product
- Why choose Splunk
- Installation record
- price
- Splunk Enterprise Security
- Splunk Phantom (SOAR)
- Splunk ITSI (Next Generation IT Operations)
- Splunk Observability Cloud
- Splunk UBA
- Macnica CSIRT App Basic
- App for Splunk for Financial Institutions
- Splunk Analytics for Hadoop
- About Apps
- Splunk Edge Hub
- What is Splunk
service
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- List of services
Specifications/Technical Information
Application for evaluation machine
- FAQ

Splunk
Splunk
[Under development] App that analyzes AD logs
We introduced our proxy App at an event held in April this year. This Proxy App makes it easy to use proxy log statistical/analytic knowledge in Splunk, such as:
- Immediate visualization of web usage
- Providing necessary analytical research methods
- Customizable dashboards and reports
And from the event questionnaire, we received many opinions that "I want an app for Active Directory logs", next to the proxy app.
In the general pattern of incident investigation, I think that it is often carried out in the order of "identifying the terminal → identifying the target communication → confirming the process executed on the terminal → reporting the incident".
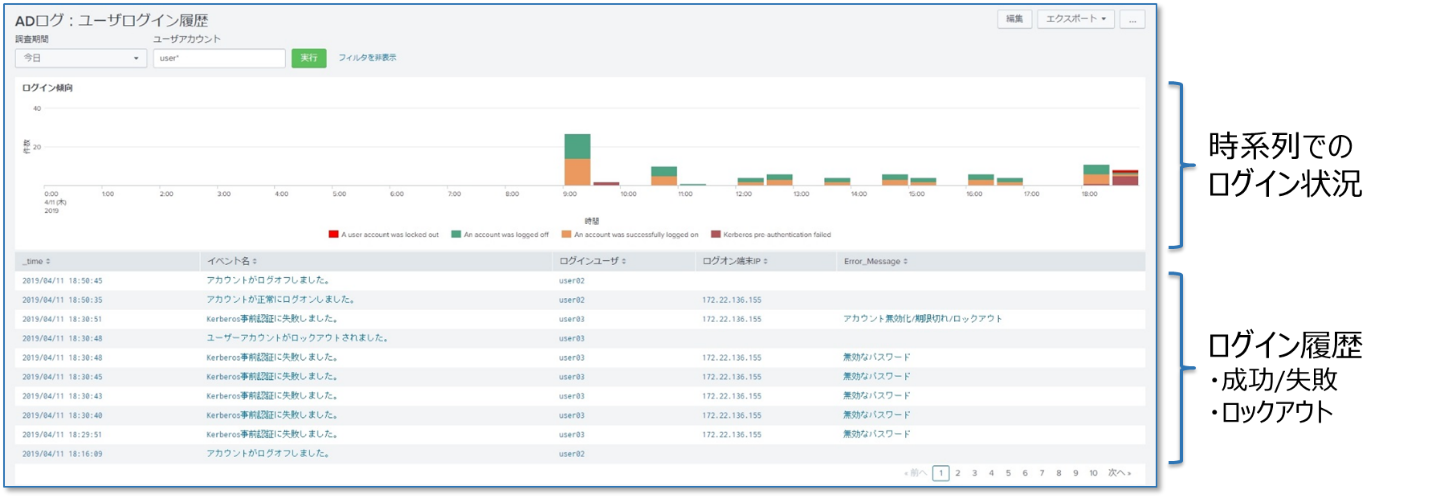
By looking at the proxy log, you can see what kind of communication was performed with the outside and on which terminal. However, we do not know what the external attacker executed on the terminal. So one way to find out what has been done on the terminal is to look at the AD logs.
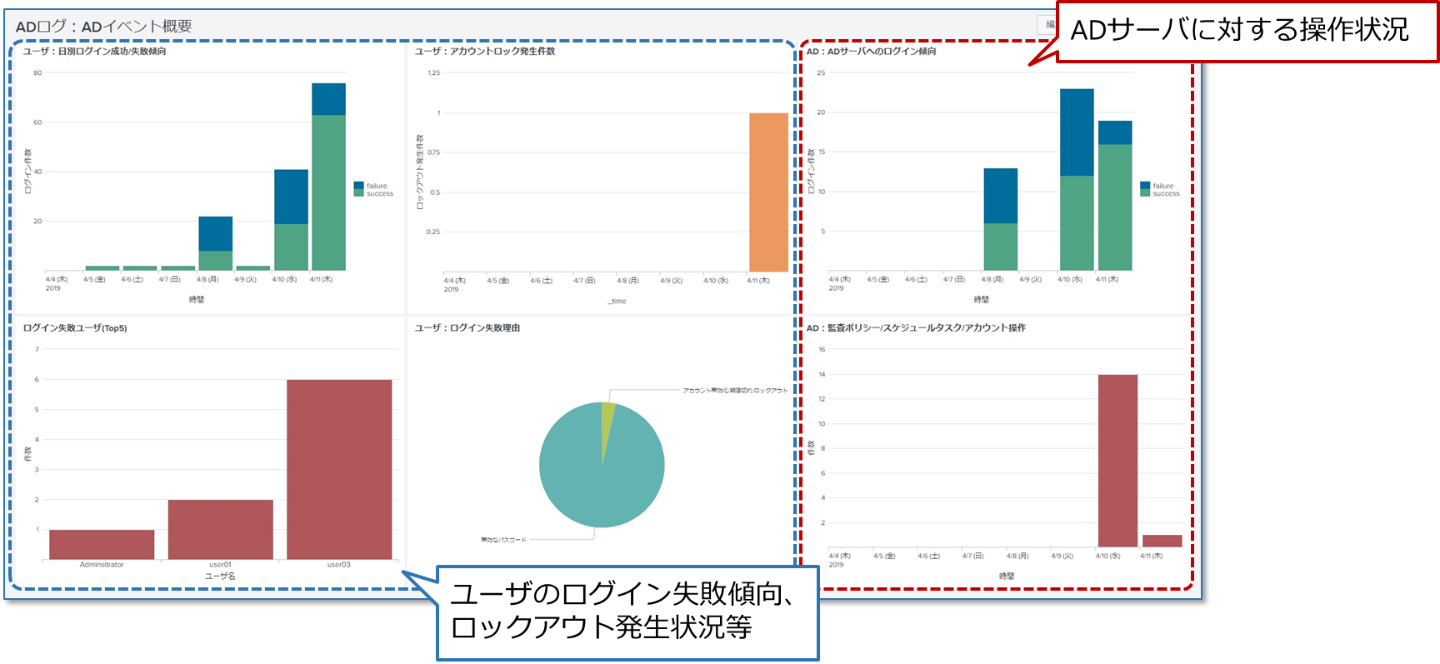
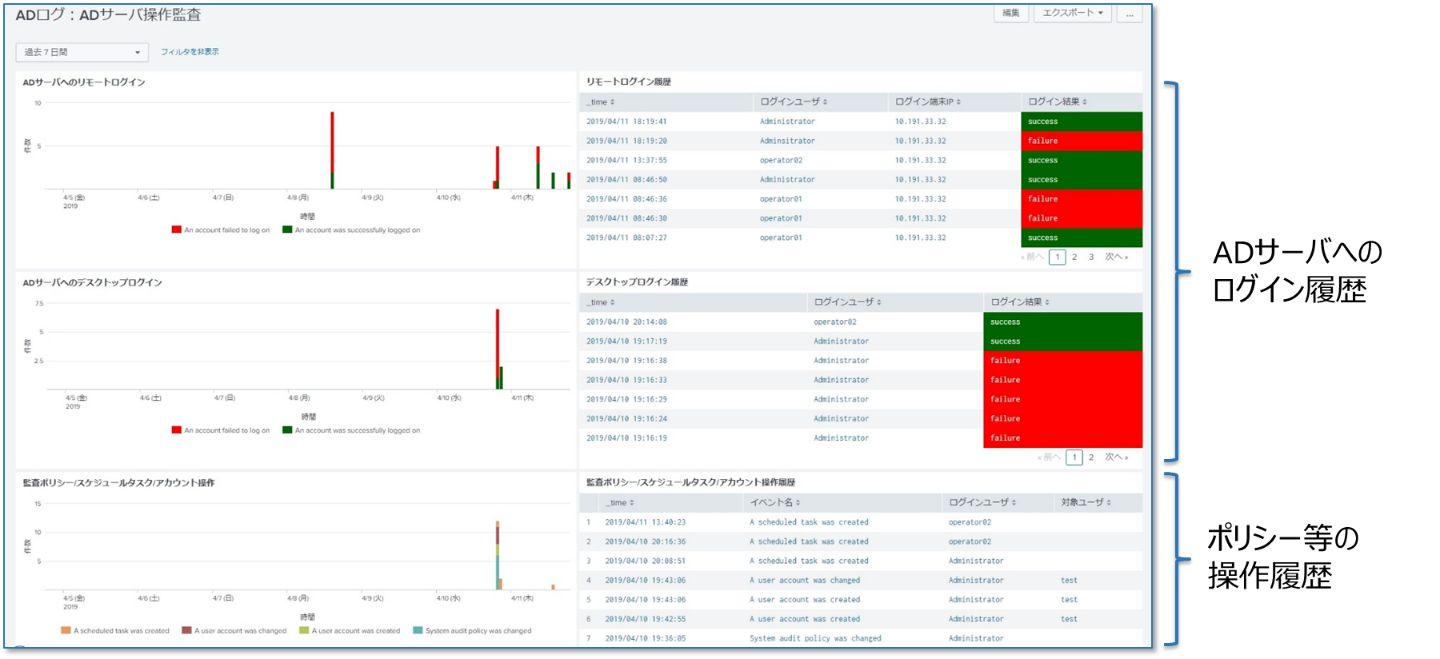
Splunk can aggregate the logs required for each investigation phase and prepare detection rules (searches) according to the phase. In order to make it easier for customers to conduct this series of incident investigations, we are exploring whether it is possible to provide an investigation method for AD logs in the form of an "App".
Here's a snippet of an AD App I'm currently working on.
<Sample 1: Visualization of AD events>
<Sample 2 domain user login history investigation>
<Sample 3: AD server operation audit>
What do you think.
ぜひAD Appについてご意見をいただければと思います!
Weekdays: 9:00-17:00
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Weekdays: 9:00-17:00
![[Under development] App that analyzes AD logs](/business/security/files/spl_blog20190814_draw04.png)