product
- Why choose Splunk
- Installation record
- price
- Splunk Enterprise Security
- Splunk Phantom (SOAR)
- Splunk ITSI (Next Generation IT Operations)
- Splunk Observability Cloud
- Splunk UBA
- Macnica CSIRT App Basic
- App for Splunk for Financial Institutions
- Splunk Analytics for Hadoop
- About Apps
- Splunk Edge Hub
- What is Splunk
service
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- List of services
Specifications/Technical Information
Application for evaluation machine
- FAQ

Splunk
Splunk
CyberAgent, Inc.

膨大な個人情報・機密情報を守るため Splunkで小さなインシデントも見逃さない環境を構築 20分の1の対応時間で分析精度も大幅に向上
- In-house system incident management is important for handling huge amounts of personal information
- Diversified analysis is difficult because it takes several days from log collection to analysis
- OSS analysis systems require advanced knowledge and increase human costs


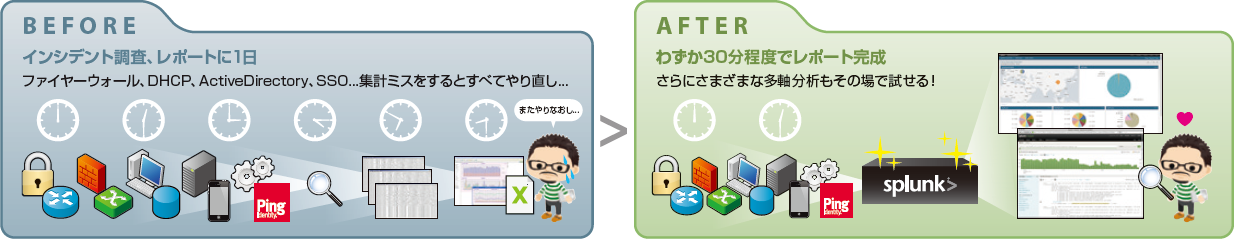
- Logs are automatically collected, and the analysis time that used to take 10 hours is drastically reduced to 30 minutes.
- 何度も試行できるため分析精度が大幅に向上
- Easily create custom reports with Splunk Apps

CyberAgent, Inc.
Company-wide System Headquarters
Rei Yamaguchi
“何でもない”インシデントもログ収集だけで時間がかかる
CyberAgent, Inc. has developed a large number of smartphone games such as “Ameba”, which represents “Amebablog”, which is used by many celebrities and celebrities, “Girlfriend (provisional)”, and “KIZNA”. It is a major Internet service vendor that mainly provides services for consumers such as community services, applications and web applications, and also develops advertising agency business such as advertisement distribution and effect analysis for companies.
In September 2014, the number of users of Ameba, which is the core of the business, exceeded 40 million, and the number of blog posts exceeded 1.9 billion. Because CyberAgent handles such huge amounts of personal, confidential, and important information, it was necessary to pay particular attention to the security management of internal systems.
Mr. Akira Yamaguchi belongs to the Company-wide Systems Division, which integrates and manages the systems used by more than 3,000 employees across the entire group. ing.
Although they had taken basic security measures using network security devices and external managed services, Mr. Yamaguchi had to handle detailed incident management, and he was overwhelmed with this response.
An incident here is not necessarily an actual security breach. Even if you don't receive any damage as a result, or it wasn't an attack in the first place, if behavior that looks like a cyberattack or virus infection is discovered, you must investigate everything. This is because of the possibility of zero-day attacks and new types of malware. Basically, these cannot be determined by measures that detect self-evident security breaches, so it is necessary to analyze and respond to them individually.
When Mr. Yamaguchi found a "strange behavior" in which he could not identify a clear cause by checking server logs in detail, it was necessary to cross-check the logs of other systems such as firewalls, DHCP, and ActiveDirectory. rice field. Even collecting logs from various systems is a hassle. Systems under Mr. Yamaguchi's control are fine, but systems managed by other staff or departments must be collected with permission.
The vast amount of logs collected in this way was formatted in such a way as to be easy to calculate using Excel and Access, and in some cases, adjustments were made by writing simple programs. As a result, even a small survey took a day or two. Even Mr. Yamaguchi, who is very experienced, takes such a long time. “In this kind of analysis, we often make predictions and try to search on some kind of analysis axis, but the number of hits is zero.・It is difficult to repeat and error.We thought that we needed a mechanism that could be repeated many times in a short time and easily find the 'analysis axis with good sensitivity'." (Mr. Yamaguchi)
First of all, in addition to Windows/Linux servers, it is necessary to have a function to centrally collect logs including network devices. In addition, it would be even better if the data could be visualized in easy-to-read graphs, etc., and it would be easier to create visual reports that are easy to report to management. You also need the ability to set thresholds and raise alerts. The solution Mr. Yamaguchi chose was "Splunk Enterprise."
Operation is easy to understand and anyone can easily respond to incidents
Mr. Yamaguchi, who is also a developer, initially tried to build an analysis system by combining the open source software "El asticsearch" and "Ki bana". Development, construction, and operation required continuous assignment of excellent engineers, and there was concern that the TCO would balloon even if the system itself was free.
While considering and testing several methods, Yamaguchi attended a hands-on seminar on Splunk hosted by Macnica. However, perhaps because he had experienced the complexity of an analysis system built using OSS, he was skeptical and thought it would be difficult to get started. "However, it was much easier to use than I expected. Even operations that aren't in the textbook are intuitive when you try them out. Even now, although I've only been using Splunk for six months, I can create reports that meet my expectations in an hour or two. You can really see how easy it is to use when you actually try it. Macnica has knowledgeable engineers who will answer any questions you may have, so I recommend attending a seminar first," said Yamaguchi.
After the seminar, Mr. Yamaguchi obtained a free trial version and decided to try analysis using log data from actual incident response. I was surprised that the analysis that previously took a long time could be completed in a very short time. Compared to the OSS analysis system mentioned above, the usability is different, and it seems that anyone can easily handle it. He was convinced that the human cost for initial introduction and operation could be greatly reduced. "Another factor in our selection was the presence of 'SplunkApps.' By looking at the templates and add-ons developed by various engineers, we were able to see how Splunk could be used to perform the analysis we expected. Now, we are free to create custom reports by referring to the Apps developed for the single sign-on system and authentication system that we are using." (Mr. Yamaguchi) )
Analysis that used to take 10 hours was completed in just 30 minutes
Splunk was introduced at the same time as PingFederate, Macnica 's single sign-on product. According to Mr. Yamaguchi, PingFederate took three months from the start of the project, but Splunk itself did not require much effort.
The Splunk server environment uses Amazon Web Services (AWS). Taking advantage of the cloud, which is easy to scale up and scale out, we realized a small start with a c3.large environment (CPU: 2.8GHz x 2.4GB memory, 500GB storage). It took 1 day to install, 1 day to set up log collection, 1 week to build the prototype, and 1 month to go live. The work was done by Mr. Yamaguchi alone, and it was enough for him to do it in between his development work.
An image of actual utilization is shown in the figure above. In addition to acquiring log files from the aforementioned PingFederate, 802.1X authentication systems, ActiveDirectory, VPN devices, firewalls, etc., depending on the system, logs can be executed by executing scripts or via network ports to perform cross-sectional searches. ing. In addition, operation logs are also collected from core systems, etc., and used for administrator audits.
By the way, I am concerned about the introduction and operation costs of Splunk. Splunk's usage fee is determined by the amount of log data per day. Therefore, in order to specialize in security management, Mr. Yamaguchi limited the logs that he constantly worked on to data useful for incident response, and kept other logs in AmazonS3/Glacier cloud storage to minimize costs. made it
If a more detailed investigation is required, or if the logs have increased due to cyberattacks, there may be a need to import more logs than the license allows. But Splunk is fine as it allows up to 4 bursts of log growth per month. In addition, since the usage fee does not depend on the number of CPUs or nodes, he likes the fact that he can control the balance between cost and performance by scaling up only at the time of investigation and shortening the analysis time. “The benefits of using Splunk were immediate. Investigations that used to take 8 to 10 hours were reduced to just 30 minutes. The ability to search multiple times has greatly improved analysis accuracy. In addition, I feel that the quality of system management has improved, as I can devote the free time to the original development work and preventative measures." (Mr. Yamaguchi)
User Profile
| CyberAgent, Inc. | |
|---|---|
| URLs | |
|
"Amebablog" where more than 10,000 celebrities and celebrities post articles as bloggers, community service "Ameba Pigg", game service "Girlfriend (provisional)", and other smartphone applications that support lifestyles. An Internet service vendor that mainly provides services for consumers with a huge number of users, and also operates an advertising agency business for companies. |
|
Weekdays: 9:00-17:00
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Weekdays: 9:00-17:00