レポートについて
マクニカでは、2018年上半期 (4月から9月)に観測された、日本の組織から機密情報 (個人情報、政策関連情報、製造データなど)を窃取しようとする攻撃キャンペーンについて、注意喚起を目的としてレポートを作成いたしました。
ステルス性の高い遠隔操作マルウェア (RAT)を用いた事案を中心に、新しい攻撃手法やその脅威の検出について記載しています。最後に、本文中で紹介した攻撃キャンペーンで使われたインディケータを掲載します。
一般に公開されているブログ、リサーチペーパーでは、マルウェアのリバースエンジニアリング、暗号解読、攻撃者の特定といった視点が多くあり、検体解析やリサーチを行う分析者には大いに助けになります。一方、組織で対策を検討して、日々検出されたアラートに対応している情報セキュリティ担当者には敷居の高い情報かもしれません。本レポートでは、組織の情報システムでセキュリティに携わっている方々へ効果的な注意喚起が図れるよう、観測された攻撃グループとその攻撃のTTPs、標的業種を表にし、脅威の検出に関しての考察を記載しています。対策手法のテクノロジーの進化に伴った際限のない投資から解き放たれ、自社が関連する業界を狙った攻撃グループに焦点を当てた効果的な対策の一助になればと考え作成いたしました。
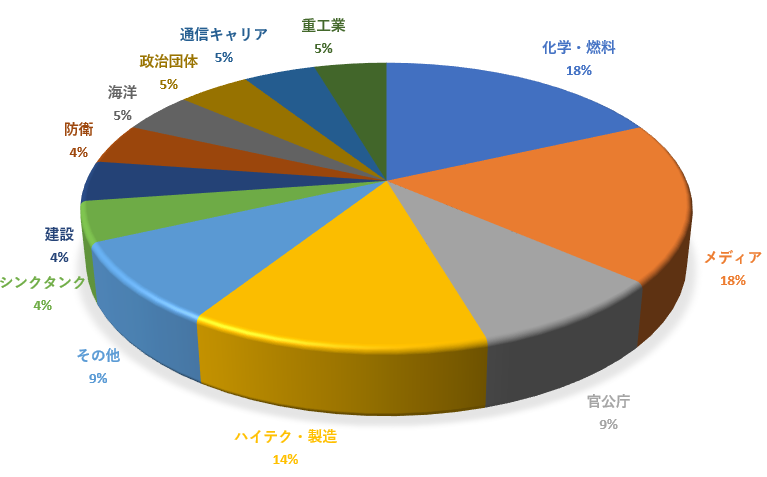
攻撃が観測された業種
2018年上半期の観測では、化学・燃料やハイテク関連の製造企業、海洋関連など、国際競争力のある企業に対して、製造データを含む知財を窃取する試みが増加しています。特に国際的な技術競争の激しい先進的な分野でより一層の注意が必要だと分析しています。通信キャリアを標的とした攻撃も発生しており、過去にCloudHopper攻撃キャンペーン で明らかになったように、その配下の大規模なネットワークを標的とするような規模の大きな攻撃キャンペーンにつながる可能性を注視する必要があると分析しています。政府高官の会談前のタイミングで、外交や政治判断に利用できそうな情報を狙い、官公庁やシンクタンク、メディアを標的とした攻撃キャンペーンは、一定のレベルで継続して発生していると分析しています。
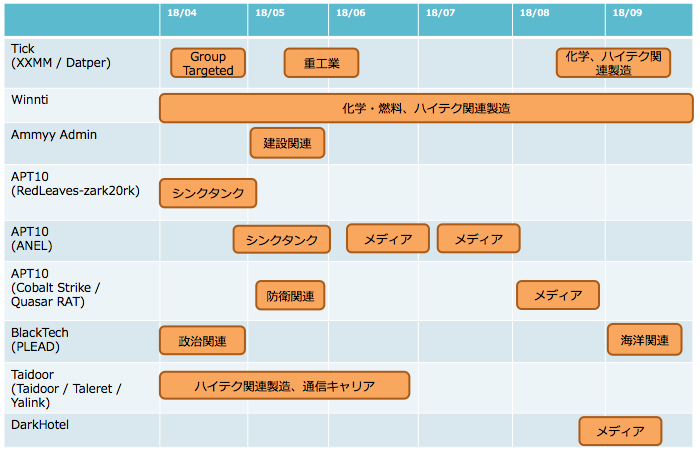
攻撃のタイムライン
以下は、弊社で把握・観測しているRATを用いた標的型攻撃キャンペーンのタイムラインチャートです。知財を狙った標的型攻撃というステルス性が高いという攻撃の性質や、日本への標的型攻撃をすべて網羅しているとは考えられないため、ここに示した事案は氷山の一角と考えています。攻撃の傾向としては、過去に台湾を標的とした攻撃でよく観測されていたPLEAD やTaidoor を使った攻撃の観測が日本国内で増加しています。新規の感染を試みるメールの添付ファイルについては、オフィスファイルが多く、マクロが多用されています。一部のオフィスファイルでは、CVE-2017-8759といった古い脆弱性が用いられ、新しい脆弱性が攻撃に活用された観測はありません。
また、検出が後手に回っていると分析していますが、グローバルIPアドレスを持つ公開サーバーでは、C&Cに通信せず、リスニングポートから遠隔操作を受け付けるタイプのWinntiグループ の攻撃がひそかに長期に継続しています。
日本を狙う標的型攻撃に対する取り組み
「日本を狙うサイバーエスピオナージ (標的型攻撃)の動向 2018年上半期」で記載した通り、日本を狙った攻撃が観測されています。日本を標的とするサイバー攻撃が、欧米諸国を狙う攻撃と、攻撃の特性が一致しているとは限りません。
マクニカでは日本企業を狙う攻撃は日本で解析する必要があると考え、セキュリティ研究センターを設け、日々攻撃を解析しています。
攻撃者に関する脅威インテリジェンスを活用したMpression Cyber Security Service™を提供し、日本を狙う攻撃への対策を支援いたします。
Mpression Cyber Security Service™とは
日本を狙う攻撃に関する脅威インテリジェンスを活用して、お客様が抱えるサイバーセキュリティにおける課題を解決する独自のサイバーセキュリティサービスです。
下記3種類のサービスを提供しています。
- スレットハンティング&インシデントレスポンスサービス
- 脅威照合ポータル
- インシデント対応サービス
スレットハンティング&インシデントレスポンスサービスとは
エンドポイントの調査ツール、平時の監視サービス、インシデント発生時の調査サービスおよび調査結果・対応策のレポートをトータルでご提供します。検知フェーズでは高度な攻撃を検出する能力を向上させ、調査・分析・対応フェーズでは適切かつ迅速に実施できるよう支援します。
特徴
- 日本の組織のみを狙う攻撃に関する業界トップクラスの脅威インテリジェンスを活用
- セキュリティに精通した凄腕ハンターによる脅威検出