Team T5
TeamT5
Threat hunting tool "ThreatSonar"
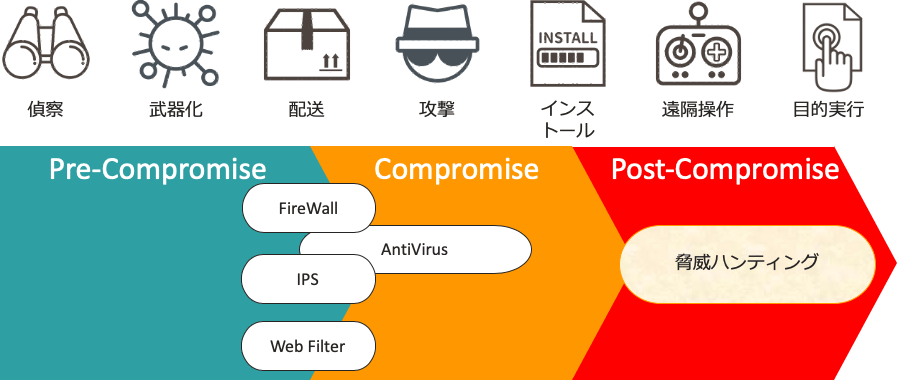
There are several types of cyber-attacks depending on the purpose, but among them, cyber-espionage attacks that target information assets are particularly sophisticated, and attacks are carried out by sneaking past existing security products. Detecting and detecting already hidden threats is difficult with existing security tools alone, and "threat hunting" is one of the detection methods. "Threat hunting" is a method of sifting through collected PC and network data based on knowledge such as attacker behavior and frequently used techniques, and then finding suspicious traces and detecting latent threats.
ThreatSonar is a platform for information gathering, data analysis, and threat analysis for carrying out "threat hunting". It is created from the advanced knowledge of the latest attack methods that Team T5 has cultivated in incident response, and is optimized to detect latent threats. The well-organized user interface makes it easy to check the analysis results and conduct further investigations based on the traces found.
Features of ThreatSonar
- Lightweight scan tools and easy-to-install servers
- lightweight scan tool
-
- Scan tool requires no installation and works in user mode
- The scan tool scans for about 30 minutes (depending on the customer's environment) and is automatically deleted when the PC is logged off
- Ability to limit CPU usage during scanning
- It specializes in detecting and collecting investigation information, and does not have functions for deleting files, stopping processes, or blocking communication, so the impact on terminals is minimal.
- Easy-to-install server
-
- ThreatSonar Server is delivered as a virtual appliance for easy installation
- Supports various platforms (VMware, VirtualBox, Xen, AWS, etc.)
- It is also possible to use our cloud server tenant (no server installation required)
- Easy-to-use feature set for threat hunting
- Implementation of threat modeling based on proprietary threat intelligence
- Process memory scanning function
- Process file writing and execution time timeline function
- Statistical outlier investigation capabilities
- An interface that can investigate the information necessary for threat hunting from various perspectives
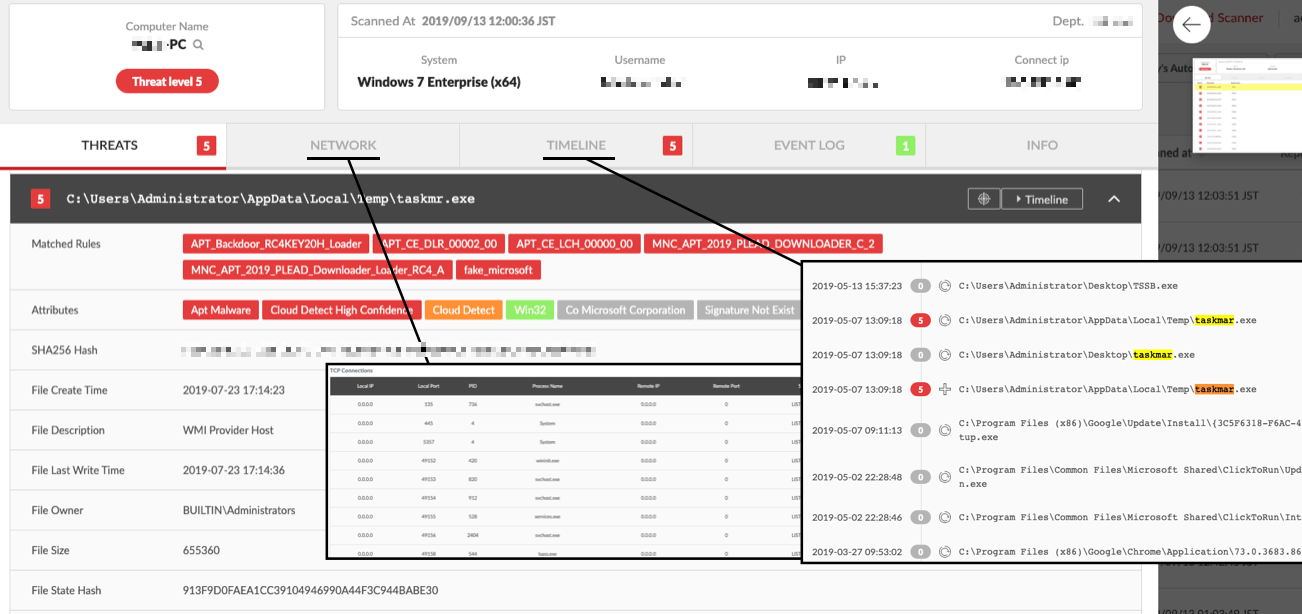
The threat level based on our unique modeling is displayed for each file and event, and it becomes the threat level of the terminal, so you can easily check the priority of the investigation. In addition, the collected information can be checked from various viewpoints, such as file-by-file, network information, and process write/execution time axis information. Possible
Use Case
- Usage example
-
- Prompt investigation of terminals and devices suspected of being infected
- PC regular diagnosis
- Usage range example
-
- Regular diagnosis of all OA terminals
- Strengthening security at overseas bases and group companies
- Enhanced security for critical assets such as servers
- Enhanced security for control terminals, etc. where agents cannot be installed
- Scan tool compatible OS
| Compatible OS | |
|---|---|
| Windows |
|
| Windows Server |
|
| Linux |
|
* Microsoft security updates KB948963 and KB968730 must be applied
Inquiry/Document request
In charge of Macnica TeamT5
- TEL:045-476-2010
- E-mail:sec-service@macnica.co.jp
Weekdays: 9:00-17:00