product
- Line up
- Network Security: Trellix (formerly FireEye) Network Security
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense
- Network Security: Trellix (formerly McAfee) Network Security Platform
- Endpoint: Trellix (formerly FireEye) HX
- Endpoint: Trellix (formerly McAfee) Mvision
- Data Protection: Trellix Data Security
- Email Security: Trellix (formerly FireEye) Server Edition
- Email Security: Trellix Cloud Edition
- Security Operations: Trellix (formerly FireEye) Helix
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management)
- Enhanced cloud governance: Trellix (formerly FireEye) Cloudvisory
- File Security: Trellix (formerly FireEye) Malware File Storage Scanning
- Integrated Management Solution: Trellix (formerly FireEye) Central Management
- NDR Solution: Network Investigator (NI) / Packet Capture (PX)
- Cloud-based File Threat Protection: Trellix IVX Cloud
Specifications/Technical Information
- Trellix (formerly FireEye) Technical Information
- Trellix (formerly FireEye) Specifications
- Network Security: Trellix (formerly FireEye) Network Security Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Specifications
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Technical Information
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Specification
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Technical Information
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Specifications
- Integrated Management Solution: Trellix (formerly FireEye) Central Management (CM) Series Specifications
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management) Technical Information

Trellix
Trellix
Email Security 1 - Latest Trends and Trends Seen in FireEye Research

Many cyber crimes are said to start with emails.
Although companies have introduced email security products and are taking countermeasures, attackers are still trying to infiltrate their systems using all sorts of means. In order to take the best countermeasures, you first need to know your enemy. In this article, in order to reconsider email security measures, this time, based on the report "Email Threat Report: What the Statistics of the First Quarter of 2019 Revealed" by Trellix (formerly FireEye), This section introduces the increasing number of email attack methods and the trends of each method.
Techniques (How Threats Evade Email Security Products?)
- Attack using URL
- Malicious URLs using HTTPS, which was originally thought to be secure, are increasing
- Attacks that send URLs by means of bypassing mail filters are increasing
Example) Emails with only a URL and no content, or URLs that cannot be clicked
- phishing attack
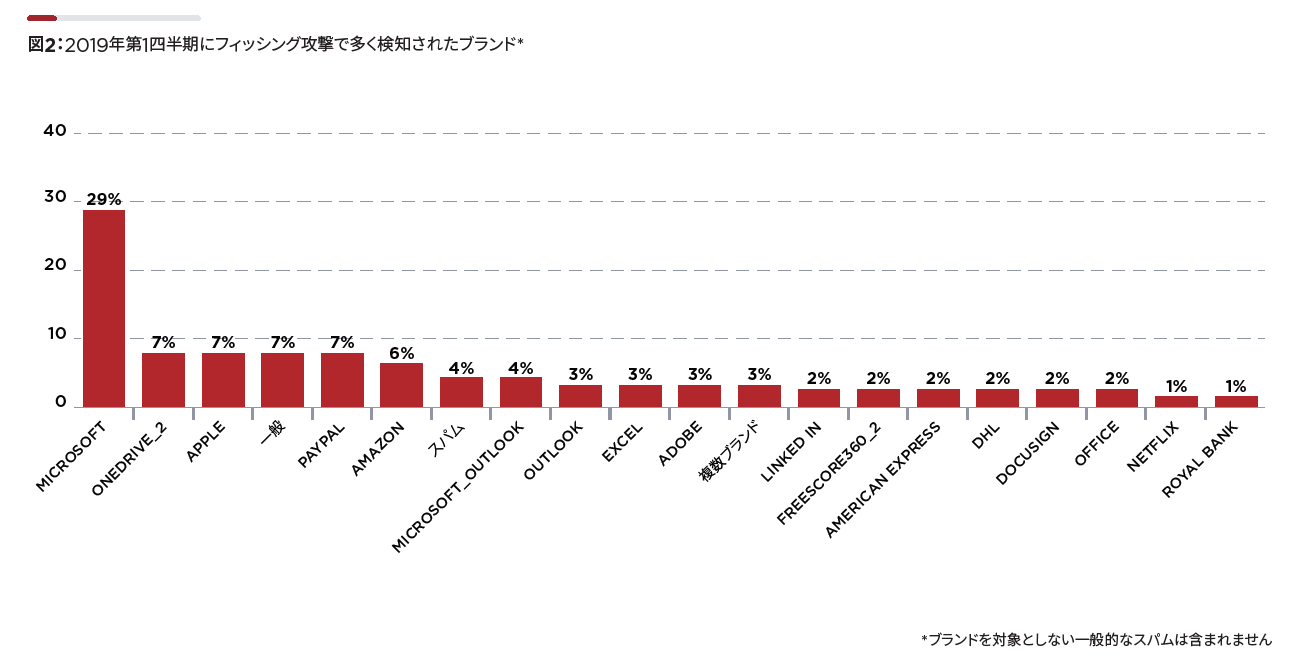
- Phishing attacks increased by 17% in January-March 2019 compared to September-December 2018
- Phishing emails impersonating Microsoft are overwhelmingly high, accounting for 30% of the total.
This is intended to convince recipients of authenticity through Microsoft's brand power. - Phishing emails using personal service brands such as Netflix, Amazon, and LinkedIn are also on the rise.
This is aimed at stealing credentials and credit card information.
- impersonation attack
- Spoofing attacks such as CEO fraud and business email compromise (BEC) are on the rise
* Increased by 25% from April to June 2019 - Two main attack methods are increasing
1. A method of impersonating an executive and sending a request to change a payroll account to the payroll department
2. Methods of compromising or spoofing systems of business partners who routinely interact with target companies
- Other attacks
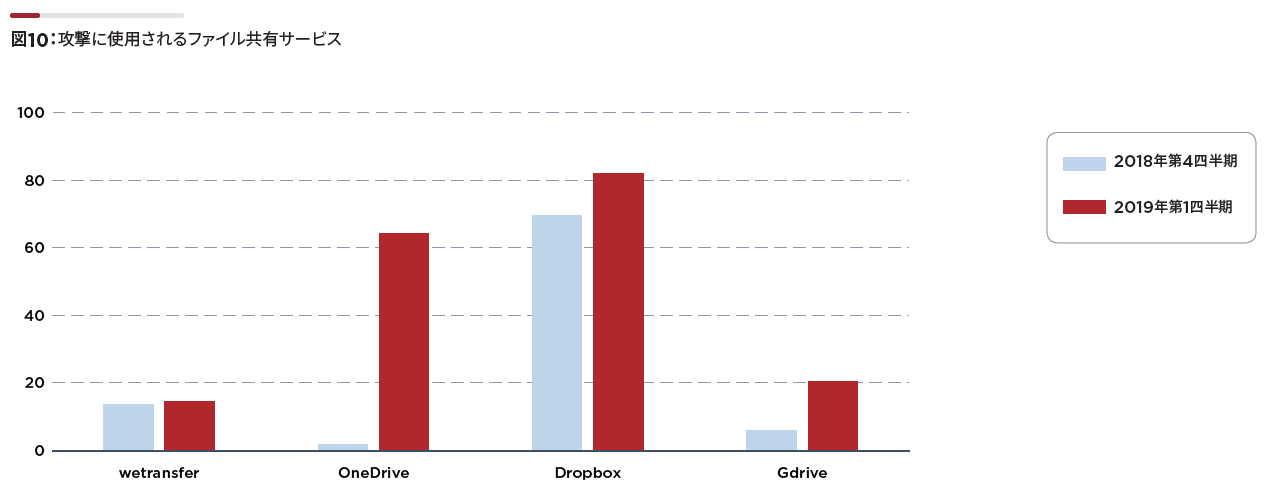
1. Attacks exploiting file sharing services
- A method of uploading a malicious file to a trusted file sharing service such as Dropbox, OneDrive, Google Drive, etc. and making the file open.
- Dropbox in particular tends to be abused, but the number of people using Onedrive has increased rapidly recently.
2. Attacks using nested emails
A method of attaching another email containing a malicious URL, etc. to the sent email
used to evade detection
3. Conclusion
As mentioned at the beginning, in order to take the best email security measures, it is first necessary to know the enemy (attacker's trends and attack methods).
This time, we will briefly summarize the latest email security threats by excerpting the content published in the "Email Threat Report 2019 First Quarter Statistics" published by Trellix (formerly FireEye). I tried.
In this report, each attack method is explained using actual e-mails sent as examples, so if you are collecting information on e-mail security or are considering introducing an e-mail security product, please report it. please look at!
In addition, the 2020 edition of the "M-Trends" report, which is packed with the latest threat trends and best practices published annually by Trellix (formerly FireEye), has been published, so information other than email security is also collected. A must-see!
Inquiry/Document request
In charge of Macnica Trellix Co., Ltd.
- TEL:045-476-2010
Weekdays: 9:00-17:00