのではないかと。
なぜ、お客さまのEDR製品が、EDRのソリューションではないと感じたの?


私が調べて認識しているEDRと、お客さまがお話しになられたEDRとの間にズレを感じたからです。とはいえ、私の知識レベルでは、お客さまがお使いのEDR製品は、EDRではないとの確信が持てず、お客さまに「それはEDRではありません」といえませんでした。そこで今回、山田さんに「Detection & Response」の本質的なところを改めて伺うことにしたわけです。
なるほど、確かにEDRは沢山のメーカーからリリースされていて、持っている機能も様々だから、EDRとしては不十分と言えるような製品があってもおかしくないね。そして、「Detection & Response」ソリューションに求められる要件についてだけど…。


お願いします。
「Detection & Response」ソリューションの本質とは
吉川さんはすでに知っていると思うけど、「Detection & Response」のソリューションは、AI(人工知能)を使った最近のウイルス対策ソフト(=次世代型ウイルス対策ソフト:NGAV)や次世代型ファイアウォール(NGFW)のようなサイバー攻撃による脅威の侵入を防御するソリューションではなく、内部ネットワークに侵入した脅威を検知し、対応するための仕組みだ。


はい、その辺りは理解しています。NIST(National Institute of Standards and Technology:米国国立標準技術研究所)が定めるセキュリティ対策フレームワークを使って言えば、「①識別(Identify)」「②防御(Protect)」「③検知(Detect)」「④対応(Respond)」「⑤復旧(Recover)」のうち、「③検知」以降の対策を支える仕組みですよね。※1
そのとおり。サイバー攻撃のプロセスで言えば、攻撃者はマルウェアを通じてターゲット組織の端末を乗っ取り、遠隔から操作しながら、ネットワーク内部でマルウェアの感染を広げたり、偵察をしたり、管理者権限を窃取するといった内部活動を展開する。そうした内部活動を早期に検知して、対応するための仕組みが、EDRなどの「Detection & Response」ソリューションということになる。それを図で表すとこうなるね。

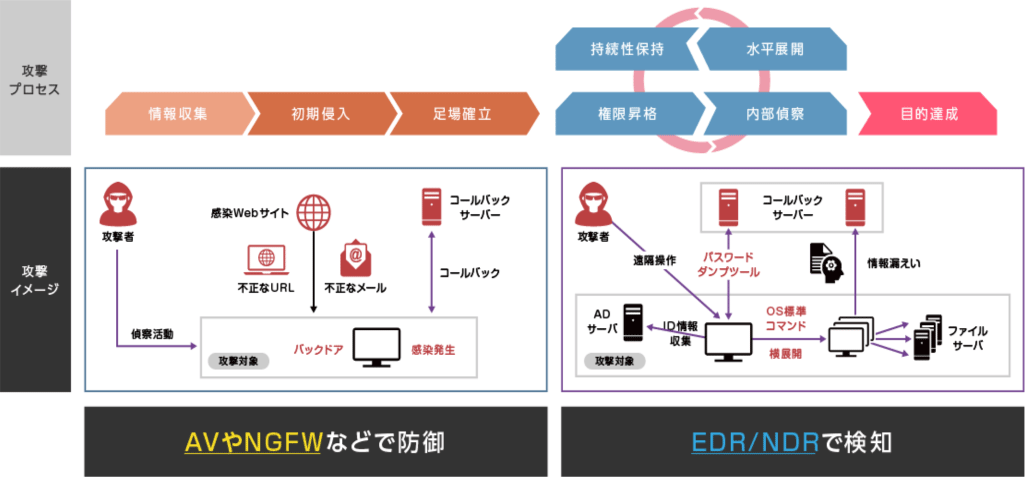

この図もわかりやすいですね。
そこで吉川さんに質問です。EDRなどのソリューションによって、何らかのセキュリティインシデントの発生がとらえることができたとする。それに適切に対応するうえでは、何が必要になるでしょう。


それは、ログの調査によって、インシデントの影響範囲をすばやく特定することと、脅威侵入の経路を突き止めことですね。そうしなければ、適切な対処・対応ができないはずですから。
そう。脅威の検知に加えて、そうした調査と分析を速やかに行えるようにすることが「Detection & Response」ソリューションの本質といえる。そして、そのソリューションを実現するうえでは、ログを過去に遡りながら調査し、マルウェアの感染源を突き止め、そこからどのような経路をたどって、どのように感染が広がり、インシデントの発生につながったかを調べ上げなければならない。言い換えれば、「Detection & Response」では、遡及調査と分析によってインシデント原因を突き止めて整理し、恒久的な対応策につなげることが大切で、「Detection & Response」のソリューションには、それを支援するための仕組みとして、インシデント対応に必要なログをきちんと記録し参照できることが非常に重要なんだ。


そうですよね! 私も、EDRについてお客さまと対話しているときに、そう考えたんです。ところが、先に触れたお客さまは、お使いのEDRの機能について、AIを使った振る舞い検知のお話ししかせず、ログの遡及調査は行えないし、そのような機能は知らないとおっしゃられていたんです。そこに違和感を抱いたんです。
うーん、おそらく、そのお客さまが使われているEDRは、NGAV製品をEDR製品と称して販売しているものかもしれない。実は、そうした製品は意外と多くて、それが原因でEDRソリューション、あるいはEDRソリューションの要件に対する誤解がお客さまの間で多く見受けられているんだ。

「Response」に求められる知識とスキルとは

ところで、EDRなどのソリューションを導入することで、セキュリティ担当者の運用負担が大きくなるとのお話しを伺いました。また、その問題を解決するのがXDRであるとも伺いました。
そうだね。


確認のために「Detection & Response」を遂行するうえで必要とされる知識とスキルについても、少し具体的にお聞かせください。
まず、「Detection」の部分は、適切なEDR製品を選ぶことで自動化されるので、そこには知識やスキルは必要とされないと見たほうがいい。


としますと問題は「Response」の部分になりまね。
そうだね。「Response」に関しては、例えば、EDRのソリューションが発した多くのアラートの「真偽判定」を行ったうえで、問題端末をネットワークから隔離したり、各種のログ(Active Directoryなどの認証ログ、FWログ、プロキシサーバログ、ファイルサーバログ)を確認したりする必要がある。


それらの作業を適切に行うにはどのような知識やスキルが必要なのでしょうか。
最低限必要とされるのは、最新の脅威や脆弱性に対する相応の知識とともに、アラートやログを分析するスキルが必要とされる。ただ、最近のEDRやNDR(Network Detection & Response)の中には、問題端末をネットワークから隔離する作業を支援してくれる製品も多いので、利用する製品によっては、必要となるスキルレベルを抑えることができるようになっていることもあるね。。


いずれにせよ、そうした高度な知識・スキルが要求されるEDR、NDRによる「Response」のハードルを下げるのが、XDRの役割であるということですね。また、XDRの導入効果を高めるためにも、EDRなどに関する製品選びにも慎重を期す必要がありそうですね。
そのとおりです。


本日もありがとうございました。
今回の3つの学び
- D&Rの本質とは?
「Response」の作業を効率化することであり、ログを記録として保持し、インシデントの原因と感染経路を過去に遡って調査できるようでなければならない - Detectionとは?
内部ネットワークに侵入した脅威を検知し、インシデントの影響範囲をすばやく特定、脅威侵入の経路を突き止めることである。また適切なEDR製品を選ぶことで自動化されるため、ここに高度なスキルや知識は必要となさないと考えても良い。 - Responseとは?
検知された脅威に対して、迅速かつ適切な対応を行うことを指す。Responseの主な手法は、検知された脅威の隔離、削除、修復などとなり高度なスキルや知識が必要となる場合が多い。
※1出典:独立行政法人情報処理推進機構セキュリティセンター「重要インフラのサイバーセキュリティを改善するためのフレームワーク1.1版」
お問い合わせ・資料請求
株式会社マクニカ XDR 担当
- TEL:045-476-2010
- E-mail:XDR@macnica.co.jp
平日 9:00~17:00


