product
- Why choose Splunk
- Installation record
- price
- Splunk Enterprise Security
- Splunk Phantom (SOAR)
- Splunk ITSI (Next Generation IT Operations)
- Splunk Observability Cloud
- Splunk UBA
- Macnica CSIRT App Basic
- App for Splunk for Financial Institutions
- Splunk Analytics for Hadoop
- About Apps
- Splunk Edge Hub
- What is Splunk
service
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- List of services
- Macnica Premium Support for Splunk (utilization support, version upgrade monitoring)
Specifications/Technical Information
Application for evaluation machine
- FAQ

Splunk
Splunk
JGC Information Systems Co., Ltd.

J-SYS has taken security measures based on the theory of sexuality. Freely analyze and monitor logs with Splunk to strengthen deterrence and visualize IT infrastructure
- Relying on deterrence with security measures based on the theory of good nature, it was not possible to grasp the status of compliance with rules
- There were few system administrators, and they also had other duties, and it was difficult to understand the problem because the operation of the equipment was inexperienced.
- Due to the bloated and complicated logs, there is a limit to human analysis, and the work know-how depends on the individual.


- Quickly visualize access history for each user by strengthening security based on the theory of sexism
- Enables quick analysis of logs from multiple devices even for system administrators who are not familiar with the functions
- By making rules after visualization, operation that does not depend on know-how is realized

JGC Information Systems Co., Ltd.
Sales Headquarters System Analyst
Mr. Nobuhiro Shibusawa
Breaking away from the traditional good-natured theory to security based on the premise of the bad-natured theory
JGC CORPORATION was spun off from JGC HOLDINGS CORPORATION a general engineering company, in July 1983 and established as a user-oriented IT service provider. In addition to providing system management services to JGC, our parent company, we have inherited the methodology of prime contractors that JGC has cultivated over many years, and we also offer package business and commercialization of the technology and intellectual property to companies other than JGC. It provides contracted software development business and outsourcing business. The strength of the company is that it consistently proposes rational project management and system integration know-how based on an engineering approach, from the concept stage of information system construction to the operation phase.
In recent years, security damage such as cyber-attacks and malware infections, which have become more complex and sophisticated, poses a threat to companies. . The engineering business, which is a collection of advanced proprietary technologies, is a mass of confidential information, and cyberattacks targeting it may exploit vulnerabilities not only in JGC and J-SYS but also in group companies. There was a need to create a drastic mechanism, such as the possibility of information leaks from overseas bases in the future.
"We believe that the basics of security measures are 'deterrence power' that makes it seem impossible to break, 'defense power' that reliably prevents fraudulent acts, and 'traceability' that allows us to verify incidents. However, in addition to that, we realized that the conventional system of the goodness theory was insufficient, and unfortunately, we changed our policy to protect our company's information assets with a new security policy based on the premise of the badness theory."
That's what Mr. Shibusawa, who was in charge of planning and introducing in-house IT equipment at the J-SYS Technology Development Department at the time, said. Until now, J-SYS had regarded security measures as a deterrent, so even if someone copied data from the company's file server, it would not be detected. The system administrator did not know whether Although logs were collected, the contents were not checked on a daily basis, and the means of analysis was not clear.
"Since the number of system administrators was limited, they were not skilled in all the functions of security devices, and they were not able to take time to work concurrently with system development. was"
I felt the possibility of achieving unprecedented visualization and generating inspiration
On the other hand, according to Mr. Shibusawa, the current situation of security log analysis and monitoring systems is becoming more severe year by year. In addition, log analysis related to the Internet, such as proxy servers, DHCP servers, and web filters, requires matching work that correlates each data. Since knowledge and experience are required, it was also a problem that know-how was accumulated by individuals and tended to become dependent on individual skills," he recalls.
For threats such as zero-day attacks that cannot be completely dealt with by anti-virus software, rapid log analysis and automation are means of early detection. Also, in the event of an incident such as a data leak, it is essential to use a tool suitable for analyzing huge logs such as file operation histories. It was no longer possible to strengthen security manually, and there was an urgent need for systematization.
Mr. Shibusawa was looking for an integrated log management product to solve these problems, and was strongly interested in the uniqueness of Macnica 's Splunk. "By using Splunk to automate and improve the collection and analysis of various system logs, which had previously relied on human labor, we were able to achieve unprecedented visualization and felt that there was a possibility for inspiration to emerge. An important objective was to create a system that automatically detects events, but we believed that implementing a log analysis and monitoring system using Splunk could have a significant effect."
Collecting, integrating, and analyzing logs to strengthen "deterrence" based on sexually evil theories
The company began researching integrated log management products, including Splunk, in October 2013, and at the same time as taking Macnica 's Splunk hands-on seminar in November, they introduced a free evaluation version to test the functionality in detail. Verified. Mr. Shibusawa said, ``When we actually imported the data and verified it, we got the results we expected, and found that the functions were easy to understand and very easy to operate even for first-time the Company. I felt it was the best fit."
After that, while evaluating other companies' products in parallel, the company confirmed the superiority of Splunk's functions, applied for the development budget for the next fiscal year, and decided to introduce Splunk. From April 2014, we officially started using the evaluation version environment as it is in the production environment.
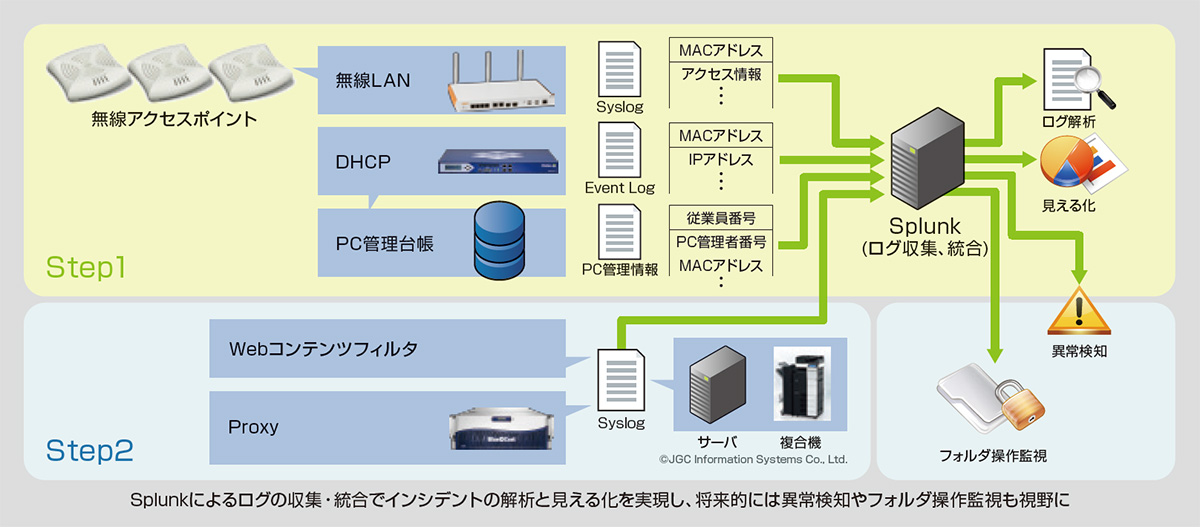
From May to August 2014, as Step 1 of Splunk utilization, we started by collecting, integrating, and analyzing access logs for wireless LANs, DNS/DHCP servers, and file servers as monitoring targets. Visualization was realized by comparing it with the PC management ledger. In addition, the company also provides conditional permission for BYOD (Bring Your Own Device), in which personal devices are used for business purposes, so remote access monitoring of devices brought in is also conducted.
In addition to being able to accurately grasp the usage status of terminals on a weekly and daily basis, it is now possible to instantly analyze logs from multiple devices to see who, when, where, and what kind of access is being performed. , it is also possible to quickly visualize the access history of each user.
Mr. Shibusawa said, "An important result of Step 1 was that we were able to strengthen the 'deterrence' based on the theory of sexuality. In addition, Splunk displays parameters in the search function, so system administrators who are not familiar with the function can However, various information can be viewed with simple operations, and it has become possible to operate without depending on the know-how."
After the evaluation of Step 1 was completed in August, the plan for Step 2 was started. In Step 2, by importing logs from web content filters, proxies, etc., we plan to monitor folder operations and strengthen the other issues of "defense power" and "tracking power."
Mr. Shibusawa says that the introduction of Splunk has produced various side effects that were not originally planned. "By visualizing changes in the number of access points to wireless LAN access points, it is possible to understand the usage status of information assets within the company, which is useful in considering where to install access points and balancing the load."
In addition, as Step 2, we plan to import the operation log of the multifunction device into Splunk, which was not originally planned, to check for operations outside business hours and abnormal numbers of prints, and to monitor information taken out of paper. It is said that
“By encountering Splunk, I was able to analyze logs from various angles, centrally manage all kinds of data, and visualize the IT infrastructure. By producing results, the person in charge is interested in the monotonous log analysis work, and this has the effect of bringing new awareness," says Mr. Shibusawa. He also emphasizes that it is important to be able to lead to the next action regardless of who analyzes it without making the skill dependent on the individual.
And I'm convinced that Splunk is the easiest way to make that happen.
User Profile
| JGC Information Systems Co., Ltd. | |
|---|---|
| URLs | |
|
JGC Information Systems was established as a user-related IT service provider in July 1983 after the information systems division of JGC, a global engineering company, spun off. In addition to supporting JGC's information infrastructure, we provide total consulting, system construction, and operation for four domains (construction, facility/asset management, infrastructure, products & services) with the two strengths of "engineering" and "project management." providing. |
|
Weekdays: 9:00-17:00
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Weekdays: 9:00-17:00