product
- Why choose Splunk
- Installation record
- price
- Splunk Enterprise Security
- Splunk Phantom (SOAR)
- Splunk ITSI (Next Generation IT Operations)
- Splunk Observability Cloud
- Splunk UBA
- Macnica CSIRT App Basic
- App for Splunk for Financial Institutions
- Splunk Analytics for Hadoop
- About Apps
- Splunk Edge Hub
- What is Splunk
service
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- List of services
- Macnica Premium Support for Splunk (utilization support, version upgrade monitoring)
Specifications/Technical Information
Application for evaluation machine
- FAQ

Splunk
Splunk
The Japan Net Bank, Limited

About 5 years of experience using Splunk, increasing the number of target logs and expanding the scope of use Preventing new frauds that are rapidly increasing in the cashless era and building labor management reports in a telework environment in a short period of time
POINT
- Starting with log analysis of in-house network equipment, expanding to transaction data and fraudulent site information linkage
- Debit card credit master attacks can also be detected
- Automate intelligence updates to strengthen countermeasures against fraudulent remittances
- Incorporating zero trust security and building a visualization environment for telework in a short period of time

The Japan Net Bank, Limited
General Manager, Cyber Security Office, IT Management Department
Mr. Kazuhito Ozawa
Splunk is an important weapon of JNB-CSIRT, a specialized organization that supports the safety and security of many accounts and deposits
The The Japan Net Bank, Limited (hereafter referred to as The The Japan Net Bank, Limited) is known as "the first ordinary bank license obtained after the war," "the first bank in a new style," and "Japan's first Internet-only bank." Since it started operations in October, it is a venture in the banking world that has continued to take on the challenge of improving convenience and developing new services with speed and creativity not found in conventional banks.
Sumitomo Mitsui Banking Corporation and Z Financial Co., Ltd., a subsidiary of Z Holdings Co., Ltd., have formed a strong alliance to promote joint marketing and the development of affiliated products and services. In addition to our core banking business, we have a rich portfolio of lottery/BIG/toto sales, VISA debit services, public gaming, FX (foreign exchange margin trading), foreign currency deposits/investment trusts, etc. As of January 2020, the number of accounts is about 4.6 million accounts, and the deposit balance is about 900 billion yen (excluding marketable products).
The biggest feature of The The Japan Net Bank, Limited is that it offers a wide range of services, from sole proprietors to business accounts (corporation accounts) with the potential for high-value transactions, and the expansion of strong internet security. Supporting this is the The Japan Net Bank, Limited CSIRT (JNB-CSIRT), a specialized organization that investigates and responds to computer security incidents. Launched in 2013, currently 13 people are selected from two IT-related departments: the IT Management Department, which is responsible for IT planning and management, and the IT Headquarters, which develops applications and infrastructure.
An important weapon for JNB-CSIRT is the machine data analysis platform ``Splunk Enterprise'' (hereinafter referred to as Splunk) introduced from Macnica in 2015. "In the past, even though we collected firewall logs and proxy logs for our internal system environment, we operated them separately, so we were unable to make full use of them. However, we have integrated the log analysis mechanism and are now able to analyze the results. We introduced Splunk to be able to understand the situation at any time.We mainly use it for log analysis, such as anti-phishing measures and detecting and monitoring fraudulent remittances,'' said The Japan Net Bank, Limited Mr. Kazuhito Ozawa, head of the Cyber Security Measures Office, is the brainchild of the CSIRT.
A SOC (Security Operations Center), commonly called a monitoring center, was also set up in the cyber security countermeasures office, and Splunk was used as a detection system on a daily basis. As the amount and types of logs to be captured increased, the purpose of use changed and the method of use also became more sophisticated. For example, as a countermeasure against targeted attacks on internal information systems, aggregate proxy logs by FQDN (Fully Qualified Domain Name) and by IP address on a daily basis, and register major communication destinations on a whitelist to exclude them from aggregation. This makes it easy to discover C&C communications caused by malware infections, such as by enabling you to watch only rare communications destinations.
Real-time monitoring of huge amounts of transaction data
Currently, JNB-CSIRT imports logs into Splunk in two ways. One is the internal system environment side. Firewalls, next-generation firewalls, proxy access logs and filtering logs, Active Directory access logs, etc. are collected in real time.
The other is internet banking. Akamai's CDN (content delivery network) server access logs, application access logs, request headers and responses from Akamai Cloud Monitor (a push-type real-time monitoring and analysis service for web, mobile, and API traffic) In addition to headers, geographic location information of IP addresses, response time, WAF detection information, and transaction logs of VISA debit cards handled by The Japan Net Bank, Limited, etc. These are collected every 10 minutes to 3 hours, and as of March 2020, the combined amount has reached about 35 GB/day.
The recent boom in cashless payments has led to an increase in new customers and traffic, resulting in a sharp increase in logs, but Splunk is handling it without any problems.
In addition, the General Incorporated Association Financials ISAC (Financials ISAC), which conducts information sharing and analysis on cyber security by Japanese financial institutions, frequently provides IP information of fraudulent money transfer cases that have occurred at other banks. , Based on the IP information and the customer's transaction data, whether there is unauthorized access, what kind of transactions are being performed with that IP information, whether you have logged in to another customer's account by pretending to be a third party, Splunk grasps in real time, such as whether illegal remittances are being made.
“At first, members of the IT-related department were not permitted to directly access the personal information of customers, so it was not possible to conduct follow-up investigations. After importing customer transaction data into Splunk, the utility value of Splunk improved dramatically,” says Mr. Ozawa.
Instantly create detection rules for new fraudulent methods Example of how Splunk minimized damage
In addition, The Japan Net Bank, Limited is making full use of Splunk to deal with the recent threats that shake the financial industry. Here are three major examples.
The first is a prompt response to the damage caused by fraudulent remittance phishing. From September 2019, the damage caused by fraudulent money transfer related to Internet banking has increased rapidly, and the number of incidents in November reached 573, the highest number since 2012 when statistics were available, and the damage amounted to about 776 million yen. Many of them are thought to be due to sophisticated phishing targeting smartphone users. Familiarize yourself with bank service specifications, such as by not only entering account and password information, but also one-time passwords and secret passwords by e-mail or short message (SMS) that guides you to a fake login site masquerading as a financial institution. It was speculated to be a highly organized criminal group. The The Japan Net Bank, Limited also suffered some damage, but it was able to minimize it by using Splunk.
“Although it was difficult to respond, Splunk allows customization and tuning of detection rules in almost real time, so by flexibly changing the detection rules of ad-hoc search according to the target, the phishing site itself can be discovered quickly. We also prevented unauthorized logins from customers who had their accounts stolen. Without Splunk, the investigation would have taken longer and the damage would have spread like other banks,” says Mr. Ozawa. and appreciate its speed.
The second is the detection of credit master attacks. A credit master attack is a technique that exploits the regularity of credit card numbers and adds special calculations to mechanically brute force numbers to identify other people's card numbers. The Japan Net Bank, Limited handles VISA debit cards, and since this type of card, which is immediately debited from a bank account when used, can cause enormous damage, transactions are constantly monitored, and if a certain method is used, Splunk can easily can now be detected.
According to Mr. Ozawa, "In order to detect credit master attacks, it is important to monitor transactions on a daily basis and immediately start an investigation when an abnormality is discovered. Splunk is extremely suitable for such a detection method. Thanks to you." We were able to greatly reduce the workload,” he said.
The third is to prevent fraudulent use of accounts. Unauthorized use of bank accounts refers to the use of bank accounts for acts that violate laws, regulations, or public order and decency. It is used to deposit and withdraw criminal funds such as fictitious billing and Internet fraud. The Japan Net Bank, Limited is striving to prevent such incidents by clarifying internal roles and responsibilities, centrally managing information, and strengthening monitoring of abnormal account transactions with Splunk. In addition, based on the information obtained from Splunk, it is said that it has a close cooperation system with each prefectural police, the Financial Services Agency, the Japanese Bankers Association, etc.
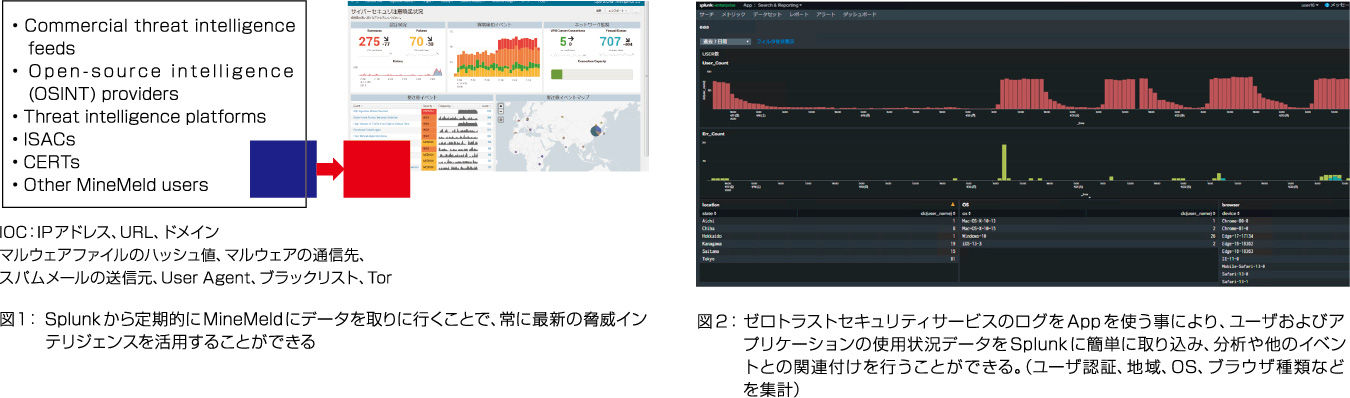
Connect Splunk and MineMeld for the latest threat intelligence
In addition, The Japan Net Bank, Limited has recently strengthened its use of Splunk Apps. Of particular note is the automation of threat intelligence using the PaloAlto Network MineMeld (MineMeld) framework that can be linked with Splunk. MineMeld uses OSINT (open source intelligence) to automatically acquire and integrate IOC (security indicator) data from various sites (feeds). Based on that information, threat information is blacklisted and output so that it can be blocked by various security devices. By regularly retrieving data from Splunk to MineMeld, you can always use the latest IOC and block it with various security devices. In addition, it supports multiple IOC distribution sites by default, and in addition to IP addresses, URLs, domains, etc., malware file hash values, malware communication destinations, spam mail senders, User Agents, blacklists, etc. It can be collected with Splunk.
“I mainly use Tor (freeware that anonymizes connection paths in TCP/IP) to monitor access. Tor updates its IP address list daily, so I let MineMeld relay it to Splunk. We are taking it in.” (Mr. Ozawa)
The Japan Net Bank, Limited 's efforts have been reported to the Financial ISAC's Working Group on Countermeasures against Illegal Remittances, and they are also contributing to sharing attack methods and monitoring know-how that Splunk is implementing.
Easily realize telework labor management by utilizing zero trust solutions
Security is not the only use of Splunk by The Japan Net Bank, Limited. Since March 2020, the company has deployed telework using a remote access service on a company-wide scale, but Splunk is also being applied to labor management and employment management, which is said to be delayed in its operation. “What the HR department needed was who worked from what time to what time (the time they logged out). Collect logs with the Splunk App, aggregate the results with stats, and send them to the HR department every day. We are providing it,” explains Ozawa. Based on Splunk, he created this system in just one day.
This log collection mechanism leveraged the Splunk App for remote access services. This service is a next-generation remote access solution based on a "Zero Trust Security" model that provides appropriate authentication and minimum access privileges for access from any user, device, or location. Easily achieve secure access to various business applications distributed over the network, improving business efficiency and security at the same time. With Apps, you can configure Splunk to call APIs, making it easy to bring user and application usage data into Splunk for analysis and correlation with other events. It is mainly used to manage overwork, prevent shadow overtime, and check unauthorized overtime work.
"Because it is Zero Trust, gateways and firewalls are not required, construction costs are low, and it works smoothly even with an internet connection. By combining Splunk and Apps, we were able to build a safe visualization environment for telework in a short period of time." (Mr. Ozawa) )
In the future, The Japan Net Bank, Limited plans to update Splunk's management server and strengthen its operational environment. "It's been five years since we started using Splunk. When an incident such as phishing occurs, the operational flow for immediately grasping the situation using Splunk has become firmly established. The number of young employees in the cyber security countermeasures office and JNB-CSIRT has increased, and Splunk With the widening range of human resources who can use it, new ideas for its use are born every day,” says Ozawa.
As a first mover in the domestic banking world, the industry is wondering how The Japan Net Bank, Limited will continue to challenge the development of new services and improve convenience with unprecedented speed and creativity. I am paying a lot of attention.
User Profile
| The Japan Net Bank, Limited | |
|---|---|
| URLs | |
|
Established in September 2000. For the first time since the end of World War II, we acquired a business license under Article 4 of the Ordinary Banking Law, and began operations in October of the same year as the "first bank in a new form" and "Japan's first Internet-only bank." Currently, as a group company of Z Holdings and Sumitomo Mitsui Banking Corporation, we leverage our strong financial base and cutting-edge network in our products and services, and our financial soundness rated A+ (stable), high capital adequacy ratio, and safe assets. Its strengths are operations and a well-balanced profit structure. |
|
Weekdays: 9:00-17:00
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Weekdays: 9:00-17:00