Cloud/next-generation gateway security
Due to changes in the times such as work style reforms, the number of connecting terminals has increased from internal PCs to external PCs and mobile terminals, and the use of cloud services has shifted the data to be protected from internal to external (boundary).
CASB is a solution that provides visibility, data protection, and governance for cloud applications used by enterprises.
Points to consider regarding information leakage from cloud services
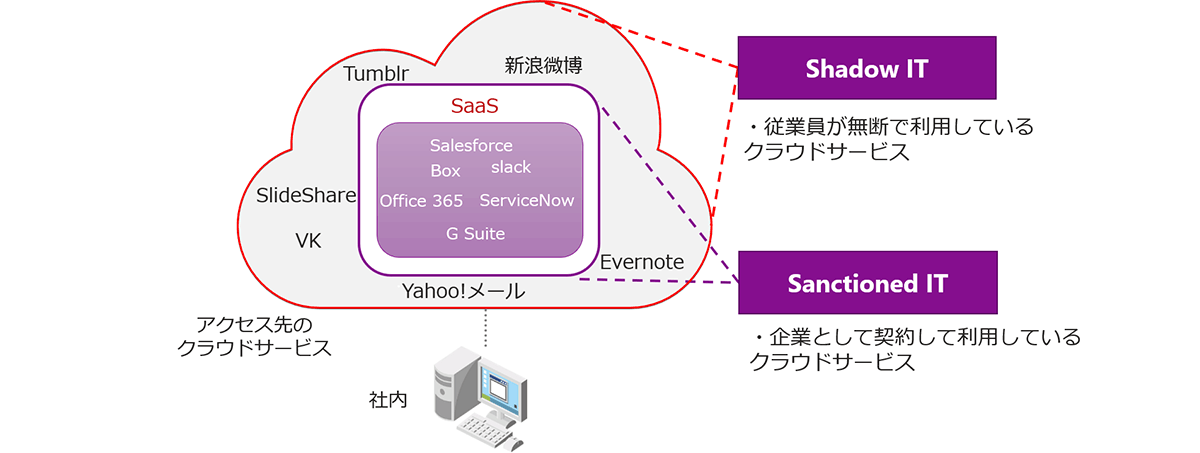
Points to consider regarding information leakage from cloud services
- Shadow IT is a cloud application that employees use without permission from the company.
- IT admins don't know
Assumed risks when using cloud services
ShadowIT: Shadow IT
- Leakage or loss of data due to the use of unauthorized cloud applications (apps with low encryption strength, apps that can be accessed by third parties, etc.) (internal fraud/negligence)
- External accountability for cloud application usage (compliant with standards)
Limitations of Web Filter and Why We Need CASB
- Category-based access control has limitations.
- For example, if you allow access to the category "file storage" in Web Filter, all file storage can be used regardless of company policy.
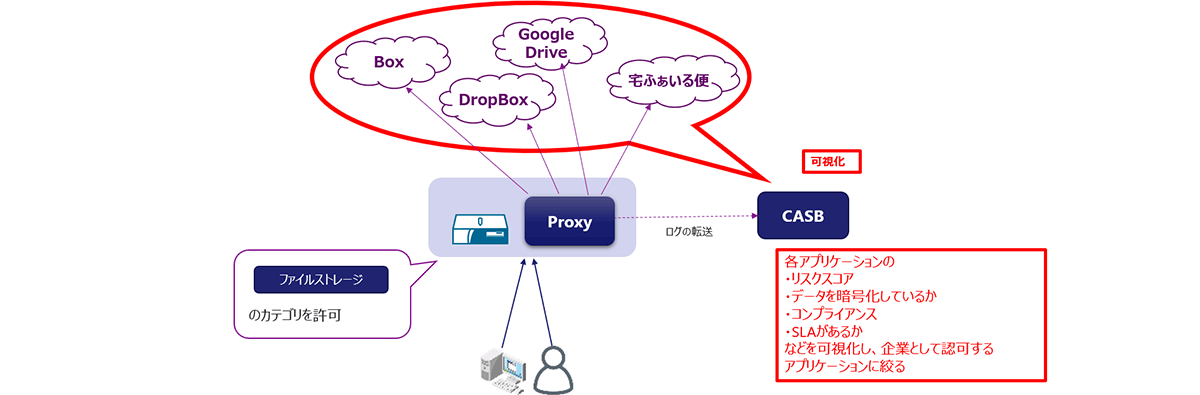
- Conversely, even if you block the "file storage" category in Web Filter, you can still access sites that were not determined as file storage by Web Filter (there is a possibility that omissions have occurred).
Examples of information leakage via shadow IT
- Employees arbitrarily use cloud services that are not permitted by the company and upload confidential information to the cloud service.
- Data is stored without encryption on the cloud service provider side, and information leakage via the cloud service

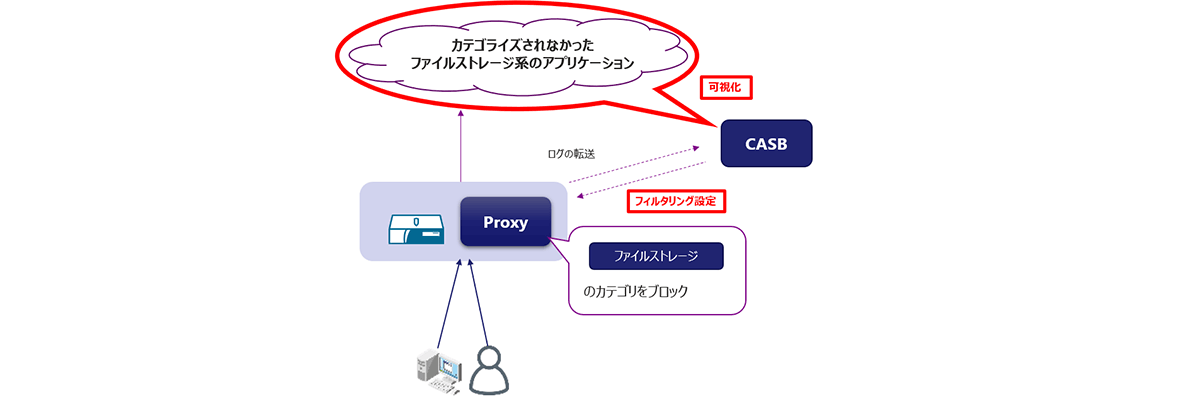
CASB (Shadow IT) introduction configuration example
- Visualization of shadow IT becomes possible by linking access logs acquired by Proxy and Firewall to CASB

CASB's Approach to Shadow IT
Visualization
Visualization of cloud application usage by employees
Evaluation
Evaluation of cloud applications (risk score, data encryption, compliance)
reporting
Output the above information as a report
Shadow IT operation flow
- In order to use cloud services safely, it is necessary not only to visualize shadow IT, but also to implement the following flow by utilizing CASB.

Key points when choosing Shadow IT
- Extensive cloud application information
-
- How many cloud services can be evaluated
- How often is the data being evaluated updated?
- Reflection speed when requesting registration
- Compatibility with existing Gateway products
-
- What is the configuration when forwarding logs from Proxy or FW?
- Can control and monitoring be performed smoothly after visualization?
- Is it a double investment with the current Gateway product?
- agentless
-
- Is it necessary to install an agent on the terminal?
What is Sanctioned IT?
- Sanctioned IT = Cloud services contracted and used by companies, authorized cloud services (Office365, box, Slack, etc.)
Assumed risks when using cloud services
Sanctioned IT:Sanctioned IT
- Unauthorized data exfiltration due to over-sharing of data within cloud applications
- Account hijacking, data destruction, leakage, etc. due to unauthorized access to cloud application accounts
- Internal User Fraud
- Delivering malware through shared files
- Lack of visibility into data stored on cloud applications (audit)
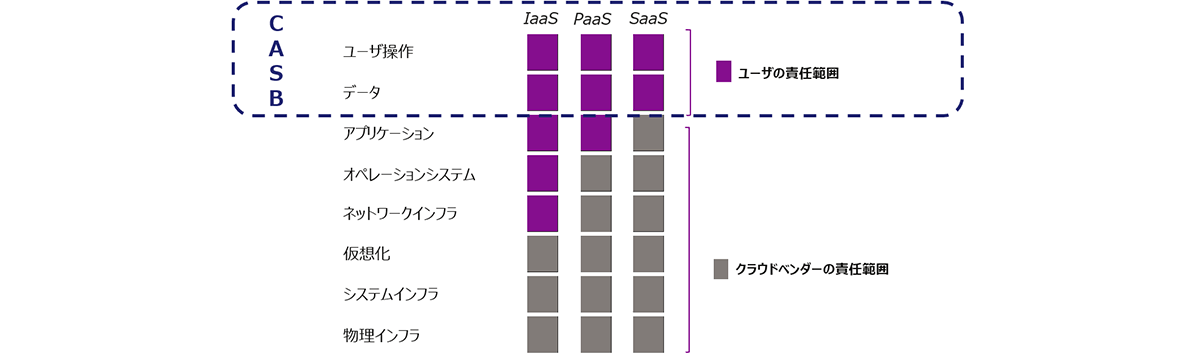
shared responsibility model
- Responsibilities vary by service
- Users are responsible for data protection and account management on cloud services
Sanctioned IT introduction configuration example
- API linkage is performed with the target cloud service and CASB

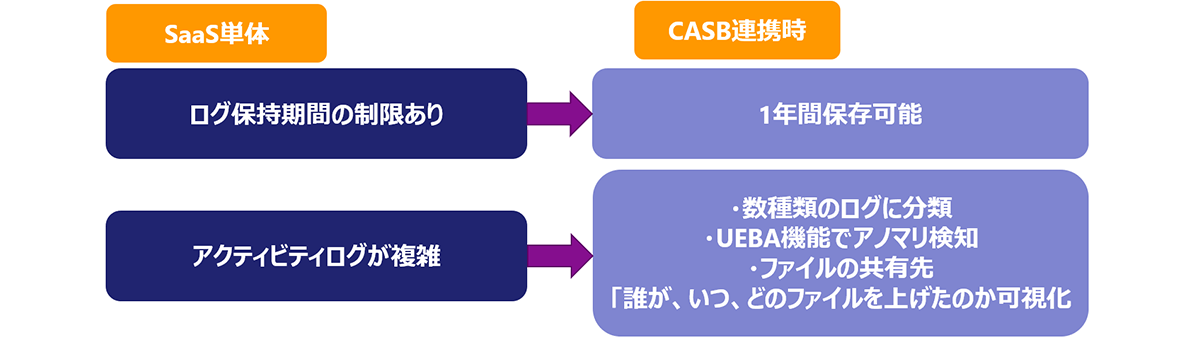
Sanctioned IT Issues Solved by CASB
CASB's Approach to Sanctioned IT
Visualization
Understanding and monitoring what kind of data is uploaded to the target cloud application (shared destination/shared data)
behavior detection
Whether the employee before retirement is acting suspiciously or whether the account of the cloud service has been hijacked
data protection
Detect and, if necessary, control when data identified as sensitive information is uploaded to cloud services
Selection points for Sanctioned IT
- Speed and frequency of API calls
-
- API is not real time. The speed of API calls varies depending on the SaaS/CASB manufacturer
- Easy to understand activity log
- Anomaly event detection
-
- There is a function that can detect user behavior by machine learning
- Presence or absence of optional functions
-
- Box in target cloud service
- URL filtering function in the target cloud service
Related solutions
Broadcom products
Skyhigh Security
Cato Networks


