product
- Line up
- Network Security: Trellix (formerly FireEye) Network Security
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense
- Network Security: Trellix (formerly McAfee) Network Security Platform
- Endpoint: Trellix (formerly FireEye) HX
- Endpoint: Trellix (formerly McAfee) Mvision
- Data Protection: Trellix Data Security
- Email Security: Trellix (formerly FireEye) Server Edition
- Email Security: Trellix Cloud Edition
- Security Operations: Trellix (formerly FireEye) Helix
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management)
- Enhanced cloud governance: Trellix (formerly FireEye) Cloudvisory
- File Security: Trellix (formerly FireEye) Malware File Storage Scanning
- Integrated Management Solution: Trellix (formerly FireEye) Central Management
- NDR Solution: Network Investigator (NI) / Packet Capture (PX)
- Cloud-based File Threat Protection: Trellix IVX Cloud
Specifications/Technical Information
- Trellix (formerly FireEye) Technical Information
- Trellix (formerly FireEye) Specifications
- Network Security: Trellix (formerly FireEye) Network Security Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Specifications
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Technical Information
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Specification
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Technical Information
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Specifications
- Integrated Management Solution: Trellix (formerly FireEye) Central Management (CM) Series Specifications
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management) Technical Information

Trellix
Trellix
Email security (3) - A must-see for companies that have introduced Office365! What cloud email security should be implemented now

Many cyber crimes are said to start with emails.
Although companies have introduced email security products and are taking countermeasures, the current situation is that attackers are also trying to infiltrate using all possible means.
In particular, the number of companies using Office 365 has increased significantly, and simultaneous attacks against multiple targets have been carried out.
Unknown threat detection and analysis of various file types are important for the secure use of Office 365.
In this article, we analyze the actual state of targeted attacks and the gaps between current security measures, and introduce Trellix (formerly FireEye) Email Security solutions that are effective for companies that are considering introducing Office 365.
table of contents
- Current Status of Cyberattacks Using Email
What is the method that has changed from malware attachment? - phishing attack
Introducing phishing attacks impersonating Microsoft, which surged in 2019 - Standard functions are not enough to use O365 safely
How does Office 365 respond to unknown malware and phishing emails? - Reality of passing through
Detected by Trellix (formerly FireEye) Email Security! - What Trellix (formerly FireEye) Email Security Can Do
How are you parsing the emails after the attack emails are sent?
(1) Current state of cyberattacks using e-mail
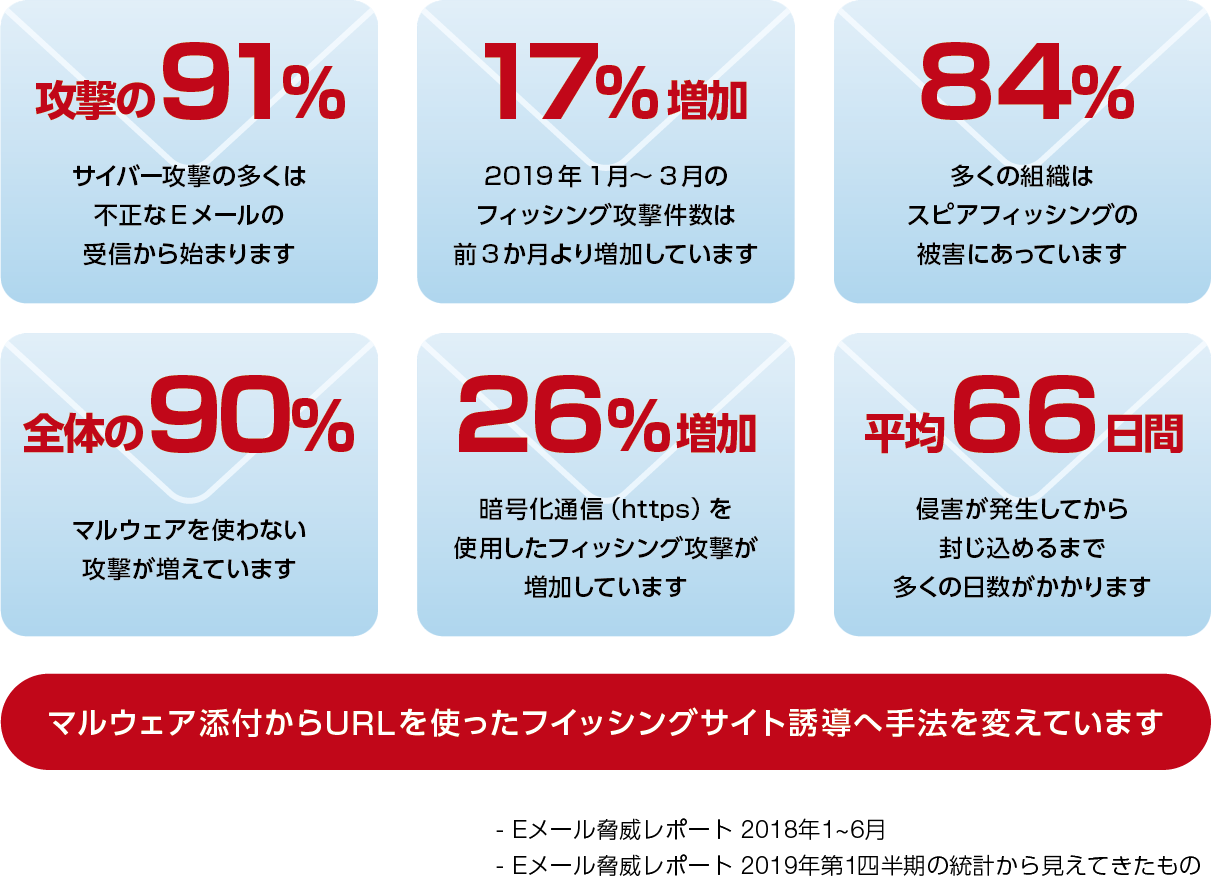
91% of cyberattacks start with receiving malicious emails. We are changing the method from attaching malware to phishing sites using URLs. Many organizations are also victims of spear phishing, which accounts for 84% of the total. From this, we can see that attacks that do not use malware are increasing, and attackers are changing their method from attaching malware to phishing sites using URLs. Therefore, there is a need for a solution that can not only inspect attachments, but also thoroughly inspect URLs in emails for maliciousness.
91% of cyberattacks start with receiving malicious emails. We are changing the method from attaching malware to phishing sites using URLs. Many organizations are also victims of spear phishing, accounting for 84% of the total. From this, we can see that attacks that do not use malware are increasing, and attackers are changing their method from attaching malware to phishing sites using URLs. Therefore, there is a need for a solution that not only inspects attachments, but can also inspect in detail whether URLs in emails are malicious or not.
In the following chapters, we will introduce the results of a survey by Trellix (formerly FireEye) on the number of phishing attacks spoofing Microsoft, and the detection results of Trellix (formerly FireEye) Email Security regarding Office 365 bypass.
Detailed document "A must-see for companies adopting Office 365! What is cloud email security that should be implemented now?"
Inquiry/Document request
In charge of Macnica Trellix Co., Ltd.
- TEL:045-476-2010
Weekdays: 9:00-17:00